Firefox 74 will drop support for TLS 1.0 and TLS 1.1
Version 74.0 of the Firefox web browser will drop support for the encryption protocols TLS 1.0 and TLS 1.1 entirely. Sites that don't support at least TLS 1.2 will show a "secure connection failed" error page when the change lands preventing users from accessing the sites.
Mozilla and other browser makers including Google, Microsoft and Apple revealed plans in 2018 to deprecate TLS 1.0 and TLS 1.1 in 2020 to improve the security and performance of Internet connections.
The announcement was made well in advance to give webmasters and organizations time to migrate services that still used one of the protocols to a newer protocol.
TLS 1.3 Final was published in 2018 and browser makers like Mozilla or Google implemented support for the new protocol in their browsers. All major web browsers support TLS 1.3 as of today.
While support for better more secure protocols is available, some sites have not migrated to using these protocols exclusively. A Mozilla scan in mid 2019 showed that about 8000 sites of a list with 1 million top sites were not supported TLS 1.2 or higher. The count may be lower by now considering that another six months have passed since the scan was made.

Starting in Firefox 74, sites that use TLS 1.1 or lower won't load anymore in the browser. The same will happen at around the same time in Google Chrome and other major browsers such as Microsoft Edge or Apple Safari.
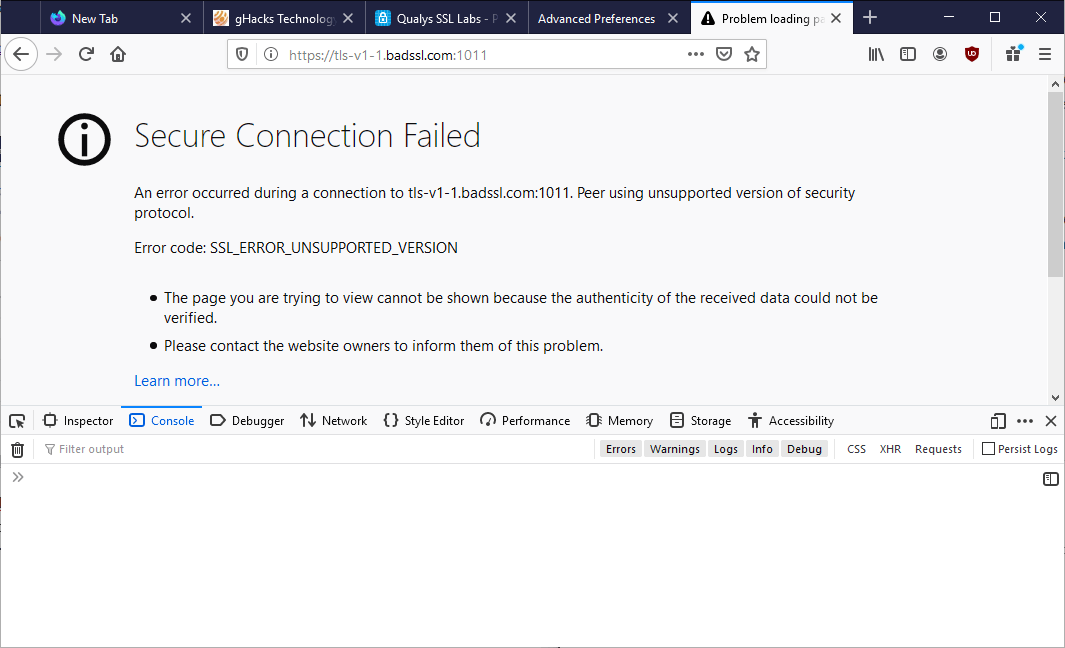
In Firefox, the browser will throw a "secure connection failed" error message with the error code "SSL_ERROR_UNSUPPORTED_VERSION" with no option of bypassing the error (because support for TLS 1.0 and 1.1 is removed from the browser).
Sites that are actively maintained will likely be updated in time to support newer protocol versions so that connections to these sites won't be interrupted.
Some sites, e.g. those that are not actively maintained anymore or cannot be updated to support newer protocol versions, won't work anymore once the change lands. Most Firefox users will see minimal disruption, if any, when Firefox is upgraded to version 74.0.
Firefox 74.0 Stable is scheduled for a March 10, 2020 release.
Now You: Do you know of any device or site that still relies on TLS 1.1 or lower?






















Two devices on my local 192.168.1.xxx address both are not TLS1.2 according to firefox. I think this should be an exemption
how will “upgrading” to v74 impact the use of ghack’s user.js [github?
also
http://www.ghacks.net
CNAME ssl.marfeelcdn.com
CNAME marfeel.map.fastly.net
what fun!
… http://rfc-clueless.org/pages/listing_policy-dsn
ghacks is concerned about privacy but then hosts email via google?
As a bare minimum wouldn’t it be better for us if they instead:
Displayed the website with Javascript Disabled, Interaction Disabled, and possibly somehow Sandboxed.
Perhaps also with a large Banner continuously across the top saying this.
This way at least we could still view information of interest, on certain sites that would (might?) still display it.
Hank
@Anonymous – But Martin said “The same will happen at around the same time in Google Chrome and other major browsers such as Microsoft Edge or Apple Safari.”
Non-government sites has been switch to TLS 1.2 in the past (after 2009) due to opposite against TLS 1.0, what if say some government sites will be 100% HTTPS worldwide or not after switch to TLS 1.2 and later.
“Do you know of any device or site that still relies on TLS 1.1 or lower?”
Yes, I work every day with enterprise equipment that doesn’t support anything greater than TLS 1.1. That equipment is deployed around the world, and it will probably be years until any of it is upgraded.
This meant more people won’t be using Firefox because of that
@Anonymous:
It’s worse than that, because all of the major browsers are doing this. What it actually means is that a lot of companies will have to use older versions of these browsers for these purposes.
“SSL Report: http://www.ghacks.net“, initialized Fri, 10 Jan 2020 13:05:09 UTC : 4 A+ for
151.101.2.207, 151.101.66.207, 151.101.130.207, 151.101.194.207
“https://www.ssllabs.com/ssltest/analyze.html?d=www.ghacks.net&hideResults=on”
Martin, that’s very good, I’ll add some whiskey to your coffee!
Enjoy it. I don’t drink alcohol but I’ll add an extra bit of milk to my coffee this morning to celebrate in style :)
I wonder if there should be a workaround to view TLS 1.0 and 1.1 sites, and just consider them as secure as HTTP.
I think there are still going to be a lot of TLS 1.0 and 1.1 sites around, especially for sites that are still functional and useful but not actively maintained. Furthermore, plenty of sites are still using plain HTTP, including (surprisingly) sites of many software authors, as well as many government sites.
You would think that all software developers and governments would at least be using HTTPS for their sites by now.
About time… Cutting off the connection is the only way to nudge some webmasters to finally update.
For recall, Firefox settings regarding TLS :
security.tls.version.min // Default=1 (FF72)
security.tls.version.max // Default=4 (FF72)
Where 1=TLS 1.0, 2=TLS 1.1, 3=TLS 1.2, 4=TLS 1.3
So at this time min TLS is 1.0
From there on, considering I keep these default values and that I don’t monitor web sites, secured or not, I have no mean to know of any device or site that still relies on TLS 1.1 or lower (given the browser accepts the lowest).
Of course I have in mind switching ‘security.tls.version.min’ to at least 2 (TLS 1.1) but I hesitate given the advice included in Ghacks-user.js stating “[WARNING] Leave these at default, otherwise you alter your TLS fingerprint.”.
I may anticipate on FF74 and switch ‘ ‘security.tls.version.min” to at least 2 (TLS 1.1) if not 3 (TLS 1.2 = FF74), whatever the fingerprinting issues. Not sure the deal is worth it.
@Tom Hawack,
AFAIK, security.tls.version.min doesn’t have an option of “4” (TLS 1.3), probably because it would break alot of site (everything seems to default to TLS 1.2, including ghacks, AFAIK).
I have it set to “3” (ever since I read it here), & I don’t recall any websites not working.
It’s about time Firefox deprecated TLS 1.0 & 1.1, since they’re insecure.
Too bad that all TLS implementations are broken against quantum computing.
Mozilla needs to push for a quantum computing resistant (is anything really quantum computer proof?) update to TLS, since it’s emphasis is privacy. Likewise with Chrome, but unfortunately, Google (as an advertising company) doesn’t care about your privacy.
@notanon, thanks for the info. In any case would I set ‘security.tls.version.min’ to 4 , but only 3 (=TLS 1.2) at the most. You report not recalling any secured website failure within what would be a long period. Counter-argument is fingerprinting but as I wrote it, not sure increased fingerprinting is worth a lowered TLS tolerance. I’m likely to follow your reasoning.
SSL Report: http://www.softonic.com (35.190.13.197)
https://www.ssllabs.com/ssltest/analyze.html?d=www.softonic.com&hideResults=on
SSL/TLS Capabilities of Your Browser
https://www.ssllabs.com/ssltest/viewMyClient.html
SSL Report: http://www.ghacks.net
Grade: F, A+, A+, F
â€Warning: Inconsistent server configurationâ€
https://www.ssllabs.com/ssltest/analyze.html?d=www.ghacks.net&hideResults=on&latest
dig into DNS for an answer
you might find ssl.marfeelcdn.com
thanks NextDNS ;)
“`
SSL/TLS Capabilities of Your Browser
https://www.ssllabs.com/ssltest/viewMyClient.html
“`
This simply analyzes the user-agent string, which many of us spoof.
You should just tell us the exact error that you see.
Strange, I’m getting all A+ ratings https://www.ssllabs.com/ssltest/analyze.html?d=www.ghacks.net&hideResults=on
IP 151.101.194.207 get F with Chrome Version 80.0.3987.42 (Official Build) beta (64-bit)
F
https://www.ssllabs.com/ssltest/analyze.html?d=www.ghacks.net&s=151.101.194.207&hideResults=on
Yes it was strange. I tested again and it failed, then with Safari and I got all A+ ratings. (My previous comment didn’t appear). So this site is secure, of course.
Firefox: Grade: F, A+, A+, F. Then new test failed.
Safari: All A+ ratings and no warning. Conclusion is that your server is secure and there is something wrong with my Firefox.
“Do you know of any device or site that still relies on TLS 1.1 or lower?”
Of course. Most governments are using them and i mean they do not even support TLSv1.2 at all.
Their most lovely ciphersuites are kRSA (which is TLS1.2) without PFS to decrypt the visitors input in realtime.
So if security would be the goal for Mozilla and google they should only leave TLS1.3 to work or dropping kRSA too from their supported ciphersuits.