Twitter disables SMS Two-Factor Authentication for most users on March 20, 2023
Twitter announced this week that it will turn off SMS-based two-factor authentication on the site for most users. Only Twitter Blue subscribers may continue using two-factor authentication through SMS text messages after the March 20, 2023 deadline.

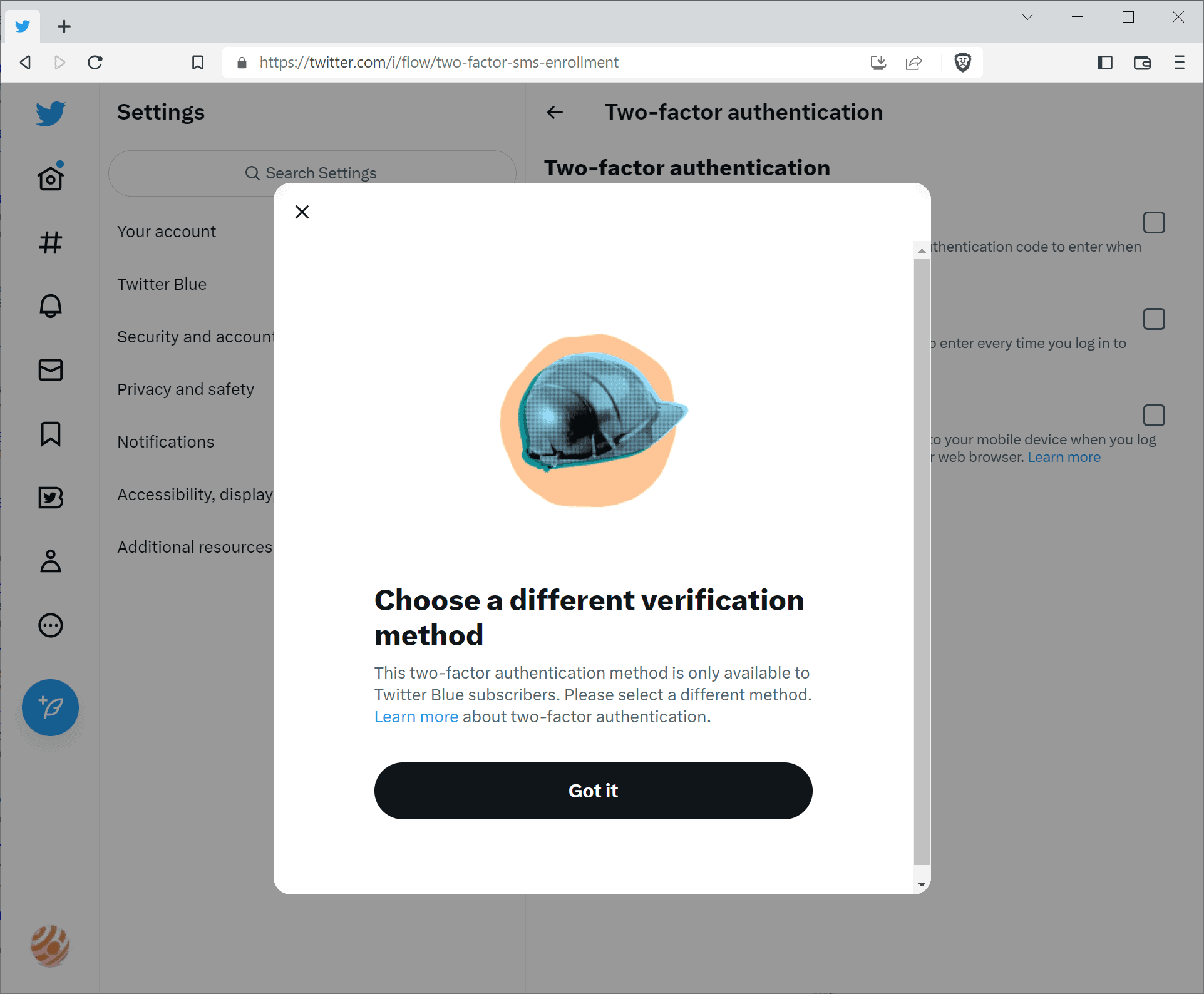
Twitter users who use SMS as the two-factor authentication method at the moment may disable it manually, or have it disabled by Twitter on March 20, 2023. Twitter recommends that users switch to another authentication option. The service supports two additional two-factor authentication methods that require an authentication app or a security key.
Twitter users who select Text message as the two-factor authentication option receive a prompt that asks them to choose a different verification method, as it is "only available to Twitter Blue subscribers".
Twitter Blue was turned into a subscription service in late 2022. Users and organizations pay $8 per month, or $11 per month on iOS, to get the blue checkmark on the site and some privileges associated with it.
Two-factor authentication adds a second layer of verification to the sign-in process. Instead of signing in with the username and password, users will also have to enter a code that they generate or receive using a support method. Text-based verification is very common, as it means receiving the code as a new SMS on a mobile device.
Twitter argues that phone-number based two-factor authentication has been "used - and abused - by bad actors". It is unclear what the company means by that specifically, and why it is keeping the feature enabled for Twitter subscribers.
Here is what the change means for regular Twitter users, who use text messages as the two-factor authentication method. The feature works until March 20, 2023. The feature is disabled by Twitter on the deadline day automatically, making these accounts less secure than they were before. Twitter notes that associated phone numbers are not automatically removed from the accounts, but that users may do so in the settings.
How to set up two-factor authentication on Twitter
Twitter users who rely on two-factor authentication protection may want to disable the text message two-factor authentication option before March 20, 2023 to switch to another.
There are two alternatives available: authentication app or security key. Most may select authentication app, as they may not have access to a security key. Companies like Yubico have a range of security key products that Twitter users could use for that.
As for authentication apps, options include Google Authenticator, Microsoft Authenticator and Authy among many others.
Here is how you set up two-factor authentication on the site (website only, may be different in Twitter's mobile apps)
- Open the Twitter website and sign-in to the account.
- Select the three-dots menu and then Settings and Support > Settings and privacy.
- Select Security and account access > Security > Two-factor authentication.
- Select either Authentication app or Security key, depending on what is available or your preference.
- Follow the instructions to set up the feature. Note that this requires entering the Twitter password first to verify account ownership.
- If Authentication app is selected, it is necessary to link the app with the Twitter account by scanning a QR code and entering authentication code generated by the authentication app. This pairs the app with the account.
You may check out this support article on Twitter for detailed instructions.
Closing Words
Twitter is making the site deliberately less secure for non-Twitter Blue users who use text message two-factor authentication. While it is true that text messages are not secure for two-factor authentication, it is better than not using it at all.
Some may switch to another method, but there will likely also be users who won't enable another two-factor authentication method. The "abuse" argument by Twitter does not really make sense, as Twitter Blue users may continue to use text message authentication. It may have something to do with Twitter cutting costs everywhere to make the service profitable.
Now You: what is your take on this?



















my stupid Bank still uses SMS as 2FA..unbelievable, and they don’t seem to want to change any time soon.
Banks are the absolute worst at cybersecurity. You’d think with all of the money they handle they would make security a priority and yet they are so far behind everyone else.
Almost the only person in this world who “abuses” Twitter is its owner Elon Musk.
This has been so long overdue, but better late than never. Since Twitter has so many users I hope this starts a larger industry-wide push to phase out SMS-based 2FA altogether since it’s so wildly insecure:
https://krebsonsecurity.com/2021/03/can-we-stop-pretending-sms-is-secure-now/
Unlike SMS, authentication apps aren’t tied to your phone number which is a HUGE win for privacy and since some apps allow you to easily backup your private keys to other devices, 2FA using authentication apps are no longer “single-point of failure” where if you lose or damage your phone you won’t also be locked out of your accounts like you would be with SMS. It’s bad enough to lose your phone but also being unable to access your critical accounts at the same time is a double-whammy no one should have to deal with. SMS also requires a phone signal which isn’t always available or can be spotty at times, which is yet another downside of SMS.
My favorite authenticator app is Aegis Authenticator. It’s open-source, encrypted by default, and makes importing and backing up codes relatively painless.
https://getaegis.app/
+1
That’s not a “huge win” for privacy, as this was non-mandatory.
It’s a huge loss for anyone who loses the device with an authenticator app, whether by theft, natural disaster or simple misplacement.
Isn’t the blog you’ve linked the one that popularized the idea, that EV certificates are useless and browsers should stop displaying them, just because US is a comedic country in which two companies can have the same name?
Sorry, but in the [Editor: removed a word, replaced with “the”] world things are different and I’m not going to waste time reading about how insecure things are in US, as this 99% of the time doesn’t affect me.
@ridiculous
If you don’t care that the 2FA method you use is tied to your phone number, you do you.
A person who uses an app like Aegis which encrypts access to your authentication codes (by default) and allows for easy backups separated from the phone itself won’t suffer a “huge loss” in the event of phone damage or theft. Doubly so if the phone itself is also locked with encryption (that’s two layers of encryption).
You can install authentication apps on multiple devices to access your codes from more than one device simultaneously. You can’t do that with SMS since no two devices can have the same SIM to receive texts associated with one phone number.
@ridiculous
You can lose OTP access by sim without you knowing while you can block any account when you lost your auth device. Device with authenticator app also forces security setting to be enabled like pin or password.
Phone number is much more not secure, read the article above, if you don’t like the blog just search other information source. It’s been happening in real life not fiction.
Meanwhile your natural disaster case is fiction, I never heard anyone losing their device with authenticator app. Let’s be a realist kay?
+1
Aegis Authenticator may be not as fancy as others but is less troublesome than Authy (if correctly configured and backed up)