Check if Windows is affected by the Freak Attack vulnerability
Freak Attack is the name of a new SSL/TLS vulnerability that came to light on March 3, 2015. The vulnerability can be exploited by hackers to weaken the encryption used between clients and servers when HTTPs connections are used.
Affected are servers, according to a site that is tracking the issue 9.5% of Alexa's top 1 million domain names but also web browsers such as Chrome, Safari and Internet Explorer.
Browser's are not necessarily vulnerable on all systems they support. Chrome is for instance vulnerable on Android and Mac OS X but not on Windows.
Firefox appears to be the only browser not affected by the vulnerability at all on all systems it supports.
Since Internet Explorer is affected by the vulnerability on Windows, it is important to check whether your PC is vulnerable and do something about it if that is the case.
The easiest way to do that is to use the Freak Client Test Tool which tests for the vulnerability and reports back if your browser is vulnerable or not.
Side Tip: If you run a server that supports SSL/TLS, use this tool to check for the vulnerability. If your server is vulnerable, use Mozilla's recommended configuration to disable support for vulnerable cipher suites.
On Windows, only Internet Explorer appears to be vulnerable while all other browsers appear to be protected against exploits.
Microsoft released a security advisory yesterday that includes a workaround for some Windows systems. Some? The workaround requires access to the Group Policy Editor which is only available on Professional, Ultimate and Enterprise versions of Windows.
There is no workaround for systems that don't support the Group Policy Editor.
- Tap on the Windows-key and type gpedit.msc and hit enter.
- Use the left sidebar to navigate to Local Computer Policy > Computer Configuration > Administrative Templates > Network > SSL Configuration Settings.
- Double-click on SSL Cipher Suite Order.
- Switch the policy to enabled.
- Copy the Cipher suite order from Microsoft's advisory page to the clipboard, and paste it into the SSL Cipher Suites form.
- Click ok and restart the PC.
This protects Internet Explorer from the vulnerability. Windows won't connect to systems that use a cipher not supported in the list that you have added in the Group Policy Editor.
To undo the change at a later point in time, set the policy to disabled.
To mitigate the issue on Windows, use a browser that is not Internet Explorer for the meantime or apply the workaround mentioned above if possible. (via Deskmodder)
Now You: Is your system vulnerable?
Update: Firefox users who get reports that their system is vulnerable may want to check if add-ons or security software is interfering with the process. Ghacks reader Torro noticed that Avast's Web Shield was the cause for vulnerability reports in his version of Firefox.
I consider there to be a number of factors you can do to cure porn addiction, but it is
a process that you need to go through that will target a number of things in your
life. Dissimulation means to disguise (one’s intentions, for example) under a feigned appearance, or to conceal one’s
true feelings or intentions. However, in Reality, your
behavior is greatly increasing your risk of being
rejected.
In my Samsung Tablet Galaxy Tab3
w/Android 4.22.
the test site:
https://www.freakattack.com
reports that
the pre-installed Google Chrome browser
is:
“VULNERABLE!”.
I updated Chrome browser,
via the Google Play Store
BUT still get the same old version,
(latest for Chrome under Android 4.2.2?).
When will Google or SAMSUNG push
the latest FREAK-safe patch/fix
for Chrome under Android 4.22?
Hello SAMSUNG / GOOGLE INC.!
Are you listening??????
We need a patch for the Android 4.2.2
Chrome browser… NOW!!!
The FREAK vulnerabilty
is out there!.
Signed:
Your customers.
– Pale Moon 25.2.1 and FF 36
– Ubuntu Linux 12.04 (32-bit)
– Samsung Tablet Galaxy Tab3 / Android 4.2.2
Being in the minority of the 2% of users running Vista I received the warning and it has to do with Bitdefender. When I turn “Scan SSL” OFF the test turns out to be okay and as usual Bitdefender is slow to respond as to why, as posted on their forum.
http://forum.bitdefender.com/index.php?showtopic=57620
That’s on my HP lappy, which I don’t use much.
On the Win7 Dell desktop Bitdefender’s “Scan SSL” is ON and the test is fine.
The FREAK vulnerability on Scan SSL is patched by Bitdefender in latest build v18.22.0.1521.
Folks, just update BD, restart and enable Scan SSL, then visit https://www.freakattack.com
@Martin[Author], update the post.
Sir Martin..
I am confused why older version of web browser is protected to this Freak Attack vulnerability…
I don’t get it, why always need to be update….?
(
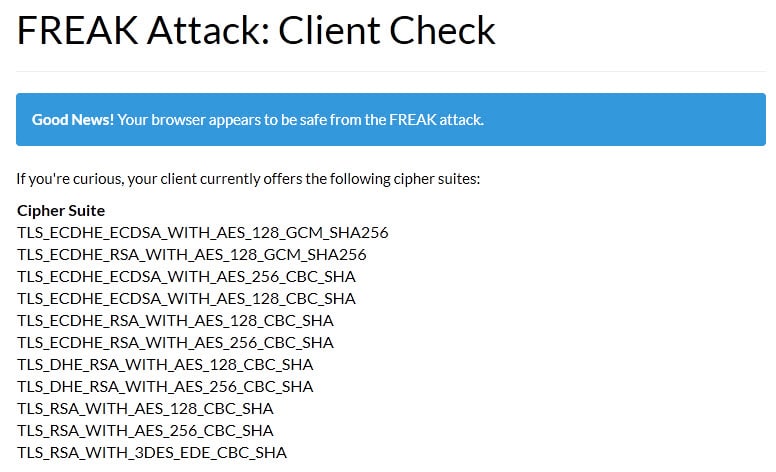
FREAK Attack: Client Check
Good News! Your browser appears to be safe from the FREAK attack.
Chrome for Windows and all modern versions of Firefox are known to be safe. However, even if your browser is safe, certain third-party software, including some anti-virus products and adware programs, can expose you to the attack by intercepting TLS connections from the browser. If you are using a safe browser but our client test says you’re vulnerable, this is a likely cause.
If you’re curious, your client currently offers the following cipher suites:Cipher Suite
TLS_DHE_RSA_WITH_AES_256_CBC_SHA256
)
About Opera
Version information
Version
12.14
Build
1738
Platform
Win32
System
Windows 7
Browser identification
Opera/9.80 (Windows NT 6.1) Presto/2.12.388 Version/12.14
I am still having problem after workaround. Most of HTTPS websites are not getting opened in IE including https://technet.microsoft.com/
Do any one has complete list of ciphers.
After applying the Policies workaround suggested by Microsoft there is an Error Code 80072EFE in Windows Update and I am unable to connect to some HTTPS websites (Microsoft ones included) using Internet Explorer. I can use Firefox and Chrome but there is still the problem with Windows Update. I have W8.1 Pro 64. By the way, Amazon.com (https) tells me that TLS is disabled, therefore I believe that the ciphers list in the workaround is incomplete.
Thanks Martin for letting Tor users through again.
This site has been blocking Tor for months.
I enabled the workaround and rebooted, only to find my event log filled with Schannel 36887 fatal alert 40. I disabled logging to stop it, but I’m really not happy.
The fix mentioned in MS Security Advisory creates a lot of issues.
Issue – 1: Windows Update was working fine even after several reboot. However, from past few hours, they don’t check for updates.
You’ll receive Error Code:80072EFE Windows Update ran into a problem.
Fix: However, once you change the group policy back to not-configured/disabled and a reboot, the Windows Update works fine.
Issue-2: Many websites don’t load at all including MS websites.
Are these f**king MS check before they release a workaroud/patch. Most of their updates have/create new issues and then MS inform users to uninstall or install the new repacked update. It is a hell with Windows and MS.
Also, I think this is a pre-planned attack produced by MS and Google to create problems in security to old version users[like Win7/Win8/8.1] and [old Android v2.x, 3.x, 4.x] forcing them to upgrade to new version or devices due to these security issues.
What kind of world is this? Its really Worse and it’ll get more Worse by these kind of s**tty giants.
Those responsible for the freakattack.com forgot to activate the feature of user contributions in order to build a list of vulnerable browsers.
This month’s Patch Tuesday will be interesting because Microsoft’s willingness to fix the FREAK vulnerability in all of its currently supported OSes and software will be gauged.
What a shock that most popular third-party browsers (except the latest versions of Firefox and Chrome as already stated above) for Android have the FREAK vulnerability. (Even the AOSP browser has that too. Almost all websites that had reported on the situation as news forgot to mention third-party mobile browsers.) “FREAK = Heartbleed of 2015” incoming.
The website smacktls.com also has a FREAK vulnerability checker, but it does not give away any more details on the testing results.
Doing the workaround as described by Microsoft caused Schannel errors to appear in my event log. I discovered this while trying to fix another issue so if you are not seeing these errors read no further.
A little research led me to this Microsoft webpage: http://support.microsoft.com/kb/2992611 .
On it is a list of these four problematic ciphers
TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
TLS_RSA_WITH_AES_256_GCM_SHA384
TLS_RSA_WITH_AES_128_GCM_SHA256
The first two are being (re)enabled by the original workaround.
As an experiment I removed them from the list MS provided and re-applied it. The Schannel errors are gone, but I can’t vouch for any other bad side effects.
Action items:
1) I don’t recommend doing what I described. It’s possible it could break something important.
2) Someone who knows how to contact Microsoft should forward this info to them.
Yes! “Firefox appears to be the only browser not affected by the vulnerability at all on all systems it supports.” +1 for Firefox.
Just in case anyone gets a “vulnerable” report from https://freakattack.com/clienttest.html be sure to check out this:
“However, even if your browser is safe, certain third-party software, including some anti-virus products and adware programs, can expose you to the attack by intercepting TLS connections from the browser. If you are using a safe browser but our client test says you’re vulnerable, this is a likely cause.”
There’s a handy little tool which you can use to configure the other versions of Windows 7 to enable the Group Policy Editor. It’s been downloaded and applied by many people, all of whom report success.
You can read about the file, and find the link to download it on ASKVG
“How to Enable “Group Policy Editor†(gpedit.msc) in Windows 7 Home Premium, Home Basic and Starter Editions?”
http://www.askvg.com/how-to-enable-group-policy-editor-gpedit-msc-in-windows-7-home-premium-home-basic-and-starter-editions/
My browsers aren’t vulnerable. Firefox, no. Chrome, no.
There is an issue with loading some websites[example: hotmail.com] after we modify group policy.
Previously, it used to redirect to sign in page of outlook[login.live.com/…..]. However, after we do this workaround, this redirection doesn’t happen. Please check from your end as well and also help with a fix. Other browsers are loading the page successfully. Only IE is affected.
Since Dolphin was included in one of the comments as vulnerable, how about UC Browser for android? Is it affected?
“mail.live.com” also not redirecting. It says “This page can’t be displayed” in IE.
Found a fix: Once we configure group policy to enabled and rebooted, I’d suggest to re-configure the same group policy to “not-configured” and do another reboot. Now, it should be fine with IE. You can run the test again with these links[Test both the links]:
https://cve.freakattack.com/
https://cve2.freakattack.com/
If both the links doesn’t load in IE, then the fix is successful.
Some more browser results.
Android 4.4.4 on Nexus 5 and Nexus 7 (2013)
Chrome Beta v41.0.2272.81 is SAFE
Chrome v40.0.2214.109 is VULNERABLE
Firefox Beta v37.0 is SAFE
Firefox v36.0 is SAFE
Dolphin Browser v11.4.2 is VULNERABLE
W7 x64
Pale Moon v25.2.1 is SAFE
Firefox v36.0.1 is SAFE
Chrome Beta v41.0.2272.74 (64 bit) is SAFE
IE11 LOL
Thanks for the article Martin!
There is missing a backslash ?
…Configuration\SSL0010002
…Configuration\SSL Backslash 010002
I have made a reg Key (freak.zip) on my site.
http://www.deskmodder.de/blog/2015/03/06/freak-sicherheitsluecke-ueberpruefen-und-einstellungen-die-microsoft-empfiehlt/
You are right. I corrected the comment.
If you have a version of Windows that lacks gpedit.msc, here’s the registry key that contains the policy.
Copy this into notepad or text editor, and save as SSLPolicy.REG ,starting with the Windows Registry Editor Version 5.00 line:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Cryptography]
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Cryptography\Configuration]
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Cryptography\Configuration\SSL]
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Cryptography\Configuration\SSL\0010002]
“Functions”=”TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P256,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P384,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P256,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P384,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P256,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P384,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P256,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P384,TLS_DHE_RSA_WITH_AES_256_GCM_SHA384,TLS_DHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384_P384,TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P256,TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P384,TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384_P384,TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P256,TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P384,TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P256,TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P384,TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P256,TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P384,TLS_DHE_DSS_WITH_AES_256_CBC_SHA256,TLS_DHE_DSS_WITH_AES_128_CBC_SHA256,TLS_DHE_DSS_WITH_AES_256_CBC_SHA,TLS_DHE_DSS_WITH_AES_128_CBC_SHA,TLS_DHE_DSS_WITH_3DES_EDE_CBC_SHA”
Wonderful, thanks!
My browser results
for freakattack.com test:
———————————
a) UBUNTU LINUX 12.04:
– FF 36.01 is safe
– PALE MOON 25.2.1 is safe (<== my main browser…whew!)
– CHROMIUM 37.0.2062.120 is safe
b) ANDROID 4.2.2 Samsung Tablet:
– FF 36.01 is safe
– CHROME is NOT safe !!!
– "Native" Internet Browser (pre-installed in Tablet) is NOT safe !!!
– Naked Browser and NB PRO+ (super fast Android browser) is NOT safe !!!
Just sharing.
– Pale Moon 25.2.1 and FF 36
– Ubuntu Linux 12.04 (32-bit)
– Samsung Tablet Galaxy Tab3 / Android 4.2.2
My results:
FF 36.01 is safe
IE11 (workaround applied) is safe
Thanks for the tip Martin!
Some more data points: I’m using Windows 8.1 Pro 64 bit
Bog stock Firefox Version 36.0.1 is OK
Chrome Version 41.0.2272.76 m (64-bit) is OK
IE Version 11.0.16 says it’s Vulnerable
This happened even after I applied the Group Policy fix, ran gpupdate, and logged out. After rebooting and clearing the browser cache, IE says it’s OK.
TLDR; Try clearing the cache if you folks are having trouble with IE after applying the MS fix.
Latest Chrome x64 and Cyberfox AMD x64 (FF variant) both invulnerable.
Chrome Version 40.0.2214.115 is vulnerable on a Windows 7 64-bit machine
Despite that the Web Shield (or whatever name various products give the web data flow protection) function sounds useful at first sight I’ve always had various issues with this feature of many security related products. In this case it turns out that at least Avast’s Web Shield acting as a proxy, which, above FREAK, can be the source of many other issues and might make one’s computer more vulnerable than without beeing used at all.
One more reason to just disable these extra components and just surfing the web with common sense.
No problem Martin
Keep up the good work
I just checked on my Windows 10 test system. Was vulnerable, ddded the new cipher order, restarted, checked again, got the message that my browser may be incompatible this time, clicked on the link and it displayed an error which meant that it is no longer vulnerable.
Firefox 36.0.1 Portable – Windows 8 32bit – Not vulnerable
Slimjet 3.0.4 Portable – Windows 8 32bit – Not vulnerable
Just for curiosity
Iceweasel 36 – Linux 32bit – Not vulnerable
Chromium 41 – Linux 32bit – Not vulnerable
Slimjet 3.0.4 – Linux 32bit – Not vulnerable
yes i rebooted after each attempt
I have no idea then, sorry. Maybe some other software is interfering?
Tried the workaround on my windows 8.1 pro and i’m still vulnerable?
Did you reboot your machine?
Portable Firefox 31.5.0 ESR on Windows 7 64-bit in not vulnerable.
Chrome on iOS 8.1.3 in not vulnerable. Safari is.
Chrome 41.0.2272.74 beta-m (64-bit) on Windows 7 64-bit in not vulnerable.
am I vulnerable if I use HTTPS everywhere by EFF?
It is not protecting against the vulnerability. Check the client page to verify.
you can be, i have that add on and my results show that i am vulnerable. Although I’m not sure why.
One website mentions that Opera on Linux is vulnerable. I don’t have Opera, but on my old Mint 17 laptop:
Chromium 40.0.22 is OK
Firefox 36.0.1 is OK
Midori 0.4.3 is OK
Qupzilla 1.6.0 is VULNERABLE
I don’t use Qupzilla much, but there it is.
The article says FF is not vulnerable, but when i click on the link to test , it says i am vulnerable. Maybe FF isn’t safe?
EDIT: I get the red banner that says,
“Warning! Your browser is vulnerable to the FREAK attack. It can be tricked into using weak encryption if you visit a vulnerable website. We encourage you to update your browser right away.”
I just updated FF yesterday to 36.0.1
I run Fx 35.0.1 and although it is supposed to be safe, I found rc4 settings that need to be toggled from true to false, and after that, freak test said my browser was safe.
In typing rc4 in about config in Fx 35, you obtain the following results which I have toggled from true to false:
security.ssl3.ecdhe_ecdsa_rc4_128_sha;false
security.ssl3.ecdhe_rsa_rc4_128_sha;false
security.ssl3.rsa_rc4_128_md5;false
security.ssl3.rsa_rc4_128_sha;false
However, when I read about these settings, I find they list 6, not 4 settings. Have no idea what the other two are.
It is likely HTTPS web-protection feature.
I know BitDefender and Avast have HTTPS traffic scanning, which works by acting as a proxy between your browser and the outside world. Since these AVs support legacy/weak SSL ciphers, you can still be vulnerable. In Avast, uncheck “enable HTTPS scanning” in “Web Shield” section.
From what I read, FREAK attack works because the hacker’s machine acts as a HTTPS proxy, and requests to use a weak SSL cipher instead of the strong SSL cipher your browser requested. Since many browsers and servers still support legacy SSL ciphers, the weak SSL cipher is used, and the hacker can work in the background breaking the weak encryption.
uninstalled (using clear avast tool) and reinstalled avast and now I am showing that I am safe from freak attacks. The one time i used avasts in software updater and it bugs out. Guess i’ll stick with manually updating Avast once again and from here on out.
+1
I’ve also had issues after using the updater.
Big ones too.
It’s a huge hassle doing a clean install of Avast, but I have haven’t had any other choice. Well, the other choice is to use another program, but, I’m not going with that one.
Thanks Martin, and Torro
Latest AVAST update appears to block the FREAK attack
https://forum.avast.com/index.php?topic=167473
Offline installer / Avast Uninstall Utility:
https://forum.avast.com/index.php?topic=167184.msg1189543;topicseen#msg1189543
Yeah I have updated version of avast, and still get the vulnerable to attack.
If i remember correctly, i think avast web shield uses their own “thing” (sorry forgot the correct term) that may be causing theproblem. what i am curious is with avast web shield on, and my comp showing vulnerability, what are the consenquences? Will i be vulnerable to freak attack, with avast web shield on, or is it safe and just shows unsafe (bug)?
Ok tried everything from disabling add-ons, to safe modes, checking network settings,and found culprit for the Firefox being vulnerable to freak attack.
It is because Avast, I temporarily disabled Avast Web shield and ran the freak test again and I now receive the,
“Good News! Your browser appears to be safe from the FREAK attack.”
maybe add that in the article for Avast users?
I am using Avast Free and IE11,Firefox 36.0.1 and Pale Moon 25.2.1 are safe.
Did you updated Avast to the latest version (2015.10.2.2214) ?
Great that you discovered what caused the issue. I add the information.
Im going to try the IE workaround, just so I can do all that i can t r and fix this. Do i copy the ciphers over what is already listed in the cipher suite form or do i copy them after that list but adding a comma first?
Just copy the ciphers from the link provided in the article into Notepad, make it so that there is no whitespace between them, then enable the SSL Cipher Suite Order Group Policy, removing the information in it and replacing it with the new ciphers. After you disable this GP, the ciphers will revert to the options in the Policy before you edited them. Good luck.
I’m using Windows 7 64bit professional
Strange, that is the same operating system that I’m using.
Which operating system are you running? I just checked and got a not vulnerable in Firefox 36.0.1.
Strange. In my case IE11 (Windows 7 Ultimate x86) is safe.Why ?
I don’t know.