Google Chrome 108 adds support for Passkeys on Windows, macOS and Android
Google Chrome 108 was released to the stable channel last week. It added support for a new way to sign in to online accounts, passwordless logins, aka Passkeys.

Google Chrome adds support for Passkeys
The name might seem familiar to you if you read my article about macOS 13 Ventura. Apple Safari in iOS 16, iPadOS 16 and macOS 13 was the first browser to add support for Passkeys.
What are Passkeys? Passkeys are a secure login method, that was developed by the FIDO Alliance and World Wide Web Consortium (W3C), which includes the giants of Silicon Valley like Apple, Google and Microsoft.
What's the need for it? Regular passwords can be phished, leaked, stolen or brute forced if the passphrase is weak. Passkeys sidestep these issues completely, there is nothing to be guessed, leaked or stolen. The Passkeys are stored on the user's device in an encrypted form that can only be accessed with biometric data such as FaceID, fingerprint ID, Windows Hello, PIN, etc. The Passkey on the user's device is referred to as a private key. This is used in tandem with a public key (username) stored on a website's login system.
If a user has saved their account credentials as a Passkey, and they try to log in to the website that the account belongs to, the server's public key asks the user to provide the Passkey associated with their account. This is done by approving the login, by using the computer or mobile phone's fingerprint scanner, camera (FaceID), or the PIN code used to unlock the screen. The device scans the encrypted Passkey data that is stored locally, and tells the server to approve the login request. In other words, your Passkey never leaves your device. You may sync Passkeys across devices, this depends on the app and OS that you use.
Intrigued by the new security feature? You can start using Passkeys in Chrome on websites that support it. That's the issue, very few sites have adopted the new protocol. This Passkey directory page (owned by 1Password) has a list of services that support the new protocol, these include PayPal, BestBuy, eBay, Microsoft, NVIDIA, etc.
How to use Passkeys in Google Chrome
1. Open Google Chrome on your Android phone. You need to have password saving and syncing enabled in the app.
2. Go to a website that supports Passkeys. e.g. You can try it on this demo site https://webauthn.io/
3. Create a new ID.
Note: If you are testing this with another site, you should sign in to your account and change the login type.
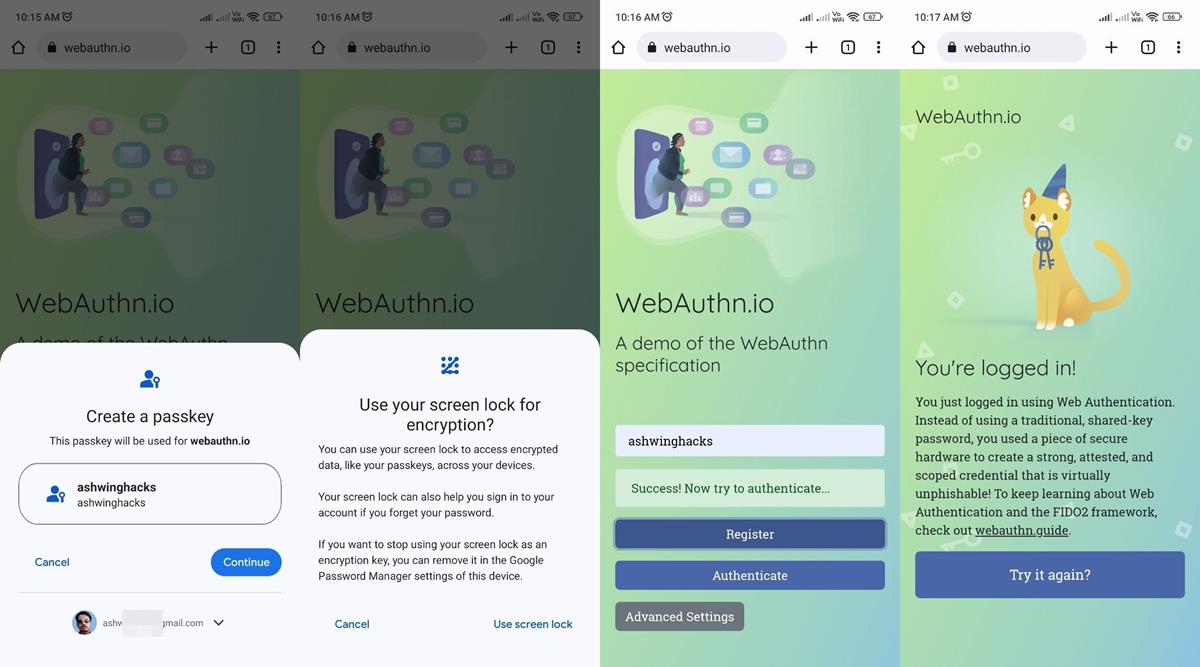
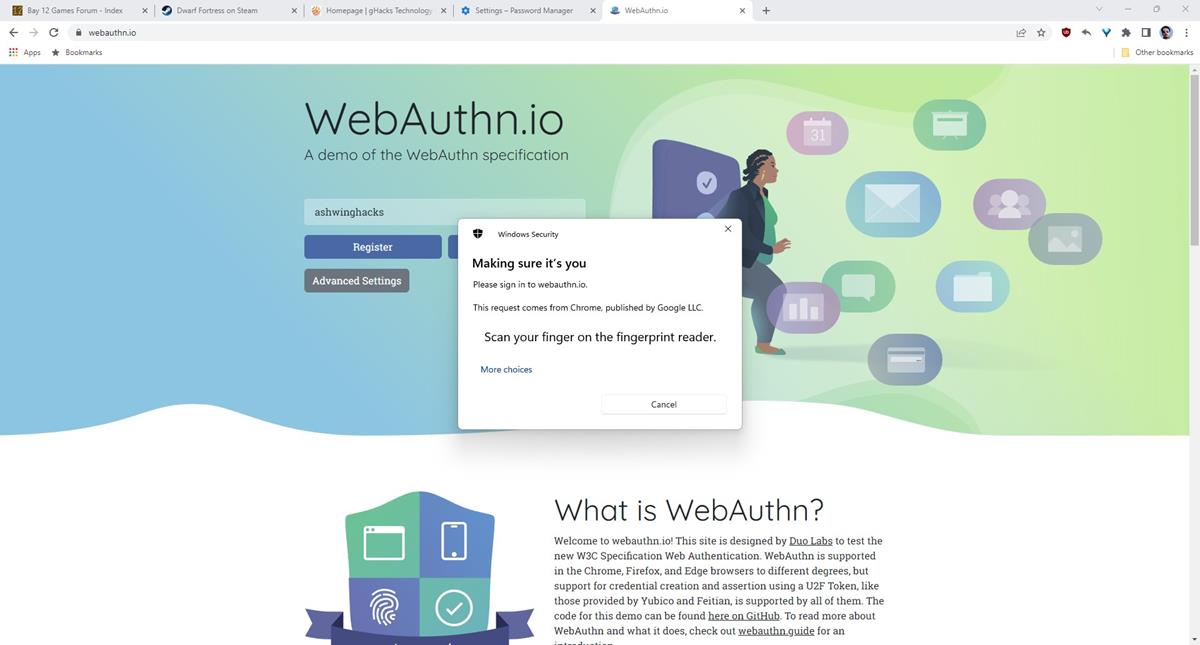
4. Chrome will offer to save the site as a Passkey. (refer to the first image in this article)
5. Select yes, and it will prompt you whether you'd like to use your mobile device's screen lock as the Passkey.
6. Accept it, and confirm your fingerprint ID or PIN.
7. Now, open Chrome on your Windows or Mac computer, and go to the same site.
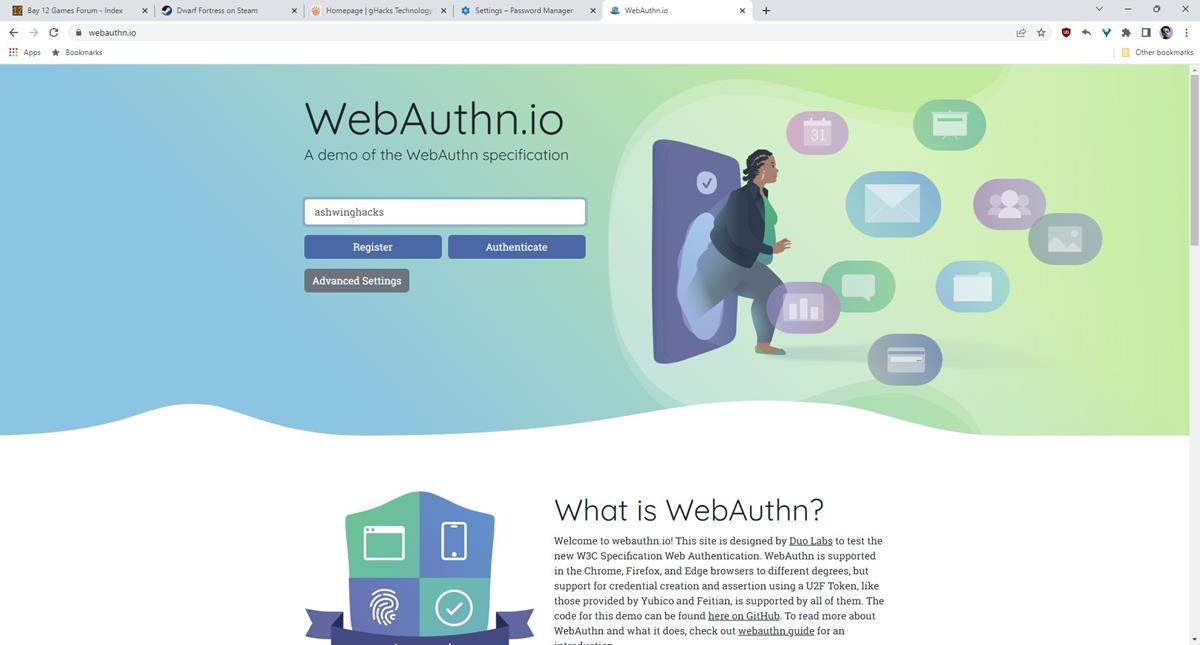
8. Try to log in to your account, and authenticate your profile. The site will display a panel that asks you to use your Passkey.
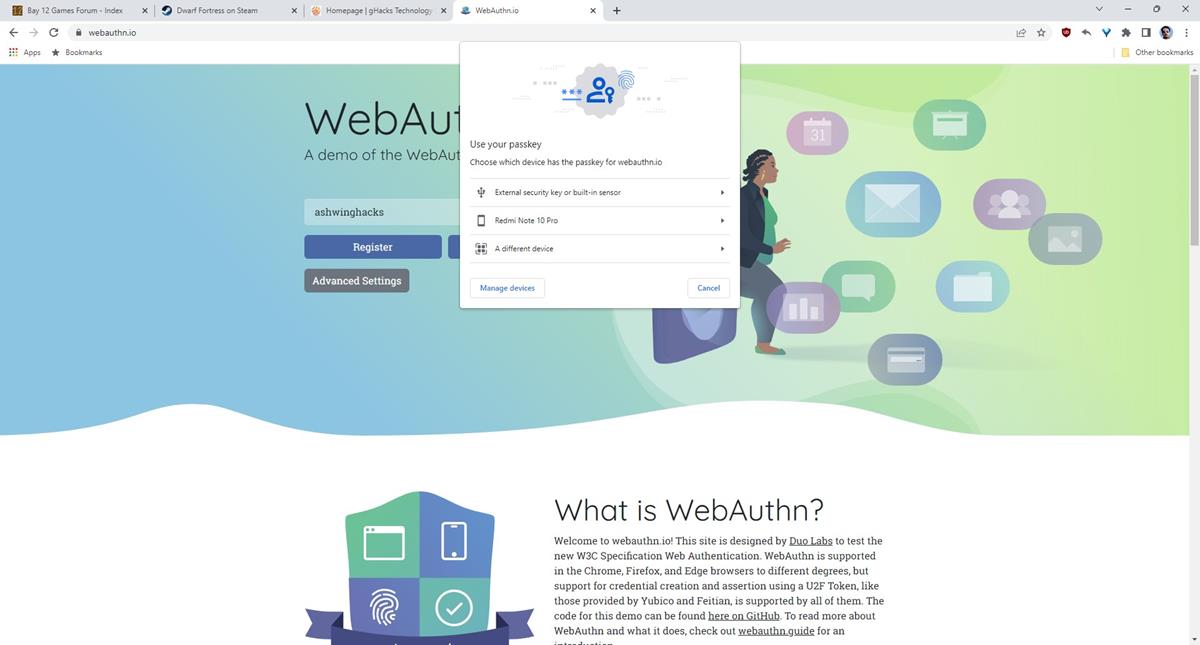
9. Select the device's name that has the Passkey stored in it, and you should see a notification from the Chrome mobile app.
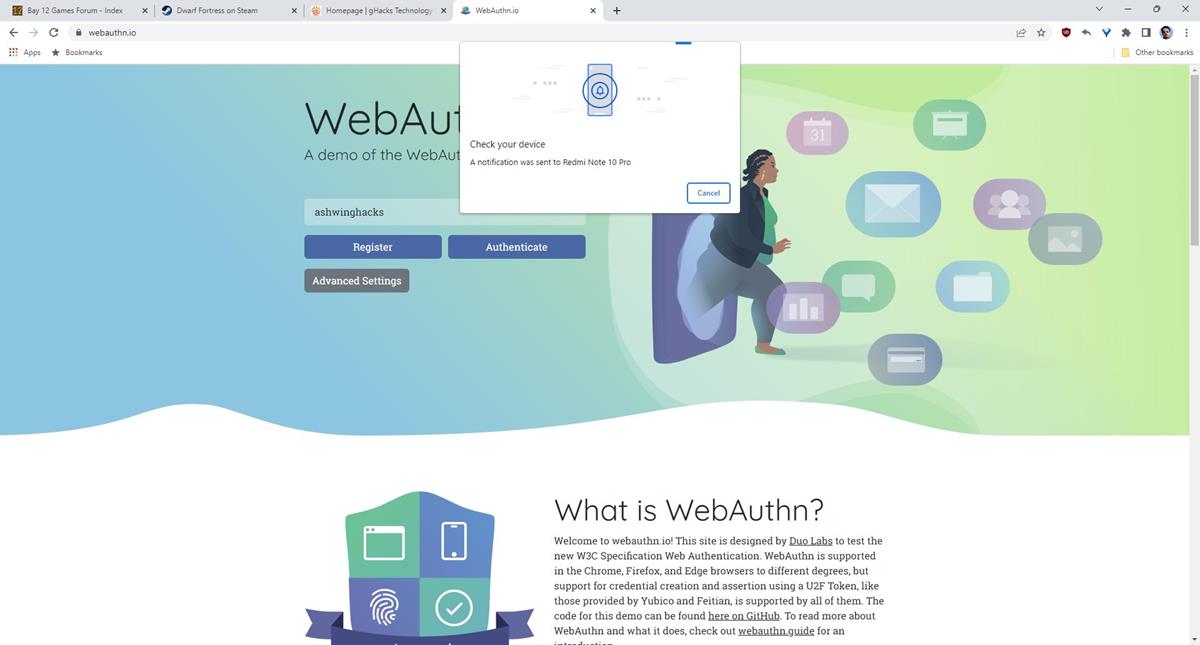
It will request to turn on Bluetooth on your phone to connect to your computer. Once that is done, it will display a prompt to unlock the screen.
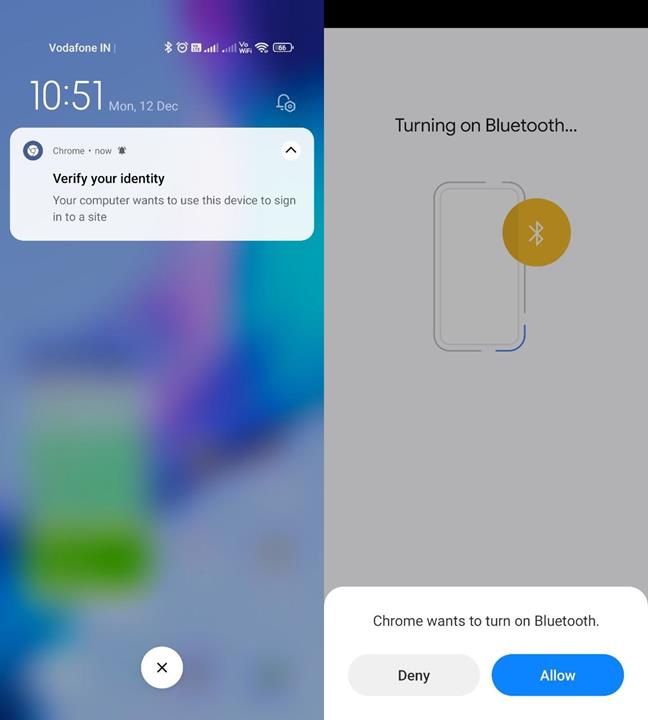
10. Approve the login request with your screen lock code or fingerprint or Face ID.
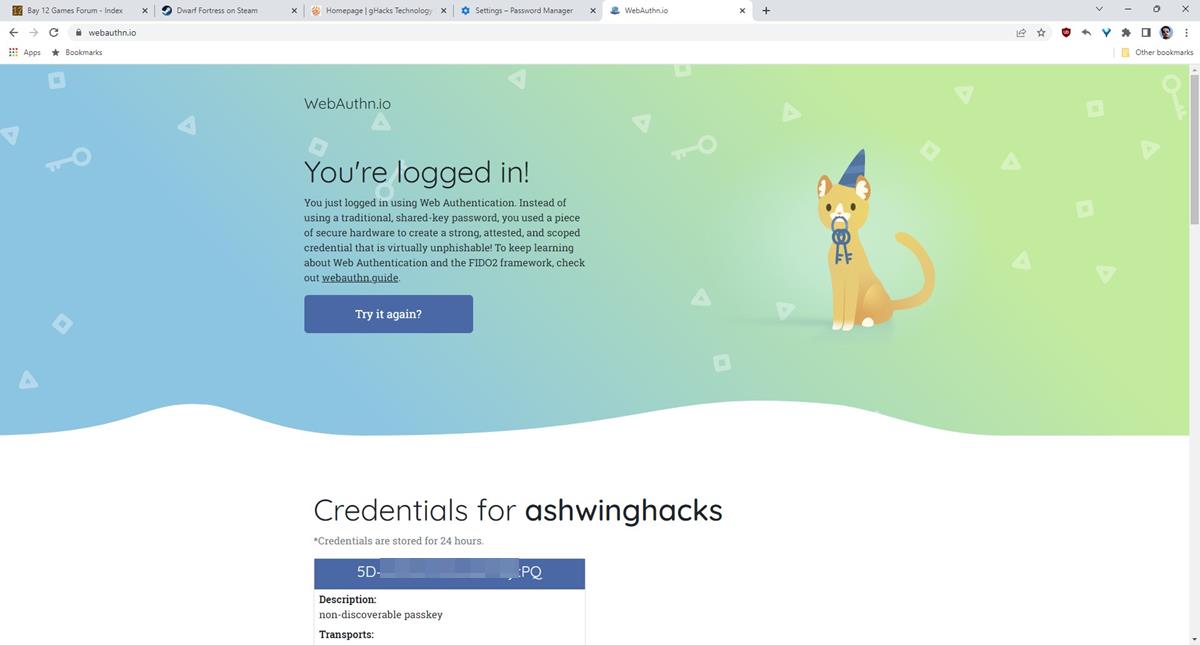
This is how Passkey's passwordless system works. You may also use your mobile phone to scan a QR code to sign in using the Passkey, though the process is a little different.
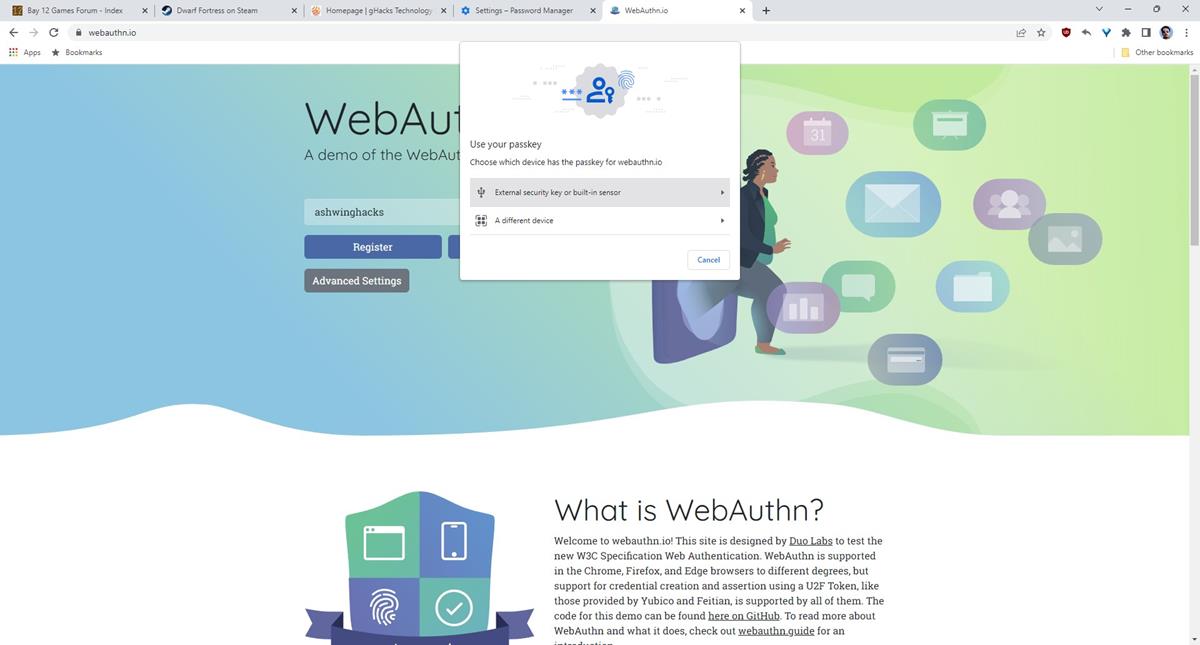
If you select use another device, the site displays the QR code.
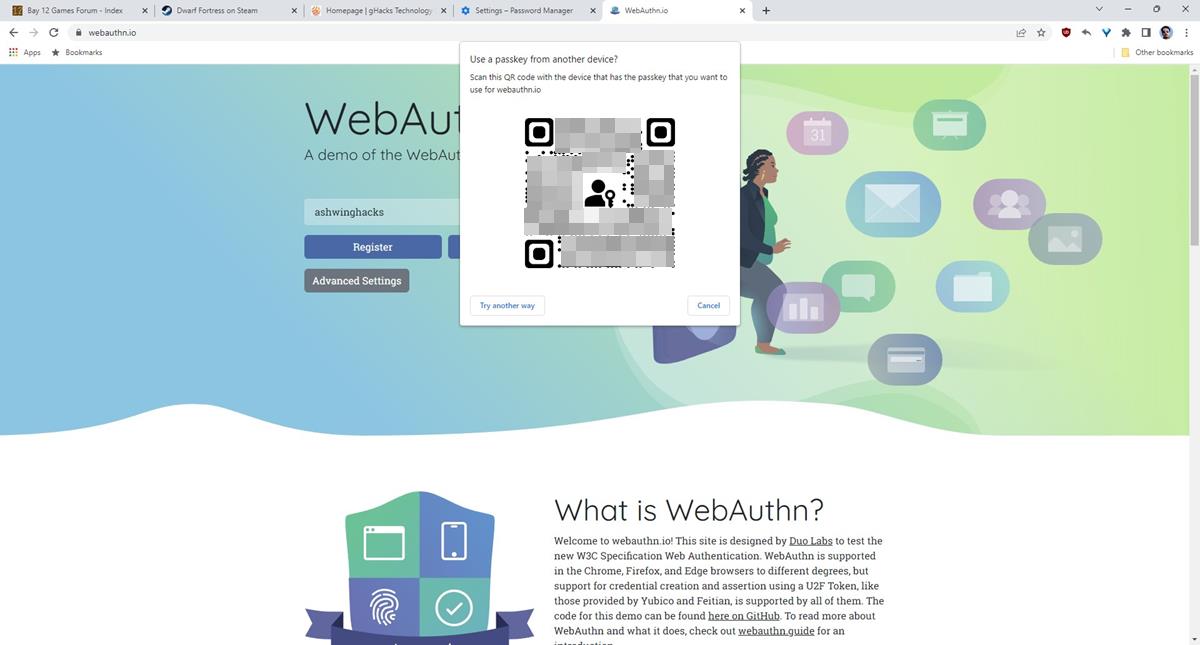
Scan it with any camera app that supports QR, and you should see a URL that begins with FIDO:/ followed by a long numerical string. Tap the open button, and Chrome will start the authentication process using (step 9 above) Bluetooth. Though it sounds complicated, the whole process only takes a few seconds to complete.
In addition to this, Passkeys also supports hardware security keys such as Yubikey USB devices, so you should be able to use it with any FIDO supported device. I have not tested this method.
Some services that support Passkeys don't allow it to be used directly, and instead rely on two-factor authentication. Microsoft is probably the best example for this. You can switch your regular account to a "passwordless account", and it will use your Windows Hello PIN or Fingerprint ID to access the account. This doesn't log you in though, it sends a notification to the Microsoft Authenticator app on your mobile phone, which you have to approve manually. This is sort of like the 2-step verification that you get on your phone when you try to log in to your Google account, and it asks you to approve the request.
Passkeys in Google Chrome
macOS syncs your Passkeys between your devices using iCloud Keychain. Chrome on iOS and iPadOS follows the same pattern, but this doesn't support macOS, instead it saves it in a local profile. Chrome uses Windows Hello to store the Passkeys, and doesn't support syncing with other devices. Users will have to rely on their mobile phone that has the Passkey to scan a QR Code and approve the login request. Once they do this, the Windows computer stores the data in Windows Hello, and this is used for subsequent logins. Coming to Google's own OS, Chrome on Android stores Passkeys in the Google Password Manager, and are synced between devices that have the app.
Chrome supports Passkeys on Android, iOS, iPadOS, macOS and Windows. The chart says that Linux is not supported. I think it only means that Passkeys cannot be created/stored on Linux computers, so it should still allow you to sign in using your mobile phone by scanning a QR Code.
You can manage your Passkeys from Chrome's autofill section on Windows, macOS and Android. Google's announcement mentions that future versions of Chrome on Android will allow third-party password managers that support Passkeys to be used for autofill. Please refer to the FAQ on FIDO's website to learn more about Passkeys.
Passkeys may be a little inconvenient to use compared to autofill, but that's a small price to pay for better security.
Have you tried Passkeys?




















Vendor locking the sheep in denial and storing their passwords on remote servers which they eventually wont be able to access or invoke directly without a passkey, what could go wrong?
In retrospective, passwords are still the ideal solution, especially with 2-factor authentication and so many identity services already (you can login into many sites using your single google, facebook, github account and any login attempt not confirmed with 2fa would be rejected).
“Passkeys are a secure login method, that was developed by the FIDO Alliance and World Wide Web Consortium (W3C), which includes the giants of Silicon Valley like Apple, Google and Microsoft.”
No thank you. Anything by these fools always have some hidden agenda behind it.
W11 is like a war, it never ends too fast, it never is too short and it never leaves you good feeling. Thanks @Ashwin for the articke. :]
So your phone (which can be damaged, lost, or stolen) becomes a single point of failure?
What could go wrong? ;)
Passkeys sync between multiple devices, therefore you may still have another device (like a laptop) you can log into and recover from.
If you only have a single device, or both your laptop and phone were lost/stolen/damaged at the same time, then you will need to fall back to whatever recovery mechanisms the vendor (Apple/Google/Microsoft) uses, such as recovery passwords, etc..
Recovery passwords take about 5 business days to provide help. Good luck with that. If in an unfortunate situation you lose your phone and you’re away from your laptop, you may as well kiss and make out with devil than hope for something from Google, etc.
So you’ll need a phone now in order to sign in to a website when on your computer? Hmmm nah, I don’t wanna.
Although that’s how Google word it, I sincerely hope it’s not a restriction that is applied.
Many people do not have (or want) a smartphone and many people are not allowed phones in certain facilities (such as government, research, etc.).
>Chrome supports Passkeys on Android, iOS, iPadOS, macOS and Windows.
I wonder why in the article it is not mentioned anywhere that, according to Google itself, passkeys are only supported in Windows 11, in other news sites (Ars Technica for example) this is mentioned as one of the big flaws of this authentication system, I mean, Windows 10 is the most widely used desktop OS in the world (and will be for many years to come), so the fact that these passkeys are not supported on that OS is going to significantly delay its adoption.
I’m not sure if this is Google’s or Microsoft’s fault, I think this restriction was imposed by Microsoft who wants to promote the adoption of Windows 11 at all costs, but I don’t think many users will switch to Windows 11 simply to be able to use passkeys, on the other hand, the fact that it is not supported in Windows 10 will delay its adoption.
Absolutely.
Windows 11 market share is only around 15% and not growing very fast. Restricting it to Windows 11 will unquestionably hamper adoption.
I can understand the requirement for a TPM module in order to securely store the Passkey private keys on the local machine (which some Windows 10 machines may not have), however TPMs, Secure Boot, etc. have been around a long time now and therefore there’s no physical reason why a lot of Windows 10 machines could not use Passkeys.
Intel 5th Gen Broadwell machines came out before Windows 10 was released and many of those machines (especially business-orientated machines like Intel/HP/Dell) had TPM 2.0 modules either via a chip or via Intel Platform Trust Technology (PTT) built into the firmware. These machines have already been able to use FIDO2 for years now, so there’s no reason why they would not be able to use multi-device FIDO credentials (Passkeys) too.
In addition, even if a Windows 10 machine may not necessarily have the required hardware requirements, such as a TPM module or Secure Boot, there’s no reason why hardware security keys such as YubiKeys could not support Passkeys in the future via USB if Windows 10 supported it – like they currently do with FIDO2.
Microsoft prioritising profit over user security will surely backfire. What could have been a huge step forward in securing users from password and phishing attacks using a universal platform-independent standard, is now pretty much a damp squib for those who use Windows 10 day to day (I.E. most people).
If I recall correctly, the Apple documentation also has some hardware restrictions and mention they require biometrics (Touch ID or Face ID), which may also hamper adoption. However, I’ve recently seen someone say that they were able to use Passkeys on an M1 Mac Mini without biometrics. As I don’t have one to try I’m not sure of the details, but I’m guessing despite the documentation, Apple also allows authentication via an alphanumeric PIN – like you can with Windows Hello – to authenticate to the TPM/Secure Enclave.
Its only supported on the latest MacOS which many many Macs cant run. Both Apple and Microsoft have made sure that this important Security standard is a decade away from widespread adoption.