How to prevent Cryptolocker Ransomware to hit your PC
Cryptolocker is a relatively new kind of ransomware that was first detected in the wild in September 2013. Ransomware for those who do not know the term refers to malicious software that, when executed on a PC, encrypts files on it so that they cannot be accessed anymore unless decrypted.
Cryptolocker displays a ransom notification to the user of the system that states that the ransom -- usually between $100 and $300 -- has to be paid to unlock the files again. If the demand is not met in 96 hours, the option to do so will expire and the files will be lost forever.
The malware lands on PCs the same way other malware does. In the case of Cryptolocker, it is usually through email attachments that contain the malicious payload. This can be (fake) customer support emails from companies such as Fedex, UPS or DHS for example, and the payload is usually disguised as a PDF file using the same icon that PDF file use.
If you look at the full file name, you will notice that it is in fact an executable program ending with .pdf.exe that should never be executed.
If your computer gets infected because you have run the executable file and your antivirus solution did not pick up on it, the following background process is started by it.
- The malicious program adds itself to the autostart of the system.
- It will then connect to a control server on the Internet and retrieve a public encryption key.
- Once the key is downloaded, the software will scan all local and network drives on the computer for specific file extensions such as xls, docx, psd, jpg or pptx.
- The list is large, and any file that it discovers will be encrypted by it so that it cannot be accessed anymore on the PC.
- Once the encryption of files has finished, a ransom message is displayed to the user on the screen.
If you notice that your computer is hit by the malware, you may want to disconnect it from the Internet to prevent further damage. This can be done by disconnecting the router from the Internet, or disabling the Internet connection on the local PC.
Recovery
There is no option to decrypt the files, and while it is theoretically possible to decrypt them using brute force, the use of a unique RSA-2048 key makes this impossible for home users at this point in time.
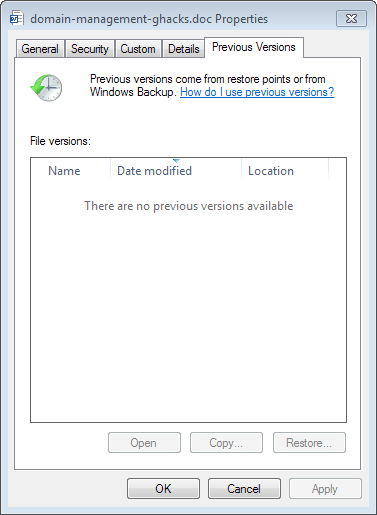
There is however one option that you have: previous file versions. You can right-click any file in Windows Explorer, select Properties and then Previous Versions to display previously saved versions of that file on the system. While there is no guarantee that you will indeed find one, it is the best option that you have to restore important files on the system.
There is also the chance that you have backup copies of files. Most file synchronization services enable you to download previous copies of a file as well.
Prevention
The best prevention is to know what you are doing on the PC you are working on. A basic understanding of how things work goes a long way in staying safe on the system. In fact, I believe that this is the best protection against many kinds of malware attacks you are exposed to on the Internet.
Good antivirus software should detect Cryptolocker by now. Malwarebytes and Symantec do detect it for example.
If you are particularly worried about your PC getting infected, you can run the tool CryptoPrevent on it. It locks down executable file from being run in directories that Cryptolocker is known to use.
Video
Further reading
This guide has been designed to provide you with a quick overview, and is not as detailed as the guides posted below. If you want to find out more about Cryptolocker, consult the following guides and pages:
- Cryptolocker ransomware information on Bleepingcomputer
- Malwarebytes blog post about Cryptolocker
- Sophos analyzing the malware
- Wikipedia on Cryptolocker
HitmanPro.Kickstart
HitmanPro.Alert with CryptoGuard
CryptoPrevent
Which?
I assume that HitmanPro.Alert with CryptoGuard makes it wholly unnecessary to use HitmanPro.Kickstart and if this is correct, then it leaves HitmanPro.Alert with CryptoGuard vs (or maybe not vs) CryptoPrevent.
Use both or is HitmanPro.Alert with CryptoGuard sufficient?
Cryptolocker Prevention Kit :
I visited the CryptoPrevent download page and only read a little of it, for I downloaded HitmanPro.Alert with CryptoGuard tonight for installation later today, after getting a few hours of shut-eye. But, I noticed that the page refers to a more complicated app. called Cryptolocker Prevention Kit.
So, I’ll add that app. to the questioning presented with this post for feedback and I’m not going to crack my skull with trying to guess what the possible reply or replies may be. I only began learning about this crypto ransomware piracy crap tonight and am a wee bit confused at the moment. Adding to the confusion is that I already use Firefox with NoScript and RequestPolicy, albeit those don’t help with the Thunderbird email app. And I additionally have Avira free plus Malware Defender, as well as WinPatrol, always running real-time, with Avira and Malware Defender set to their maximum security settings.
Kickstart is included in HitmanPro, HitmanPro.Alert is a standalone program that can only detect and quarantine but needs HitmanPro or another program for removal.
CryptoPrevent handles only the Cryptolocker malware, and as a side-effect, against (some) other cryptolockers that use similar technologies.
If you think your resident security software is up for the task, you can install Alert which is definitely a good choice.
I have HitmanPro, but it’s the free version, so I maybe this won’t for removal of things HitmanPro.Alert suggests should be removed. But, as long as it shows the directory path and filename for files that either should or else need to be removed, then this’ll still be good enough.
I ran it on Saturday though and it showed some OpenCandy stuff as well as plenty of things associated with or from Conduit. I don’t know how Conduit stuff got installed, but it has to be with some software that I personally installed. I’m the only person who does any sys. admin. sort of work and software installations, as well as removals, with this PC. Anyway, I let HP ignore the OC stuff and had it remove the Conduit stuff, figuring that this surely can’t do any harm. The system has run without any problems since.
But that’s “just it”. If it was able to remove the Conduit stuff, which hasn’t been reported again with subsequent scans done with HP, then I wonder if HP would also work for doing the removals suggested by HitmanPro.Alert. I hadn’t run HP for some years, having even forgotten that it’s installed until coming across your article this past weekend. It won’t be forgotten now, for it’s been changed to run at every Windows start.
I think to have once read that HP, when used for free, will initially do some things that it’ll cease to do after a period following installation and possibly first use; a trial period, I guess. It must’ve been run when I first installed it, but this is too long ago for me to be able to remember this detail. If the installer offers to run HP at the end of installation, then the scan was surely done. If it was, then it was a long while back and it seems to have definitely eliminated the Conduit stuff this past weekend.
If it’s not supposed to do that after all of this time since installation, then the programmer apparently would’ve forgotten to have HP check how long it’s been installed in order for the program to be able to determine if it should run in limited, free version manner, or complete.
I am the sys admin for a smaller biz. One of the users used his aol.com email account and opened up a file that got thru and infected some of our network folders. So probably ~1000 or so file. We stopped it before the virus finished and therefore we did not recieve the ‘ransom’ letter. So we thought we were done with. But, they started a new website where you can submit a part of an infected file and ‘they’ can search their database for the private key to decrypt it… Guess what? yes they did have that key… It was a crazy long one. We payed up 1 bitcoid.. about 400$ and we got the key. We then were able to decrypt all of our files and are continuing to do so. In our case it was worth it to the client. It should be said, that this happened and then we were brought in to do damage control and this is what we found. Normally I would say HELL NO i wont pay, but it was the company’s money and honestly not that much. It sucks Yes, but taught them/us a very valuable lession. Good luck to the rest of you. And NO, we did try EVERYTHING. It was encrypted and nothing we could do.
what about editing the hosts file? Isn’t it known by now where the program gets its public key from (step 2)? If you add these inet addresses to the hosts file and point them to 127.0.0.1 then the virus is unable to obtain its key and cannot start encrypting. Right?
Pretty sure it encrypts the data with a predefined key, and then bothers to call home. You are already in trouble if you get it, preventing further internet isn’t going to help.
We created a free scan tool that finds CryptoLocker encrypted files dumps the list into a CSV file. This is handy when trying to figure out what files need restored from backup.
http://omnispear.com/tools/cryptolocker-scan-tool
A common sense and and a little knowledge replaces even the best Antiviruses out there!
Yup, did me solid for more than a decade. The problem is, the average Joe on computers now doesn’t do this. That’s why some people need that bloated crapware. The alternative is worse, I guess.
I just figured how to make this malware useless for its owner..even if I got infected.
“Once the key is downloaded, the software will scan all local and network drives on the computer for specific file extensions such as xls, docx, psd, jpg or pptx.”
That means if I have custom file extensions on my laptop it won’t find what it is looking for :)
There are plenty of methods for mass renaming eg.FreeCommanderPortable :)
Unless I’m missing something somewhere; if you change the file extensions how does the usual program that opens the files know what it’s looking for?
Well you can map any file extension to any program.
won’t the firewall on your PC prevent it from connecting to their server after infected ?
You’ll have to open it to decrypt your stuff then.
Depends on which you use and how it is configured, likely won’t on most systems.
Anti Cryptolkr measures… Back up your hard drive and/or registry hives.
To help protect your computer against this attack, open Control Panel > Administrative Tools > Local Security Policy (not available in Home version of Windows). Click Local Security Policy and locate Software Restriction Policies under the Security Settings heading. Right-click Additional Rules and select New Path Rule to open the new-rule dialog box.
Type the following Path, Security Level, and Description information as separate rules:
For XP users, enter:
Path: %AppData%\*.exe
Security Level: Disallowed
Description: Don’t allow executables from AppData
and
Path: %AppData%\*\*.exe
Security Level: Disallowed
Description: Don’t allow executables from AppData
For Vista and newer, use same as above, plus the following settings:
Path: %localAppData%\*.exe
Security Level: Disallowed
Description: Don’t allow executables from AppData
and
Path: %localAppData%\*\*.exe
Security Level: Disallowed
Description: Don’t allow executables from AppData
More paths for preventing ZIP-file locations are described in the bleepingcomputer.com CryptoLocker Ransomware Information Guide and FAQ. The following will ensure the virus won’t launch from embedded or attached .zip files.
Path: %Temp%\Rar*\*.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened with WinRAR.
From archive attachments opened with 7zip:
Path: %Temp%\7z*\*.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened with 7-Zip.
From archive attachments opened with WinZip:
Path: %Temp%\wz*\*.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened with WinZip.
From archive attachments opened using Windows’ built-in .zip support:
Path: %Temp%\*.zip\*.exe
Security Level: Disallowed
Description: Block executables running from archive attachments opened using Windows built-in ZIP routine.
REBOOT YOUR COMPUTER to make the changes effective!
These rules should work for the current threat. If attacker’s change the method of attack, these rules make not prevent the attack. But, for now, this is about all you can do.
These are fairly extreme measures against a pretty significant threat. You might have to undo some of these rules if you find that you cannot update applications or install certain software. If you have a problem, you might also find the misbehaving rule by checking the Admin section of the application event log. You might also consider the fairly technical path of application whitelisting.
Anti-virus apps are no guarantee against this evil attack.
This is definitely some good info and preventive measures, thanks.
This people behind Cryptolocker DO follow through when they are paid. They decrypt your files and they do not re-infect your system again. They require that you head down to CVS or Walmart and purchase a green dot money card. So, actually, you pay $305, not $300. Once you do this, you go back to your computer, follow the instructions, and wait for the bastard to essentially “steal” the money. After that, within a few hours, your files start getting decrypted.
We’re in IT and we’ve seen this Malware hit a few clients. It sucks and it’s the worst thing out there to date. I know people who have paid to avoid losing ALL the pictures of their children for the last 15 years or who pay to make sure they can access their client base.
I have no respect for this sort of behavior in the tech community. These people are thieves, plain and simple, and, hopefully, will be caught before they rake in too much more cash.
Would Crytolocker work if one were using Sandboxie for browser and email programs?
Only if it got onto your main file structure, which depends on its attack vector. You might be safe from ever getting it using a sandboxed email. Just be careful if you ever install an attachment.
Wow… Malware… you just got interesting… Can’t wait for the first time one of my friends get this…
Friend: “This program says my files are encrypted!”
me: “Do you have your files backed up?”
Friend: “No”
me: “Welp, you’re f***ed”
Makes my life a little easier, and teaches them a valuable lesson of backing up.
Why would it make YOUR life easier? How about you be a good friend, and tell them to backup or install this preventive tool now, instead of laughing at them later?
Well I don’t know much about encryption except that it’s very very hard to break – but assuming paying $300 really does give you your files back, there should be a way to fool the ransomware that the payment is done – hacking into the files of the ransomware from a bootable Windows/Linux copy?
Yes, I’m rather curious about this…I can’t think of ANY files on my computer that I’d pay a $300 ransom for…Those pictures of the dog have great sentimental value, but not $300.00 worth. But still I wonder, does anybody actually PAY the ransom, and if they do, does the ransomer actually deliver the hostage by providing a valid key, or just disappear with the money?
I suppose if the ransomer accepts credit cards, he could be fairly easily foiled…Simply provide a credit card, and then once you have the decryption key, immediately call the card issuer to cancel/report the card as stolen, preventing the ransomer from making any additional charges. As for any charges incurred BEFORE the card’s cancellation, the cardholder can simply dispute those charges. It would seem that such a dispute would have to be decided in the cardholder’s favor by default, since the card issuer likely would not even be able to reach the ransomer to verify that the charge is “valid.”
On the other hand, perhaps they don’t accept credit cards and ask for your bank account # and routing #, with the real goal of not just taking $300.00, but draining your entire account…
Either way, it’s not something I’d be willing to TRY, but I am still curious about what would happen if anyone did…And surely some people have, considering the number of people who have been willing to provide their bank details in an effort to assist some Nigerian prince who just happened to send them an email…
Imagine 3 years of baby pictures gone. You would pay to have them back. Just because you don’t care about your dog, doesn’t mean lots of other people out there care about their stuff.
They do give you back your data after getting paid, that’s the only way it would work. No one would pay if they didn’t. The only way they can continue is by doing that. Locking up a bunch of people’s stuff and never doing anything would never accomplish anything or gain anything for anyone. By unlocking, they generate positive marketing for people to pay them. The cost is just enough to be affordable, and still be worth while. It’s quite a clever scheme.
“I can’t think of ANY files on my computer that I’d pay a $300 ransom for”
I never said about paying – I talked about hacking the ransomware’s files to force it to decrypt the files.
There has been many documented cases where people have paid and did get the files decrypted. It may not be worth $300 for some home users, but any business shouldn’t think twice to pay that to get their files back.
Indeed, personal education on basic computer security do’s and dont’s is the best antivirus. On top of that I use Avast free (love the new interface) and every month I make an exact clone of my harddisk onto another harddisk that is normally disconnected and turned off, so no virus in the universe can ever infect it. So even if my entire disk dies, I still have a backup. No need to restore files, simply swap the broken disk with the backup and I’m ready to go.
@Dario
Smart but… when your Bios got compromised too then you are done.
He’s also done when a meteor hits his computer.
Also, how exactly would he be “done”? The backup disappeared mysteriously in your scenario?