How to display all cached DNS entries on Windows
The Windows operating system uses a cache for DNS entries. DNS (Domain Name System) is a core technology of the Internet that is being used for communication. In particular, it is used to lookup IP addresses of domain names.
When users type a domain name in the browser, one of the first tasks that is executed when the site is loaded is to look up its IP address. The process requires access to DNS servers. Often, DNS servers of the Internet Service Provider are used automatically, but administrators may switch to other DNS servers, as these may be faster or offer better privacy.
Switching DNS providers may also help bypass Internet censorship, if DNS is used to block access to certain sites.
Windows uses the DNS resolver cache to speed up lookups. Each DNS lookup is added to the cache to speed up consecutive visits to the domains. Sometimes, entries may become old and may point to the wrong IP address. Our guide on fixing resolving host issues in browsers is still valid up to this day. Flushing the cache may help with that, as it removes all cached items to start from scratch.
Tip: you may use the free software DNSLookupView to log all DNS activity on Windows.
Display all cached DNS entries
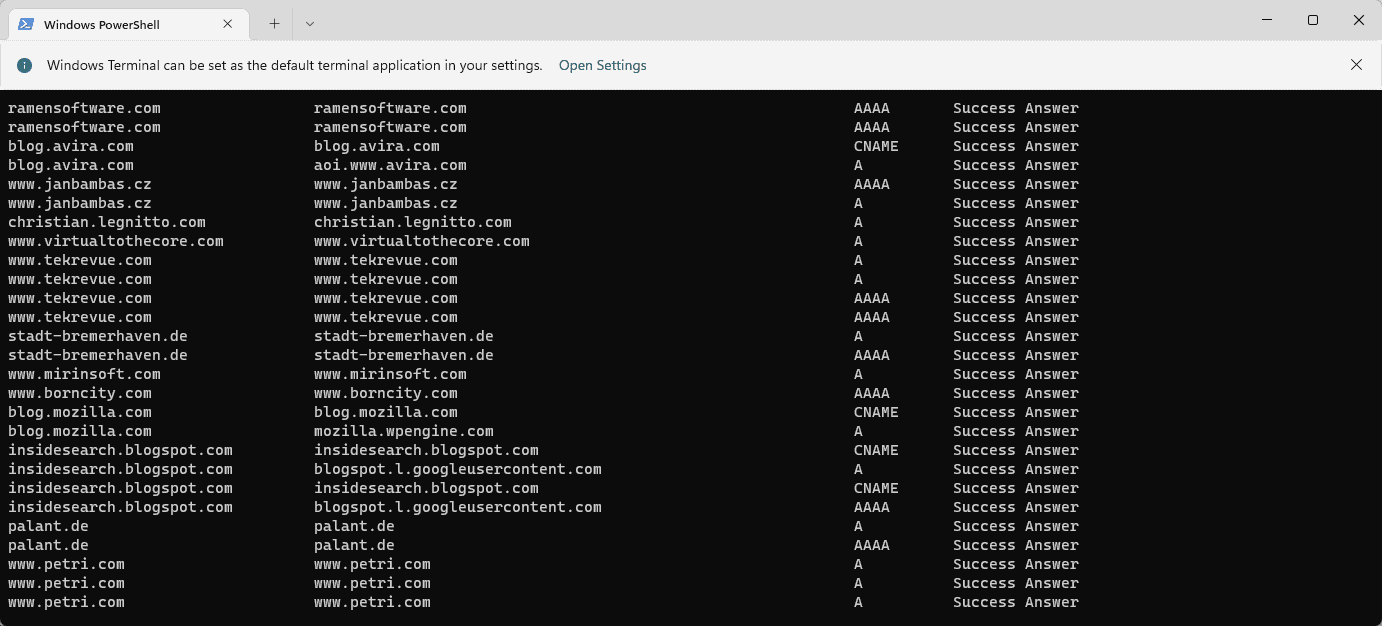
The list of cached entries can be useful for a number of purposes. Webmasters and developers may check if the correct IP address is assigned to a property, and users may be interested in seeing all entries, e.g., to find out which domains have been accessed during a session.
- Open the run box with the shortcut Windows-R.
- Type cmd.exe and hit the Enter-key.
- Type ipconfig /displayDNS to run the command.
Windows returns all cached DNS entries in a long list. You may also redirect the output to a plain text file by running the command ipconfig /displayDNS > %USERPROFILE%\Desktop\dns.txt. This saves the output to the file dns.txt on the desktop.
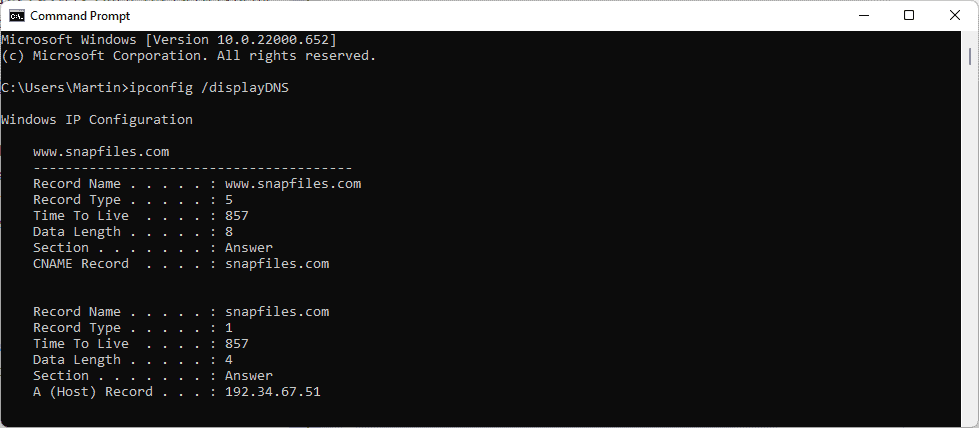
The very same command can also be run using PowerShell:
- Open Start, type PowerShell and select the result. If you have Terminal installed, type Terminal instead and select that result.
- Run the command powershell "Get-DnsClientCache | Format-Table -AutoSize".
The output uses better formatting. You may redirect the output to a text file as well using the command powershell "Get-DnsClientCache | Format-Table -AutoSize" >%USERPROFILE%\Desktop\DNS.txt.
To flush the DNS cache, run the command ipconfig /flushdns. Check out this guide if you are getting the error Could not flush the DNS Resolver.
Now You: which DNS provider do you use? (via Eleven Forum)






















out-file : Cannot find a part of the path ‘C:\WINDOWS\system32\%USERPROFILE%\Desktop\DNS.txt’.
En línea: 1 Carácter: 1
+ powershell “Get-DnsClientCache | Format-Table -AutoSize” >%USERPROFI …
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : OpenError: (:) [Out-File], DirectoryNotFoundException
+ FullyQualifiedErrorId : FileOpenFailure,Microsoft.PowerShell.Commands.OutFileCommand
Error with.:
powershell “Get-DnsClientCache | Format-Table -AutoSize” >%USERPROFILE%\Desktop\DNS.txt.
Run better.:
powershell “Get-DnsClientCache | Format-Table -AutoSize” >”$env:userprofile\Desktop\dns.txt”
sorry for traslate.:
powershell “Get-DnsClientCache | Format-Table -AutoSize” >”$env:userprofile\Desktop\dns.txt”
Is the DNS cache deleted when the system is re-booted?
There’s only one DNS address showing when running that command which is “download wireguard.com”.
That’s probably due to the fact I’m using Mullvad VPN on the Wireguard app along with a SOCKS5 proxy.
I use Avast VPN ONLY because I got a free subscription (I live in S. Korea), otherwise I would never use it or any Piriform product. Having said that, 50% or more of my cached DNS entries are from Avast even though I rarely use it. Is this something that I should be worried about from a privacy perspective?
Do people even know what a DNS resolver is?
the only thing it does is to replace the address of a page for the proper IP, that’s all it does… why people talk about privacy and “I disabled cache” how is it better to disable a service cache and let it resolve addresses all the time? actually that would create more data being sent.
People are so clueless about technology, the whole “we don’t log” is just BS to start with anyway.
I understand using Adguard DNS or NextDNS or pihole because you can add lists and resolve what you want to resolve so it works as an adblocker or resolve more addresses like web3 whatever, or use ones that can filter adult or malware sites or something, but people thinking someone is spying on what addresses you are resolving it’s stupid, they are not watching that, if they want to watch anything they would see your traffic and steal your crap, like happens with people who use public wifi.
But seriously people disabling Windows DNS cache service are the worst… yeah, resolving things over and over again, that’s smarter and faster than just cache it. /s
it’s ridiculous to think some dns server will somehow with you more privacy and all that, when you are using a website that you have to ‘consent to your data being stored’, and probably have google account, use youtube, have phones and tvs with wifi and etc etc. Do people really care?
But I guess people’s fairy tale of privacy placebo and anonymity will be happy doing useless crap that will not do anything about anything because governments will get the information they want from you even if you ‘resolve’ the addresses in whatever server you choose.
I mean, use a good firewall or an adblocker, and addresses will still be resolved even if there is no connection to them, that’s how it works, with all the addresses and 3rd party addresses and anything that gets connected when you go to a simple website, then that means it is stupid to worry about dns resolvers unless it gives you a good feature like NextDNS or it works better and faster or filter less and you want to have access to all websites or give you other type like web3, you know, something relevant, but thinking “I want to switch because I don’t trust my ISP” is just stupid.
The problem : https://dnsprivacy.org/the_problem/
Ridiculous? Phantasmagorical?
The problem? [ https://dnsprivacy.org/the_problem/ ]
Ridiculous? Phantasmagorical?
Nextdns.io and a 2,156 line hosts file to block all the Zuckface garbage.
Enabled by default, the DNS Client service needs to be running for that cache to work.
There will be no DNS cached if DNS over HTTPS (DoH) is used.
Quad9 is used for my Win10 systems, Firefox is Cloudflare DoH.
Router is cable ISP default.
That setup avoids DNS headaches I experienced when getting too fancy with DNS.
Cloudfalre DoH used for two google controlled mobile devices (aka “phones”).
We’re using Cloudflare for DNS as you have to get through them for most sites anyways.
I use Quad9 DNS provider.
Also, on my Windows virtual machines, I see no reason to cache these entries, so the the service is disabled here.
[https://social.technet.microsoft.com/Forums/windows/en-US/a04284f9-cf27-4f37-82fe-31255f70625f/how-to-disable-windows-10-dns-cache-services?forum=win10itpronetworking]
You gain only milliseconds (less than 10) per server, with the service enabled.
And then there’s also the browser cache, which is in RAM here. :)
If I leave it on, it has to parse my HOSTS file first, which takes some time.
Running as always (Speedy Gozales -> Speedy Hawack) I forgot to mention this regarding DNSCrypt-proxy :
1- Anonymization only works with DNSCrypt servers :
[https://github.com/DNSCrypt/dnscrypt-proxy/wiki/Anonymized-DNS#configuring-anonymized-dns-in-dnscrypt-proxy]
2- DNSCrypt-proxy : using DNSCrypt protocol or DoH protocol? :
[https://www.reddit.com/r/privacytoolsIO/comments/7wakeh/dnscrypt_v2_vs_dnsoverhttp2/]
I disable Windows 7′ dnscache service to start with.
DNS is performed with DNSCrypt-proxy which includes its own cache.
DNSCrypt-proxy includes so called anonymized relays, which means that the DNS resolver ignores the requirement source. Not all DNS servers accept being called via anonymization.
Generally I use the servers (dnscrypt compatible) with two conditions : distance and support for anonymization. At this time I use, via DNSCrypt-proxy, 3 servers of which 2 in France (distance), one in Belgium, all three supporting anonymization.
DNScrypt-proxy supports DoH and DNScrypt protocols. I prefer the latter because, without being an expert myself, I read that is was the most elaborated for encrypted DNS.