Mozilla is rolling out Total Cookie Protection to more Firefox users
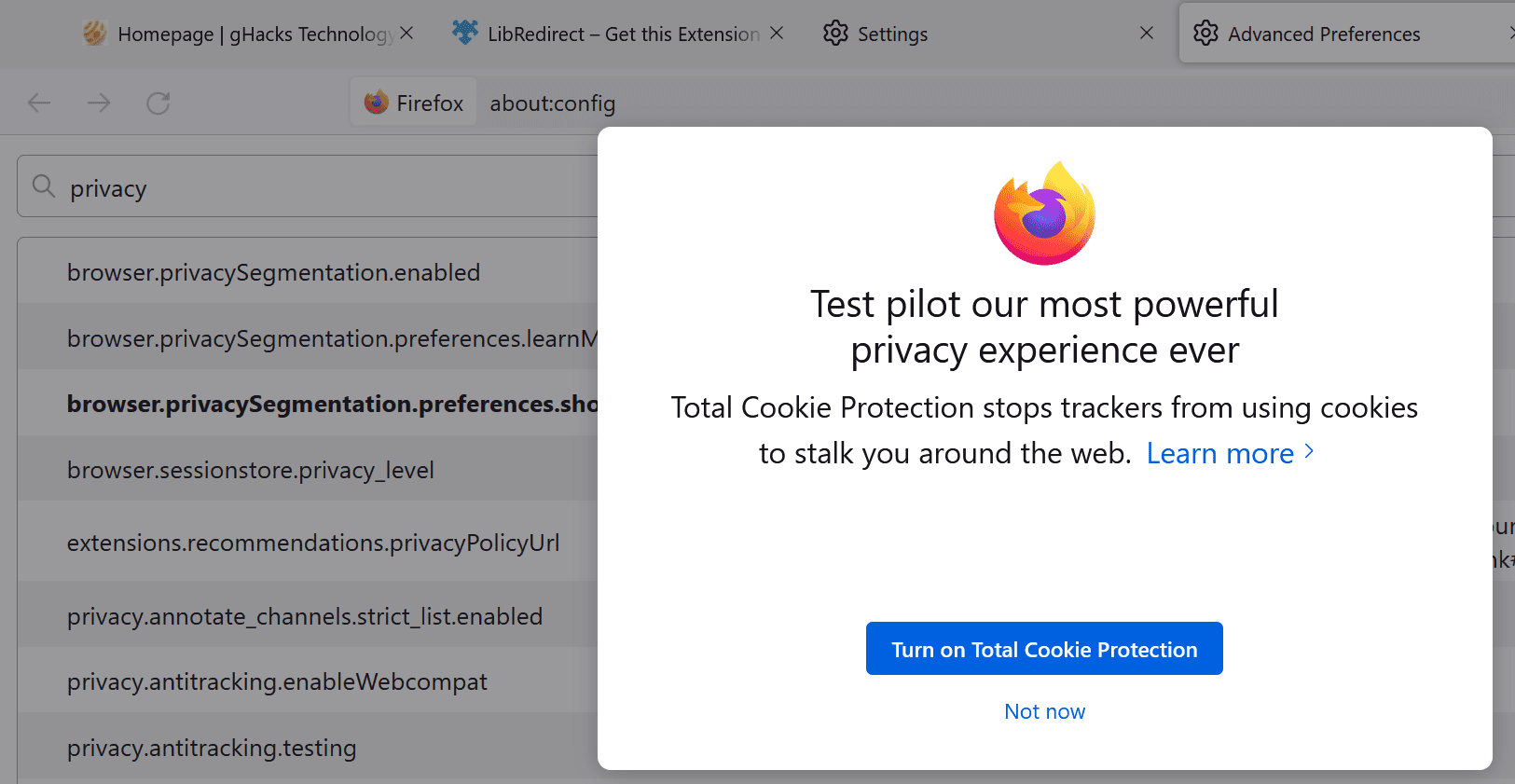
Firefox users may receive a prompt on startup of the web browser that gives them an option to enable the browser's Total Cookie Protection feature.
Total Cookie Protection separates cookies in the browser so that only the site that planted it in the browser has access to it. The protective feature limits cross-site tracking in the Firefox web browser. Some sites and services require third-party cookies to work properly; these providers get automatic permission to use cross-site cookies when Total Cookie Protection detects that a Firefox user intends to use that provider.
Mozilla describes Total Cookie Protection in the following way:
Total Cookie Protection builds a fence around cookies, limiting them to the site you're on so third parties can't use those same tracking beacons to follow you from one site to the next. For example, if you visit socialnetwork.example, the site won’t be able to view your activity on shopping.example, healthinsurance.example, or your cousin’s cooking blog later.
First introduced in Firefox 86 Stable, released in February 2021, Total Cookie Protection has been restricted to Firefox's strict tracking protection feature. Mozilla enabled the feature in Firefox 89 for the browser's private browsing mode.
The roll out in Firefox brings the feature to the default tracking protection configuration in the browser when enabled. Firefox users who get the prompt in the browser may activate the "turn on Total Cookie Protection" button to add the protective feature to the browser.
When they do that, a new checkbox appears in the privacy settings to toggle the functionality.
Total Cookie Protection is in early access currently according to Mozilla. No additional data is collected when the feature is enabled. Mozilla states that the rollout helps the organization improve the feature before it is enabled by default for all users of the web browser in a future version.
Firefox users may activate the Shield icon on sites with broken functionality, after enabling Total Cookie Protection, to turn off the feature for the site and optionally inform Mozilla about that.
Firefox users who do not get the prompt or the setting in the browser may set the preference browser.privacySegmentation.preferences.show to TRUE on about:config to display it in the browser. According to Mozilla, it may also be possible to enable this by setting network.cookie.cookieBehavior to 5 on about:config. Others may prefer to enable the Strict privacy setting, as it includes the new functionality already.
How does it differ from blocking third-party cookies outright? If you enable the setting, sites are blocked from setting third-party cookies; this may break some site functionality, unless exceptions are set. Total Cookie Protection allows the setting of third-party cookies, but it restricts access to these cookies.
Mozilla has yet to reveal when the feature will become available as a default for all users of the web browser.
Now You: what is your take on Total Cookie Protection?
Why had not this been implemented, like, 5-10 years ago? I mean, I am no expert, but this solution to tracking seems pretty obvious and not too hard to implement, an I right?
Google has already set plans in motion to counter this:
https://www.ghacks.net/2022/05/23/brave-joins-mozilla-in-declaring-googles-first-party-sets-feature-harmful-to-privacy/
Plus, tracking networks putting local files into your browser that can either be isolated or deleted has no future for obvious reasons: This is going the way of the dodo because you have way too much influence over these files! Stateless tracking is where it’s at these days, e.g. fingerprinting. If an adversary needs to put local files into your browser in order to track you in 2022, this means that said adversary is not using state of the art forms of tracking. Sorry to say.
bet it won’t work with ubisoft’s websites. that monstrosity uses 100 different address (eg… a.c.com, a.ci.com, etc) for different parts of its sites. fucking stupid.
Smartblock is there for exact reason you mentioned.
You left out how exactly this works?
Somehow FF builds a DB of what ip can access what data stored on my pc?
Perhaps as is more common, a cloud based service is used?
It is limiting access to cookies based on the sites you visit; this is automated, no need for looking up information in a database or cloud service.
Ok, more simple.
How does FF decide wether or not to allow site B to access the cookie from site A?
… “based on sites you visist” says nothing. PC’s work on 1s and 0s, they need data to perform functions. What data is used and where is it?
@Tachy, to access and to set a cookie of its own to start with.
With Total Cookie Protection ( “browser.contentblocking.category” = “strict” and “network.cookie.cookieBehavior” = 5) visiting a site which calls an embedded Dailymotion video will allow Dailymotion to set its cookie and lay its data in the user’s IndexedDB folder, for instance [ https+++www.dailymotion.com^partitionKey=%28https%2Clcp.fr%29 ], and this partitionKey instructed permission is not removable with an extension such as ‘Cookie Autodelete’.
This occurred in the past with YouTube which apparently had abandoned this practice and which is why in my above comments I have first denounced this feature before retracting myself on the grounds my past YouTube experience had become obsolete… unaware that other domains (such as DailyMotion) could behave the same.
Why does a 3rd-party site have the possibility of setting its cookie?
It’s all explained here : [ https://developer.mozilla.org/en-US/docs/Web/Privacy/State_Partitioning#storage_access_api ] :
“If a third-party iframe is granted storage access to the parent context, Firefox sets a permission. To revoke access you can clear the permission via the Site Information Panel in the permissions section under “Cross-site Cookies”.
I have never found this permission via the Site Information Panel in the permissions section under “Cross-site Cookies”. Where is it?
I’ve tried all that is mentioned on that page, including blocking heuristic permissions : nothing does it, DailyMotion continues to lay its cookie and IndexedDB data.
I read this data is isolated. That participates to your question but not to the fact of First-Party tracking : DailyMotion may be the only domain to have access to its data uploaded to the user’s profile it remains nevertheless that the user will be tracked by DailyMotion on each site calling DailyMotion, tracked for the session if the cookie is session-only but tracked trans-session if the user has allowed cookies for DailyMotion. The user may wish for instance that only DailyMotion cookies be kept but not its IndexedDB data, and that’s where an extension such as ‘Cookie Autodelete’ comes in action, but with such ‘partitionKey’ permissions nothing, no extension can wipe it.
On the contrary, First-party Isolation does everything Total Cookie protection does and even more at this time : with the above example DailyMotion when accessed as 3rd-party, cannot upload ANYTHING. And that’s what I want, personally.
So I can read and hear all the reported magnificence of ‘Total Cookie Protection’, as far as I’m concerned I’ll adopt it only when, if it handles a sixth cookie behavior option : 6=Isolate cookes (like ‘5) AND block ALL third-party cookies. Not before.
This is a bit late but okay commenting(is that a word?) anyway. In some sites, aka government ones or college related, you get a different icon right next to padlock in address toolbar which indicates cross-site cookies are allowed. Icon is bit similar to DRM icon, I clicked on it thinking why this site needs DRM but it was cross site cookie icon. Cross site cookies were allowed on that site but then it was because both sites had same base domain. ETP strict was the setting at that time.
In one site which I forgot, I got a prompt asking to allow cookies. I did and then after clicking on the same icon next to padlock, there was an option to remove cross site cookies. After which it said this page may need a refresh for proper behaviour.
Maybe try it with new profile. At the end it depends on site which are very hard to find, which are allowed cross site cookies under TCP.
@Yash, thanks to RSS feeds I don’t miss your comment.
Because I have heavily tweaked Firefox, including the GUI, including what appears or not in the urlbar, I have disabled all about:config and CSS that could interfere in the correct display of native Firefox functionalities. Nothing did it. I checked every button in the urlbar when visiting [lcp.fr] above mentioned, itself calling embedded Dailymotion videos : nothing did it, I never found the “Cross-site Cookie” reference which should have allowed me theoretically to remove rights for Dailymotion iframe cookie.
All I can still try is open a new profile. Easy but I’m really not motivated at this time knowing that even should it handle correctly denying a given cross-site cookie I’d still wouldn’t be convinced by the Total Cookie Protection approach.
At the end all this is complicated, IMO. With ‘First-Party Isolation’ everything is clear. My opinion is that ‘Total Cookie protection’ is either a blend of good will and a keyhole for corporation tracking, either a non-finished product. Seems to me Firefox developers would have made a better choice by elaborating the ‘First-party Isolation’ than trying to develop a hybrid complexity understood by practically no one.
If future versions of Firefox remove this ‘First-Party Isolation’ I’m likely to abandon Firefox. There is too much of hesitations at Mozilla in the strategy to adopt when split between idealism and realities as conceived by them.
The thing with FPI and dFPI/TCP is both have different approach but end result is nearly same yet there is a noticeable difference.
FPI is all or nothing approach. Same is for 3rd party cookies. You visit a site, if a functionality is broken because of FPI you can’t do anything. And if a site needs 3rd party cookie either you allow it which then allows all cookies or you don’t. Simple but ineffective because a) Step up from no FPI to FPI and vice versa is massive and even the most privacy conscious users get frustrated because site is not working and you can’t do much about it apart from creating a new profile without FPI. But then you don’t have any protections at all.
b) In case of 3rd party cookies, if site needs one you need to allow everything, inviting tracking from not only a specific domain cookie which site truly needs but other unwanted domain cookies as well.
In dFPI you get all the protections of FPI. So if site A needs something say 3rd party login for example, either you don’t do anything, maintaining FPI level privacy. However if you really need it you don’t need to create a new profile with no protections. You only need to click on 3rd party login which will create exception for that 3rd party service only on that particular site. In a different site B if you don’t want that site to access 3rd party login from site A, you don’t click on 3rd party login and site B remains untouched aka FPI level privacy on site B.
In dFPI IMO cookies are handled in a better way. So if you need a cookie there will be prompt. You’re not allowing all domain cookies but rather only a specific domain cookie in that prompt.
Plus in my example when cross-site cookies were allowed, site had same base domain and there was an option to revoke the permission. If I had disabled 3rd party cookies I would have to allow all cookies from every domain. With TCP only same base domain cookies were allowed which is not a privacy violation.
I also have a profile which is modified albeit not at same extent as yours. I have FPI enabled with 3rd party cookies disabled. But over time I’ve visited several websites which gets broken due to FPI and 3rd party cookies disabled. For those sites I used to create a new profile with no protections and then after visiting them everything is deleted. Few days ago I needed to fill a form(govt. thing) and so you don’t have much option. You don’t want site functionality broken. So I created a new profile quickly but this time I set ETP to strict. To my surprise no site functionality was broken. Cross site cookies allowed were of same base domain with a prompt for different base domain cookie. I would say that’s as effective as 3rd party cookies disabled. Biggest surprise was flexibility of TCP. Even in Brave browser I used to enable 3rd party cookies. Now not anymore with ETP strict.
Still I’m sticking to FPI but there is now one more reason to atleast consider dFPI.
@Yash, thanks for sharing an instructive explanation. I understand.
I guess as always one’s opinion is double : relatively to ourselves, relatively to the pertinence, the legitimacy on a global approach.
Personally I’ve encountered only once an issue with FPI-block 3d-party cookies in that a medical site called another for displaying x-rays and that the latter needed access to former’s cookies. Indeed in that case dFPI would have made it.
My workaround for a 3rd-party cookies issue is a userChromeJS toolbar button I’ve created that switches the “network.cookie.cookieBehavior” value from 1 (block 3d-party cookies) to Block-All (=2) to Block-None (=0) which allows flexibility. But that won’t handle a siteB’s access to a SiteA’s cookies : for that indeed FPI with it’s all-or-nothing as you say is far less pertinent than dFPI as I understand it.
What I either misunderstand or legitimately disagree with is dFPI’s easiness to set permissions for 3rd-party iframes :
“If a third-party iframe is granted storage access to the parent context, Firefox sets a permission. To revoke access you can clear the permission via the Site Information Panel in the permissions section under “Cross-site Cookies”.
I do not understand why a site delivering an embedded video is granted storage permission : I-do-not-understand :=)
Now that’s when the “cross-site cookie” user-input permission is supposed to be able to revoke that permission. OK, but I’ll have to find it, hence create a new profile then try to find the culprit within my dozens of Firefox Autoconfig and Group Policies I’ve set over time, always carefully but obviously one/one+ is blocking.
Listen, I understand your explanation, clear, logical, pertinent. If I manage to find the culprit among my settings which prevents the access to “cross-site” cookies, I’ll give a thorough try to dFPI and TCP. Maybe then will I be enthusiast (that happens in life which means : try, always try.).
Remains that you end your comment by stating that whatever the pros and cons of FPI and dFPI, you stick to the former. The difference with me is that I haven’t experienced dFPI, hence your choice is somewhat more legitimate if I may say :=)
We’re far, need to say, from the era of our first browsers, aren’t we? …
I think biggest problem came for Mozilla in 2008 not in the form of Chrome but smartphone adoption. More and more folks started using it and biggest issue about smartphones was/still is they’ve removed the line separating convenience and more customisable software. So due to increased smartphone adoption users got used to few options and they started to expect that from desktops as well. This approach took Windows to where it is now.
It left Firefox wondering what it should do – make things easy for new audience and yet simultaneously having more advance options for its core users. Unfortunately as we see in society it is not about which idea is best or which approach is better, it becomes which one is being adopted quickly.
In an ideal world Firefox would burn everything to ground and start everything up again with smartphone users as the main focus. But it is not possible because it has a core audience. This then forces Mozilla to do something different, making sure you have options for core users and some users who will explore more options and yet having the simplicity for those users who only care about simple approach.
This is visible in TCP. Firefox has the most advance option in FPI but it doesn’t have better adoption. Not because it is hidden away in about:config, but because many users will dump it at first sight of broken site. So they bring TCP, flexible but as with every decision it marginalises advance users.
I don’t think FPI is getting abandoned anytime soon mainly because as flexible as TCP is, in Tor browser you need rigidity. So FPI will remain forever.
But with every new decision it is clear we’re getting away from our first browser we loved.
There is a brilliant song summing up our current feelings towards all this – https://youtu.be/6VTicelwAn0
It is a simple check. You visit Site A, cookies that Site A set in the past are accessible. Site B cookies are not.
“network.cookie.cookieBehavior” is already set to “5” on FF 100.0.2 presumably because I use Strict mode except for banking for which I created a separate profile.
I got this over the weekend, so that’s where it shows up once you turn it on. Thanks for the info Martin.
Does Mozilla plan to add this privacy measure to the Android version or will it only be for the desktop versions?
Very interesting feature, I hope it will be available really soon! Thanks for the article. :]
Martin What are your thoughts on librewolf in terms of privacy?
https://www.unixsheikh.com/articles/choose-your-browser-carefully.html#librewolf
I tried it myself once, but don’t like the fact that it resizes itself all the time.
If you like full screen browsing then you won’t either.
I’ve remained faithful to the ‘First-Party Isolation’ rather than to the ‘Enhanced Tracking Protection’
pref(“privacy.firstparty.isolate”, true); // First-Party Isolation enabled
pref(“browser.contentblocking.category”, “custom”)
pref(“network.cookie.cookieBehavior”, 1); // block 3rd-party cookies
I’m aware 3rd-party cookies may be required, i.e. for logging purposes. I never encounter such requirements but should I that I’d avoid such places.
I had tested the ‘Enhanced Tracking Protection’ when it came out and realized that the ‘Cookie AutoDelete’ extension would fail to wipe at least a site’s upload data to my IndexedDB when this site was ‘privileged’ by Mozilla, so to say. I’ve described it on the ‘Cookie Autodelete’ GitHub repository :
[https://github.com/Cookie-AutoDelete/Cookie-AutoDelete/pull/1363#issuecomment-1134381862]
Of course Firefox’s ‘Enhanced Tracking Protection’ isolates such cookies but the point is it isolates them so well that 3rd-party tools cannot handle them when the site is ‘privileged’. As described on the above-mentioned GitHub page, what if I want this :
– Allow cookies YouTube
– Keep only some of the YouTube cookies (CONSENT) and wipe LocalStorage and IndexedDB?
I can perform this with ‘Cookie Autodelete’ but not if ‘Enhanced Tracking Protection’ is enabled.
So I remain faithful to First-Party Isolation. It may be removed in future versions of Firefox? I’ll reconsider my choice then, of course.
ABOVE POST (Tom Hawack said on May 27, 2022 at 9:46 am) IS OBSOLETE
I’ve tested again with :
pref(“privacy.firstparty.isolate”, false); // First-Party Isolation disabled
pref(“browser.contentblocking.category”, “strict”)
pref(“network.cookie.cookieBehavior”, 5); // default with ‘browser.contentblocking.category’ = “strict”
This time the ‘Cookie Autodelete’ wiped correctly as with First-Party Isolation enabled.
No idea what happened but I’m sure previous testing which led to my first post above as well as on CAD’s GitHub repository was accurate.
Hence sorry for the bother. I’ve notified as well this U-turn on CAD’s GitHub repository.
If you are blocking third party cookies, you will be better with privacy.firstparty.isolate turned off. All isolation features beside cookies are not enabled by default. You don’t need to isolate cookies if you block them. privacy.firstparty.isolate is no longer maintained.
@Anonymous,
> “privacy.firstparty.isolate is no longer maintained.”
Really? It’s still active in FF100.0+. But I’ve heard that it wad bound indeed to be no longer maintained.
> “All isolation features beside cookies are not enabled by default [by First-Party Isolation].”
‘Firefox Privacy – The Complete How-To Guide for 2022’
[NOTE : 2022, not 2017]
[https://restoreprivacy.com/firefox-privacy/]
—
“First party isolate
privacy.firstparty.isolate = true
Changing this to true will isolate cookies to the first party domain, which prevents tracking across multiple domains. First party isolation also does much more than isolating cookies, it affects: cookies, cache, HTTP Authentication, DOM Storage, Flash cookies, SSL and TLS session resumption, Shared Workers, blob URIs, SPDY and HTTP/2, automated cross-origin redirects, window.name, auto-form fill, HSTS and HPKP supercookies, broadcast channels, OCSP, favicons, mediasource URIs and Mediastream, speculative and prefetched connections.
This preference was added in late 2017 as part of the Tor Uplift Project.”
—
Also,
‘Privacy.firstparty.isolate vs total cookie protection : firefox’
[https://teddit.net/r/firefox/comments/o1ntqi/privacyfirstpartyisolate_vs_total_cookie/]
“The most important difference between DFPI and FPI is that DFPI will adhere to exceptions granted through the storage access API and thus ensure better web compatibility.” …
“exceptions granted through the storage access AP” is what I was referring to when evoking above “privileged” domains.
… “and thus ensure better web compatibility.” : for sure, but at what cost, that of allowed “exceptions”.
I’m not the only one by far to prefer FPI and the Web is filled with related articles.
The arkenfox user.js has privacy.firstparty.isolate = false… I assume there are good reasons for that…….
@Annonymous,
> “*All isolation features beside cookies are NOW enabled by default. Sorry.”
Well, above answer remains coherent.
*All isolation features beside cookies are NOW enabled by default.
Sorry.
Another gelding tool to take away power from the despicable ad industry. Very good!
@Frankel
Big Tech and government and ad industry has thousands of ways to get information from people without cookies (which are mostly for site configuration), so your response is really ignorant and dumb, and clueless if your really think this will take any power or make ad industry weaker.
I mean, Mozilla receives HALF BILLION from Google which is one of the biggest ad industries around and Mozilla release addons and ‘sign up programs’ and features that literally grab your information.
So if you even trust Firefox for anything, that’s why you sound clueless.
@Anonymous
It is the very people like you, who do nothing but assume bad faith & very personally attack & insult people for no reason, that make the web — and ghack’s comments section in particular — a miserable place.
* [Editor: removed, please stay polite]
Also Anonymous and Iron Heart always have the same opinion. Nice sockpuppet.
@Hitomi
I never write under another pseudonym than “Iron Heart” here, when will you understand? Can you read? I draw no benefit from using any other pseudonym. Stop being such a joke.
And Mozilla being pseudo-opposition to Google is obvious:
https://www.weforum.org/organizations/mozilla-corporation
https://www.weforum.org/organizations/google
https://en.wikipedia.org/wiki/Mozilla_Corporation#Google
Like, where is the argument here? What @Anonymous says above is not wrong even though the appropriate sources are lacking. I have them, and I mentioned them because you mentioned me, @Hitomi. Good job. You are doing your fellow Firesisters and your own propaganda a disservice by angering me.
I have never seen you write anything intellectual during my entire stay here. It would appear your desire to drop unwarranted argumentum ad hominem reduces you to nothing more but a troll :^)
@Anonymous
Big Tech and government and ad industry has thousands of ways to get information from people without cookies (which are mostly for site configuration), so your response is really ignorant and dumb, and clueless if your really think this will take any power or make ad industry weaker.
I mean, Brave receives its browsing engine and extension store and app store from Google which is one of the biggest ad industries around and Brave release addons and ‘sign up programs’ (Uphold) and features that literally grab your information.
So if you even trust Brave for anything, that’s why you sound clueless.