TrueCrypt alternative VeraCrypt 1.12 ships with interesting PIM feature
VeraCrypt is one of the few programs that came into existence after development of True Crypt was abandoned.
Even though True Crypt's security audit did not uncover any backdoors in the program -- see results of the first and second phase of the audit -- left at least some users puzzled and confused as to whether they should continue using True Crypt to secure their data or switch to a different program offering similar functionality.
We have reviewed VeraCrypt twice in the past, first when it was released and then later on again to find out how it had improved in the meantime.
A new version of VeraCrypt was released two days ago and with it comes a new interesting feature the developers call Personal Iterations Multiplier (PIM).
It is an optional component that could improve the security of data protected by VeraCrypt significantly, so, lets take a closer look at that.
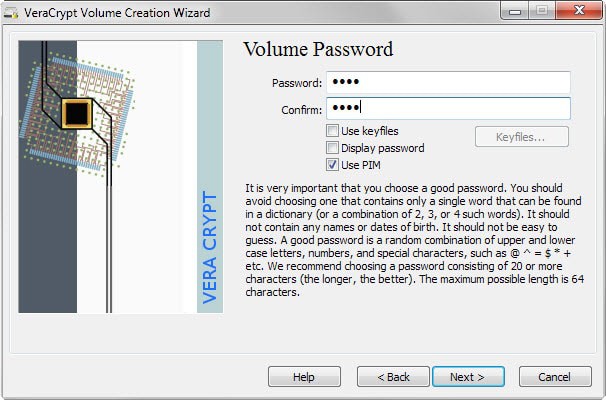
When you go through the volume creation process, either to create an encrypted container or encrypt a partition, you will eventually come to the stage where you need to enter the password that protects it. This password is being used to mount the container or partition whenever the need arises using VeraCrypt. There you find the new "use PIM" option that is disabled by default.
When you check it, you are taken to a new page after setting the password which prompts you to enter a volume PIM. You may enter any number or use 0 to use the default instead (which is 485). The only restriction is that the PIM cannot be lower than 485 if the password has less than 20 characters.
A lower PIM value may speed up the mounting process but reduce security if the password is not strong.
The mounting process of the encrypted container or partition changes slightly if you set a PIM. You need to type the PIM in addition to that for the mounting to be successful.
Check the "use PIM" box. Once you do you will notice that it changes to a field that you can enter the PIM you set during creation.
The container or partition is mounted only if password and PIM are correct.
This looks like two-factor authentication and is to a degree with the exception that the PIM is set during creation just like the password and not generated on demand.
Additional information about the new release are available on the project website.
Closing Words
Adding a volume PIM increases the security of the encrypted container or partition significantly, especially so against brute force attacks.
Version 1.13 of VeraCrypt has been published. Have a look at https://veracrypt.codeplex.com.
What is the advantage with “[password]” plus [pim] (for example the number 490) compared to a longer password e.g. “[password]490”?
I’m assuming that an attacker would need to bruteforce each field together.. and the variations available of [infinite password longer than 20] + [3-digit PIM] just means brute force gets even harder to achieve.. not to mention the need to enter vs 2 fields at once vs just the password field?
“The only restriction is that the PIM cannot be lower than 485 is the password has less than 20 characters.”
I think you meant “… IF the password has…”
This is good to see. Although I think the explanation is a little opaque, anything to encourage folks to use long passwords is a good thing.
Still, I would recommend that folks encrypt their entire computer before using this feature. There FAR more security-affecting attacks to consider ahead of guessing every password. Brute force attacks are employed primarily by dedicated, well-funded attackers. In other words, you’re far more likely to have your laptop stolen and have a thief look around for what’s handy than someone with a thousand computers to try every possible combination of characters.