Check Linux for Spectre or Meltdown vulnerability
Devices running Linux are affected by Spectre and Meltdown vulnerabilities as much as their Windows counterparts.
Development teams work on updated kernels for the various distributions, and users need to update browsers and other software to protect data against potential attacks.
We talked about identifying whether your Windows PC or web browser is vulnerable already. A recently published script does the same for Linux systems. You may use it to check whether your Linux distribution is vulnerable.
Spectre and Meltdown detection for Linux
You run the script if you want to know whether a Linux distribution is vulnerable to Spectre variant 1 and 2, or Meltdown attacks.
Check it out on the official GitHub project page. You find the source there so that you may analyze it before you run it on a system.
You may run the script without parameters to check the running kernel or use options to check a kernel that is not used.
A simple shell script to tell if your Linux installation is vulnerable against the 3 "speculative execution" CVEs that were made public early 2018.
Without options, it'll inspect you currently running kernel. You can also specify a kernel image on the command line, if you'd like to inspect a kernel you're not running.
Here is how it works:
- Open Terminal on the Linux system you want to check.
- Type cd /tmp/
- Type wget https://raw.githubusercontent.com/speed47/spectre-meltdown-checker/master/spectre-meltdown-checker.sh. This downloads the script from the GitHub server.
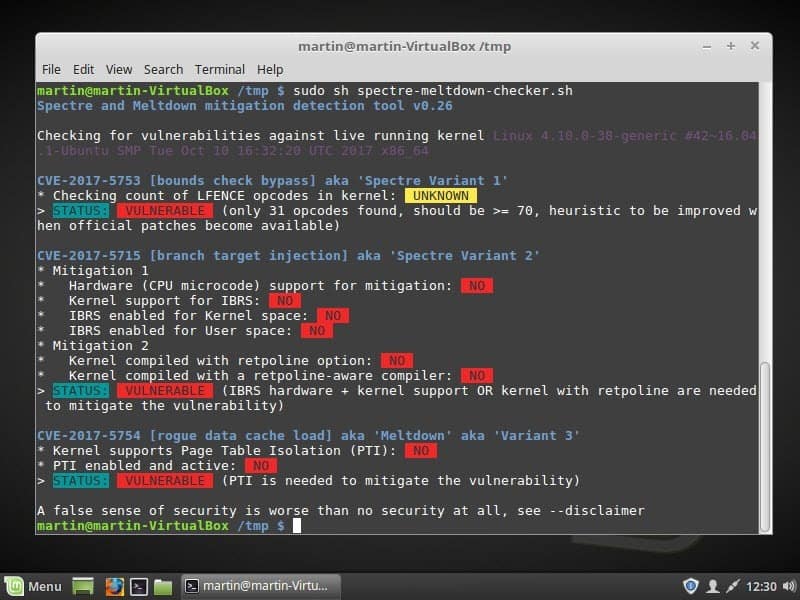
- Type sudo sh spectre-meltdown-checker.sh. This runs the script with elevated privileges.
- Type the password.
The script checks each variant individually and lists its finding. If you get "status: vulnerable," the system is vulnerable to the variant. The checks for Spectre variant 2 and Meltdown reveal additional information.
A system that is vulnerable needs a kernel update to protect against potential attacks exploiting these vulnerabilities.
How you get the kernel update depends on the Linux distribution. You select Menu > Administration > Update Manager in Linux Mint to check for available updates. The kernel is not available yet, however.
Once you run the update, rerun the script to verify that the system is no longer vulnerable.
The Spectre & Meltdown Checker supports the scanning of offline kernels as well. Use the parameter −−kernel vmlinux_file for that and if available −−config kernel_config and −−map kernel_map_file as well
I am not sure I trust this – I happen to have access to an Itanium system, and the script tags is as vulnerable, in spite of the fact that the IA64 architecture is not vulnerable to these attacks.
To patch variant 3(Page Table Isolation), is a 64 bit OS required? I run 32 bit Linux Mint and after running the script, it shows “vulnerable” for this variant.
Hi Martin,
I have run your script on my linux box. From the various status results, I got one status as vulnerable.
STATUS: VULNERABLE (IBRS hardware + kernel support OR kernel with retpoline are needed to mitigate the vulnerability
Can I check using some steps, that the above result is not false-positive ???
Thanks.
Its likely going to take months to patch variant 2 vulnerability.
Variant 1 is patched with CPU microcode updates i think.
Variant 3 is patched in Linux kernel.
I suggest you check which kernel you run and then with your distro to find out which kernel includes the patches.
Interesting – there is a script available from Intel called “intel_sa00086.py” which claims to check for kernel patch vulnerabilities. On my Dell XPS 13, running Mint 18.3 Cinnamon with kernel 4.10.0-42, it claims I’m patched and safe. Your script indicates “Vulnerable” with each of your tests. This machine has the latest Dell BIOS update supposedly addressing this issue, which I downloaded and applied two days ago. I’m inclined to think Intel’s test to be a bit optimistic. It is my hope that both Dell (and other vendors) and Intel are aware of these inconsistencies.
Thanks for your efforts!
Nice find, Martin. I’m getting “not vulnerable” on the first question (CPU microcode) on Variant 1, and also on Variant 3. I believe the Variant 3 stuff was patched when I updated to kernel 4.13 a couple of days ago. The CPU microcode thing just got patched moments ago when I installed the new Intel microcode.
Still a long way to go before all those red flags go away…. If I’ve understood correctly, we’re talking months, not days, right?
Martin, when you asked about your new layout/site, I said it wasn’t my thing. That was personal taste, not something functional. This is: I keep the articles I like by printing them to pdf. This no longer works – the layout is screwed up and most parts not printed. Any chance for a return of printability or save link to pdf?
We are working on it!
Thanks!!
Ashampoo Spectre Meltdown CPU Checker 1.0.0 for Windows
https://www.ashampoo.com/en/usd/media/1304
Thanks Martin. :)
Have you got CONFIG_PAGE_TABLE_ISOLATION ticked or set to Y?
It’s under Kernel Hacking > Security Options and listed as
“Remove the kernel mapping in user mode (PAGE_TABLE_ISOLATION)” about 1/3 of the way down on those options.
So long as that’s enabled, variant 3 (Meltdown) will be mitigated.
The other variants are gonna require cpu microcode and a kernel (and the rest) :(recompilation with an updated GCC/LLVM compiler (retpoline). Gotta wait for those new compiler patches to trickle down and then rebuild rebuild rebuild.
In related news, intel has released new microcode (8/1/2018) but seemingly only for architectures of the last 5 years with later ones having to wait til the end of the month, even removing 2 cpu signature versions for some reason…my ivybridge 0x000309a9 is also waiting :/
http://metadata.ftp-master.debian.org/changelogs/non-free/i/intel-microcode/intel-microcode_3.20180108.1_changelog
With my current seetings Kernel 4.15.0rv7 is still vulnerable
https://s17.postimg.org/t622qhmin/S_M.png
Awesome. :)
You can also download spectre-meltdown-checker.sh to your Downloads folder, right click anywhere in Downloads folder, open terminal and then sudo sh spectre-meltdown-checker.sh
Thank you for this useful article! :- )