Apple's Security: A Guide to Passwords, Tokens, and Keys

Apple supports a wide range of authentication options on macOS and iOS. This guide provides an overview of the available authentication options and gives recommendations regarding security and ease of use.
Passwords are by far the most common authentication option on today's Internet and for devices. They have been supported for a long time, and while they have several disadvantages when compared to other authentication options, they won't go away anytime soon.
Apple supports a number of authentication systems. As of March 2023, the following systems are supported by Apple:
Passwords
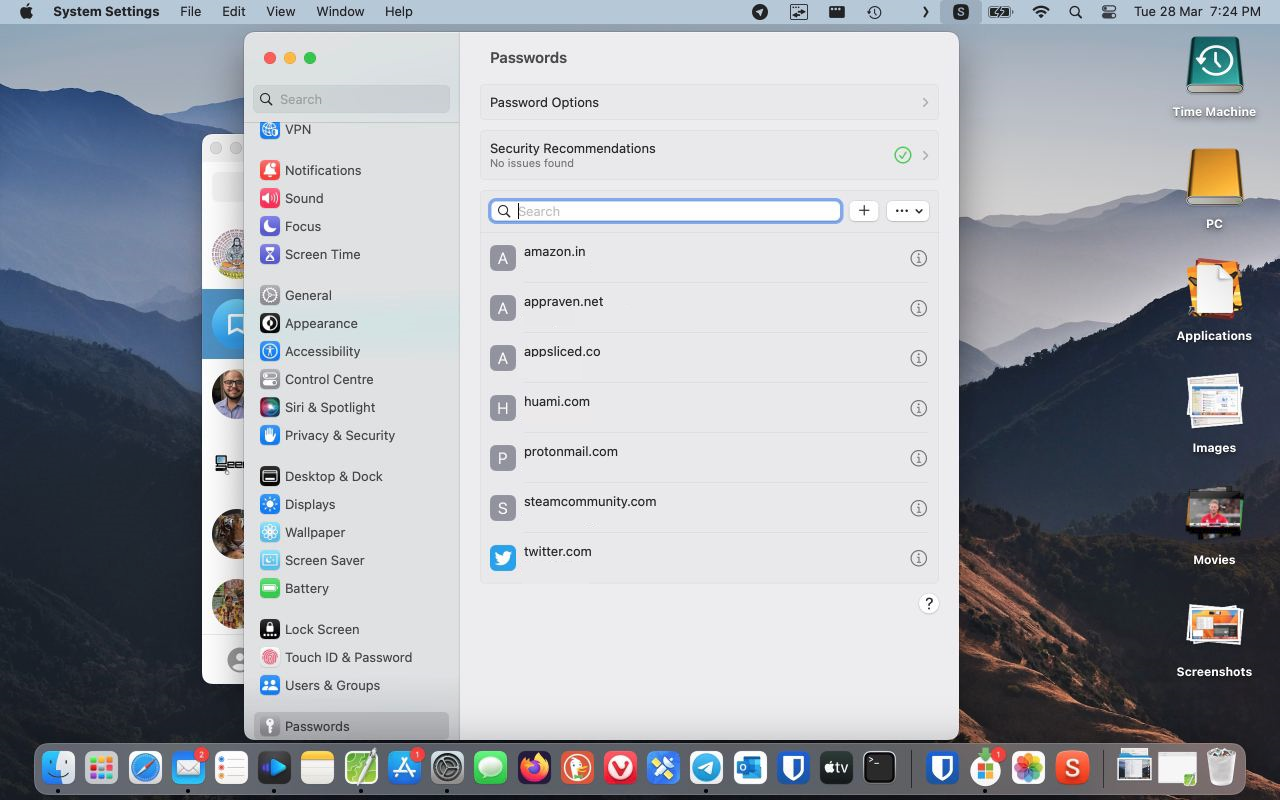
Apple's native password management systems let users generate passwords, store them securely, and use them in Safari and in apps that support WebKit View.
Apple users may access the passwords manager in different ways, depending on the operating system that is used:
- On mobile devices, e.g. on Apple iPhones and iPads: Settings > Passwords.
- In the Safari browser: Preferences > Passwords
- In Monterey: System Preferences > Passwords.
- In Ventura: System Settings > Passwords.
Passwords support the manual creation of passwords in the interface. Additionally, users may add notes, and copy stored information, e.g., to paste them into other applications directly.
Password autofill is also supported on Windows, using Edge or Chrome, with the help of iCloud.
Second-factor authentication
Second-factor authentication tokens are Time-based One Time Passwords (TOTP). They are designed to improve the security of accounts by adding a second security layer to the authentication process.
Without second-factor authentication, attackers need just the user password to gain access to the account. With the feature set up properly, the attacker would also need to get their hands on the code.
Apple added support for the feature in iOS 15, iPadOS 15, and Safari 15 for macOS. TOTPs and Passwords are synced via Apple iCloud Keychain.
Passkeys
Passkeys is a new industry standard that makes passwords obsolete. Instead of relying on passwords, passkeys are pairs of keys that get generated on the user's device. A private key remains on the device, a public key is provided to the application, service or website.
Passwords do not need to be entered anymore, but users may authenticate a sign-in with Touch ID, Face ID, a device passcode or the macOS account password. While the operation is confirmed using these, all of this happens on the local system, which means that passwords are no longer transferred to a remote server for authentication.
Passkeys are not supported by many services yet.
Hardware security keys
Hardware security keys are physical security keys that can connect to Apple devices using different types of connection options. Some support connections via USB or Lightning, others use Bluetooth or NFC for that.
The hardware key is used for the authentication process. It supports web logins and also Apple ID logins as of January 2023. The latter requires that the most recent version of the operating system is installed, as Apple integrated support for this in those versions.
Which one is best?
There is no definitive answer to the question, as it depends on a number of factors, including the devices that are used and whether hardware keys are an option.
For most users, the combination of passwords with second factor codes is probably the main option. It improves password authentication and protects against many forms of attacks. Passkeys are an up-and-coming standard, but they are not supported widely yet. Hardware keys and passkeys are more secure even, but the former require a physical key that needs to be purchased.
Now You: which authentication options do you prefer?