How to disable JavaScript in PDF documents in Firefox
Mozilla released Firefox 88 last month. The security and feature update for the organization's Firefox web browser introduced a major change in the native PDF viewer of the browser. Up until now, JavaScript was ignored by Firefox when PDF documents were viewed in the browser. The execution displayed the JavaScript document in the browser but ignored any JavaScript code that it contained.
Mozilla enabled the execution of JavaScript in PDF documents in Firefox 88; this means that JavaScript code will be executed if it is present in a PDF file that is viewed in Firefox. There are legitimate reasons for supporting JavaScript in PDF documents, for instance to verify the input in form fields or to make changes to a document based on data when it is opened or when certain events happen.
Unfortunately, JavaScript in PDFs may also be used to execute malicious code. In other words: JavaScript is a security risk when it is executed in PDF documents.
Most Firefox users may not need the feature, and it is a good idea to disable the execution of JavaScript in PDF documents in the browser to protect the system against JavaScript-based attacks.
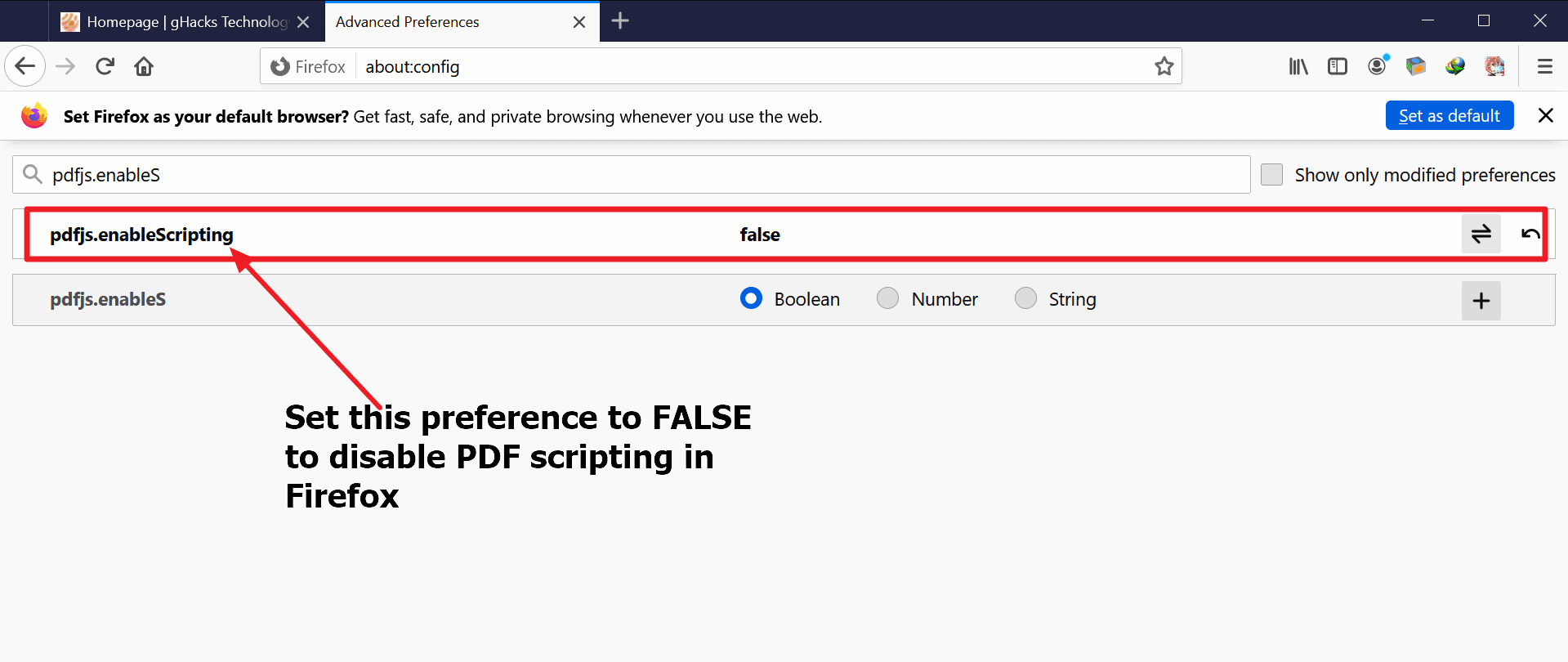
Disable JavaScript execution in PDF documents
Firefox users may disable the execution of JavaScript by the browser's native PDF viewer in the following way. Note that there is no option to turn it off in the main settings of the browser.
- Load about:config in the web browser's address bar.
- Confirm that you will be careful to proceed.
- Use the search at the top to find pdfjs.enableScripting.
- Set the preference to FALSE with a click on the toggle button at the end of the line.
- A status of FALSE disables JavaScript execution in PDF files.
- A status of TRUE enables the execution of JavaScript in PDF documents (default)
Firefox will ignore JavaScript in PDF documents if the preference is set to FALSE.
Testing
You can test the effect by loading PDF documents that include scripting from a site like PDF Scripting. Just download the sample PDF documents and check them in the native PDF viewer of Firefox to see if the execution is blocked.
Closing Words
Should you disable JavaScript in PDFs in Firefox? I think it is a good idea, especially since you may enable the feature again if you run into issues with certain PDF files in Firefox.
Now You: what is your preference?
Any Reader that allows javascript to run is asking for trouble. Thanks, Adobe, for the bloatware!
I ams sure that Firefox will provide enough security inside to avoid any risk from opening PDF files in those way related in the article. At least I wish it, obviously. Anyway, there were tons of people who had installed Flashplayer, included me, and no problem after years of hard use of it. :]
Flash was 100% known, confirmed, verified by well-known researchers and bug hunters across the world to be basically buggy as shit. It had more security holes than a bloody soup strainer. Just because you were supposedly lucky and didn’t get exploited as far as you know doesn’t mean it wasn’t a hot mess, as Adobe itself admitted. Same is the case with this feature. Defaulting it to disabled and providing an easy to find toggle under Preferences should have been Mozilla’s stance if it really gave a damn about user security. The browser could also have been made to prompt the user when any PDF with embedded JS was first encountered, clearly explaining the security impact and explicitly asking for user permission to turn JS support on. But of course Mozilla chose to do none of that because it really couldn’t care less. All they care about right now is how best to turn a once top-class browser into a loser Chrome clone.
@the MozKillsFFFromWithin connoisseur
Quote: “The browser could also have been made to prompt the user […] clearly explaining the security impact ff.”
Would you please be so kind as to clearly explain what “security implications” You mean, and give a real-world example.
Thanks
You can do your own research Emil, or wait for the inevitable sandbox escape exploits at pwn2own and the consequent CVEs, followed finally by patches from shameless and unrepentant Mozilla.
Yes, Vishal Gupta, over at AskVG, provided the security tip on April 23. I recommend reading the article for more information and why Mozilla made the choice it made:
https://www.askvg.com/security-tip-disable-javascript-execution-in-pdf-viewer-in-mozilla-firefox/
Agree with others, should have been in main menu with disabled as default.
People should avoid using Firefox if security is their concern.
https://www.whonix.org/wiki/Dev/Chromium#Firefox_and_Chromium_Security
My comment will likely trigger a lot of people, don’t expect me to answer at all. I’m not interested in useless argues.
It’s time to trust security experts rather than random people around the web.
Is that you Iron Heart? Our resident disinformation spreader in chief?
Ladies and gentlemen, imagine if ghacks had a voting system, it would be like this
– https://old.reddit.com/r/privacytoolsIO/comments/n50kb8/is_brave_better_than_firefox_even_though_it/gwys2u1/
– this is a random person on the internet getting downvoted for being a DICK and talking a load of SHIT
Meanwhile, here is someone who makes far more sense by using CONTEXT
– https://old.reddit.com/r/firefox/comments/lbu6q2/why_do_people_say_chromiums_sandbox_is_better/glxjrjg/
– this is a Firefox dev, not some random * [Editor: removed, please stay polite, even if it is hard]
Please stop listening to random * and their SHIT peddling, people!
@*Alert
Insulting people won’t change the fact Firefox is insecure compared to the Chromium-based browsers.
https://www.whonix.org/wiki/Dev/Chromium#Firefox_and_Chromium_Security
Enough facts and details are provided on the page above. I know it’s easier to insult people than actually take your time to check the content of the page.
Insulting respected security and privacy researches is disgusting and definitely unasked for.
It’s a pity Firefox users can’t stay civil when shown the sad state of their favorite web browser.
Please put an end to this ridiculous debate.
People believe what they want to believe, and deny what they don’t want to believe.
This is a theorem of all ages.
Even an unknown opinion or a different value system is an opportunity for “new discovery”.
We need to be tolerant and pay attention to different opinions. (Do not use propaganda or incite hatred, though.)
Aircraft are at risk of crashing due to bird strikes or lightning strikes.
Ships are dangerous because of the risk of running aground or sinking.
Automobiles pose a risk of accidents causing injury to occupants, personal injury, and property damage.
Even activities such as “walking” without relying on civilized devices can put us at risk of sudden attacks such as heart attacks, and get involved in some kind of accidents.
Even if you are at home, there is a danger of earthquake damage or war…
In other words, as long as we exist in this world, there will always be “danger” around us.
We should not be overconfident that things are safe.
It is important to understand things correctly and to pay attention to “risk management”.
There is no such thing as “absolute safety”, even with Chromium.
And of course, Firefox.
@Owl
The things you said are good, as there are risks with each software but some folks not just here but in other public forums as well just say stuff for the sake of it.
I currently use Ubuntu as my main OS, with Lineage OS in my primary smartphone and also has another old smartphone albeit with no sim card in it. But some folks here regularly mention some links and according to those links, Windows is better than Linux. Fair enough everyone has their preferences but then they say Linux is not secure. Same goes for not try to use LineageOS or microG or Firefox or VPN because of some weird security issue. I mean its a public forum but there’s a limit to spreading fake news which has no real world applications.
I only use Firefox on desktop(using it for years) as its more than enough for all tasks whether work related or private, and so when someone wrongly claims that it is not secure on a public forum, there is no point in just ignoring that BS.
“I only use Firefox on desktop(using it for years) as its more than enough for all tasks whether work related or private, and so when someone wrongly claims that it is not secure on a public forum, there is no point in just ignoring that BS.”
Disagreeing with claims made by security experts doesn’t make those claims false or “bullshit”.
You’re free to use whatever software you like, but don’t claim facts are false or “bullshit” only because you don’t agree or like them.
Inform yourself who Daniel Micay is, and then check what he had to say about the censorship on Reddit when he stood his ground regarding Firefox’s security:
https://twitter.com/DanielMicay/status/1264204763748589568
@Anonymous 9:46 am
I know who Daniel Micay is but the website I was directing my finger at is https://madaidans-insecurities.github.io/index.html (and you are more than welcome to raise its so called concerns that maybe I’m not going to type below), I don’t know who its author is(interestingly it works on open source projects including Whonix) but it is regularly mentioned here in gHacks by someone else.
That website view regarding VPN is ‘VPNs give nearly no security benefit as around 90% of websites already use HTTPS which encrypts your connection. VPNs will only ever give a security benefit when you’re browsing a site lacking HTTPS which is rare.’
The link to that article is – https://madaidans-insecurities.github.io/vpns.html
It further states – Although, a VPN can have a privacy advantage since it does hide the websites you visit from people monitoring your traffic.
It says more things in that so called insightful article but I’m not going to mention them here. So here’s my view, in web world a user always has to check whether a service is useful and can be trusted. There are many VPN providers who have lied but dismissing a service outright is equally bad. That website guy hasn’t heard of no log VPNs, ram disk mode in VPNs which by the way defeated a certain government warrant. You are more than welcome to comment on it.
https://madaidans-insecurities.github.io/security-privacy-advice.html – In this link, it states to use Chromium browsers not Firefox, not use Linux but other OS namely Windows(yes open source project guy suggesting open source Windows), not use LineageOS but GrapheneOS on Pixel 3 or iPhone.
In this link https://madaidans-insecurities.github.io/android.html it says LineageOS doesn’t include firmware updates and its a security risk. Don’t use microG and most laughable reason to use Pixel 3(he says its because of hardware) on GrapheneOS is because of Titan M chip and the link redirects to Google blog. The website also says to use Edge Browser because of Windows Defender Application Guard(WDAG) – brilliant although it has a bug currently(surprise!) and gHacks has an article currently on homepage. And it has many more hilarious bits regarding no use of Netguard app and many more.
I check the things I’m using and take views of both types of people whether they are opposing Firefox, Linux, etc or supporting them, and to see whether issues raised have real world applications, but unfortunately some folks have one agenda and that is to spread fake news regarding a particular software.
So you better raise some valid points or you’re more than welcome to rant about everything like @Lemengton 9:23 am did above or countless others do on every Firefox article.
I gotta say I’m more than excited to face the security risk of LineageOS, Firefox, VPN, Linux in my personal devices that would close this debate once and for all. But the thing is I’m still waiting to encounter those issues myself but I hope in 31st century I would confront them.
@Yash
First of all, I would like to say that I appreciate the polite way you replied to me. This is how a normal discussion is supposed to be held. I appreciate that you didn’t come at me with insults, like some other users did, totally unasked for.
Secondly, I think we shouldn’t comment on other things besides Firefox and Chromium in this gHacks article, simply because the article is about Firefox. Discussing OS’s, VPN’s, and other unrelated things to the article is literally off-topic.
Madaidan’s article is part of the Whonix page above only because of his Firefox and Chromium security comparison. If you, or someone else, would like to discuss other parts of his article, it would be the best if you directly reach out to him, this gHacks article is definitely not the correct place to discuss that.
Lastly, I believe enough has been said here. Everyone is free to use whatever software they like, for one or another reason, but please don’t turn gHacks into Reddit, where saying anything bad about certain software leads to hidden comments and directed harassment. We have to thank Martin and his team for not censoring people who aren’t afraid to bring up concerns regarding different subjects.
I for one have decided that listening to respected privacy and security experts such as Daniel Micay is a lot more meaningful than listening to random people around the web. Everyone has to do their own choice.
That’s all from me. I don’t feel like dragging this any further since I raised my concerns, backed up by the views of security and privacy experts, so I don’t think I can add anything more to the discussion.
Thanks to everyone who kept the discussion civilized, that’s how all discussions should be.
Take care!
@Anonymous
The thing is when you’re going to take someone’s views(read madainsecurities guy for some folks) on a particular product then its better to check what he has to say on other things, that’s how one finds out if he’s legit or not. And I mentioned VPN, Linux above to tell those who regularly mention that guy and his article links time and time again that if even that guy probably said one thing correct(highly unlikely), then the same guy is saying some downright stupid thing about other software and when I read those I was like – What a load of waffles.
There are some resident shills who blindly support one browser and try to insult others who use something else. One example – They mention a link which say Firefox collect more telemetry than Brave or any other browser but the issue is, that so called test was not done fairly. Brave Browser does not build its own engine, it doesn’t need telemetry(even though there is a switch to turn that off in Brave, IDK why there is a need for that). Firefox is building its own engine(and its telemetry is not evil, Leanplum maybe and so better turn that off) and one can turn most of things off through main settings only which includes Telemetry, Normandy, Safebrowsing, DRM and many more (visible in about:config modified preferences). Take this current article for example, JS in pdf can be turned off(though I never opened pdf through Firefox viewer) and yet some shenanigans are at it again.
A guy who doesn’t know anything about Browser fingerprinting regularly trashes those who do take measures against it and user.js file without taking positives into account. That guy said in previous articles that Brave revealing device name in user agent is good and I’m thinking couple of months back Brave did hide the device model in one update only to reveal it again in next update, but if Brave did hide again, then for him the whole theory of Browser fingerprinting would change overnight.
And finally for Daniel Micay and whonix, me or any Firefox user are not saying that Firefox is invincible but there has to be some real world issues to buy what he is saying like for anything in web world or mortal world. Firefox has gone third party audit and for normal folks like me its more than enough. If there would be a vulnerability exploited in wild, I would give it another thought. Until then its more than secure enough for a regular guy like me.
@Yash
My gosh, you are lying through your teeth again rather shamelessly. Thanks in advance for wasting my time again.
> There are some resident shills who blindly support one browser and try to insult others who use something else.
False claim. I am fighting blatant misinformation coming from people like you.
> One example – They mention a link which say Firefox collect more telemetry than Brave or any other browser but the issue is, that so called test was not done fairly.
It was done fairly, stop lying through your teeth. Firefox does in fact collect more data than Brave, including stuff like the default browser (even if it isn’t Firefox), or whether or not people have telemetry enabled (yes, they actually collect telemetry from people who have disabled telemetry). This has nothing to do with engine development, stop lying.
> it doesn’t need telemetry(even though there is a switch to turn that off in Brave, IDK why there is a need for that).
Brave Software modifies Chromium in ways that are not insignificant, ignorant.
> and one can turn most of things off through main settings only which includes Telemetry, Normandy, Safebrowsing, DRM and many more (visible in about:config modified preferences).
Telemetry should be opt-in, Normandy shouldn’t even exist, SafeBrowsing should be proxied when enabled, DRM should be opt-in. Fixed that for you.
> A guy who doesn’t know anything about Browser fingerprinting regularly trashes those who do take measures against it and user.js file without taking positives into account.
Says the guy who is most misguided when it comes to fingerprinting. Dude, you are literally * [Editor: removed] enough to hide your timezone (a weak identifier), now being among a very very small crowd of people doing that (turning the lack of information into a strong identifier – “no result found” is a result just like any other result as far as scripts are concerned), forgetting that it can still be uncovered via your IP address even if the browser hides it. STUPID.
You hide your device model (again, only a very small crowd of people does that because there is no reason to), forgetting that it can still be found out via your amount of RAM, hardware concurrency, screen resolution etc. STUPID.
You think enabling RFP fixes anything despite only a small crowd of people doing that, which consequently does nothing against advanced scripts. Even for naive scripts, Firefox would still leak WebGL which is the most checked item after Canvas. Disabling WebGL puts you in a very very small crowd once again, which solves nothing and is therefore STUPID.
You, pal, are a danger(!) to anyone seeking privacy, because your ideas are 100% counterproductive. That you accuse others of “not knowing anything” after your mental striptease is just the cherry on the cake.
> That guy said in previous articles that Brave revealing device name in user agent is good and I’m thinking couple of months back Brave did hide the device model in one update only to reveal it again in next update, but if Brave did hide again, then for him the whole theory of Browser fingerprinting would change overnight.
* [Editor: removed]The device model is a weak identifier to begin with if you own a popular model (should be self-explanatory, right?). Hiding it does nothing if other true values still leak. My logic doesn’t change overnight; it doesn’t have to, contrary to yours, it is not unsound or incoherent.
> Firefox has gone third party audit and for normal folks like me its more than enough. If there would be a vulnerability exploited in wild, I would give it another thought. Until then its more than secure enough for a regular guy like me.
Ignorant, what you said doesn’t mean that a) there are no security issues of FF and that b) FF would be more secure than Chromium. All you say is “It’s good enough for me!”, which is just your totally irrelevant opinion! This doesn’t prove anything, this doesn’t refute anything, this is totally inconsequential.
People like you should treat people like the Whonix devs or Daniel Micay as gods and their word as gospel, you are so clueless, you can basically only learn something from them. This is my 100% uncensored opinion, no bashing intended. It’s just a reality.
PS: You think it’s an ingenious rhetoric trick to not mention the names of the people you are harassing and bashing, so that they need to come out and confirm that they are anything you are claiming they are, by virtue of them responding to your false accusations, right? That’s not an ingenious rhetoric trick *[Editor: removed]
@Iron Heart
Your ignorance level is too high bro, and your default browser fingerprinting guide are a joke. As I said in previous articles, you haven’t got a clue of what browser fingerprinting really is. Your so called two rules – 1. RFP results in miserable browsing experience – For your kind information, RFP hides(read – hide or generalise) ‘REAL’ timezone so if someone’a using a VPN its original timezone wouldn’t show up. It hides amount of ram, hardware concurrency, spoofs screen resolution and other things you mention but of course since you haven’t tried RFP in real life you are manipulating FACTS and are telling lies. The best thing about RFP is(RFP users know this already unlike you) browsing experience remains the same but since you haven’t used a certain RFP thing, can’t share a screenshot to prove your false point, you are welcome to rant about it.
2. Default setting are best – Again I guess you would be happy to reveal that you’re using a certain Samsung Galaxy Note 20 Ultra device with 8 GB ram with Eastern timezone or a certain HP Pavillion laptop with central timezone to just browse a damn website. Brave only randomizes WebGL(which in previous articles you admitted its a security issue when I said it first) and Audio(again laughable as I have two different smartphones and both have same audio fingerprint in Firefox despite one being years old, in other words Firefox generalise Audio fingerprint even without RFP but of course you don’t know that as you haven’t used Firefox) and reveals amount of ram, screen resolution, hardware concurrency and many more REAL values you mentioned above which by the way can’t be hidden in Brave – no options for that. Brave fingerprint protection are same as – like me trying to hide my name from someone I just gave my bank account details which already knows everything about me as he has my bank account details. But of course stupid folks like you would be okay with that.
Even in above comment you said stupid and laughable things like device identifier is a weak value, timezone hiding is pointless and its a weak identifier, telemetry has nothing to do with developing browser engine. Good job a certain guy who hasn’t written a single line of coding by yourself. Brave is not developing browser engine and yet can’t hide Canvas, even forks like Bromite(FYI a chromium fork but miles better than Brave), Iceraven, Fennec, Biscuit are better than Brave which by the way should be a criteria for comparing forks with forks. If you’re going to compare Brave(a fork) to a complete browser like Firefox, you have to take things into account that in Firefox, telemetry is easily disabled, but you even lied in that part in your comment above. But then mighty ignorant Iron Heart is gonna ignore all this because he knows everything in his little bubble.
I have nothing against Daniel Micay but what he is saying has to have real world applications, and so far me or any other Firefox user in the whole world hasn’t suffered any issues mentioned by him. And Daniel Micay isn’t the only security expert in the world mind. And the madainwhatever guy is a joke(read my comments above).
Now finally to all those gHacks readers who are going to read this comment now and in the future(assuming people are gonna scroll down to comments), Its better for you folks to enable RFP(resist fingerprinting) and check the results yourself in various Browser fingerprinting test, if you do that you would find RFP is very good tool and even default Firefox fingerprinting protections are better than Brave(a fork which by the way is not developing its browser engine and is not even a good choice in forks world), and you would also find whether RFP hides real values or not which Iron Heart falsely claims it doesn’t(see his comment above). Spoiler alert – If you’re going with the Iron Heart way, in other words not checking anything and just ranting then that’s fine, but if you do a real world test you would find that Iron Heart and regular Brave shills produce a hell lot of guff with no credibility, and they are just jealous because Brave isn’t even best fork of Chromium although better than Chrome, Opera but then that’s not saying much, as Google is a trillion dollar company with Ads broking and user tracking as main business and the less said about Opera the better.
> WebGL which is the most checked item after Canvas
Seriously, where do you get all this shit? Do you just make it up on the fly?
Prove that statement. I bet you can’t. And it’s wrong. Just think about it and use your brain for once. Where would user agent sniffing come in at: surely every single script would check that? But WTF does ranking these have to do with anything? A metric is a metric. You protect them all. If you took the top 500 fingerprinting scripts, you would find they all have a dozen things in common: there is no fucking top two items.
You rank metrics on their possible entropy: which is clearly why Brave pissed around with audio with very low entropy, and ignored fonts (and other metrics) with very high entropy
> Even for naive scripts, Firefox would still leak WebGL
You’re like a broken record screaming the sky is falling. A naive script is fooled by randomness. Firefox’s RFP includes randomness. You know this (after having been told a dozen times) and even finally admitted that RFP alone is effective at defeating naive fingerprinting (after screaming hundreds of times that it isn’t). This just proves that you are being totally disingenuous, manipulative, and trolling
Iron Heart logic “Even for naive scripts, Brave would still leak [insert list of 100 things here]. Holy shit, that Brave is fucking crap. It’s a turd burger masquerading as an advertising company funded by venture capitalists”
Brave is *only* interested in defeating naive scripts. With advanced scripts, Brave is completely fucked. Where are they at, let’s see
– canvas protection can be totally bypassed and this was the first thing they did: doesn’t inspire any confidence
– audio can be totally bypassed: Brave *knew* this and still choose to implement it, because they only care about naive scripts
– some randomness is a joke: stripping out leading, trailing and double spaces in userAgent, how amateur and pathetic
– nothing has been done for screen, device pixel ratio, fonts, timezone, languages, and dozens and dozens and dozens more
How about before you go screaming BS about Firefox’s RFP, which at a bare minimum (naive scripts) is the equivalent of Brave, you look at your own fucking beloved shilled product
At least Firefox implement protections that aren’t bypassed, and understand what the fuck is going on. Like the proper solution for audio which is already known.
@”Anonymous” * [Editor: removed]
> Where would user agent sniffing come in at: surely every single script would check that?
Even non-fingerprinting scripts check that, which is why I didn’t explicitly include it. Every fucking website checks that. Use your brain, yes, how about you set an example here for once.
> A metric is a metric.
Yes, some with more entropy, some with less, which is why some get checked more often, and some less. Some scripts also check many to get a more complete picture. Is this the fingerprinting ABC, or?
> You protect them all.
Nobody does that, complete bullshit.
> which is clearly why Brave pissed around with audio with very low entropy, and ignored fonts (and other metrics) with very high entropy
Oh, so you are again pissing on fingerprinting defenses that are still in their infancy? Great, I am sure FF got it right in its first year, hell, its first month. Oh wait…
> A naive script is fooled by randomness. Firefox’s RFP includes randomness. You know this (after having been told a dozen times) and even finally admitted that RFP alone is effective at defeating naive fingerprinting (after screaming hundreds of times that it isn’t).
You are claiming that FRP also beats advanced scripts which is bollocks, only Tor does that because there is a crowd to hide in. Those piss poor user.js scripts provide you with no crowd. Yet you are still claiming that those scripts do anything, which is somewhat between dumb and dangerous. General use browsers can likely only beat naive scripts. I don’t dispute that. Web compatibility is a great limiting factor here.
Firefox doesn’t beat naive scripts as long as WebGL leaks, by the way. Prove me wrong, naive scripts DO check for that. Providing no value for WebGL fixes exactly nothing.
> With advanced scripts, Brave is completely fucked.
So is Firefox. RFP can’t defeat advanced scripts. Firefox likely can’t even defeat naive scripts because of the WebGL leak.
> canvas protection can be totally bypassed and this was the first thing they did: doesn’t inspire any confidence
Will be fixed, you expect Brave to achieve perfection in like, the first month, while giving Firefox a pass for WebGL leaks after years and years of development. LOL, you utter hypocrite.
> audio can be totally bypassed: Brave *knew* this and still choose to implement it, because they only care about naive scripts
They also care about web compatibility concerns, which is why they implemented it in the way they’ve implemented it. Brave is a general use browser. (So is Firefox, it too fails against advanced scripts, but hey, ignorance is bliss…)
> some randomness is a joke: stripping out leading, trailing and double spaces in userAgent, how amateur and pathetic
I know that you don’t care about breakage, but you know, web compatibility concerns are a thing for a general use browser that is not Tor.
> nothing has been done for screen, device pixel ratio, fonts, timezone, languages, and dozens and dozens and dozens more
Perfection in their first year, giving Firefox a pass for certain leaks even after years of development etc. Same old story all over again. Why do you think that Brave Software calls the FP defenses a work in progress?
> which at a bare minimum (naive scripts) is the equivalent of Brave, you look at your own fucking beloved shilled product
The problem is not me, the problem is you, because you claim that RFP can defeat advanced scripts (it can’t), berate Brave for doing the sensible thing which is to try and beat naive scripts, while not giving two shits about web compatibility (which is the reason advanced scripts aren’t tackled by Brave). It’s always the same old, tiring story with you.
> At least Firefox implement protections that aren’t bypassed, and understand what the fuck is going on.
Fix the WebGL and extension ID leak and then we’ll talk.
> Like the proper solution for audio which is already known.
Web compat is a thing, you know. Firefox’s solutions, copied from Tor, have no place in a general use browsers. The alu hat community enabling RFP because some idiotic user.js tells them to are easy prey for advanced scripts (“advanced” here apparently meaning scripts that check for WebGL, lol).
Listen, nothing you say will convince me or any other sane person to sacrifice web compatibility, performance, overall security by switching to the dying product Firefox. You see, FF’s RFP won’t beat advanced scripts, there is no crowd to hide in. That’s what Tor is for. For naive scripts alone (most of which are likely already blocked by any adblocker), I won’t switch to a browser that is inferior in so many areas. I also don’t buy into your bullshit scare claims that the things Brave doesn’t cover YET will never be tackled. What you say is not convincing in the slightest. Just move on and attend to other matters, I am sure the dwindling Firefox bubble will gladly be listening to you.
> Even non-fingerprinting scripts check that, which is why I didn’t explicitly include it
Iron Heart logic: “Even non-fingerprinting scripts check canvas, which is why I didn’t explicitly include it” – we’re not talking about every website. We are explicitly talking about fingerprinting
The holes and inconsistencies in your narratives and diatribe make Trump look like a saint
> Yes, some with more entropy, some with less, which is why
Exactly WTF I said “You rank metrics on their possible entropy” – are you ever go to add anything worthwhile to the conversation?
> Nobody does that, complete bullshit
So sorry, let me make the assumption more clear “You try and protect them all”
> They also care about web compatibility concerns
This was your answer to audio. Audio randomizing doesn’t affect compat. If you knew anything about fingerprinting you would know this. They also added it even though they knew it leaks via equivalency. It’s a joke marketing gimmick. It sucks in all the suckers who suck up to their marketing garbage. It’s pure threatre, like the seven day lifespan for only one type of cookie.
For the record, RFP does care about compat: you are confusing absolute implementation: security of the real value (RFP) with “only wanting to fool naive scripts” (Brave). And your claims of compat issues are greatly over-exaggerated
> You are claiming that FRP also beats advanced scripts
Where did I say that? What I have said in other articles is that in Firefox RFP and other changes can probably defeat some advanced scripts, as not all scripts are the same.
> Firefox doesn’t beat naive scripts as long as WebGL leaks, by the way. Prove me wrong, naive scripts DO check for that. Providing no value for WebGL fixes exactly nothing.
So RFP on it’s own beats naive scripts which you have stated and agreed is the case, because the randomness of canvas fools it. But if the same naive script also includes WebGL then somehow it isn’t still fooled by the canvas value anymore?
Wow, just wow. A poison pill stops working when you add more metrics. Go back to school. In fact, just stop talking, you’re embarrassing yourself even further.
> sob story over Brave implementation and lacking metric coverage
Cry me a river. Brave has the benefit of a decade of solutions and research to look at. Canvas poisoning has been around for many years. When Brave first announced it’s “farbling”, you proudly claimed Brave was the best fingerprinting protection in the universe. And then you proceeded to shit on RFP and shit on Tor Browser, and argue about the most basic of things
You’re confusing my FACTS about the current state of Brave’s Shields, as an attack on them. It’s not, it’s pointing out your hypocrisy
> Wow, just wow. A poison pill stops working when you add more metrics. Go back to school. In fact, just stop talking, you’re embarrassing yourself even further.
to clarify
– “A poison pill stops working when you add more metrics” is what Iron Heart is suggesting, which is clearly wrong
– Iron Heart: “Firefox doesn’t beat naive scripts as long as WebGL leaks”
Ladies and gentlemen, please ignore Iron Heart. He isn’t an expert and can’t even get the most rudimentary basics correct
And since some of you might not believe Daniel’s claims without a direct Reddit reference, here I will provide yet another proof:
https://twitter.com/DanielMicay/status/1263895065224712192
So yes, keep disrespecting privacy and security experts because a loud group of people on Reddit is doing that every time someone mentions something negative about Mozilla Firefox.
@owl
“People believe what they want to believe, and deny what they don’t want to believe.”
I agree with you but that doesn’t mean we shouldn’t raise valid concerns regarding subjects. Unlike on Reddit, here Martin and his team allow us to discuss things freely, without a certain group of people downvoting and hiding comments only because they don’t want people to be aware of valid concerns regarding their favorite web browser.
“We need to be tolerant and pay attention to different opinions. (Do not use propaganda or incite hatred, though.)”
People must learn to respect each other’s opinion without jumping to insults when they read something they don’t like. I don’t understand the propaganda part in your sentence, though. The Whonix page consists of links to sources that prove the worrying state of Firefox’s security. I believe it’s propaganda claiming there are no issues when there apparently are, something happening on a few Reddit subreddits, and something some gHacks users are attempting here. I sincerely hope you don’t believe respected privacy and security experts are spreading propaganda against Firefox.
“There is no such thing as “absolute safetyâ€, even with Chromium.
And of course, Firefox.”
I agree, but once again – people shouldn’t insult each other when valid concerns are raised. Users deserve to be made aware of worrying but valid concerns regarding both Chromium-based browsers and Firefox.
Once again, keep discussions civilized, insulting each other changes absolutely nothing.
@Anonymous,
You seem to be mistaken, I was not commenting on you alone.
My comment was a revelation to “those who are replying” and to “subscribers who are not replying”.
It is important to extinguish “fires” in their early stages. If it flares up, jumps off and spreads, it will inevitably be “out of control”. I am not “denying” anyone, but this exchange is “outrageous and unseemly”. Most of the subscribers will turn away, and their valuable opinions will be buried.
For subscribers,
This site is a community called “gHacks Tech News” (a place where we exchange technology and other useful information with each other through different means but with the same goal).
If you want to abuse someone or bare dislike for something, please do so on “Twitter”.
Commenters on gHacks should be given to advise “cautions” or “alternatives”.
@”*Alert”
If gHacks had a voting system, the fanboy mob would be allowed free reins here. Downvotes are not given for factual disagreement, they often merely reflect childish dislike even if the information given is factually correct.
I have debunked the “Firefox dev” you cite already:
https://www.ghacks.net/2021/04/28/mozilla-is-working-on-firefox-background-updates-on-windows/#comment-4493631
There is an explicit admission of a problem in that post and some irrelevant mumbo jumbo about Rust that is unrelated to any security-relevant component of the browser, as those are in fact not written in Rust.
I am a long term commenter here knowing the weaknesses and strengths of browsers by now, not some random * [Editor: removed, please stay polite, even if it is hard]
> I have debunked the “Firefox dev†you cite already:
No you haven’t. You quoting yourself as THE source, where you don’t put anything in context and are biased (because you hate Firefox), how pathetic. You’re even just making things up, like what code parts are more susceptible than others and what has been converted to Rust. You haven’t even got a clue what parts of Firefox use Rust or the actual effect it has had on security
YOU are the random dude on the internet everyone needs to ignore, not the Firefox dev (and not that mad adam guy, his points are (likely mostly) valid when taken in context: not as some general “ooh look, fuck, bad” that you make it out to be).
People .. vote: do you trust the Firefox dev who works in this area, or Iron Heart with a proven record of disinformation and bias?
+1 for the Firefox dev
-100 for Iron Heart, again
+1 firefox developer
I think I speak for the entire internet …
+1 Firefox developers and context
-1 for cherry picking and out of context posted by trolls
> I think I speak for the entire internet …
No, you speak for people who fail to understand that…
– The FF dev admitted the necessity of Project Fission, admitting to an issue madaidan pointed out.
– The mumbo jumbo talk of the FF developer about Rust is inconsequential until the most attacked components of FF are transferred to Rust.
As I said:
– ignorance
– inability to read what the FF dev said
I am sure most of you guys have not even read the post of the FF dev. Most of you are just here to troll in the usual fanboyish manner.
add another +1 for the firefox dev
+5 firefox dev
> +1 firefox developer
+1 ignorance
+1 inability to read what the FF dev said
> +5 firefox dev
+2 ignorance
+2 inability to read what the FF dev said
@RichardAlert
You are the one who is pathetic because you are woefully unable to refute madaidan. The Firefox dev you cite admitted the need of Project Fission and talked a bit about Rust, without mentioning that major parts of FF are still written in memory-unsafe languages. I am also not quoting myself as a source, you fool, I am quoting from here:
“Firefox does have some parts written in Rust, a memory safe language, but the majority of the browser is still written in memory unsafe languages and the parts that are memory safe do not include important attack surfaces so this isn’t anything substantial and Chromium is working on switching to memory safe languages too.”
source: https://madaidans-insecurities.github.io/firefox-chromium.html
> +1 for the Firefox dev
> -100 for Iron Heart, again
If you say so… Your ability to cope with reality is seemingly at -100 at this point.
@anonymous.
the majority of the web is geared towards chromium and firefox browsers so your comment is nonsense,you provide just one link/opinion and expect it to be embraced as fact.
Ladies and gentlemen Iron Heart is back. See @owl above has said it correctly that it is not Firefox issue. Its the web standard. But in Firefox you can turn it off. See my comment below, it would have been better if this option was visible in main menu but its not the end of the world. Plus if security is topmost priority then by the way Brave leaks Canvas – just saying for some security conscious folks.
@Yash
The above comment wasn’t written by me, I never ever write under any other pseudonym here than “Iron Heart”, my dear.
Your assumption that I am the only one who is aware of Firefox’s security issues is highly idiotic, as is your claim that a “Canvas leak” is a security issue (as in: can be exploited to gain partial or full control of the host OS).
Also, as far as leaks are concerned, Firefox is leaking unique extension IDs as well as WebGL, how is that any better? You, my friend, are exactly what gHacks needs right now, yet another clueless Firefox fanboy.
@Iron Heart
Thanks for clearing that up, its just that whonix link was mentioned up above and so I thought it was you.
As for UniqueIDs, its not the case with Firefox but I’m not going to write essay about the things which are not present in Firefox.
Atleast now I know that even though your views about Firefox are different, you post comment only under IRON HEART avatar.
@”I smell something”
> All you have ever done is point at bugzilla, which does not say HOW. You had to be told that it involved web accessible resources.
Read the Bugzilla links for once. They explain it there perfectly. No need to rinse and repeat.
> You had to be told that some extensions protect it like uBO.
Do you think it matters to me that As for UniqueIDs, its not the case with Firefox (…)
It is. Stop spreading misinformation. Read the Bugzilla links, the Mozilla devs confirm the leak there.
“Stop spreading misinformation. Read the Bugzilla links, the Mozilla devs confirm the leak there.”
I did not say it wasn’t leak proof. I asked you to show everyone that you know what you are talking about and to back up your claim that this is trivial.
Please tell us how this is so trivial in Firefox and how you would do it? We all know it’s extremely trivial in chromium, even if the extension does nothing to a website, it only needs to be enabled.
If you can’t tell us how, then you must be lying
> Firefox is leaking unique extension IDs
– IF the extension has web accessible resources
– IF it isn’t protecting them like uBO
– IF you can craft an attack to catch it, because you can’t use the internal UUID
Not ideal, but certainly not worse than leaking even protected UUIDs in chrome – EVERY SINGLE FUCKING ONE of them, via timing attacks, via persistent IDs you cannot change
https://github.com/uBlockOrigin/uBlock-issues/issues/1572
More Iron Heart out of context crap from our resident bullshitter in chief
You still haven’t answered many readers’ requests on your bold statement that it is trivially easier to get Firefox extension IDs. Please feel free to answer now.
@”fecal_spotter”
You are basically confirming that there is a leak unless extensions specifically shield themselves against it, is that correct?
Also, Chromium’s extension ID leak only reveals non-unique extension IDs, because that is what they are in Chromium – non-unique. Firefox has unique IDs in every install.
> You still haven’t answered many readers’ requests on your bold statement that it is trivially easier to get Firefox extension IDs. Please feel free to answer now.
I have, and often. People like you just refuse to take notice for their own private reasons. Here we go again:
https://bugzilla.mozilla.org/show_bug.cgi?id=1405971
https://bugzilla.mozilla.org/show_bug.cgi?id=1372288
You didn’t even discuss the WebGL leak that can’t be stopped short of disabling WebGL (which makes you stick out even more, not less). I am countering the evergreen “Brave is the only browsers having leaks yadda yadda” complete bullshit here and you know that perfectly well, hence the fanboy reaction.
> I have, and often
No you haven’t. All you have ever done is point at bugzilla, which does not say HOW. You had to be told that it involved web accessible resources. You had to be told that some extensions protect it like uBO.
Please inform of HOW you can trivially get any Firefox extension’s UUID if the extension has web-accessible resources, as you keep claiming.
@ “Iron Heart”
no one ever said that the issue doesn’t exist. the issue is you not presenting all the facts
firefox extensions with web accessible resources
pros: unknown ids, protected from side channel attacks because they are unknown, no “universal” method to just check them, and can be protected by extensions like uBO’s token
cons: IF leaked, you are unique. thank you for being the iron boy wonder by informing everyone that the UUID is unique: that’s what the UUID stands for. Being unique solved all the shit chromium has
chromium extensions with web accessible resources
pros: WHEN leaked the id is not unique
cons: the id is universal, so it is trivial to check. even those protected like with a token, still leak. 100% of the extensions leak their ID. It doesn’t take many extensions to make your fingerprint exponentially worse, if not unique
There. CONTEXT. Was that hard?
Guess what I would rather have: My trusted vetted few Firefox extensions and NO leaks at all. How’s that, my NO leaks vs your ALL leaks.
> You didn’t even discuss the WebGL leak
webgl? what the fuck does have to do with anything I said? You brought it up because you feel the need to fling shit and make noise. Can you try and be an adult and stick to the BS topics one at a time that you keep bringing up. You have already shown your knowledge on fingerprinting is disgustingly bad
A tiny snippet of your ignorance you have shown over dozens of article comments and hundreds of posts of ranting
– https://www.ghacks.net/2021/04/19/here-is-what-is-new-and-changed-in-firefox-88-0/#comment-4492187
– https://www.ghacks.net/2021/04/19/here-is-what-is-new-and-changed-in-firefox-88-0/#comment-4492335
– https://www.ghacks.net/2021/04/19/here-is-what-is-new-and-changed-in-firefox-88-0/#comment-4492488
– https://www.ghacks.net/2021/04/19/here-is-what-is-new-and-changed-in-firefox-88-0/#comment-4492537
– https://www.ghacks.net/2021/04/19/here-is-what-is-new-and-changed-in-firefox-88-0/#comment-4492542
Highjacking the thread to ask a serious question – do disabled extensions in Firefox leak IDs and contribute to fingerprinting?
@”fecal spotter”
> unknown ids
…until they leak, making users unique. :D
> protected from side channel attacks because they are unknown,
They leak via trivial fetch requests.
> no “universal†method to just check them,
They leak in a trivial manner.
> and can be protected by extensions like uBO’s token
Strong emphasis on “can” here. The percentage of extensions actually doing that is ridiculously low. Plus, uBlock Origin still leaks via specific behavioral patterns.
> WHEN leaked the id is not unique
Yep. Which is why I don’t worry about leaks for popular extensions.
> it is trivial to check.
Firefox also leaks trivially.
> 100% of the extensions leak their ID.
That rate isn’t much lower for FF. Almost no extension defends against leak. You always mention uBlock Origin, kudos, you found one that takes its precautions. What about the rest, though? 90%++++ of all FF extensions leak their IDs.
> It doesn’t take many extensions to make your fingerprint exponentially worse, if not unique
That’s also true for FF, except FF is already unique with one extension that leaks, even if it’s a popular one.
> There. CONTEXT. Was that hard?
Hard to read that kind of stupidity, yes.
> and NO leaks at all.
Don’t think so.
> How’s that, my NO leaks vs your ALL leaks.
Leaks are only problematic when the leaked values are unique, which is not the case with Chromium, especially if only popular extensions are installed.
> webgl? what the fuck does have to do with anything I said?
Discuss Firefox’s WebGL leak and the braindead mitigations you propose (disabling WebGL), mitigations that do not in fact reduce uniqueness in real life. Why not, it is 100% related to the “leak” topic. Discuss it.
> A tiny snippet of your ignorance you have shown over dozens of article comments and hundreds of posts of ranting
* [Editor: removed]
* [Editor: removed] I see you are back to your standard “quote and dissect every single sentence” and repeating the same comments over and over again, which just shows you have nothing to add of any value and can’t hold an adult conversation. Your ignorance is truly world beating: here is just ONE example from that FloC-load of runny shit above
> Leaks are only problematic when the leaked values are unique
Wrong, and just yet another example of your total ignorance on how fingerprinting and entropy work.
A leaked ID confirms an exact binary answer. Combined leaked IDs raise entropy almost exponentially. Fingerprinting does not work in isolation with just one metric.
Chromium extensions leak, the IDs being KNOWN is a weakness and allows ALL of them, 100%, to leak. There is nothing the extension developer can do about it.
—
You still haven’t shown that YOU know HOW to TRIVIALLY expose all the Firefox extensions – because you can’t, because you are just making it up drawing conclusions with lack of knowledge of how it actually works
This is your MO: point at something valid that someone says, twist the fuck out of it, claim some sort of pat on the back and victory, double down, attack people
You have gained another -5000 in trustworthyness (which at this is immaterial, you already have no credibility)
@”fecal spotter”
> can’t hold an adult conversation.
Do I need to have an “adult discussion” with a “fecal spotter” to begin with? You already disqualified yourself for that before you typed your first post.
> Wrong, and just yet another example of your total ignorance on how fingerprinting and entropy work.
You are the ignorant. Take uBlock Origin as an example, this extension has millions of users, if its known ID in Chromium leaks, this is hardly a strong identifier, since the ID is not unique pr user. The exact same leak (of another extension, because as you know, uBlock Origin belongs to the Combined leaked IDs raise entropy almost exponentially.
Combined? Did I ever say you are supposed to pile up extensions in your browser? That would already be problematic because of the behavioral fingerprint which also exists, you know.
Don’t break your legs while moving those goalposts.
> Chromium extensions leak, the IDs being KNOWN is a weakness and allows ALL of them, 100%, to leak.
That they are “known” is totally irrelevant for popular extensions with millions of users. Nice strawman argument right there. Anyway, the unique ID leaking in Firefox is problematic without anyone having to know what extension exactly hides behind the ID. The ID alone is the identifier, that is comparable to giving every single Firefox user a unique number.
> You still haven’t shown that YOU know HOW to TRIVIALLY expose all the Firefox extensions – because you can’t, because you are just making it up drawing conclusions with lack of knowledge of how it actually works
Read the Bugzilla links, it is being discussed in depth there. I won’t cite 10 pages worth of discussion here. That’s why I link to it in the first place.
> You have gained another -5000 in trustworthyness (which at this is immaterial, you already have no credibility)
* [Editor: removed]
> That they are “known†is totally irrelevant for popular extensions with millions of users
Still failing to grasp basic English comprehension and simple mathematics I see
Behavioral effects are not precise fingerprinting. Example adblocking. Those effects could be caused by the browser’s builtin blocking, by any of dozens if not hundreds of blocking extensions, or by something at a network level like PiHole. All this shows is a binary yes/no to a vague metric of “is the user blocking some stuff”. Some tests might be able to pinpoint more specific block items, and there is entropy to gained here. A leaked extension ID is precise, in fact it is EXACT
Comparing generic behavioral detection to an actual extension ID shows you do not know what the fuck you are talking about
Most users do not use extensions. Extension use / distribution is heavily against the user. With uBO, a user might only represent 2% or 3% of those users. AMO shows approx 5mn uBO users for all 220mn Firefox users as an example. Now add in more entropy from specific uBO lists (entries which may or may not exist in other blockers), and the user may be even more identifiable. So in Brave the user has gone from 1 in 25mn to maybe 1 in 500k, out of 4 billion users worldwide, probably significantly worse.
If the user happened to have another extension that uses web-accessible resources, like some sort of dark reader, and it was tested for: then you rapidly start falling into a very select group. Dark Reader is at an educated guess, about 0.3% of Firefox users. Between the two there will probably be some overlap, but the group will be extremely small. This user might now be 1 in 20k users, depends on the overlap and popularity of the extensions
Knowing the exact extensions involved vs binary yes/no detection (with false positives) of some vague metric, isn’t even in the same ballpark.
The more precision and more precise points, the higher the chance you become unique. Brave fingerprinting protections are already extremely weak and severely lacking: canvas and audio can be fully bypassed. Add this to the flaw of persisting 100% ALWAYS LEAKING extension IDs for all users, and you should be able to grasp what I am saying
Meanwhile, in Firefox, this always known, persistent, always leaking ID does not exist. However, the solution of random unique UUIDs per profile then created a POTENTIAL worse outcome: IF they leak, then they are unique. No one has ever disputed this. But you can’t just go check for them like you can in chromium – e.g. the timing side-channel will not work if you don’t know the UUID to start with.
What’s even worse, is that the extension doesn’t even have to be applied on a website to be detected with timing in chromium: e.g. whitelist a site in uBO, it is still detectable – test here: https://arxenix.github.io/chrome-ublock-detection/. So that applies to all extensions: whitelisting sites will not hide it. As long as the extension is enabled, it leaks. This is not the case in Firefox.
So tell us how you propose to TRIVIALLY, 100% reliably, detect Firefox extensions with web accessible resources. You can’t. You keep claiming you can. I’ve read the bugzillas, and unlike you, I understand them. Please show you understand them, now is your chance.
@fecal_spotter * [Editor: removed]
– Behavioral fingerprinting is rather precise, your claims are refuted by scientific evidence, such as this study: https://www.cs.uic.edu/~skarami/files/carnus/carnus-ndss20.pdf
– You picked adblockers, because they all have similar behavior… Wow, nice strawman. What about more uniquely behaving extensions interacting with websites? Care to talk about those? Your argument dies down before it even started for extensions that behave more uniquely than adblockers do. And yes, you fool, I can tell apart an adblocker from Pi-Hole because the adblocker will apply cosmetic filtering (yes, I can detect that), while Pi-Hole won’t. This should already disqualify you, but hey, let’s look further.
– uBlock Origin protects against the known leaks, so not sure why you are citing this. There are better examples that do leak.
– You are moving the goalposts yet again, by implying that custom lists will be added to uBO, which is not necessary in most cases. It’s just an assumption of yours. Most users of uBO will be using the default lists.
– More goalpost moving by implying that the user runs even more extensions. How likely is that, considering that users with extensions are already in the minority? How many use more than an adblocker and maybe a password manager? Laughable.
– The group of users of some user.js file is also small and identifiable, but I never see you talking about that. Why?
– FF’s fingerprinting protection leaks WebGL and there is a potential unique extension leak, you can ride Brave’s Canvas leak to death, doesn’t mean FF does any better. Brave’s Canvas leak will be fixed, not so sure about the FF leaks.
– I certainly won’t re-post an entire Bugzilla conversation here for no apparent reason, I have already told you that. The developers accurately describe the issue there, that is more than enough for anyone who cares to look. I don’t do exercise therapy for you.
> now is your chance.
* [Editor: removed]
> I certainly won’t re-post an entire Bugzilla conversation here for no apparent reason
No one asked you to. If it is so trivial, as you keep claiming, you can describe it a single sentence. But you can’t. You lack the knowledge and just keep overstating anything you can twist by making extravagant claims in your holy crusade to burn Mozilla.
I believe you have now been asked by a dozen people, over twenty times to explain HOW YOU would do it. Clearly you don’t know
—
Oh, look, pointing at another paper and claiming to be an expert. Can you even understand what the paper says? I do, I’ve read it before, in depth.
There is nothing new about any of this (except they proto-typed an automation for it)
– WARs – this is what we are discussing
– anything that touches the DOM can be detected
– anything that injects JavaScript can be detected
– anything that fetches additional resources can be detected
Would you like me to tell you EVEN MORE ways I can detect extensions? Do I really need to list them all for you, or do we stick to the topic of WARs
Do you realize your arguments and the paper-in-general also hold for non-Firefox browsers, and hence this adds nothing to the conversation about web accessible resource leaks?
Just another attempt to deflect and twist the narrative
—
What part of “Some tests might be able to pinpoint more specific block items, and there is entropy to gained here” (talking about adblockers behavior detected in the DOM) went completely over your head?
Where was it said that all extensions can’t be ID’ed via other means?
What’s wrong with using adblockers as one example of two, when adblockers are by far the most prevalent extension type installed by users, and we have been discussing uBO?
Please tell the readers how can YOU would detect “user set” cosmetic filters, which are going to be site specific, in order to help your fingerprinting? You can’t, as it is not stable and can’t be used to link traffic. Showing your ignorance again.
What about all the users who just use default lists and nothing else: set and forget. How do you detect them as different from the others? Like the majority of what rules are applied to websites. Oh wait, that’s right, you test lots of specific rules, sucking up extraordinary amounts of time: and come up with nothing.
How do you keep up to date with your universal script used by thousands of sites which don’t want it because of performance issues, when the blocklists and rules used keep changing?
How can you detect the difference between a blocked item that is blocked by the browser, blocked by uBO and blocked by PiHole? You can’t.
Did you know that detecting this all is slow and performant heavy and scripts need to be fast and reliable to be widely used. Did you know there are far easier ways to fingerprint 95% of the population. Did you know that scripts factor in cost, ease, performance and payoff?
Also, YOU can’t detect anything, you lack the knowledge.
I don’t like my web browser to be bloated.
PDF documents are displayed in “SumatraPDF” via Sandboxie-Plus.
And I use “LibreOffice Writer” to edit PDFs.
Of course, I have disabled the “PDF” feature in my web browser.
Mozilla would make a can of worms, then make a lid for it, where the sensible person would just not make the can of worms in the first place.
@beemeup5,
The specification to “enable JavaScript execution in PDF documents” in browsers is a requirement of many users.
It is possible in Chromium, and there have been constant requests from Firefox users to enable it.
This is not limited to Firefox; it is a standard specification for today’s web browsers.
In short, it is important that there is an option to “disable” it.
People could always save the PDF and open it with their PDF program. Why should it be the browser’s job to handle PDF? Why not handle Word and Excel formats too while they’re at it, they’re equally common.They took out FTP (instead of just disabling it by default) and told users to use their external FTP program, claiming it was for “security reasons” but then they turn around and add javascript capabilities to PDF and have it enabled by default to boot. This is a contradiction in design philosophy. If they’re okay with adding functionality at the risk of security in one instance, why are other instances too problematic?
Chromium is wrong to have enabled it too so “because Chromium did it” is not a good excuse. Why not add the extra PDF functions as an extension? Isn’t the whole point of extensions to extend the browser? The modular approach to browser functionality is clearly better but Mozilla lost sense over a decade ago.
Well said beemeup5.
I don’t use Firefox’s native PDF viewer, preferring SumatraPDF to handle it all :
pref(“pdfjs.disabled”, true); // Default=false
about:preferences / General / Applications / Portable Document Format (PDF) = Use SumatraPDF (default)
To allow PDFs to be viewed immediately rather than downloaded (when the site decides to trigger a “save as”) I use the ‘No PDF Download’ Firefox extension, originally built to handle PDFs handled by Firefox, which works as well with PDFs handled by whatever application (SumatraPDF in my case as mentioned above).
Nevertheless, should I switch back to Firefox’s native PDF that I’ve set as mentioned in the article :
pref(“pdfjs.enableScripting”, false); // Default=true
The main reason I had switched to SumatraPDF to handle PDFs on the Web is that some PDFs wouldn’t render correctly if browser.display.use_document_fonts=0. I dislike in particular serif fonts and many sites use them. Nevertheless some pages do require browser.display.use_document_fonts=1 which is why I use another Firefox extension called ‘Enforce Browser Fonts’ which allows a per-site authorization for document fonts.
A bit lengthy, sorry, but I thought explaining why and how I avoid Firefox’s native PDF viewer could be worth it.
I happen to be convinced that my options are the best but I’m not in this case. Nothing is definitive, open minds authorize themselves to modification, right? :=)
JS can still force you you to view PDFs in-browser
Thanks emilia. I hope the about:config option will disable JS in embedded PDFs too in FF, or else it’ll be time to move on to something better.
Jack, that example was using canvas, but a polyfill doesn’t have to do that
https://en.wikipedia.org/wiki/Polyfill_(programming)
I wrote “eternal loop” which makes me smile now that I read my comment.
T’was a spatiotemporal mismatch : eternity is to time what infinity is to space. In other words the old corny joke (*really* corny, which you don’t hear anymore, fortunately) : “- Have you got the time, please? – I’ve got the time if you’ve got the place” isn’t as stupid as it may sound, whatver corny it is!
@emilia the hun , I haven’t encountered a PDF bypassing my settings to get opened in Firefox (which would lead to an eternal loop given pdfjs.disabled is set to true). Not only are PDFs opened with SumatraPDF (which is a user’s authorized choice, no tweak) but moreover always opened with SumatraPDF (even when the site forces a “save as”) thanks to the ‘No PDF Download’ Firefox extension.
Tom, the pref “pdfjs.disabled” merely controls the options and default behavior. JS can, If. It. Wants. To., still open PDFs in-browser
@emilia the hun
Can you link to any such page where JS can override the user’s explicit browser preferences?
Jack, sites can use any of hundreds of viewers and many sites do embed PDFs this way
– https://usefulangle.com/post/20/pdfjs-tutorial-1-preview-pdf-during-upload-wih-next-prev-buttons
Great choice, Tom. I’ve been using Sumatra myself for years; helping with bug reports and testing for both it and Artifex’s Mupdf on which it relies. I also highly recommend Tracker Software’s PDF-Xchange Editor (replaces the older Viewer only product), which you can use in both portable and installed modes.
@Jack, Tracker Software’s ‘PDF-Xchange Editor’ is certainly a great application but it’s heavy (300+ MB) compared to SumatraPDF (version 3.2 x64 is <9MB).
Of course all depends of one's needs. No advanced features with SumatraPDF, which doesn't bother me except for one thing : the typewriter. I remember having had to fill out too small boxes to be handwritten on a printed PDF, so I had to convert the PDF to an image (BMP to keep it optimal), then edit the image with nice characters that would fill the boxed neatly, then print the image and/or convert it back to a PDF. Ouf! cumbersome! So a PDF's viewer without the typewriter feature is the only utility I really miss with SumatraPDF. Clear enough : PDFs here are mainly viewed.
Yes @Tom, PDF-Xchange Editor is certainly heavier (although I do use the non-OCR portable version which is a 50MB ZIP), but of course it’s also far more feature rich and v. handy on occasion (esp. when one needs stuff Sumatra will never have, trust me). Sumatra’s still my primary PDF viewer however.
Totally unnecessary “feature” (I mean JS in PDF as such, not the disabling). There’s no need to add this kind of bloat to web browsers, especially when it introduces new security risks..
@shoot,
> Totally unnecessary “feature†(I mean JS in PDF as such, not the disabling). There’s no need to add this kind of bloat to web browsers, especially when it introduces new security risks..
I personally “agree”, but the existence of Vivaldi (which continues to add niche features and bloat) symbolizes that there are no few users who want to “do everything, in a web browser”.
In fact, no few users are repulsed by Firefox’s “Proton” project (which removes niche features).
Mozilla (Firefox) cannot ignore the existence of these users.
The problem with removing features is that it’s always a pain to give up something you’ve already gotten used to, more so when the reasons given for removal are BS, as is often the case with Mozilla. But you really don’t need to add too much to the core browser if you have good extensibility, so all kinds of niche features can be available to those who want them. Of course Firefox still isn’t on par with the extensibility that was removed when legacy add-on support was dropped. Actually this PDF/JS functionality could be done transparently to the user via an official Mozilla extension, there’s no need to sneak it in without most people even knowing it’s there – until they suddenly see a security advisory about it, lol.
This should be something that should be put on the Privacy and Security of the Preferences page, not hidden in about:config.
Scripting in PDF should also be off by default, and prompt the user if they want to enable JS on the PDF.
Yes, I agree.
Hear, Hear jobbautista9. Ridiculous that this is buried within about:config and ON by default. (I prefer to use third party viewer and download, view later since forever..)
thanks a lot for this information. checked in my FF and Nightly and both were set to True, now changed both to False to make PDF’s safe again.
I thought FF was promoting a safe browser but making this change without widespread warnings, is not correct imho. FF had better set the default to False and allowed a change for those who want to use javascript, be it temperary or permanent.
The important question is: Does Firefox 88 have any mechanic to protect users from malicious javascipt code in PDF?
FYI
“Firefox’s internal PDF viewer (based on pdf.js) converts the PDF to HTML. There is a possibility that a PDF could be crafted to trigger some kind of vulnerability in that conversion code, but it would have to be a different kind of attack from ones affecting native applications like Adobe Reader/Acrobat or Apple Preview. Also, you may feel more comfortable knowing that if the PDF contains JavaScript for an Adobe application or any other PDFviewer, that is disregarded by the pdf.js viewer.”
Info about the PDF viewer:
https://github.com/mozilla/pdf.js/blob/master/README.md
No one is forced to use the built-in PDF viewer
https://support.mozilla.org/en-US/kb/view-pdf-files-firefox-or-choose-another-viewer#w_disable-the-built-in-pdf-viewer-and-use-another-viewer
in nuce
No browser in the world can protect you from your own stupidity … let alone breastfeed you, because a browser has no tits!
Grow up! The best precaution is still to check from which source you download your PDF’s.
“Also, you may feel more comfortable knowing that if the PDF contains JavaScript for an Adobe application or any other PDFviewer, that is disregarded by the pdf.js viewer.â€
How clever of you Emil to omit where you copied this text from. For the information of all it is taken from the answer to “Does Firefox’s internal pdf reader protect against malware?” (https://support.mozilla.org/en-US/questions/1285774), given by some guy named jscher2000 MORE THAN 1 YEAR AGO on 4/30/20, obviously when pdf.js in FF didn’t even support JavaScript in PDFs. Since it does so now, and that too by default with no prior warning to the user, quite obviously THIS ANSWER IS NO LONGER VALID. A fact that you naturally are desperate to hide.
Funny how much and just how often you fanboys have to lie in order to try and protect the reputation of your favorite browser and cover for the latest bit of idiocy from Mozilla. In one thing you are correct – truly nothing can protect you from your own stupidity.
@IH-BS
>>>”How clever of you Emil to omit where you copied this text from.”
First, the text is clearly marked as a quotation by citation marks.
Second, I’m not writing a thesis here, so a precise citation of sources is not mandatory.
>>>”MORE THAN 1 YEAR AGO on 4/30/20, obviously when pdf.js in FF didn’t even support JavaScript in PDFs”
Until Firefox 87 the
pdfjs.enableScriptingconfig option was set tofalseyou could set it totrue… the default since Firefox 88>>> THIS ANSWER IS NO LONGER VALID.
Read the Quote again:
JavaScript for Acrobat APIs is not only a bit different compared to Browser support for JavaScript APIs
https://developer.mozilla.org/de/docs/Mozilla/Add-ons/WebExtensions/Browser_support_for_JavaScript_APIs
but also can handle a bunch of other things.
https://opensource.adobe.com/dc-acrobat-sdk-docs/
That’s what malicious code is primarily aimed at!
For further details please contact your preferred malware developer.
Conclusion: The answer is still valid … do your homework first à la improving your reading skills, and second do a proper research before spreading your * [Editor:removed] again.
@Editor in persona
Quote: “before spreading your * [Editor:removed] again.”
Thanks for this glorius demonstration of your perfect skills to weed out contributions that are irrelevant, obscene, illegal, or insulting with regards to useful or informative contributions.
But …
… since you feel compelled to censor in my last sentence
the four letters “IH-BS” (read = Iron Heart – Bullshit), it would be kindly appropriate to consequently remove the same four letters in the salutation “@IH-BS”.
Thanks
Like Lemegeton said, you guys keep ranting about the “haters” while turning a blind eye to all of Firefox’s bugs and user-hostile defaults like this JS one (“oh, but we have about:config” you say, which hardly any average user will touch because they know nothing of how the defaults affect them – just what Mozilla wants). Not to mention the very deliberate gimping of features for no good reason whatsoever. Case in point – just see how hostile they are towards users who complain on Bugzilla about how the recent View Image context menu change has broken their workflow and muscle memory and how the new version is demonstrably worse than the old one. Apparently Mozilla’s awesome UI team has decreed that Firefox should match Chrome in its UI stupidity. Honestly, hard to believe such a bunch of retarded morons is in charge there. This browser is clearly developed by a gaggle of idiot kids and it’s become a spectator sport now to see it hurtling towards its doom i.e. miniscule user base and thus complete irrelevance. Sure, you 5 guys left can be happy then down in your well celebrating your “win” with your Chrome-lookalike but insecure browser, giggling and trading about:config secrets with each other, while the rest of the world shakes its head, laughs and moves on.
@MozKillsFFFromWithin,
I’ve been a subscriber to gHacks for many years, but your “HN” seeing for the first time.
“MozKillsFFFromWithin” is a handle name that seems appropriate for you.
In short, you’ve declared yourself a “troll”.
Trolls don’t belong in the “gHacks Tech News” community, which is a respectful, not hostile, place where people can exchange skills and information for a shared purpose, even if they have different values and means.
Go to Twitter!
So anyone who says anything against your favorite browser, even if it’s a 100% verifiable fact, is automatically a troll, right owl? Just stick your head in the sand and poke it out only when you want to troll those speaking the truth to power here. Pathetic behavior as expected from the FF mafia. Why don’t YOU scurry off to Twitter, oh great keyboard warrior? Lol.
P.S. Nobody gives a rat’s a$$ how long you’ve been a so-called ‘subscriber’ here. So what, you think it gives you some sort of privilege over the rest? Clearly in all these years you haven’t learnt that all commenters are treated equally here by Martin & co.
@Emil Brausewetter,
ðŸ‘
Absolutely right,
I agree with your view in its entirety.
Furthermore, repeat that quote:
> The best precaution is still to check from which source you download your PDF’s.
@Emil Brausewetter
The thing is most people are so obsessed with Firefox(FF haters) that if a thing changes in Firefox its like end of the world for them. That was the same with Firefox background update article and literally with every Firefox article. If Firefox changes a thing – Its bad, if Firefox doesn’t change a thing – Its bad. They forget that you can easily disable things, change things in Firefox to an extent that same Firefox version can be configured to behave like Chrome’s install and forget it approach, or very same version can be configured to Iceweasel configuration.But those folks just want to rant about Firefox I guess.
The Tor Browser recommend against opening any downloaded file when connected to internet and so that’s what I prefer to first download files only from safe or trusted places and then open them on third party viewer.
@Yash
Blaming the “haters” for all firefox’s problems only makes firefox situation worse. And users will only leave the browser more.
Don’t worry: at some point there will be no haters left, and at that point you will suddenly realize that the browser has almost no users left: it will be like some Chopera with about 1% marketshare. There will be no one left to “hate” the browser.
And pray that Mozilla will have enough money to continue development. Because the amount of money they have for development directly depends on how much they earn through affiliate programs with search engines, etc. And this is directly related to the number of browser users.
Mozilla is already firing developers. And it’s not from the good life.
P.S. The market share of Firefox is dropping, while, for example, the market shares of Vivaldi and Brave are growing. Suddenly (sarcasm), it is possible to make changes in a browser that will please browser’s users.
And when the news about the changes in FF looks like this: removed this, disabled this, removed the ability to configure this, and only the collection of telemetry becomes more, then there will be “haters” of such changes.
When the news comes that, for example, the new version of Firefox has disabled by default all telemetry and it can not be enabled remotely – almost everyone in the comments will rejoice. But you can’t wait for such news, can you? That’s how we found out who “generates the haters”.
Presumably they’ve coded their JS interpreter and compiler with security in mind and sufficient safeguards. Of course bugs can always be present and exploited by bad actors who discover them, so since I’ve got along fine without this feature so far, I’ve disabled this already.