FontOnLake Malware Can Target Linux Systems
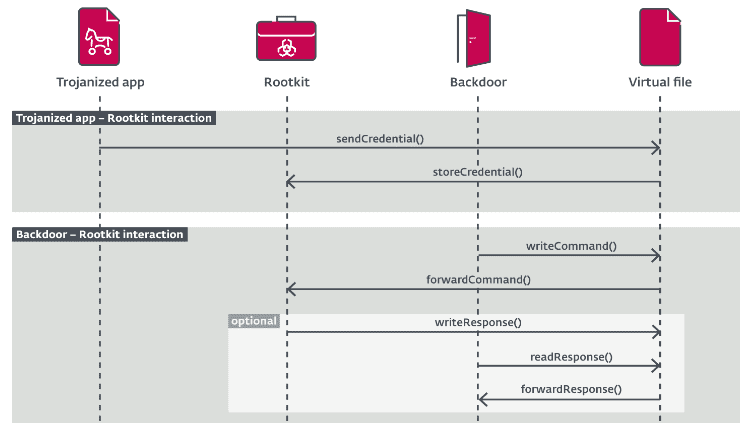
Documentation released by internet security company, ESET, on October 7th, has given details to what was lesser known malware family that emerged this past May, including details that are very relevant to the Linux world, especially those using older RedHat Enterprice Linux systems for production servers.
The malware family given the name FontOnLake, uses custom modules providing remote access to infected systems, using a rootkit to conceal the infection. The malware is able to collect credentials, and also acts as a proxy server by the use of advanced designed components that can be placed into three categories, according to the ESET release:
- Trojanized applications – otherwise legitimate binaries that are altered to load further components,
collect data, or conduct other malicious activities - Backdoors – user-mode components serving as the main point of communication for its operators.
- Rootkits – kernel-mode components that mostly hide and disguise their presence, assist with updates,
or provide fallback backdoors.
The documentation also gave some insight into the cautious measures taken by the operators of the malware, “We believe that its operators are overly cautious since almost all samples seen use different, unique C&C servers with varying non-standard ports The authors use mostly C/C++ and various third-party libraries such as Boost, Poco and Protobuf. None of the C&C servers used in samples uploaded to VirusTotal were active at the time of writing, indicating that they could have been disabled due to the upload. We conducted several internet-wide scans that imitated initial communication of its network protocols targeting the observed non-standard ports in order to identify C&C servers and victims. We managed to find only one active C&C server, which mostly just maintained connectivity via custom heartbeat commands and did not provide any updates on explicit requests.”
The malware contains applications that likely have been modified at the source code level and rebuilt to perform malicious actions not existent in the original versions, such as collecting sensitive data by using modified functions such as auth_password from the sshd package. The method in which these modified packages and applications are being distributed to victims is currently unknown.
ESET has also disclosed that they have discovered three backdoors as part of the malware, using the Asio library from Boost. The documentation goes into explicit detail about how the backdoors function, what commands they utilize, and how they collect and store information necessary to function.
In regards to the Rootkits, the disclosure states that all current samples of the malware target kernel versions 2 6 32-696 el6 x86_64 and 3 10 0-229 el7 x86_64, which are older kernels from the RedHat Enterprise Linux system, however despite them being older it should be noted that a large number of production servers may still be using older systems and kernels to maximize stability, or simply as bad practice from lazier systems administrators of the ‘if it’s not broken, don’t fix it’ mindset. Another thing worth noting from the documentation are comments in the conclusion section stating,
“Their scale and advanced design suggest that the authors are well versed in cybersecurity and that these tools might be reused in future campaigns.” And , “As most of the features are designed just to hide its presence, relay communication, and provide backdoor access, we believe that these tools are used mostly to maintain an infrastructure which serves some other, unknown, malicious purposes.”
So, while typical home-users may not have to worry about their desktop Linux PC, this information is still valuable to note that while many people boast the security of Linux systems, it is not infallible, and proper maintenance and upgrading is still essential in protecting yourself.
The documentation in PDF form can be found at the welivesecurity website, an IT security website with insights from ESET experts. https://www.welivesecurity.com/wp-content/uploads/2021/10/eset_fontonlake.pdf

















Kernel 3.10.0-229 dates back to 2015-03-05. Systems administrators still running that kernel in 2021’s security environment, should look for a new line of work.
Oh my, ESET:
“ESET NOD32 ANTIVIRUS FOR LINUX DESKTOP currently receives limited support and will be terminated in Q3 2022”
https://www.eset.com/int/home/antivirus-linux/
https://web.archive.org/web/20211014194531/https://support.eset.com/en/kb7911-migrate-from-eset-nod32-for-linux-desktop-to-eset-endpoint-antivirus-for-linux
I cannot trust a proprietary virus scanner anyway. The *only* exception are the Live CD/DVD/USB images some AV provide for free which are of course Linux for the most part LOL. But a proprietary AV running on my Linux box? Never.
I keep my Ubuntu system up-to-date to avoid problems. Thanks for the information.
Does ESET explained what need to do to get this malware?
User needs to install it yourself or what?
Or maybe this module is placed in RedHat repository?
The article says, “The method in which these modified packages and applications are being distributed to victims is currently unknown.” As that is all the information given by ESET in those regards, at this time :)