How to enable DNS-over-HTTPS (Secure DNS) in Chrome, Brave, Edge, Firefox and other browsers
DNS-over-HTTPS, known as Secure DNS in most Chromium-based browsers, is a relatively new feature of modern web browsers that is designed to protect DNS information. DNS is used in most user-initiated requests on the Internet, e.g. when you click on a link in a browser or type a site manually in the browser's address bar. Up until recently, these requests were in plain text; this meant that your Internet Service Provider and other users on the same network could get a clear log of all your Internet activity.
DNS translates human readable domain names and hostnames to IP addresses that computers use. Secure DNS encrypts the data, which protects it against spying and also manipulation. Secure DNS in Chromium-based browsers is off by default, unless a Secure DNS provider is used on the system.
Since it is beneficial to enable Secure DNS, users may want to check the settings of their browsers to make sure that it is enabled, or to enable it if it is not.
Tip: you can test if your browser supports Secure DNS.
Configure Secure DNS in Google Chrome
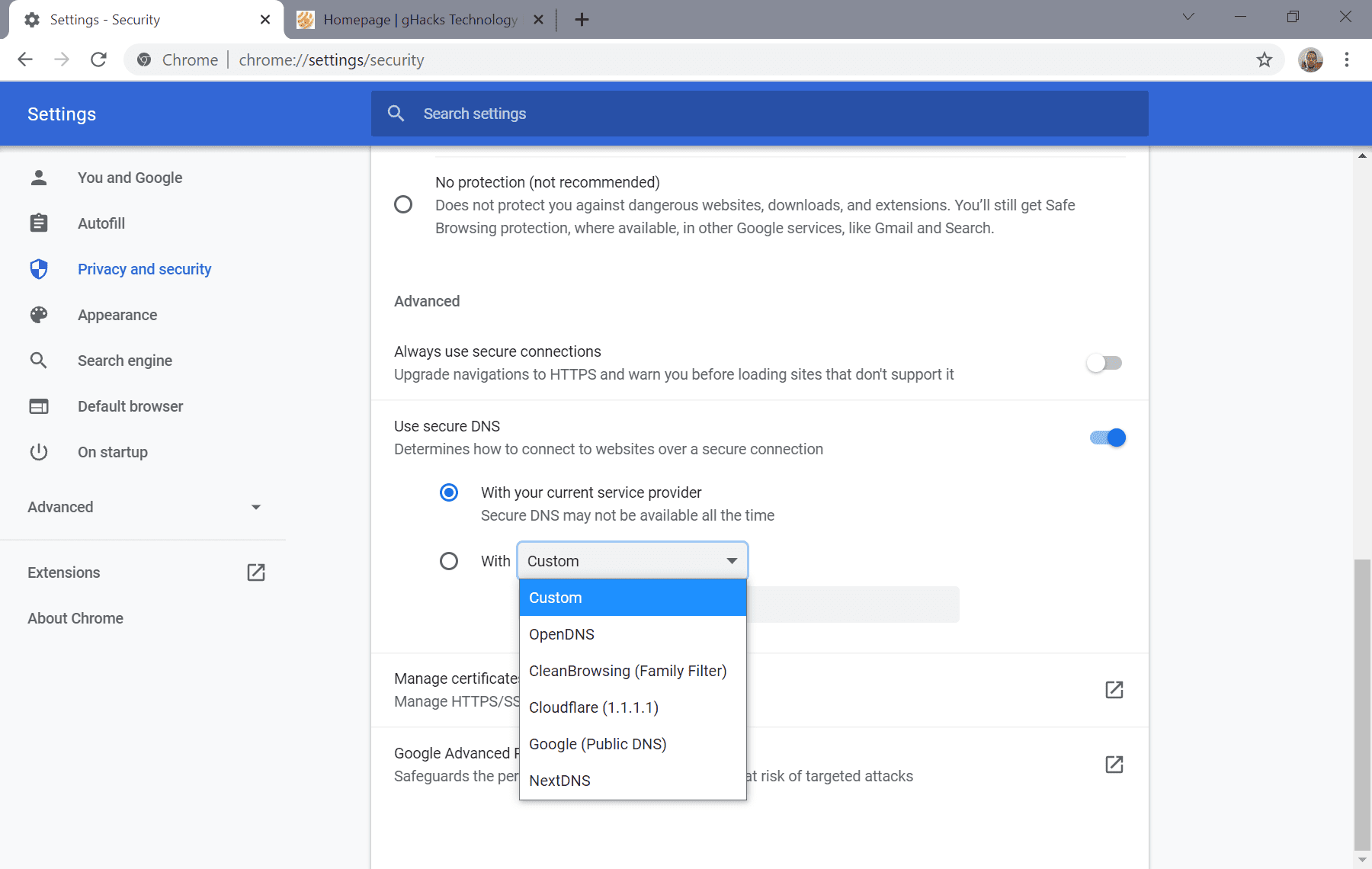
To get started in Google Chrome, load the browser's security page by pasting the following URL in the browser's address bar: chrome://settings/security. If you prefer to go there manually, select Menu > Settings > Privacy and Security > Security.
The "Use secure DNS" preference determines whether the feature is turned on or off. If it is set to off, toggle it to enable it. You have two main options at this point:
- Configure Chrome to use the default DNS provider of the system
- Select one of the preset Secure DNS providers or set a custom provider.
The first option works only if the default DNS provider supports Secure DNS. Many ISPs don't, and it is usually better to pick a specific DNS provider from Chrome's listing of supported providers or add a custom provider.
Select the "With" option, and pick one of the preset providers, OpenDNS, CleanBrowsing, Cloudflare, Google, or NextDNS, or select custom to add a custom provider using a URL (these are provided by the provider).
Configure Secure DNS in Microsoft Edge
The configuration of Secure DNS in Microsoft Edge uses a similar system. Either load edge://settings/privacy directly in the browser's address bar, or go to Menu > Settings > Privacy, search and services manually.
The preference "Use secure DNS to specify how to lookup the network address for websites" determines whether Secure DNS is enabled. If it is turned off, toggle it to enable it. Edge uses the current service provider, meaning the DNS provider that is set on the system, by default. Switch to "Choose a service provider" and click in the field below it to pick a preset provider or to add a custom provider using a specific URL.
Configure Secure DNS in Brave Browser
Brave follows the default Chromium implementation of Secure DNS for the most part. Load brave://settings/security in the browser's address bar to get started, or select Menu > Settings > Privacy and security manually instead to open the configuration page.
The setting "Use secure DNS" determines whether Secure DNS is enabled in the browser. By default, the system's service provider is used. You may switch to "With" to select one of the preset providers or to set a custom provider. Brave supports Quad9 next to the default selection of providers that Chrome supports.
Configure Secure DNS in Opera
Opera Browser supports Secure DNS, called DNS-over-HTTPS, as well. Either load opera://settings/?search=dns directly, or go to Opera Menu > Settings > Advanced > Browser, and scroll down to the System group of preferences.
The preference "Use DNS-over-HTTPS instead of the system's DNS setting" determines if secure DNS is enabled. If it is not, toggle the preference to get a selection of providers and an option to set a custom provider.
Opera lists several Cloudflare options and Google Public DNS only.
Configure Secure DNS in Vivaldi
Vivaldi follows Chromium's implementation. It is a bit weird that you can't find the option when you browse the regular settings or search for it in the Settings. You need to load chrome://settings/security in the browser to display the option.
There you find the option to toggle "Use secure DNS" to enable or disable the feature, and to switch between using the system provider, a preset provider or a custom provider. Like Brave, Vivaldi supports Quad9 next to all other providers.
Configure DNS over HTTPS in Firefox
Firefox supports DNS-over-HTTPS as well. Users of the browser need to load about:preferences#general in the address bar and activate the Settings-button under Network Settings on the page that opens.
The setting "Enable DNS over HTTPS" determines if the feature is enabled or not. Check the box to enable it. Firefox includes just two preset providers, Cloudflare and NextDNS, but has an option to set a custom provider as well.
Closing Words
Most Chromium-based and Firefox-based browsers support similar options.
Now You: Have you enabled Secure DNS / HTTPS over DNS?
It’s interesting that although firefox is privacy oriented, it doesn’t have quad9 dns.
In my =Chromium= browser
(latest version for Ubuntu Linux 20.04),
the “Secure DNS” entry
is not visible.
I tried:
chrome://settings/security
but can’t see this option.
Martin ?
Anybody can point me in the right direction?
Would this prevent dns injection attacks?
Yes
DNS Providers lists:
https://kb.adguard.com/en/general/dns-providers
https://github.com/curl/curl/wiki/DNS-over-HTTPS
…
( https://www.rethinkdns.com/ )
…
Good!
DoH or DoT: no thanks!
As usual when blogs are repeating verbatim big tech’s speech, this is only telling the smaller half of the story that benefits them, while ignoring the important facts that result in an opposite conclusion about the claimed privacy benefits.
Encrypting DNS towards the default provider has the claimed privacy benefits. That’s the first of the options that are proposed by Google, the right thing to do.
Using another DNS provider than the ISP-provided, even encrypted, globally lowers privacy, because the ISP is still able to infer what sites are visited, so that this mainly only duplicates that data to another organization, which thus lowers privacy even if that other company can be trusted.
https://blog.powerdns.com/2019/09/25/centralised-doh-is-bad-for-privacy-in-2019-and-beyond/
If in addition that other organization can’t be trusted, for example a well known data rapist like Google and Cloudflare or openly police funded like Quad9, then of course it’s even worse. So when Martin Brinkmann writes that
“it is usually better to pick a specific DNS provider from Chrome’s listing of supported providers or add a custom provider. Select the “With” option, and pick one of the preset providers, OpenDNS, CleanBrowsing, Cloudflare, Google, or NextDNS, or select custom to add a custom provider using a URL (these are provided by the provider).”
he doesn’t only lie about third party encrypted DNS being globally more private, he even lies about using nothing less than Google as a DNS provider as being more private. As could be expected, the industry pushing the first lie initially was only a first step for now, a bit later, pushing the worse, second one, now without even a word of warning next to that.
I see that there are also lesser known data rapists like Cisco’s OpenDNS that are advertised here (did those DNS providers pay browser companies for that or was it only a solidarity gesture between members of the data abuse industry against all the rest of humanity ? Either way it’s selling your sensitive personal data to a third-party, at a zero or non zero price). Let’s have a look at their privacy policy, the OpenDNS one redirects to the general Cisco’s one (already something not really legal to do at least in the EU):
https://www.cisco.com/c/en/us/about/legal/privacy-full.html
“We may share personal information in the following ways:
Within Cisco and any of our worldwide subsidiaries for the purposes of data processing, such as marketing,
[…]
With Cisco business partners or vendors, so that they may share information with you about their products or services.
[…]
With […] other third parties as necessary to […] protect the rights, property, or safety of Cisco, our business partners, […] or others
[…]
In aggregated, anonymized, and/or de-identified form [for any purpose]”
Thank you for protecting our privacy with partners like that, browser companies.
Let’s note finally that among the listed spyware browsers, the worst two for that specific problem seem to be Opera and Firefox, for not even providing the only privacy-positive option of encrypting the default DNS, just instead suggesting third-parties.
In fact, Firefox is much worse than all the others for that specific problem for being the only one, or the first if they’re not the only one (I don’t know if the other browser companies have yet dared to be that low on privacy), to switch lots of its users *by default* to a third-party DNS provider (and often a data rapist one like Cloudflare initially to add to the problem).
By the way, at Mozilla they usually experiment their worst new anti-features such as this one on USA users first. I’m not sure how they determine if one is a valid target, possibly the language locale. Therefore be careful if you follow those “privacy hardening guides” that tell you to use an english locale in Firefox to “fight fingerprinting”, especially if those guides are from people of a dubious background who have had an habit of justifying everything Google/ads in Firefox, you may end having your DNS queries sent by default to a US data rapist company, even if you’re not from that country, and even if Mozilla itself had not intended to feed your data to them. Example here:
https://github.com/arkenfox/user.js/issues/1027#issuecomment-883190687
This has been around since before dirt. It’s confusing as hell. Now so called Big Tech is climbing on board with their “First!” BS. There’s a reason Google is so late to the party and FF was first (at least in the mainstream.) Has to do with where chromium gets DNS; search it.
No matter how “secure and private” you think you may be, you still have to make a request and the reply has to know where to go. How that’s done is where the confusion enters.
You can hide nothing (http), just your data (https headers?) or everything with a real VPN, where your trust is placed in the VPN provider. This is just consumer stuff.
Play with stubby and see how confused you become.
The whole subject is a mess, you really have to first determine what your obfuscation level is to be, then proceed with something you remember six months down the road when it breaks from a win update or whatever.
Why evoke a lie when an approximation or a mistake could as well explain it all (given we consider a disagreement)?
Anyway, I quite agree that Encrypted DNS servers are to be chosen with caution. Google, Cloudflare, OpenDNS are not the wisest choice, to put it mildly. I wouldn’t be so affirmative with Quad9, but I may be mistaking; anyway I use neither of those three.
I emphasize on the DNSCrypt-proxy system-wide DNS-Encrypted choice. You’ll find dozens of servers to choose from (Google, Cloudflare, OpenDNS included : it’s up to the user!). Want a list? Here’s the of Public DoH and DNSCrypt servers : [https://dnscrypt.info/public-servers]
Be sure to click on ‘Rows per page’ > ‘All’ at the bottom of the screen!
Logically, is cost money to run a ‘public’ server so cash input is required. No further comment.
Very few certitudes but doubts are to be taken for what they are and not for counter-certitudes.
I don’t think it is wise to reconsider the best on the ground it’d be parasitized by an hypothetical bad intrusion.
Choices imply risks. We just try to minimize them. Too little or too much are both the culprits of a wide majority of mistakes. On the other hand taking life as it comes seems to offer a limited perspective. “Too much order is sclerosis, too little is anarchy” as would say Konrad Lorenz : same with any decision, it’s all in the balance, a calculated risk as we say.
Your comment, implicitly considering that caution is to be exercised with free products, seems a wise attitude. The problem here is that there are free solutions which happen to be healthy, and that complicates the equation.
At this point the question is wich DNS do you use out of curiosity. On PC (as you know, I gave you an AH script) I use Acrylic DNS Proxy (as you know, I gave you an AH script) + DNSCrypt-Proxy 2 without front end. Simple DNSCrypt need an update.
As a similar alternative on smartphone in the new adventure of a pig who gives personal data to the world of apps (nothing of pork is thrown away) right now I set DoH with Rethink DNS+Firewall. As a first impresion it allow DoH, DNSCrypt, filter lists on device blocklist and I can block apps.
PS: if listening thanks to @Ash user for the tips. Much work to do, many question to ask. Joking about it in comparison I promote Win10 as a ‘privacy friendy’ OS. :-)
Many questions to ask? You know you made me feel better. Atleast for a couple of seconds this non-techie ass believed himself to be a tech expert. I saw you and Tom Hawack’s exchange in a different article on DNS and everything went above my head, but hey if there is anything I would love to help assuming I know about it to begin with :-)
@Yash
Tom Hawack is the real busy guy who puts effort and time into all of this. I usually limit myself to read the news about some new extension or software, so I asked him for some tested DNSCrypt server.
In fact, I probably read from him about AcrylicDNSProxy and since I tried it and I liked it but I didn’t find a quick method to merge the lists from filterlists.com (if I remember correctly he used HTTP Downloader + HostMan), a very simple script with AutoHotkey was born by miracle. Happy to see he still use it.
AcrylicDNSProxy supports DoH and you can also set one or more file hosts like Windows (named in the tutorial AcrylicHostsGroup1, 2..) to filter DNS queries.
Right now one question is about voice search input where I don’t understand if there is an alternative to Google app. If I disable com.google.android.googlequicksearchbox I lost the feature. I read something on AnySoftKeyboard but I can’t figure it out.
Try Kõnele. Enable it in voice menu. I use OpenBoard, not because it is better than Anysoft but I just use it – haven’t really put much thought into it. After enabling Kõnele in Voice input menu, I was able to use it by tapping voice input in keyboard so it should work in any keyboard. Though big issue is service is mediocre at best.
Here are links related to app –
https://github.com/Kaljurand/K6nele-service
https://github.com/Kaljurand/K6nele
There’s eSpeak also to check if it can work.
https://github.com/alphacep/vosk-api – This is another service to try, though the procedure is complicated for my mind.
Flite TTS doesn’t work as voice recognition service, it only works as TTS service.
I don’t use Voice input mainly because Google has a monopoly, and so options are severely limited other than Google which is huge privacy issue, and other services doesn’t work well.
@Ash?
@Anonymous
Right: @Yash
My memory sucks.
@Shiva, hello :)
I do remember our past exchanges regarding DNScrypt and I still use the AH script you provided, though somewhat modified; in particular I now have set the script to download blocking lists with the ‘HTTP Downloader’ application (command-line) given the script’s native download process encounteres issues with some servers (maybe related to ciphers, not sure).
Presently I call upon Encrypted DNS servers located in France and Belgium :
BEST-1: server_names = [‘moulticast-fr-ipv4’]
BEST-2: server_names = [‘opennic-R4SAS’, ‘scaleway-fr’]
BEST-3: server_names = [‘moulticast-fr-ipv4’, ‘opennic-R4SAS’, ‘scaleway-fr’]
BEST-4: server_names = [‘dnscrypt.be’, ‘moulticast-fr-ipv4’, ‘opennic-R4SAS’, ‘scaleway-fr’]
BEST-5: server_names = [‘dnscrypt.be’, ‘acsacsar-ams-ipv4’, ‘moulticast-fr-ipv4’, ‘opennic-R4SAS’, ‘scaleway-fr’]
Mostly BEST-4 but BEST-2 when I wish to use the Anonymized DNS Relays (not all DNS servers accept them).
As for the smartphone alternatives : I don’t use a smartphone, only a basic mobile.
@Tom Hawack
Ok, thanks. I also set scaleway-fr among the servers.
If the AH script very rarely encounters download issues it is usually due to changes in the address of the lists. I’ve made some changes too using now 3 AcrylicHostsGroup: software (like Firefox, Potplayer), WindowsSpyBlocker (not often updated like the other lists) and the main unify filter lists. Then another 2 scripts to download and merge WindowsSpyBlocker and update hosts file using the AcrylicHostsGroup above and the exceptions rules.
Honestly I don’t dislike the new smartphone. Surely it is a creator of superfluous urges but the are also some good stuff. But… Apart from the model chosen where I was wrong not to check about the compatibility with custom ROMs (completely unaware of it), after I installed or replace nearly all apps from F-Droid I started to search a good choice related to pay\donate the developers: after reading Exodus data and permissions at Aurora Store I’ll do it on PC. Maybe I became paranoid without my knowledge but it seems like a big market of personal data.
Firefox the right choice!
Anyway also Windows 11 has a DNS-over-HTTPS in dns settings.
@name_same
> Firefox the right choice!
DoH is not exclusive to Firefox. However, Firefox is the only browser silently hijacking the DNS provider in the background, replacing it with whatever provider is paying Mozilla for that sweet data flow (usually Cloudflare).
@IH,
You get a dropdown to pick semantically or can add whatever IP you want. Been like that for quite a while.
@ULBoom
Unfortunately, Firefox did opt users into Cloudflare’s DNS in the US automatically. That’s hijacking of the DNS provider and is unacceptable if done behind the user’s back. More info here:
https://ungleich.ch/en-us/cms/blog/2019/09/10/turn-off-doh-firefox/
https://old.reddit.com/r/privacy/comments/f99umb/firefox_turns_controversial_new_encryption_on_by/
Settings >> General >> Network Settings >> Enable DNS over HTTPS
Disable, use NextDNS or use custom. Done.
Switching the DNS provider behind the user’s back = no biggie, as you can turn it off in case you even notice. Laughing my ass off, LOL.
I have nothing against the setting being offered, I have something against the automatic hijacking.
It appears if Manual Encrypted DNS is added in Windows Network & Internet Adapters’s setting, then DoH doesn’t appear to work if Browser DoH is also turned on.
Both https://www.cloudflare.com/ssl/encrypted-sni/ & https://1.1.1.1/help only showed as DoH working when I turned Off Browser setting for it and only kept the Windows setting.
Is this how’s its supposed to work or something clashing on my machine locally.
Windows 11 supports DoH, not the competing standard DoT. So, the second link you provided should say Yes for DoH and no for DoT when you’ve disabled the browser functionality, as I think you should (using both doesn’t make sense).
The first link you mentioned doesn’t get that specific. On that one, the first three items should be green. Encrypted SNI is apparently dependent on browser support, which may still be in progress.
Browsers’ DNS-over-HTTPS are better than nothing but remain tied to the browser.
For system-wide DNS-over-HTTPS or DnsCrypt protocols the DNSCypt Project is my choice.
DNSCypt Project : [https://dnscrypt.info/] -> DnsCrypt-proxy, all platforms
Simple DNSCrypt : [https://github.com/bitbeans/SimpleDnsCrypt] -> simple management tool to configure dnscrypt-proxy, only on windows based systems (a front-end so to say).
DNSCrypt-proxy includes releases for Windows based systems, very easily configurable with one file : dnscrypt-proxy.toml — Really *very* easy, even for non-techies as myself.
If there’s more than one device going through a gateway, it’s much simpler to do whatever you want in your router vs. individual configs.
(unless you have some yucky thing from your IPS that won’t allow it.)
Only downside is roaming, you’ll go back to the IPS DNS or whatever is default.
:)
This! (DNSCrypt)
Also available on linux.
This!
Or you can use YogaDNS.
I use dns.watch. Would anyone know the url I insert under Custom DNS? Tried several and it’s not accepting any.
The german one, one of their IP’s is:
84.200.69.80
Their site will give you the others.
The one it tells you to use on their homepage?
https://resolver2.dns.watch/dns-query
Tried it, it doesn’t work.
Although Chrome and Quad9 is not the fastest choice I could make, it is the best compromise overall for me in US.
@chesscanoe
Quad9 is really fast here in The Netherlands (ping avg. 8ms).
Maybe they don’t have a server near you?
Using latest Win10 21H1, Chrome stable, and Quad9 to a server 100 miles away I get ping=9, jitter=0, download=410, upload=28. I connect my laptop to my gateway/router box via RJ45 cable through a plugable (brand name) converter to USB. I’m happy.
About the “performance” argument that was used by some third-party DNS providers as an excuse to steal data (“you real men don’t care about that hippie privacy/anti-corporate garbage, you trust us to provide you with the most performant and convenient products and understand it’s worth the costs”) , it’s also an absurdity.
The ISP provided DNS servers are on the contrary likely to be the fastest, as the closest and also more able to return the IP of the fastest servers when that matters.
But anyway, the performance difference being of an opposite sign to that announced by those third-party providers doesn’t really matter because its absolute value is too small to matter compared to more important problems like privacy which also tell us not to duplicate our DNS query data to those third-parties.
If you use the program DNSJUMPER you can select from several DNS-suppliers, also the secure version.
Is assume that then I use secure DNS OS-wide, so with any browser??
I have installed Vivaldi v. 4.3. Bld 2439.56 (x64) (From ‘-21-10-21) and when I go to vivaldi://settings/security I cant find the by you, suggested setting?
When I search for Menu > Settings > Privacy, search and services there is a separated privacy and security branch, but no services branch?
And also in the privacy branch and security branch there is no advanced section and also there is no secure DNS section?
So did you use a beta version or a other browser?
Same problem here.
@Anon – missed your tip, “lines crossed” maybe.
Which one to choose from?
Cloudflare?
Thanks!
The hard to understand answer is that you have to enter the url chrome://settings/security, which then takes you a vivaldi://settings/security url which allows you to make the change. It makes no sense to me but it works
Replace the url with chrome://settings/security for Vivaldi. Worked for me.
Thans Anon,
For your respons.
Not ferry smart of me to think about the Google chrome possibiltys.
Still don’t like DoH. DNS is protocol, so is HTTP, you can encrypt both so please don’t mix them.
DoH will not magical make DNS secure against tracking and at the moment it is incompatible with every embedded security hardware out there.
DoH moves the decision-making from the OS level to the application level and adding some complications. It is centralizing your metadata in some big company’s (eg. cloudflare, google), so nothing can go wrong, right? Right?
On 24th June the Playstation Network was down because of a Verizon configuration error.
And Amazon, and Cloudflare, and Linode, and many many more …
Now imagine a more and more centralized DoH getting it’s chance to do that.
You seem smart. Can you fix this internet protocol mess?
It’s impossible to enable the option in Edge for me : “This setting is disabled on managed browsers.” ??
Chrome or some extensions seem to cause that. I needed to prune registry. That may not be the answer for you. Start reading
https://geeksadvice.com/remove-chrome-managed-by-your-organization-browser-hijacker/
The only way I found is to use Ultra Virus Killer program. In “Threat Scanner” section, it gave me “Microsoft Edge reset options”. I applied those and it unlocked “This setting is disabled on managed browsers.” warning.
It didn’t work for me.
I believe that it’s enough to have changed some settings that displease Microsoft.
And I have no idea how to disable that message. Single user, no network, no admin other than myself. Who knows. I try to minimize my use of Edge.
Thanks. That indicates https everywhere can go.
One issue on restart (that shows it works) is my home page is set to a town family’s http page. I am getting a double warning about proceeding to and insecure page. Is there a method to set exceptions?
HTTPS Everywhere and DoH have got literally nothing to do with each other.