Add "Run in Sandbox" options on Windows 10
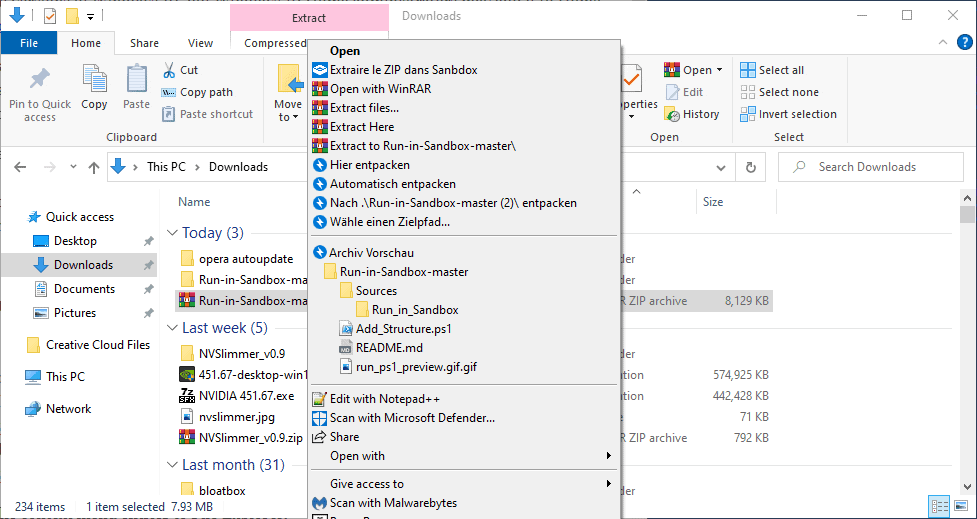
Run in Sandbox is a useful PowerShell script that Windows 10 administrators may use to add options to run executable files, zip archives, and scripts, in the Windows 10 sandbox.
Microsoft introduced Windows Sandbox in late 2018 as a way for administrators to run content in its own environment to avoid harm or changes to the underlying system. The Windows Sandbox is available in all professional versions of Windows 10 version 1903 or newer, but Windows 10 Home administrators may add it to Home systems as well; check out this guide that explains how to do that.
Run in Sandbox adds shortcuts for various file types to File Explorer on Windows 10. Once installed, all it takes to run a supported file type in the sandbox is to right-click on it and select the "run in sandbox" option from the context menu.
The main requirement for the script is that Windows Sandbox is installed already on the system. You can add the sandbox by searching for "turn Windows features on or off" and checking the "Windows Sandbox" entry in the Control Panel applet that opens. It is likely that this is going to be moved to the Settings app in the future, but for now, it works.
To install Run in Sandbox, do the following:
- Download the latest version from the developer's GitHub project site, e.g. select Code > Download Zip.
- Extract the archive on your system and open a File Explorer instance to navigate to the folder.
- Select File > Open Windows PowerShell > Open Windows PowerShell as Administrator.
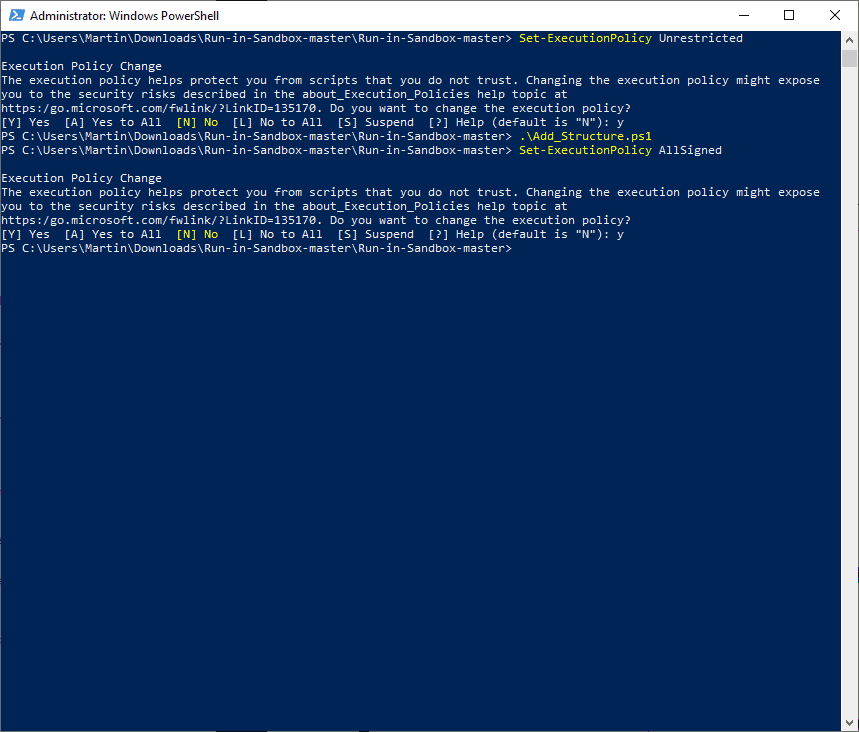
- Run the following commands in the PowerShell prompt and select Y whenever you are prompted.
- Set-ExecutionPolicy Unrestricted
- .\Add_Structure.ps1
- Set-ExecutionPolicy AllSigned
The script adds the context menu entries to File Explorer.
Note: When I tested the script on an English Windows 10 Pro version 2004 system, I noticed that it added French menu entries instead of English ones; this is probably a bug but easy enough to understand.

Run in Sandbox supports PS1, VBS, MSI, and EXE file types at the time of writing. The script creates a WSB file when you select the Run in Sandbox option from the context menu and the sandbox will be launched automatically afterwards.
Scripts, PS1 and VBS, display two context menu entries instead of one. The first runs the script without any parameters, the second allows you to add parameters.
Closing Words
Run in Sandbox is a useful tool for system administrators, software testers, and other users who like to execute content in a safe environment. While that is also supported by third-party applications like Sandboxie, it is not always allowed to run these in work environments. The Windows Sandbox offers a way out.
Now You: do you use a sandbox application? (via Deskmodder)


















Hi. i want to run sandbox by PowerShell and give a file path to execute it . Would you please help me in finding this.
Furthermore I’m in search if the file during execution takes network permission than decline to run
Uh, the \Add_Structure.ps1 is missing. Sooooooo this is worthless.
This is exactly what happened to me. Luckily I had another Windows system where I were able to export the keys in HKLM\SOFTWARE\Classes\ to import them on my broken system.
I then spent about 30 minutes cleaning my registry.
Avoid this software it if you do not want to mess up your system.
BE EXTREMELY CAREFUL WITH THIS. If this script encounters an error this can lead to your system not being able to launch EXE, MSI, VBS or PS1 files AT ALL. It will take a system restore in order to get these registry values back correctly as you will not be able to run the Registry Editor, Command Prompt or even Task Manager.
To remove if you had installed en francais….
Reg.exe delete “HKLM\SOFTWARE\Classes\Microsoft.PowerShellScript.1\Shell\Exécuter le PS1 dans Sandbox” /f
Reg.exe delete “HKLM\SOFTWARE\Classes\Microsoft.PowerShellScript.1\Shell\Exécuter le PS1 dans Sandbox avec des paramètres” /f
Reg.exe delete “HKLM\SOFTWARE\Classes\VBSFile\Shell\Exécuter le VBS dans Sandbox” /f
Reg.exe delete “HKLM\SOFTWARE\Classes\VBSFile\Shell\Exécuter le VBS dans Sandbox avec des paramètres” /f
Reg.exe delete “HKLM\SOFTWARE\Classes\exefile\shell\Exécuter l’EXE dans Sandbox” /f
Reg.exe delete “HKLM\SOFTWARE\Classes\Msi.Package\shell\Exécuter le MSI dans Sandbox”
Reg.exe delete “HKLM\SOFTWARE\Classes\Microsoft.PowerShellScript.1\Shell\Run the PS1 in Sandbox” /f
Reg.exe delete “HKLM\SOFTWARE\Classes\Microsoft.PowerShellScript.1\Shell\Run the PS1 in Sandbox with parameters” /f
Reg.exe delete “HKLM\SOFTWARE\Classes\VBSFile\Shell\Run the VBS in Sandbox” /f
Reg.exe delete “HKLM\SOFTWARE\Classes\VBSFile\Shell\Run the VBS in Sandbox with parameters” /f
Reg.exe delete “HKLM\SOFTWARE\Classes\exefile\shell\Run the EXE in Sandbox” /f
Reg.exe delete “HKLM\SOFTWARE\Classes\Msi.Package\shell\Run the MSI in Sandbox”
Delete these keys to remove
I configured the xml to get this to be english but now I have both english and french. How can I uninstall the french option from my context menu?
I was able to change the language by modifying the xml and readding through this process. Now I have the french and the english version. How can I remove the french?
How do we remove this?
Hi Martin,
Nice tool.
One small thing with the article, Snapshots are showing German text, not French. :)
You are welcome. The second screenshot shows the French entry “extraire le zip dans sandbox” that the PowerShell script added.
how to solve the langeu problem: (from github)
Update (05/19/20): Add other languages for context menus
Those languages are available: French, Italian, Spanish, English, German
To configure language, go to Sources\Run_in_Sandbox\Sandbox_Config.xml
Add language in Main_Language
This language should be the language code name
Hi Martin, Do you know how to uninstall this if no longer want it?
Please correct your article’s title to specify Windows 10 Professional. All the later comments at the link you supplied to the sandbox running on Windows 10 Home say the sandbox does not run on Windows 10 Home.
has anyone used it? is it better than the sandboxie?
Hi. This might be of help:
When I ran .\Add_Structure.ps1, my system crashed and a BSOD was displayed with an error message about something watchdog something. Sorry I didn’t take note of it. But the watchdog part made me think it had something to do with windows’ integrated antivirus/antimalware. So I disabled it and sure enough, the script ran without any trouble. After it runs, one can safely re-enable the realtime protection.
That context menu is disgusting…
It’s actually pretty sexy.
I am sure it is a testing machine :)
Looks so much faster and simpler:
https://www.ghacks.net/2019/08/30/create-windows-sandbox-configuration-files-with-sandbox-configuration-manager/
https://gallery.technet.microsoft.com/Windows-Sandbox-Configurati-f2c863dc
Hopefully there comes a menu option to automate this for things like web browsers.
Once a program is run sandboxed will it continue to be sandboxed after reboots or is it necessary to sandbox the desired application upon each use?
Here you can read almost everything about Windows Sandbox.
https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-sandbox/windows-sandbox-overview