Firefox 87 to limit the referrer for all cross-origin requests
Mozilla announced plans to trim the referrer that the Firefox web browse sends when requests are made for all cross-origin requests today to improve privacy.
Requests made by the web browser, e.g. to load a webpage, image, CSS stylesheet, or advertisement, includes the referrer. The referrer is usually the URL that users see in the browser's address bar.
Up until now, Firefox and most other browsers, trimmed the referrer only when requests were made from secure sites, e.g. those using HTTPS, to non-secure sites, e.g. those using HTTP.

The URL may provide information to the servers the requests are made to that go beyond the domain name of a site. It may reveal the article title or page a user accessed, and may also include sensitive information such as search queries.
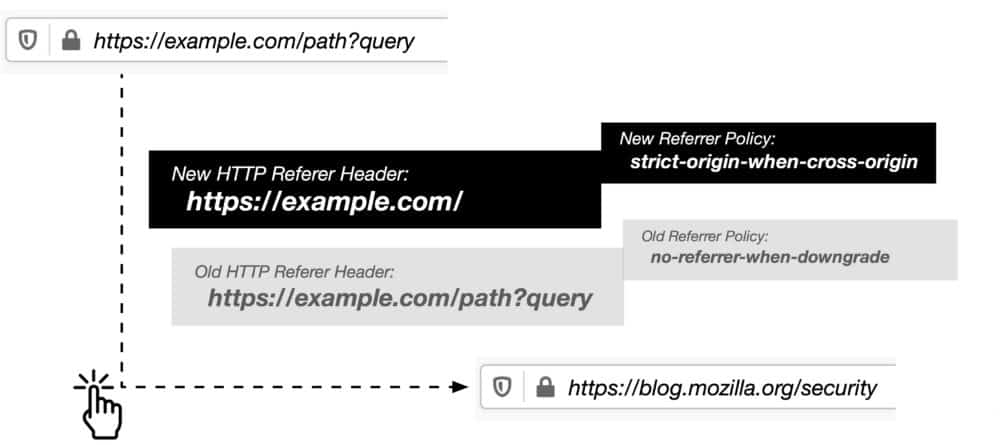
From Firefox 87 on, Mozilla will trim the referrer automatically for all cross-origin requests, e.g. requests from Site A (example.com) to Site B (secondexample.com).
Site B does not known the exact page the request originated anymore from, and other information, such as search queries, are not leaked either anymore to the site.
Instead of submitting the entire referrer, e.g. only the domain name is submitted. In technical terms, Firefox is moving from the referrer policy "no-referrer-when-downgrade" to "strict-origin-when-cross-origin".
Starting with Firefox 87, we set the default Referrer Policy to ‘strict-origin-when-cross-origin’ which will trim user sensitive information accessible in the URL. As illustrated in the example above, this new stricter referrer policy will not only trim information for requests going from HTTPS to HTTP, but will also trim path and query information for all cross-origin requests. With that update Firefox will apply the new default Referrer Policy to all navigational requests, redirected requests, and subresource (image, style, script) requests, thereby providing a significantly more private browsing experience.
The change is made silently in the background for all users of Firefox 87 or newer. Firefox 87 will be released on March 23, 2021 to the public.





















In Firefox 86.1 I’m attempting to cut and paste some Article title into A Disqus forum and something interesting happens along with that cut and pasted text and in the same color as the pasted page’s background I get more than the pasted text after submitting the post via Disqus’ system that changes any colored text into black on while text by default once the post operation is completed so a bunch of hidden text appears that’s a duplication of the website address that I had already copied over so as to make a proper citation to the article.
So I’ve taken to calling this cut and paste stuffing of hidden text that is set to the same color as the background via some nifty/nefarious scripting and really Firefox needs a Paste unformatted right clock modal dialog option that can remove all but the actually copied text so that’s it’s easier to get that rather than having to do an intermediary paste to a text only editor and then re-cutting and pasting that way.
And Firefox blocking all 3rd party cookies has really borked Disqus forums posting while trying to remain logged into Disqus and the standard Strict Privacy setting keeps me logged in to Disqus but prevents me from directly uploading content form my laptop/PC! And if I set a custom Privacy setting that allows 3rd part cookies only for pages visited I can upload content but have to re-login with each page reload even on the same website.
“Mozilla will trim the referrer automatically for all cross-origin requests, e.g. requests from Site A (example.com) to Site B (secondexample.com).”
As far as I understand, ‘network.http.referer.defaultPolicy’ will be 2 instead of 3 (as well as in Private Mode ‘network.http.referer.defaultPolicy.pbmode’)
Due to https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Referrer-Policy#strict-origin-when-cross-origin it’s just new default (!) rererrer-policy if no policy is specified (or invalid) on the site.
Will Firefox be follow less restrictive policies if they are on the site?
https://blog.mozilla.org/security/2021/03/22/firefox-87-trims-http-referrers-by-default-to-protect-user-privacy/
“Websites can use referrer information for many fairly innocent uses, including analytics, logging, or for optimizing caching.”
“Unfortunately, the HTTP Referrer header often contains private user data: it can reveal which articles a user is reading on the referring website, or even include information on a user’s account on a website.”
“Starting with Firefox 87, we set the default Referrer Policy to ‘strict-origin-when-cross-origin’ which will trim user sensitive information accessible in the URL.”
Analytics using browsing data leaked to third parties from referrers are “innocent” ?
Of course, this is written on a Mozilla site that connects to the innocent Google Analytics.
Third-parties knowing what domains you browse is “innocent analytics” use of your browsing data, only the path/query part is considered as something “sensitive” at Google & Mozilla. The rest belongs to them.
https://bugzilla.mozilla.org/show_bug.cgi?id=1589074#c30
“I think for now we want to allow websites to override this, similar to Chrome”
So contrary to user interests, user expectations, and privacy, sites can apparently override this new referrer policy with a less private one and still leak the full urls if they want to. It would seem that even Safari was less dickish that the Google duo here:
https://github.com/w3c/webappsec-referrer-policy/pull/125#issuecomment-619460219
“Safari’s change is not a change of default policy. Sites can’t change it, only users can. Third-party referrers are downgraded to origin by default regardless of the referrer policy set by the website.”
The big takeaway from the comments is that it’s highly unlikely any of you have ever had sex.
wrong deduction!
When you put too much extensions in your browser you could be increasing the threat to your privacy.
An extension for this that and another, it can be counter-productive.
Many extensions are pinging home all the time. Sometimes its best to take the bad with the good rather than trying to correct the bad with potentially even more bad. If you trust the extension though, go ahead and use it.
These overbroad fearmongering ideas against all privacy extensions, that statistically they would cost more in privacy than they would bring, because of fingerprinting or because of a malicious author, come from tracking companies. This includes Mozilla and of course Google. This is the false motive behind Google’s webextension manifest v3. This has been also a way for Mozilla to ransom innocent developers to have their “unverified dangerous extension” or something warning removed in priority by paying them.
I find it easy to spot trustworthy extension developers and suspicious ones. For those who can’t do that, they can ask for advice. The Firefox extension system is largely trustworthy, but browser companies have interests in destroying trust in it much beyond the reality of the threat. The developers of those privacy extensions like POOP, Smart Referer or Referer Modifier are much, much more trustworthy than the browser developer Mozilla itself that arrogates to itself the right to tell which ones should be trusted. Mozilla has been recommending or promoting shady extensions like Ghostery or Honey for money, that’s true. So avoid shady companies, but do not boycott the people who fight them.
I wonder if “Privacy-Oriented Origin Policy” is still useful as an addon after this update, anyones thoughts?
I think that this Firefox update:
– is only about the referrer header, not about the origin header, and
– still leaks the origin domain in the referrers, which is the only thing that the origin header leaks, so this update would not care about the origin header anyway
Something else to know: even if you remove or fully spoof your referrers with an extension instead of keeping the domain, many requests will still also contain an “Origin” header, which is like a “lighter” brother of the referrer header that sends only the domain, invented much later by Google with the hope that this one would survive even when the referrer was manually killed by the user. To tell you the current state of privacy awareness in the modern web, even the developer of the Smart Referer add-on was not aware of the existence of this now 10-year-old other privacy hostile header.
Extensions to counter this other privacy threat:
POOP:
https://addons.mozilla.org/firefox/addon/privacy-oriented-origin-policy/
Only work in progress for inclusion in Smart Referer:
https://addons.mozilla.org/firefox/addon/smart-referer/
https://gitlab.com/smart-referrer/smart-referer/-/issues/118
Of course all those are a drop in the ocean with very few users, and browser companies should be the ones doing it. Which they won’t do, for already discussed reasons.
I haven’t sent a real referer in years (by using a referer extension in Firefox), and have not experienced an issue on well over 99% of sites I’ve visited.
What sucks is when a site is so poorly written that it still requires a specific referer. It’s trivial to spoof a referer, so why any site still checks them before working properly is just silliness. It’s a completely fake security measure, perhaps done to present “security theatre” to ignorant management.
Referers are only somewhat useful as a tracking mechanism, and if a site depends on tracking users for it’s success, it would be best if they just post that detail on their front page so people know not to use that site.
BTW, hcaptcha.com and sourceforge.net are 2 of the worst offenders of sites requiring referers. As such, I avoid any site that usse hCaptcha and no longer use SourceForge to host my coding projects.
I had added hcaptcha in my exception list as needing to remove referrer for it instead of spoofing it to destination, but I haven’t noticed any problem on sourceforge when spoofing referrer.
I have Fennec and Iceraven(for all addons) installed in my phone along with Firefox. Now in Fennec and Iceraven I can access about:config option and so I have set network.http.sendrefererheader and network.http.sendoriginheader to zero, but it does break an odd site here and there(so far only banking related). How are these options going to change? If someone can explain in easy and unhateful words, it would be greatly appreciated.
And I, as an user of FF didn’t know. I don’t care for Brave or Chrome related news. And FF get’s an article about it because (thats my assumption) author likes/uses this software.
I won’t remember about it in one weeks time, but I guess it’s good. At least FF doesnt add anything or tamper with typed urls like some browsers did in the past ;) (by a mistake of course…)
Trim only, not remove or spoof to target, still leaking the domain name. That’s good but not enough. Every contacted third-party will be able to know what domain the user made the request from and if ubiquitous enough build a browsing profile. Sites are not entitled either to know where one browsed to their site from. And this should be done for same domain browsing too.
From the user point of view, the only reason not to fully kill the referrer would be the risk of a few sites being broken. But I have spoofed all referers to target sites for years and met problems only with a few sites.
From the browser companies point of view, the interests of trackers weight a lot in the decisions. Mozilla implemented a click tracking standard after all called hyperlink auditing, and tried to enforce it on. This is why they should have have done more and earlier but did not. And will pretext dishonestly that site breakage is their only concern for not doing it. But there are other circumstances where much more serious massive breakage of the web without really better positive benefits did not stop them from applying their decisions, because it was what Google or another one wanted for its own reasons. Consider also that if a major browser enforced the death of referrers, it would pressure the few sites that require it to stop requiring it to work, so the small site breaking problem would become even smaller.
Referrer extensions are thus still an important privacy addition, because the new default will be far from enough, Mozilla being in bed with the tracking business. This one will even include an updated whitelist to take care of broken sites:
https://addons.mozilla.org/firefox/addon/smart-referer/
This one is another good option:
https://addons.mozilla.org/firefox/addon/referer-modifier/
Hi there! Please, few questions:
1) Is it possible to spoof all referrers (as you did), but without using add-ons?
2) What’s the benefit of using referrer add-ons?
Thks!
To be more accurate, about:config prefs allow various forms of trimming but I am not aware of prefs that allow spoofing, another reason to use referrer add-ons (on the Firefox versions and forks where Mozilla still allows you to use them it at the moment).
I have found spoofing referrer to the target domain less breaking than plain removing it. I think that the Smart Referer approach is to send the full target URL as referrer by default, which is fine too.
Thks.
1) Yes, on Firefox versions that still allow to access about:config, and if they have not yet neutered those preferences in those versions, there are prefs to configure referrers:
https://feeding.cloud.geek.nz/posts/tweaking-referrer-for-privacy-in-firefox/
2) However I don’t think that exceptions can be set unless add-ons are used
better late than never, ymmv :)
how does it feel to have a web browser live rent-free inside your head every single day?
Yep, the flag for reducing referer granularity was there a year ago and since a few months ago it’s on by default.
Please, can you ask Mozilla to add an option to completely disable all of its auto connections that are opened every time we run the application? The functions that make use of these connections are not necessary at all for a web browser to work.
“Oh, it’s for security, privacy, performance purposes,” they say. Always using a noble pretext to violate user’s privacy. Each version they make more difficult for us to disable those connections. On 60+ they made it impossible to totally disable some.
But in the Icecat I am using, there is a disadvantage that if you have resistFingerprinting enabled then the the browser will reveal that it is Icecat in the useragent from javascript.
https://browserleaks.com/javascript
Revealing not using a mainstream browser instead of spoofing the user agent string may have a small fingerprinting cost but this has to be balanced with the benefit of telling sites and browser market share statistics tools that mainstream browsers are less hegemonic than they would look like if the user agent string was spoofed. The big browser companies probably love the idea that every user is pretending to use their browsers, it helps them kill the ethical alternatives. Adding a little bit of fingerprinting fear helps that.
@ConspiracyTheorist Use Icecat based on latest Firefox ESR. Most autoconnections are disabled by default and you can disable the rest by changing the configurations.
What Brave and even Chrome have already done… Except that Firefox ges its own article for it. :D
https://bugzilla.mozilla.org/show_bug.cgi?id=1589074#c0
“Google planned to ship that, I think it’s worth shipping it to in Firefox. But maybe we can wait until successfully shipping in Chrome”
Google decides. Mozilla follows.
@ironheart usual haters? Lmao its you who’s active 24*7 with almost no life trying to prove something in almost every other post of ghacks
@Someone
And this is your business exactly how? Also, my post didn’t contain any hate, just two facts. Writing that took me, like, under 1 minute, approximately.
@bronzeheart, like my post had some hate
And the comment section is yours?
You want to post in public space, then get ready for people to push back if they don’t like what you’re doing.
But hey, cry more, you no lfie.
> What Brave and even Chrome have already done
Firefox as well – it’s default in private mode since three years. New in Firefox 87 is the expanding to every user. But Firefox users are already able to do this since many years, even in non-private mode, if they wanted to do this.
@IronHeart
Lulz
> What Brave and even Chrome have already done… Except that Firefox ges its own article for it. :D
I hope you wore your Brave T-Shirt and Hat when you decided to write that because if you did not ITS VERY UN-BRAVE of you for BRAVE-TODAY.
@the usual haters
I see you are still allergic to the facts…
Fact 1: There was a flag in Chromium called chrome://flags/#reduced-referrer-granularity which did the exact same thing the article here described – Google removed it, because it is now the default.
Fact 2: There was no article about this development in Chromium, but we get a filler article for Firefox.
You guys are arguing against the facts. :D I don’t think I am the one with the hate boner here.
@IronHeart
Do you really actually believe that google has your best interests at heart when you decide to use chromium or forks of chromium?
You can almost guarantee that they hate Brave, much more than what you call the “usual haters” on these comments sections.
I expect Brave to be completely crippled soon enough by googles chromium adopting troublesome web standards. Brave is in bed with the devil.
Google products should be boycotted in my opinion, their censorship is truly disgusting. I don’t want big-tech deciding who i can or can not listen to. I find them to be deplorable.
That is resaon enough to take an ethical stand and not use their software as much as possible.
Google actively censors free speech, mozilla has no power to do so. That is a big difference.
@Anon7
1) The web standards are also being implemented by browsers other than Chromium. That’s why they are called “web standards”.
2) That Mozilla has a code base different from Chromium does not automatically make them trustworthy. That’s a non-sequitur.
3) Browser devs can ungoogle Chromium and there are also internal kill switches for various web standards.
4) If you are worried about censorship, perhaps you shouldn’t use a browser from a company that claims that “we need more than deplatforming” (Mozilla). They can also censor which websites you are allowed to go to within the browser, no problem.
But I know that you are woefully unable to understand all of these points…
It will be interesting to see how Brave can afford the extra cost for them to keep the Chromium code base unlinked from the mainstream direction that google is taking it. I have no confidence in them to be able to keep up.
Manifest V3 is nowhere near finished yet (despite what some may say), its full implemtation is only beginning. Brave and vivaldi are going to go the way of the dodo by trying to keep up with chromium codes invasive privacy practices. Googles direction is completely the opposite direction to what brave or vivaldi wants. Breakage, breakage, UBO works way better on firefox not chromium forks. Brave saying they are supporting UBO is a joke.
Google hate UBO. Brave a privacy browser supports chromium, what a joke. It would stand to reason that since their tor windows broke, UBO will also be prone to breakage on chromium forks going forward.
> 1) The web standards are also being implemented by browsers other than Chromium. That’s why they are called “web standardsâ€.
Mozilla is continuing to support blocking webrequest calls when manifest V3 arrives, chromium will not support it. Mozilla are more accommodating to excellent extensions like UBO. Google chromium is trying to make life hell for such extensions.
> 2) That Mozilla has a code base different from Chromium does not automatically make them trustworthy.
Who the hell releases open source code for their browser and then makes their browser totally proprietary? google will always be automatically more untrustworthy due to their history.
> Browser devs can ungoogle Chromium and there are also internal kill switches for various web standards.
Will brave offer support to block webrequest calls when V3 arrives so UBO can be used? Or should people be relying on their inferior ad blocker?
> If you are worried about censorship, perhaps you shouldn’t use a browser from a company that claims that “we need more than deplatforming†(Mozilla). They can also censor which websites you are allowed to go to within the browser, no problem.
What websites are they censoring? you’re full of sh1t, no one should be taking the rants of their ceo seriously. She is a virtue signaler. Until there is active censorship, your argument falls dead on its ass.
> But I know that you are woefully unable to understand all of these points…
I understand that google is way worse than what mozilla is.
Iron Heart still playing the victim … makes a useless post, gets surprised when called out, attacks “the usual haters”
@Anonymous
I don’t need to “play the victim” when it’s obvious that you guys are just unable to cope with reality. In fact, I am laughing at you.
The only thing they change is to make it default. You always was able to remove in firefox the whole refers if you wanted. They didn’t do it because sites like instagram and other relay on it for surfing between pages and images. you can look for “network.http.sendRefererHeader” in about:config.
And you get to be the first to comment, like in every Mozilla related article! What a crazy world we live in!
and someone needed to comment to soothe their own ass which is almost always burning for no reason
@someone: It’s Iron Heart. His hateboner for Firefox and his slavelike devotion to Brave means he’ll shitpost when he sees a Firefox thread ASAP. It’s like he has nothing better to do in life.
I can not wait for the “Google Chromium Engine Guys” to swirl around another FF article. Its so entertaining.
Their only argument is that googles funds FF.
So funny when chromium forks are completely reliant on the G for their scraps.
Mozilla has more independence than chromium forks from google.
(A) They could terminate that google search engine at the drop of a hat when the contract is up, like they did with YAHOO.
(B) They are looking for alternative means of funding (good sign) through the VPN service they are launching.
Meanwhile Brave cant even run a tor window correctly due to its crap internal ad blocker which is complete sh1t compared to gorhills masterpiece.
chromium also prone to WEB RTC leaks, absolute rubbish engine.
Gecko >Chromium