
Google Authenticator is a popular two-factor authentication app to create codes for authorization processes. Up until now, Google Authenticator did not sync codes across a customer's devices, which meant that customers had […]

VirusTotal announced the launch of Code Insight, a new feature of the malware detection and analysis platform, which uses AI to analyse code and provide information on detected threats. One of VirusTotal's […]

According to a report by The Irish Times, the National Cyber Security Centre (NCSC) has instructed employees of government departments and agencies to remove TikTok from their work-related devices following a thorough […]
Announced in January 2023, the ability to export Microsoft Word documents to Amazon Kindle devices is now available for testing. The feature is available in Microsoft Word for Windows and Word for […]

Proton, the Switzerland-based company known for its Proton line of products, including Proton Mail, Proton VPN and Proton Drive, announced the launch of Proton Pass today. Proton Pass is a password manager […]

1Password is a popular commercial password management solution. Agile Bits, the company behind the product announced a change recently that affects all users who still use classic extensions. Broken down to its […]

Tools like Microsoft Excel, LibreOffice Calc, or Google Spreadsheets are widely used both in the business world and also at home. If you work with large tables regularly, you may wonder if […]
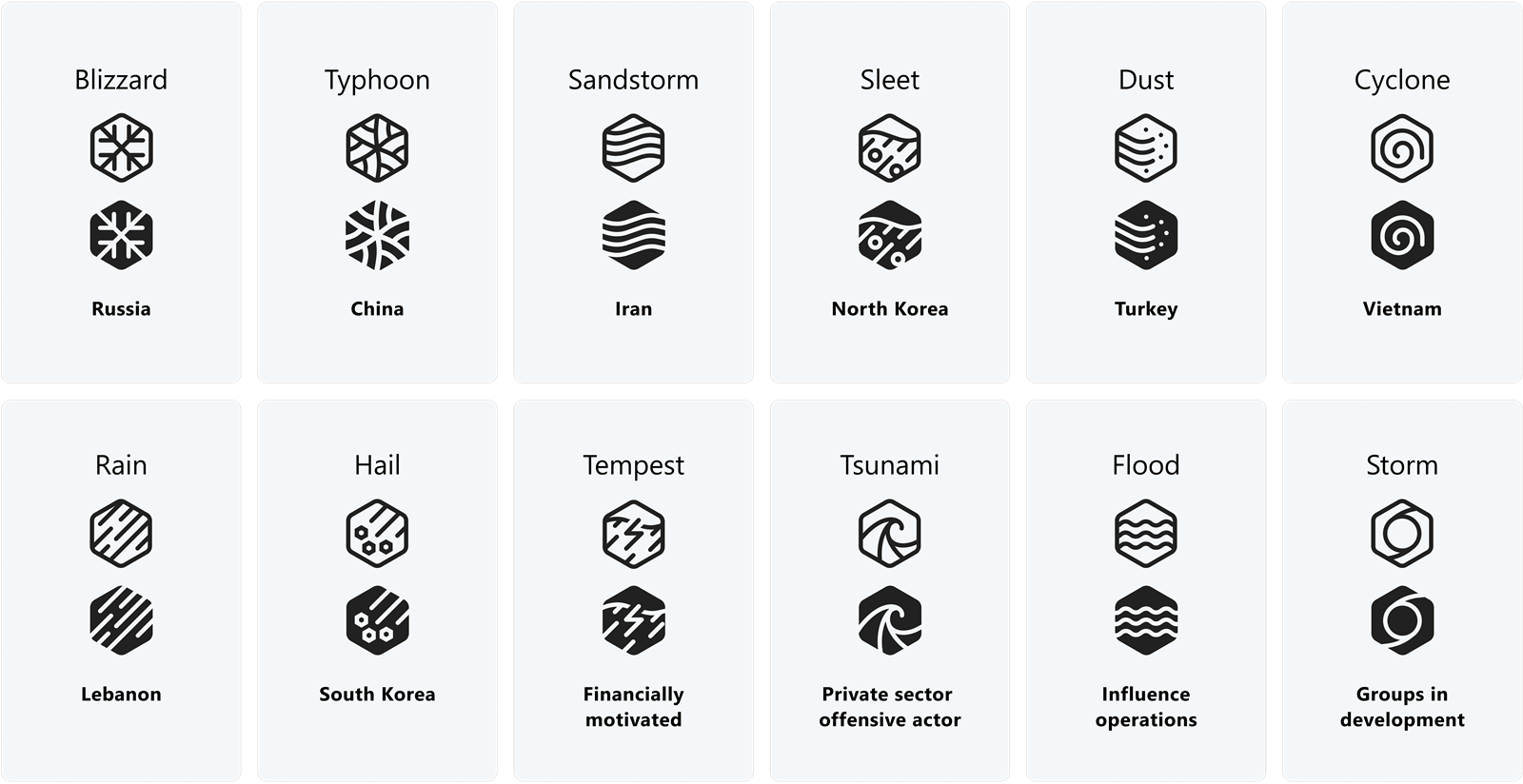
Strawberry Tempest, Night Tsunami, Aqua Blizzard or Circle Typhoon sound like something that you would order in a Cocktail bar, or a fancy coffee joint. These deliciously sounding constructs are, however, not […]

KeePassXC is a popular password manager for Windows, Mac and Linux that uses the KDBX file format from the password manager KeePass. The developers of KeePassXC have published the results of a […]

Western Digital confirmed a network security incident earlier this month, but did not reveal much in terms of information, as the investigation was still ongoing at the time. The company did shut […]

Kodi, maker of the popular entertainment center app, confirmed a data breach of its user forum software earlier this week. The development team became aware of the hack after a dump of […]

The Federal Bureau of Investigation has issued a warning against using public phone and tablet charging stations. Bad actors are using manipulated stations to infect phones and other connected devices with malware. […]

Remote work has seen an incredible boost during the pandemic. As governments and organizations scrambled to get things under control, many workers and students suddenly found themselves in quite the different work […]

MSI confirmed that it has become the victim of a cyberattack on Friday. The company published a short statement on its official site about the incident. In it, MSI describes that its […]

Google published the Android Security Bulletin for April 2023 earlier today. The bulletin lists vulnerabilities that Google has patched. It is divided into two patch levels: the first contains security fixes for […]

Western Digital confirmed a network security incident today and that some of the company's systems, including My Cloud Home and My Cloud OS, are down currently. The company detected the network intrusion […]

A decade old Windows bug, for which a fix is available, is used by malware currently in attacks against Windows devices. Malware actors may exploit the vulnerability to add malicious code to […]

Discover the advantages and potential drawbacks of smart locks compared to traditional locks. Learn how smart locks can offer added security features and convenience.

Enpass and Bitwarden are two popular password management solutions. The two products have several similarities on first glance, but when you dig deeper, you will notice huge differences. Both password managers include […]

Storing data in the cloud is often useful to users: from syncing data between devices to cloud-based backups and sharing options. While local storage still dominates, the use of cloud storage has […]

Facial recognition is considered a trusted security measure as most tech giants rely on the technology, offering it as a feature in their devices. While it offers some advantages, there are also […]
As a consequence of ongoing phishing campaigns using Microsoft OneNote, Microsoft announced that it would harden the application against phishing attacks in early March 2023. Microsoft planned to start the rollout of […]

After last year’s attack on Google users, the company is now closer to learning where the hackers are. Learn more here!

BingBang, that is the name that security researchers at Wiz gave the Azure platform vulnerability that allowed them to change Bing search results and access Microsoft user data, including emails and work […]

Whether you are traveling frequently or a remote worker, relying on public Wi-Fi may not be ideal, but it may be the only option to get work done sometimes. Many may not […]

Nexon files lawsuit. See detail of the lawsuit. Check out Ironmace using ChatGPT to show baseless claims.

Users of the Bitwarden Password Manager may install it on their desktop computers and also mobile devices. Computer users may also install the Bitwarden extension in browsers such as Chrome, Edge or […]

Discover what type of bulk Internet data the FBI has been purchasing. Discover the name of the Florida company and its affiliates.
One of the world's most popular tech YouTube channels was hacked recently. Linus Tech Tips has over 15 million subscribers on YouTube, but all of the company's technical expertise has not prevented […]

Password managers are one of the most important security tools for computer users. They store passwords securely and help with the generation of strong and unique passwords. Computer users have two main […]
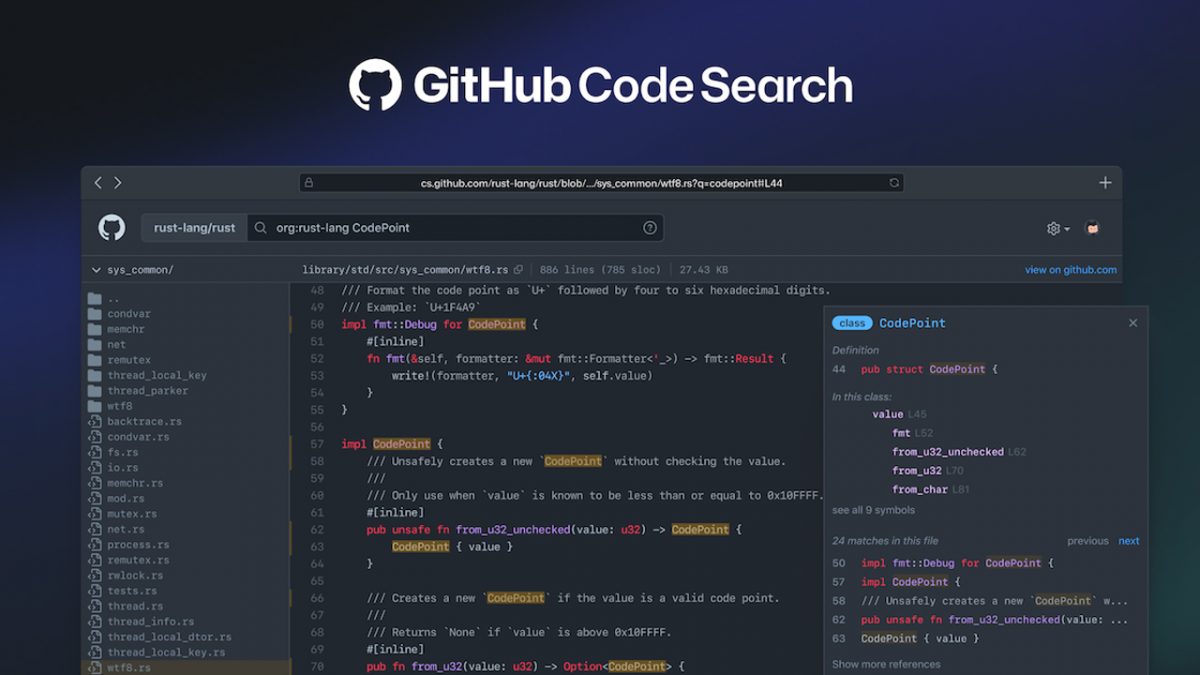
Recently GitHub seems to be getting its fair share of problems. It all started with the user who published Twitter’s source codes on GitHub. Who remains unidentified as Twitter takes Github to […]

Passwords can be a source of frustration for many individuals in the digital age, often viewed as an inconvenient necessity. While they are an essential element of online security, research indicates that […]

Twitter source code revealed on GitHub. Now they’re trying to find the culprit. Twitter has taken the issue to court making demands to GitHub.

From the U.S. and Canada to India and Afghanistan, various countries have banned or restricted TikTok due to concerns over privacy and security risks. Click here to learn more.
Our phones are multifunctional devices that help us in many ways. However, every phone activity leaves some kind of digital print, similar to our fingerprints. Almost like creating our digital identity, who […]
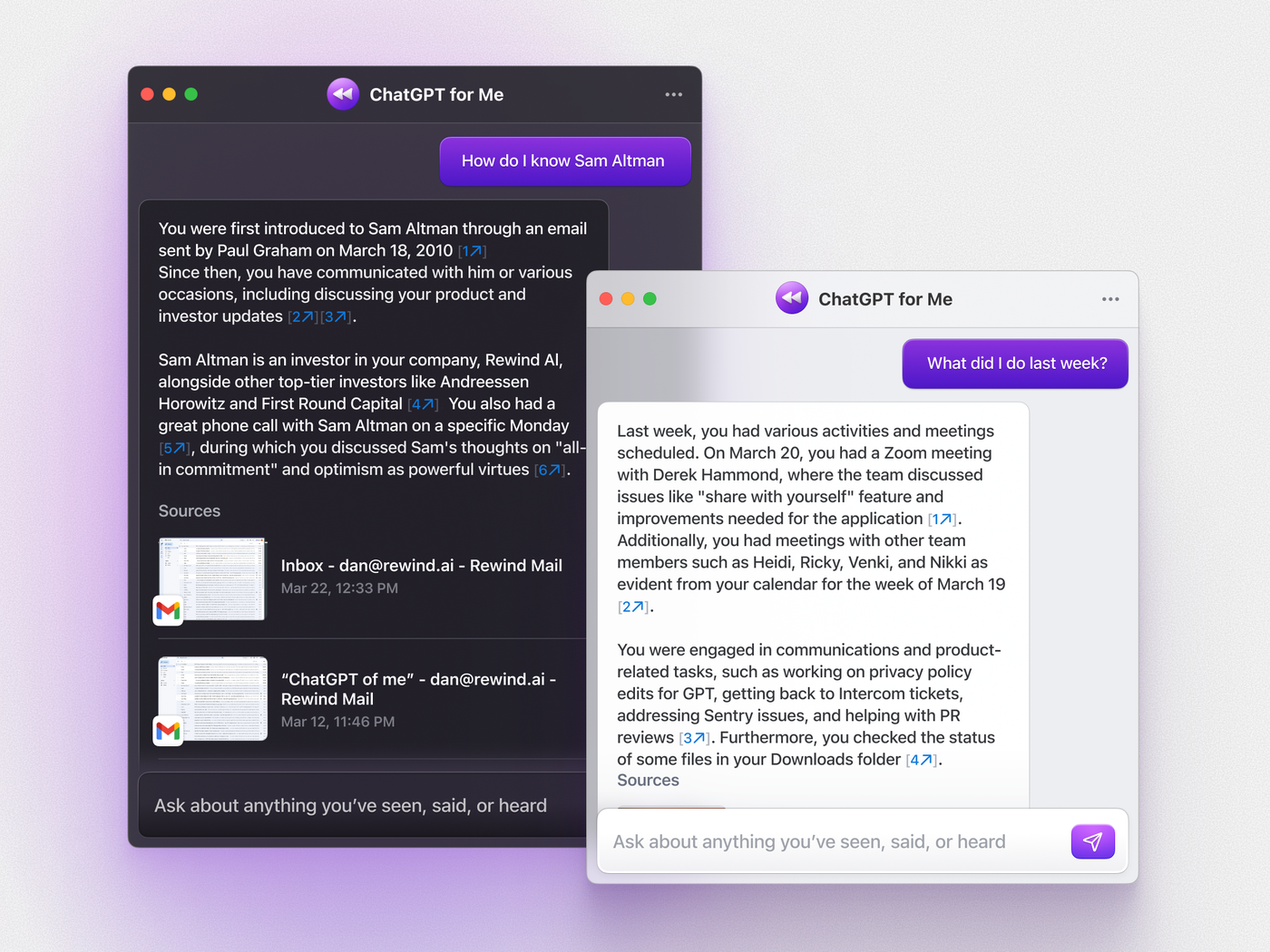
ChatGPT for Me by Rewind is a new AI system that promises to help you find things on your PC, but there are some security issues. Read more!

It is the third day of the PWN2OWN VANCOUVER 2023 hacking contest. So far, security researchers managed to crack the operating systems Ubuntu, macOS and Windows 11, and other products, including Tesla […]

Since Twitter disabled SMS-based two-factor authentication (2FA) for non-paying users, there are still ways you can protect your twitter account for free. Stay here to read more about the reasons for this […]

Earlier this month, I wrote a tutorial on enabling the upcoming security standard WebAuthn in Bitwarden as a two-step login protection. WebAuthn, which stands for Web Authentication, is integrated into operating systems, […]

Emotet is back and ready to strike via Microsoft OneNote email attachments. The Emotet threat, associated with the Gold Crestwood, Mummy Spider, or TA542 threat actor, remains active and resilient despite law […]