The Hidden Threat: 1Password Password Manager Phishing Ads on Google
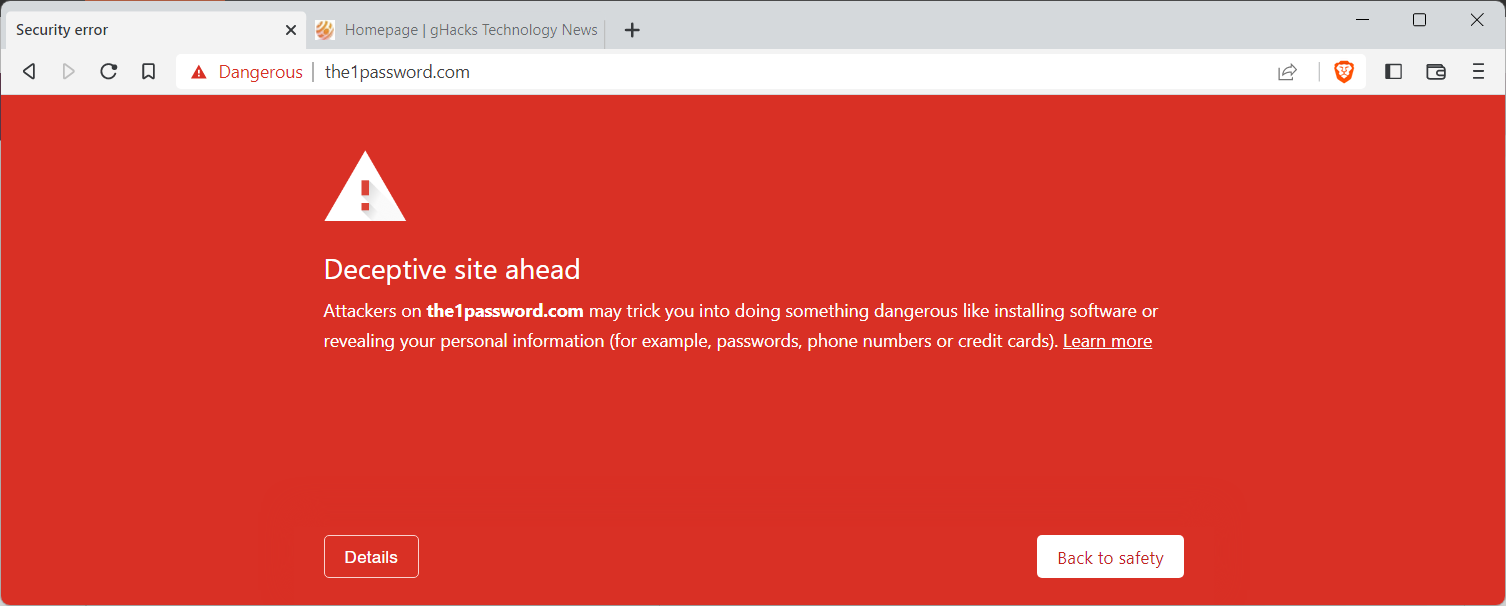
The popular 1Password service is the latest cloud-based password manager that is being targeted by scammers. Like the recently reported Bitwarden scam, new and existing users of 1Password are targeted through malicious ads on Google Search.
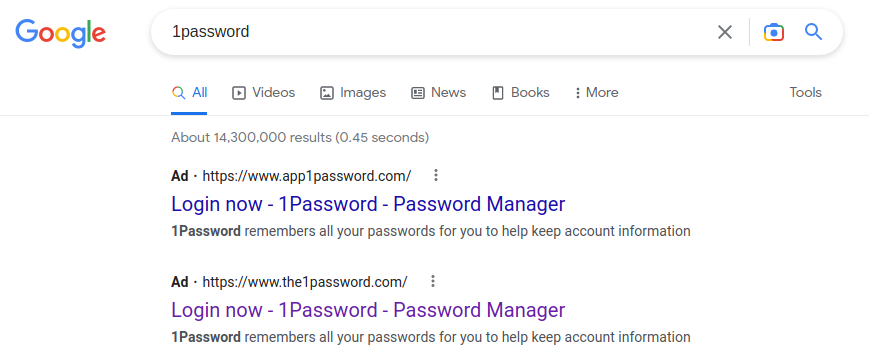
First spotted by Twitter user MalwareHunterTeam, advertisement for two 1Password phishing sites were running for a period of time on Google Search. Both ads used the same title, "Login now - 1 Password - Password Manager" and had the same description as well, "1Password remembers all your password for you to help keep account information".
It is interesting to note that title and descriptions are not identical to the ones used by the official 1Password website. The title is different entirely, and the phishers have removed the first sentence of the description and just used the second for the ads.
The phishing ads pointed to different websites, both of which had 1password in the url. Google Safe Browsing is detecting them as threats already and it seems that the two ads have disappeared from Google Search. The phishing websites are no longer available either anymore, but there is a strong possibility that they will make a comeback on new domain names that have not been burned yet.
The phishing websites displayed login prompts that looked identical to the login prompt on the official 1Password site. Cloud-based password managers support web sign-ins, so that their customers may access all passwords online without need for an application or desktop program.
The phishing site requested the user's email address, password and the secret key. 1Password is one of the few password management services that makes use of a secret key. The key is only available locally and known to the user, which improves security of the password database significantly. Even if a malicious actor would gain access to 1Password servers, they could not decrypt the data without the secret key. This is different from other password managers, e.g., LastPass, which had a break in last year.
1Password account recovery
1Password users who entered their login data on one of the phishing websites need to act immediately. First step is to change the password and regenerate the secret key. The company explains the steps required to do so on this support page. Note that the threat actor may have done the same if the data was entered on the phishing site.
The official 1Password website is https://1password.com/.
Password Phishing on today's Internet
Phishing is still a major threat on today's Internet. Threat actors started to expand attacks from being purely email based to other forms of communication. Advertisement is a prime candidate, as ads are usually shown above any website in the search results. Many Internet users trust search results and especially the first result of a search.
Password managers are lucrative targets. Most phishing campaigns targeted a specific service, e.g., a Google, Amazon or PayPal account. With password managers, they'd obtain login data for all sites that a user stored in the password manager. All data unlocks with just a single authentication.
All cloud-based password managers are endangered by phishing attacks and other scams. Once username and password have been entered on a phishing site, attackers may use the information to sign-in on the official site of the password manager to unlock a user's entire vault.
Many cloud-based password managers support saving other data, including credit card information or social security numbers in customer vaults. This information falls into the hands of the attacker as well, unless additional security precautions have been taken.
As Ashwin mentioned in his article on the Bitwarden scam, local password managers like KeePass do not face that danger. It does not mean that they are not attacked, but they are protected against phishing scams and other cloud-based attacks at the very least.
Internet users who use password managers that are cloud-based may want to save the official site of their password manager to their browser's bookmarks. New users can't do that, but they should never click on advertisement that promises to take them to the password manager's website.
Instead, they need to check the first organic search result. Some search engines, Google specifically, may display lots of ads, so that the first organic result may be below the fold, meaning that users need to scroll to get there.
Cloud-based password manager customers should also consider adding a second layer of authentication to the sign-in process. While that won't stop all phishing, as phishers may create sophisticated site-copies that prompt for a verification code as well, it stops most.



















This wouldn’t be an issue if Google hadn’t decided it’s okay to make ads look like actual search results, but that’s a discussion for another day.
Keepass is what I use. I download updates when Keepass says there is an update. I make 3 backups. 2 on external HDD’s,1 on a USB stick and my master password is stored on the same HDD’s and usb stick.
I used Qwant lite for my first download and the
updates.
Backups are done with Karens Replicator to the HDD’s and usb stick, and after that I disconnect all of them from my desktop. It certainly is not foolproof, but so far it works for me.
You store your master password on the same devices you use to back up your password database ?
Unless they are encrypted themselves, anyone stealing them could access your passwords.
1- Always download software from the developer’s Website.
2- Have powerful OS and browser anti-ad, anti-tracker, anti-malware intalled.
3- Block browser connections to 3rd-party sites.
4- Avoid web search on major search engines. Alternatives exist.
Concerning Google Search, a company hosting rotten links via advertisement (hence “malvertisement”), not sure what keeps anyone from avoiding it.
Why would anyone want to use a cloud based password service: it’s just asking for trouble. I use Keepass which is wholly local and doesn’t require an Internet connection other than to download an update.
@TelV
As long as you have a good backup policy that’s the way to go.
Problem is if you don’t and lose your drive with Keepass on it.
If you follow the 3-2-1 backup rule, then you need to keep a copy offsite. That in itself brings issues. Where do you put that copy? How often will/can you update it? Is the place your keeping it safe? Are the people your keeping it with trustworthy?
This is why many people like myself use an online password manager and keep offline copies just in case.
You could always use cloud services to backup your Keepass db and encrypt it but then we’re more or less in the same spot as using an online password manager.
Nobody has different needs to me so everything I do is always the best way for everybody else too.
If you download Password Manager from Google search, you will get scammed on something.