Encrypt your DNS traffic with Simple DNSCrypt for Windows
Simple DNSCrypt is a free open source program for Microsoft's Windows operating system to configure dnscrypt-proxy on Windows-based PCs and devices.
DNS Crypt is a technology that encrypts DNS look ups so that third-parties cannot spy on those. While some programs or services, VPN Services for instance, protect your look-ups automatically, most DNS traffic is not encrypted.
OpenDNS introduced DNSCrypt support back in 2012 but DNSCrypt was pioneered by the OpenBSD operating system years before that. It uses encryption to protect against man-in-the-middle attacks.
SimpleDNSCrypt
Simple DNSCrypt is an easy to use program for Windows that brings the functionality to Microsoft's operating system. It is not the first program to do so, DNSCrypt Windows Service Manager was released in 2014, but it is a feature-rich solution but it is no longer in active development.
Simple DNSCrypt utilizes DNSCrypt Proxy which is also available for Windows and other operating systems.
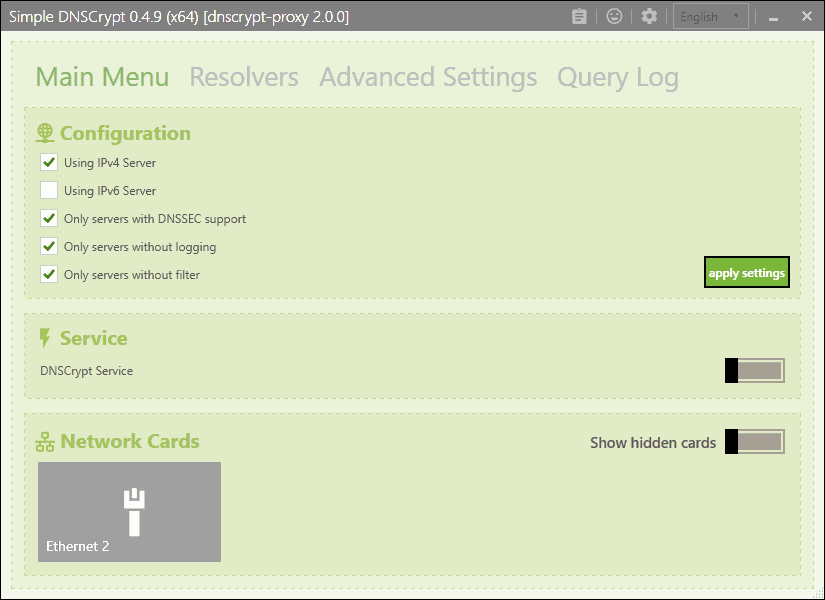
The user interface is divided into several tabs.
- Main Menu -- lists configuration options, e.g. use of servers and available network cards.
- Resolvers -- lists the available DNS Resolvers and offers configuration options.
- Advanced Settings -- additional settings that change core functionality.
- Query Log -- A log that is disabled by default.
A click on the settings icon gives you options to add additional tabs to the program interface which you may use to blacklist and whitelist domains, and check the domain block log.
Activate the DNSCrypt Service after you have configured the options to your liking to get started with the application. Once you have done so, select the network cards that you want the service to run on.
This is the bare-minimum configuration to encrypt your DNS traffic. It is recommended that you go through the settings before you enable the server to make sure all is set up correctly.
Simple DNSCrypt lists IPv4 servers by default only and blocks IPv6-related queries. You enable IPv6 servers under main menu and unblock IPv6-related queries under Advanced Settings.
The program retries resolvers that support DNSSEC and don't log or filter traffic by default. You can uncheck these options as well if you want but it is recommended that you don't unless you run into issues.
Simple DNSCrypt runs in automatic mode by default. The service picks the fastest resolver from the list of available servers and uses it. You can switch that off under resolvers by selecting one or multiple resolvers from the list. This may take a bit of testing to make sure performance is fine.
The advanced settings give you more control over the service's functionality. You can disable DNS caching there for instance. Simply put, if caching is enabled, Simple DNSCrypt tries to find the information in the cache before resolvers are used to look-up the information.
There is also an option to Force TCP, and to uninstall the Windows service.
Uninstallation worked without issues on several test systems.
Closing Words
Simple DNSCrypt is an easy to use program for Windows to protect DNS queries against man-in-the-middle attacks. One downside of the project is that you don't have control over the resolvers. There is no option, at least none is in the UI, to add custom resolvers. This means, basically, that you have to trust at least one of the servers used.
Now You: Do you encrypt your DNS traffic?
Related articles
- Encryption and Strong Passwords
- How to encrypt Windows 10 hard drives using BitLocker
- How to Speed Up a slow loading website
- ProtonMail Bridge: encrypted email for Outlook, Thunderbird, and other email clients
- Quad9 DNS promises better privacy and security
DNSCrypt is a bullshit!
It does not work!
It is ineffective and it is an illusion!
If you still believe it protects you,
Then go and test it! and you will see it!
Have fun!
The current version requires .NET Framework 4.6.1 which I’m reluctant to install.
I’m also a bit concerned about the use of Comodo certificates since the 2011 fiasco and again last month: https://bravatek.com/comodo-certificate-hack-it-gets-worse/
For the time being I’ll stick with DNS Watch which although not encrypted does at least support DNSSEC: https://dns.watch/index
You should try this with Technitium DNS and say goodbye to third party DNS services forever.
I am using SImple DNSCrypt with Cloudflare’s new 1.1.1.1 as the only DNS Server selected .
A few questions:
1) How can I test that the queries are actually encrypted?
2) How can I get new version 2.0.9 of dnscrypt-proxy into the Simple DNSCrypt app?
3) Is there a user manual anywhere?
Thanks.
why people are so mean. appreciate the jobs of other, we use it for free.
if you don’t trust, make your own…
Looking at the query log, nothing was happening after installation (X64 2.01). I did an ipconfig/all and noticed that a new loopback entry – 127.0.0.1 had been added. I did an nslookup against the new loopback, and yep the log populated with my query. I opened my adapter properties, and moved the new loopback entry to the top of the dns list in IP4 settings. Now its fine.
Am I the only one who had this issue, or did I do something wrong?
Simple DNSCrypt added 127.0.0.1 and 127.0.0.2 automatically for me. However that was before the 2.0 update so maybe a bug?
Just how much space would it take to set up a local DNS server?
I’ve been using this for over a year now and I recommend it.
However, it’s not just a set and forget (thus to use on a relatives’ PC). Specially in this new version, the auto mode sometimes picks unstable servers (although the fastest at that moment), plus 0.4.9 doesn’t seem to be working correctly with ipV6 so I had to roll back to 0.4.8 and disable auto update.
All in all, it’s a very well developed little program that adds a little extra and helps curb some censorship your ISP might have applied.
Will this conflict with the Private Internet Access client, or aid in preventing DNS leakage?
Private Internet Access comes with DNS anti-leak protection. DNS Crypt does not protect against leaks, but against man-in-the-middle attacks.
You can start your own server which costs 5 bucks a month, a description is given in the DNSCrypt-Proxyv2 Wiki. Thi is not mentioned in the article but it would maybe help to get more servers running, this is especially a problem in Asian regions.
So I am currently trying this and looking at the servers available. There appear to be about 30 of them. Most of them seem to relate to Aldus which I have never heard of. The only two that I actually know of is SecureDns (Comodo) and Openic (which before googleing I had never heard of). So I have set it to use those two.
So what DNS resolvers does everyone else here use?
I use DNS Servers of universities. I don’t trust big companies like Comodo or IBM.
“Do you encrypt your DNS traffic?” Yes, I encrypt. But only in web browser, Yandex Browser – built-in DNS Crypt and set of servers to your choice ex. AdGuard DNS, Babylon, D0wn Resolver, DNScrypt servers, Soltysiak, etc.
I use Quad9 DNS and a few months ago I saw something that implied a dnscrypt solution with Quad9DNS might be considered. I cannot find that reference now, but perhaps in the future this will come to pass. Maybe Quad9 will address this in their March 21 webinar. See
https://register.gotowebinar.com/rt/4953969873864823043
if interested.
I got a prompt reply from Quad9 support that says “We are in the process of evaluating dnscrypt for inclusion, along with several other client-to-recursor encryption and authentication methods. We will hopefully include it soon along with announcements of other privacy-enhancing protocols as we are able to ensure performance and stability of the service.”
“We do currently support DNS-over-TLS on the standard port 853, using dns.quad9.net as the auth name.”
A few years ago there was a report that said that OpenDNS couldn’t be trusted. Exactly why they couldn’t be trusted i don’t remember, but i remember that i and several other users left OpenDNS in a protest.
OpenDNS was purchased by Cisco a while back. You may have heard some rumblings when this happened.
Maybe because Open DNS is now owned by Cisco and they track what you do. Take it away from your IP Provider and give it to Cisco, instead. Nice.
https://www.cisco.com/c/en/us/about/legal/privacy-full.html
This should have no bearing on DNSCrypt itself, it’s just an encryption method. The owners of the servers and service transporting your data are who matter. AdGuard has a DNSCrypt service that can be used, for example.
Will my ISP’s resolver support encrypted DNS queries, or do I need to select specific outside resolvers like OpenDNS?
Briefly tried this once and did not get it to work fast enough. I use dns watch now and change dns at will with quicksetdns, is this bad ?
I probably should try this.. except I don’t like MSI installers and I don’t trust COMODO at all.
“File Signing: The MSI package and the SimpleDnsCrypt.exe are signed via a COMODO RSA Code Signing CA.”
It’s opensource, allright. You’re more than welcome to inspect the codes and compile from the source yourself.
…constantly removing the truth on Wikipedia and everywhere else.
Dude, I don’t give a flying fuck about comodo. I don’t use any comodo products either. I was just giving you a suggestion that you can inspect and compile the source yourself if you have trust issue with it.
What I tried to explain to you is when I don’t trust something I do not touch it. Dude.
You don’t trust it just because the pre-compiled binary is signed by Comodo? How narrow minded is that? Did you even inspect the source?
If you don’t touch something you don’t trust, then what do you use to surf the internet?
Entrust my network to strangers like using VPN, proxies, or using clouds etc, is already for me a risk I would not take. A fortiori to someone trusting COMODO.
Sorry if my question wasn’t clear.
How do you surf the internet then? You do know that almost every browser comes with Comodo SSL certificates included right? If so then how could you use something you don’t trust? That’s like a complete opposite from what you have said.
“Comodo Trust Toolbar is malicious browser plugin. Users usually have no choice on installing this toolbar because it installs itself secretly. Comodo Trust Toolbar may hide its presence, but it appears as a security helper in most cases. ComodoTrust Toolbar presents itself as helpful addition to web browser. It offers inspecting security of websites; it also provides online search and comfortable web navigation. The real functions of ComodoTrustToolbar are far from the latter description. It displays tons of advertisements on every single visited website. It redirects web browser to malicious or fraudulent websites; it may cooperate with vendors of corrupt security tools. Comodo Trust Toolbar is also capable of downloading and installing other computer parasites.” I remember a Comodo’s toolbar redirecting to malicious sites effectively, particularly malicious porn sites. How by the hell someone can trust a guy that should be in jail, I wonder?
I do not trust rich, especially when they are open source.
Maybe simple DNSCrypt, but rich it seems.
As proof I still use Pale Moon as browser, hopefully the certificate was too expensive, otherwise I should have had to find another browser: https://forum.palemoon.org/viewtopic.php?f=1&t=17859 [“IV is only available as a rare exception and requires notarized documents of a nature I cannot provide, as I found out when attempting to get a certificate from Comodo.”]. The Racket continue as I can read..
Paranoids using “HTTPS Everywhere” (just as example) should also tie down their wife to the radiator. Sorry if my answer wasn’t clear.
I don’t care about certificates or https or equivalent bullshit, I don’t trust internet for any secure transactions. Comodo SSL certificates… so risible!
I would not touch something already inspected by COMODO which spreaded malware in the past.
Running since (almost) always DNSCrypt-proxy here. Version 2 is a major update and applies to ‘Simple DNSCrypt’ as well, of course.
Be it used with a front-end such as ‘SimpleDNSCrypt’ or not, DNSCrypt is a fantastic tool, and not only for it’s first function which is to encrypt DNS requests but also for the ease of having it include IP and domain blacklists. With V2 I’ve abandoned the HOSTS file used as a blocker : far too cumbersome when i.e. you’ll have dozens of entries for a site such as 30[x].br.net and that with DNSCrypt’s blacklist function you can have them included as:
*.302br.net
*.303br.net
*.304br.net
*.305br.net
*.306br.net
*.307br.net
Fast, written in Go, and it’s truly a go, go, go, go man go application :=)
Did I say I love it?!