Microsoft discovered an exploit in macOS that could bypass System Integrity Protection

Microsoft has revealed that its security engineers had discovered an exploit in macOS that could be used to bypass the System Integrity Protection (SIP). Apple has patched the security vulnerability that was code-named Migraine.
What is the Migraine exploit in macOS
As Microsoft's report explains, SIP, also called rootless, is a security technology that was introduced in macOS Yosemite. The sandboxing mechanism is in place to restrict a user with root access from compromising the system's integrity. If not for it, a hacker could breach the system and install some malware on the computer, while creating additional attack vectors.
The report from the Redmond company notes that it used the same malware hunting technique that it had employed to discover the Shrootless vulnerability that it had discovered in 2021. This involved focusing on system processes that were signed by Apple that have the com.apple.rootless.install.heritable entitlement, i.e. a privilege that can be used for particular capabilities. The researchers found 2 child processes that they were able to tamper and gain arbitrary code execution, which allowed them to bypass the operating system's security checks related to SIP.
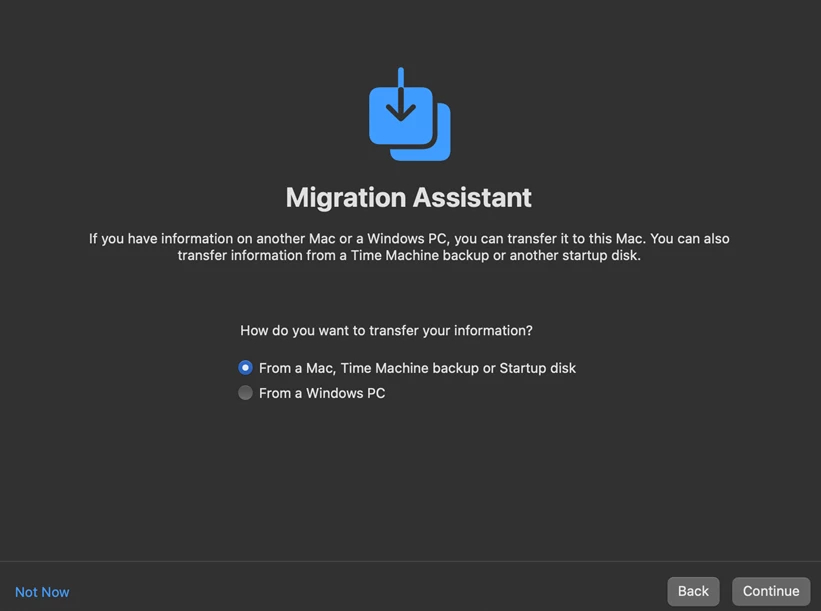
The vulnerability affects macOS' Migration Assistant, hence the name, Migraine. The tool has a Setup Assistant that helps users switch from a Mac or a PC to a new Mac, this is handy when someone buys a new Mac. The exploit that affects the utility works when the user has signed out of the system completely. Microsoft says that this flaw isn't limited to physical access, and that hackers could trigger it remotely to bypass SIP.
The researchers reverse engineered the Migration Assistant to unearth a function that signs out the user. They tried patching it to prevent the process and failed initially, but helped them discover some debug parameters. They then used the commands to trigger Migration Assistant to run without signing out the user. Microsoft's security engineers created a 1GB Time Machine backup with an arbitrary payload (like a malware) and used an AppleScript to mount it, and trigger the Migration Assistant to start loading the malware.
The researches say that this method of bypassing the SIP could have dangerous consequences such as undeletable malware (persistent), and could be used for installing rootkits, trigger kernel code attacks, etc, that could be used
Microsoft Threat Intelligence shared its findings with Apple through the Coordinated Vulnerability Disclosure. The security issue was tracked as CVE-2023-32369.
Apple has already patched the Migraine exploit
Apple released macOS Ventura 13.4, macOS Monterey 12.6.6 and macOS Big Sur 11.7.7 on May 18th. The updates contained a patch to fix the Migraine exploit, so you don't need to be worried about your Mac's security if you have installed the latest OS update. If you are yet to update your machine, you should do so as soon as possible.
The Cupertino company had credited Jonathan Bar Or, Anurag Bohra, and Michael Pearse of Microsoft for discovering the security vulnerability (related to libxpc) and reporting it to Apple. It's also worth noting that the Migraine vulnerability was not one of the 3 actively exploited security issues that were addressed in the update.





















Thanks @Ashwin for these articles! :]