Google Play Store also infested with malicious Authenticator Apps
Last week, app developers discovered malicious Authenticator apps in Apple's App Store. Now, they report that similar fake authenticator applications are also found on the Google Play store.

The primary purpose of Authenticator apps is to improve security. They add a second layer to the authenticator process, usually by generating temporary codes that users need to enter during the sign-in process. Authenticator apps are also used to confirm transactions, e.g., when using brokerage services.
There are so many authenticator apps available, that it may be difficult to pick the right one. You can check out or list of top authenticator apps for Android and iOS as a guide.
Authenticator apps prevent brute force attacks against accounts and password phishing, unless the second factor authentication is also taken into account.
Big tech companies such as Apple, Microsoft or Google have developed authenticator apps that users may use. There are third-party applications available as well, which may offer better functionality or designs, when compared to these.
Fake Authenticator apps
It is difficult to gain access to a user's Authenticator app, as device access is required for that. The stealing of codes is also problematic, as they are only valid for a short period of time.
If, however, the authenticator app or secrets are controlled by a malicious actor, it is providing them with the means to generate codes directly, even when the user device is offline or not on at all.
The QR code contains the seed, or secret, that is used by the Authenticator app to generate one-time passwords, also known as TOTP, Time-based One-Time Passwords.
Last week's report about malicious authenticator applications on Apple's App Store appears to have been just the tip of the iceberg. Now Mysk, the researchers who revealed the existence of fake apps on Apple's store, confirm that Google's Play store is also plagued by fake authenticator apps.
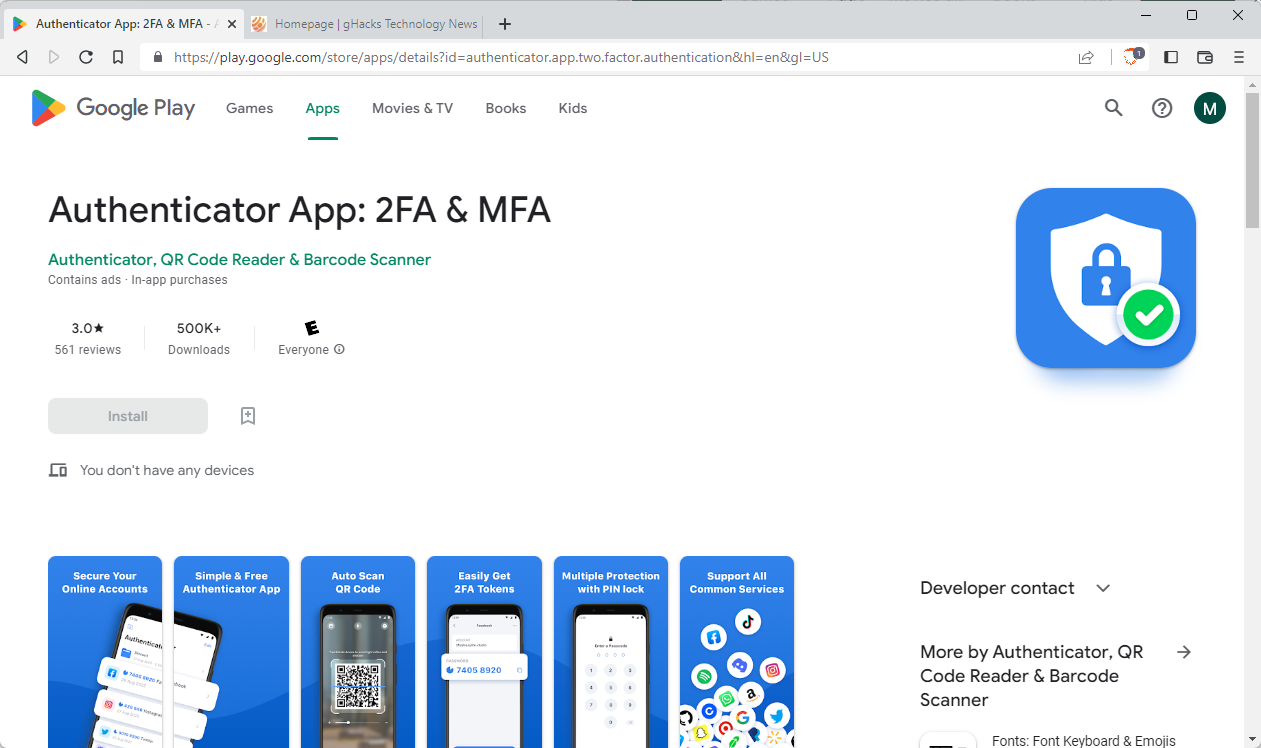
They highlight one of the fake applications on their Twitter account in particular: Authenticator App: 2FA & MFA.
The app had over 500,000 downloads on Google Play and an average rating of 3.8 at the time of the post. The malicious app is still available on Google Play, but its rating has dropped to 3.0 in the meantime. It is also returned as one of the first results for certain user searches on Google Play.
The application that Mysk analyzed functions like a regular authenticator app on first glance. Users may scan QR codes, which services display on their sites, using the app to generate one-time codes for those sites and services. Behind the scenes, the app sends the QR codes to a remote server, according to Mysk.
With the code in their possession, the malicious actors may generate codes for the linked service at any time by just scanning it in any authenticator app. While they do need access to a user's primary password and username as well, they have rendered the second layer of defense useless for that particular service, and any other the user adds to the service.
The app in question included a 3-day free trial, but it asked users to subscribe to unlock the full functionality.
Closing Words
As a regular user, it is almost impossible to know whether an authenticator application is legitimate or malicious. It is a good idea to ignore application store search options to find security apps, and pick an app from a selection of trusted companies and developers instead.






















Every year millions of downloads by users contain malware or malicious code from playstore and google still has been unable to say they are the safer place to get appa. I have never heard of malware on F-droid’s main repository in fact fdroid even warns you when you to uninstall a app if a vulnerability is discovered untill that app is updated to resolve the issue. A vulnerability is not the same as someone purposefully adding malicous code like on playstore apps but its still important to resolve. Playstore does not warn users about vulnerabilities in apps that im aware of.
Beyond a point, there’s no cure for dumb users. Internet has been around since 1993 and only gotten easier to use (to its detriment given the number of cretins using it has exploded). Warnings about email scams and malware have long since percolated to the mainstream press (as opposed to just tech blogs), and yet if people can’t be bothered to educate themselves or be more careful, they deserve to get scammed. Just like the news the other day about fake ChatGPT apps when one can verify no official app exists just by looking at their main website. To make an analogy with cars, it would be as though one has a driving license and yet can’t figure out how to work the pedals or the shifter while giving the excuse of ‘it’s too technical for me’, a century after they became commonplace.