How to search all Chrome extensions for the dangerous unsafe-eval
In this guide, I will show you how you can search all installed Chrome extensions for the dangerous unsafe-eval content security policy. The method may also work for extensions installed in other browsers provided that the extension files are readable in plain text.
A new scandal surrounding a number of extensions that recorded and sold browsing data of users made the news last week. More than 4 million browser installations were affected this time and it was just the latest in a series of privacy related issues surrounding shady browser extensions.
The extensions in questions used a well documented Content Security Policy directive called unsafe-eval to download the remote payload and start the collecting and transferring of browsing data.
Chrome extensions need to declare unsafe-eval in the extension manifest to make use of it. The Chrome web store does not highlight the use and the extensions are clean otherwise when they are uploaded to the store by the developer.
Raymond Hill, the developer of uBlock Origin described the issue surrounding these malicious extensions that downloaded a payload to the user system after installation in the following way:
For an extension to be able to execute remote code in their own context, they need to explicitly declare `unsafe-eval` in their manifest.json.
In other words: these extensions declared unsafe-eval so that they could download the payload at a later point in time.
Hill recommends that users avoid any extension that declares unsafe-eval; that requires that users check the manifest file of the extension before they hit the "add to Chrome" button, however.

We published a Chrome extensions verification guide in 2015, a good resource to verify any Chrome Web Store extension before installation.
Here is a short overview since you may not want to read the entire long guide.
- Download the Chrome Extension Source Viewer extension.
- Open the profile page of the extension that you want to check.
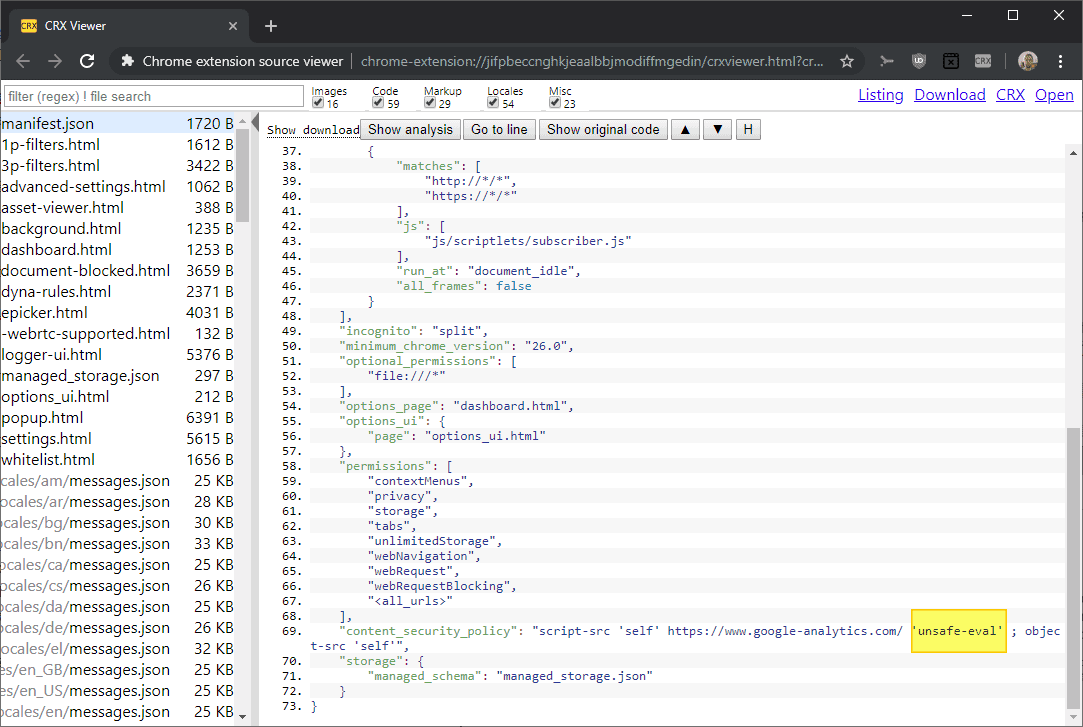
- Click on the CRX icon of the Chrome Extension Source Viewer extension and select "View Source".
- Select the manifest.json file and check for unsafe-eval, e.g. by using F3 to open the on-page search.
What about installed extensions?
While you could open the manifest.json file of each of the installed extensions to find out if any used the unsafe-eval declaration, you may also search across all of them at once to speed up the process.
Here is how that is done:
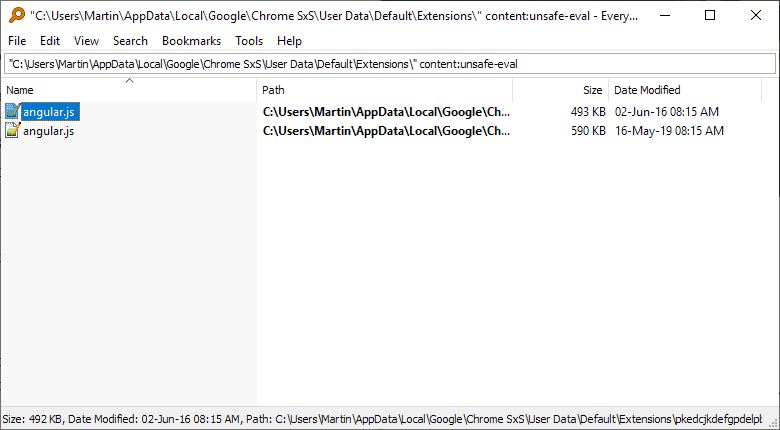
- Download the great tool Everything to your system. You may also use other text editors that support searching file content, e.g. UltraSearch or Notepad++.
- Start the program by right-clicking on it and selecting "run as administrator".
- Select Search > Advanced Search.
- Type unsafe-eval in the "A word or phrase in the file" field.
- Select the c: drive (or the equivalent on your system), or pick the extensions directory right away.
- To find the path, load chrome://version/ in the address bar.
- Copy the profile path value, e.g. C:\Users\Martin\AppData\Local\Google\Chrome\User Data\Profile 1
- Paste it into the "located in" field.
- Make sure "include subfolders" is selected.
- Hit ok.
Everything searches the entire folder structure and all files for the selected phrase. Focus on manifest.json files and double-click on them to open them in the default text editor. Use the built-in search to search for unsafe-eval to verify the finding.
The same method should work for most other browsers.
Now You: do you verify extensions before you install them?




















I use speed dial 2 new tab, and it has unsafe-eval. Should I nuke it?
Thank you Martin for all.
Wanna monetize your amazing knowledge and help the world at the same time?
Create a “Extension Certificate” where you serve as 3 party vendor and certify extensions as safe. I bet millions of users would be HAPPY to pay a reasonable monthly fee for you to say these are safe.
The average Joe doesn’t have the time/ability to do even this simple check you are describing here, on multiple extensions.
I moved our company to nearly totally Chrome OS for security (and expense) reasons. The main hole as you well know: extensions. Someone needs to solve that problem. So far no one has.
I am happy to share some specific ideas about this but we really, really need this!
Mark
After checking my Chrome extensions I found ‘UltraSurf Security, Privacy & Unblock VPN’ to contain unsafe-eval.
Tell me it ain’t so… The NoScript extension for Firefox has “unsafe-eval” in its manifest.
I checked using both the built-in “about:debugging” feature as well as the CRX Viewer extension.
Results: “content_security_policy”: “script-src ‘self’ ‘unsafe-eval’; object-src ‘none'”
I can’t believe such a popular, highly regarded security add-on would break Mozilla’s AMO rule — unless there is some deeper review by AMO that can lead to an exception to the rule.
I’m not going to knee-jerk and disable it at this point but I hope some clarification of AMO’s “rule” is forthcoming.
The first extension I checked out was NoScript 11.0 and I noticed too on line 14:
“content_security_policy”: “script-src ‘self’ ‘unsafe-eval’; object-src ‘none'”
But let’s unzip it and… :D
From a comment in the reddit thread linked above: it seems that Foxy Gestures got special permission to use “unsafe-eval” (and it’s necessary, and it always goes through review), so it’s possible that other developers might have similar arrangements. No word on whether the permission is actually required for content blockers like NoScript.
@kktkkr, indeed, thanks for the link and the information.
As a user I remain puzzled on the attitude to adopt facing ‘unsafe-eval’ declared in a Firefox extension’s manifest.json file :
1- As noted by user 99 above:
MDN web docs states :
“Extensions with ‘unsafe-eval’, ‘unsafe-inline’, remote script, blob, or remote sources in their CSP are not allowed for extensions listed on addons.mozilla.org due to major security issues.”
2- Some extensions such as ‘Heady Editor’ or ‘Foxy Gestures’ appear to have been granted “special permission granted by reviewers” as mentioned in the above mentioned linked reddit thread, maybe on the ground of the reasons mentioned above :
— Anonymous (July 22, 2019 at 2:53 pm)
“Sometimes unsafe eval is needed for frameworks that are not CSP compliant. To create the UI for example (VueJS/Angular…) and of course analytics/trackers. So it doesn’t means it’s an evilly addon.”
— Anonymous (July 22, 2019 at 9:02 pm)
“Remote code is not necessarily evil in extensions. UBlock Origin used to have remote code in the form of the automatic update of its anti-anti-adblock scripts, before Mozilla told the dev to stop doing that. Now they are updated more slowly, only when the extension is, but luckily this pace seems to be fast enough for now according to the dev.”
3- From there on what does a user do when noticing that ‘unsafe-eval’ is declared in a Firefox extension’s manifest.json file? How should he know if the extension has been granted or no “special permission granted by reviewers”? This is unclear, ambiguous.
@Tom Hawack
>>>… appear to have been granted “special permission granted by reviewers†as mentioned […]
Any reliable sources other than an “extension dev” claiming this in a reddit thread?
How the hell I am going to explain this to my browser, that one of them got “special permission from addon reviewers in IRC to use it”?
Think about it loud, you may get the joke …
@99, “Any reliable sources other than an “extension dev†claiming this in a reddit thread?”
Not that I’m aware of. You’ve got a point there. But it could nevertheless be true : spread an information and even if it’s taken with skepticism it’ll install doubt. I believe Mozilla should get this clear for everyone and not only for the add-ons developers because the fact is some add-ons including ‘unsafe-eval’ are available on AMO.
I guess I’ll stick on the refusal of any Firefox add-on which appears to declare ‘unsafe-eval’ in its manifest.json file.
@Tom Hawack
>>>I believe Mozilla should […] because the fact is some add-ons including ‘unsafe-eval’ are available on AMO.
How do you know that both operator
evaland functionevalwill evaluate their arguments – as you keep assuming over and over again?@99, if I understand your comment that would mean that in the case of operator eval and function eval not *both* evaluating their arguments, the ‘unsafe-eval’ declared in an extension’s maniifest.json is not a problem. If so address that to us all, not to me. That is I guess fresh information for most of us here so no point bouncing on our dialog to announce what is beyond it, OK? I’m just following the article and readers’ comments.
>>>If so address that to us all, not to me.
You are always among the first ones to lecture FireFox devs with absolute “should” wordings … without even “investigate” any thought wether they have already taken any measures!
Instead you are referring to a useless (Let alone the impressive list of ‘False positives’!) reddit comment – where the dev can’t distinguish between ‘JavaScript APIs for WebExtensions’ permissions and ‘Content Security Policy (CSP)’ directives – as “But it could nevertheless be true”. Oooops!
How the hell can I address anything to someone, who has stressed that he prioritizes sermonizing over >simple facts?
… throw macaronis, melons and figs upon him?
@99 I’m not assuming anything but only trying to practice what I’ve understood from the article which is that
– if ‘unsafe-eval’ is declared in an extension’s manifest.json file then that extension should be avoided,
– to find out later that MDN web docs states that “Extensions with ‘unsafe-eval’, ‘unsafe-inline’, remote script, blob, or remote sources in their CSP are not allowed for extensions listed on addons.mozilla.org due to major security issues.â€
– whilst some add-ons listed on AMO do declare this ‘unsafe-eval’
– not to mention a developer declaring on reddit that some extensions have been granted “special permission” by reviewersâ€.
If the problematic is deeper nested and complex then I’d be happy it be explicitly detailed.
I’m trying to understand what appears to a novice a contradictory, no assumption nor message.
I’m not on a coding contest, don’t consider it that way, formal logic on my part, no more.
Remote code is not necessarily evil in extensions. UBlock Origin used to have remote code in the form of the automatic update of its anti-anti-adblock scripts, before Mozilla told the dev to stop doing that. Now they are updated more slowly, only when the extension is, but luckily this pace seems to be fast enough for now according to the dev.
I’m more worried of the arbitrary remote code execution capabilities of Mozilla in my browser than in my trusted UBO, because the former have already been misused to install malware like the Cliqz experiment.
Someone compiled a list of firefox addons on reddit: https://old.reddit.com/r/firefox/comments/cgfl6e/list_of_addons_that_use_unsafeeval_or/
Keep Google Chrome Extenstion by Google uses this ‘unsafe-eval’ code as described in article.
Scanned an old profile I no longer use, a couple of extensions there get flagged:
Honey – https://chrome.google.com/webstore/detail/honey/bmnlcjabgnpnenekpadlanbbkooimhnj?hl=en
Super-highlight-search – https://chrome.google.com/webstore/detail/super-highlight-search/mnnlboenenpikhopbchpjikllhibfocl?hl=en
The situation is so bad that they need to hide it from everyone, gorhill literally blew the whistle on this and they asked him to delete his tweets too, lol
I sent abuse report for ‘mozlz4-edit’ and ‘Foxy Gestures’. I hope they took them down. Please sent reports for any other breaking AMO rules addon you find. Let’s drain the swamp together!
@Anonymous, @99’s (July 22, 2019 at 4:11 pm), that’s the point.
99 reports MDN’s web docs stating that “Extensions with ‘unsafe-eval’, ‘unsafe-inline’, remote script, blob, or remote sources in their CSP are not allowed for extensions listed on addons.mozilla.org due to major security issues.”. So why are add-ons trespassing this rule available on AMO?
I think you’re right, coherent to report theses 2 extensions (‘mozlz4-edit’ and ‘Foxy Gestures’) and I’m really looking forwards to know Mozilla’s answer.
Because either two things : or MDN’s web docs statements are strict either they are guidelines. Now, if reality is that an extension can declare ‘unsafe-eval’ without using in a way which would concern users’ security then Mozilla should say so and declare that there is a per-extension tolerance.
Whatever, this is not clear, ambiguous.
@Tom Hawack
>>>So why are add-ons trespassing this rule available on AMO?
You may declare
'unsafe-eval'as an “allowed source” in ascript-srcdirective, like it seems possible in Chrome extensions. Declared in Firefox extensions, I assume it’s invalid, because potentially unsafe practices such as the use of → eval() and friends are disallowed by default.'unsafe-eval'Allows the use of
eval()and similar methods for creating code from strings.That may the case in dependency of older JavaScript libraries or the extension developer still using the incredibly inefficient
eval()instead of the similarFunction, wich is not susceptible to execute unauthorized code.In case
evaland its text-to-JavaScript are essential to an extension, a user should consider twice, if this extension is essential for his daily browsing habits, because the developer never heard ofDo not ever use eval!
Banning the ability to execute strings makes it much more difficult for an attacker to execute unauthorized code in a browser … unless the dev is the attacker himself.
@99, interesting information, thanks.
I’ve replaced ‘Foxy Gestures’ by ‘Gesturefly”, free of ‘unsafe-eval’ in its manifest.json but on another hand requiring ‘dom.w3c_pointer_events.enabled’ to be set to true (default) as opposed to Ghacks-user.js recommendation. I’ll miss Foxy Gesture’s ability to tie a script to a gesture, but otherwise ‘Gesturefly’ is nice as well and weighs 1/4 of its competitor.
I’ve replaced ‘mozlz4-edit by ‘Add custom search engine’, free of ‘unsafe-eval’ in its manifest.json
You discover and learn every day.
Martin, Rob W.’s Extension Source Viewer is also available for Firefox.
Install it, go to AMO, load the AMO site for any add-on you’re interested in and click the CRX button in the address bar.
You can choose to download the extension as a zip file or to view the source code. I always select the latter which opens in a new tab.
In the search filed in the upper left corner you should enter !unsafe (or more specifically: !unsafe-eval or !unsafe-inline). The ! makes sure that CRX searches in all files of the extension.
I used Thomas Tempelmann’s “Find-Any-File” on my Mac to search file contents for “unsafe-eval.” There were two references to it in the Firefox app folder (XUL (Unix executable) and omni.ja (document).
I use the “Adblock Plus”, “CanvasBlocker”, “Privacy Badger” and “Pure URL” extensions but I don’t see any reference to “unsafe-eval” associated with any of them.
Great article, most valuable information.
I had a look over my 47 Firefox add-ons and discovered two (2) whose manifest.json file declares ‘unsafe-eval’ : ‘mozlz4-edit’ and ‘Foxy Gestures’. Removing them, especially the latter, bothers me.
If ‘unsafe-eval’ enables an extension to execute remote code in its own context does it mean that is has no pros facing this con? Is ‘unsafe-eval’ systematically harmful or is it what can be done with it?
Removing ‘Foxy-Gestures’ really bothers me, it’s the best of its category IMO.
MDN web docs
content_security_policy – Mozilla | MDN
Compare this with the Chrome Content Security Policy (CSP)
Tom, unsafe-eval does not say anything about whether an extension is malicious or not, it merely gives the extension the ability to execute remote code.
@Martin, what I meant was referring to the legitimacy of ‘unsafe-eval’, in that it could or not be available for good reasons even if it has the potential of being used for the worst.
Anonymous’ comment above (July 22, 2019 at 2:53 pm) fits in my wondering.
Sometimes unsafe eval is needed for frameworks that are not CSP compliant. To create the UI for example (VueJS/Angular…) and of course analytics/trackers. So it doesn’t means it’s an evilly addon.
I personnally had my code been reviewed by mozilla a couple of times for obfuscated code. So I feel pretty safe with Firefox.
@Anonymous: “and of course analytics/trackers”
Including analytics/trackers is pretty evilly, though.
More info https://news.ycombinator.com/item?id=20492449
I am a bit confused about this. I ran the search in the extensions folder and found that I have 6 files that have unsafe-eval, of which there are 3 related to uBO: Easylist.txt, unbreak.txt, filters.txt.
Then there are 4 angular.min.jsm files that are related to the Decentraleyes extension.
Martin said to focus on manifest.json files, so it safe to assume that non-manifest.json files that have unsafe-eval are safe?
The filter lists have nothing to do with that, e.g. easylist.txt. Ignore those.
I just did this check manually, having very few extensions installed, but it turns out one of them had unsafe-eval: the previously reviewed “Tabs limiter with queue”.
I’ve disabled it for now as it wasn’t essential, but there doesn’t seem to be a replacement with equivalent functionality.
This tweet had a foolow-up thread https://twitter.com/dangoodin001/status/1151999791338889216 , explaining that `unsafe-eval` is not even needed, because Chrome includes “some” undocumented CSP directives by default which allows to execute code anyway.
Gorhill created issue about this: https://bugs.chromium.org/p/chromium/issues/detail?id=985759
The link to Gorhill’s issue first asks me to log in with my Google account and then throws “Permission denied” at me…
———————————————————————————–
What happened?
You do not have permission to view the requested page.
Reason: User is not allowed to view this issue.
———————————————————————————–
Must be a quite serious issue then…
I think it’s blocked for PR reasons.
do I have to comment in order to unsubscripe/change subscription options?
Manage your subscriptions: https://www.ghacks.net/subscription-management/?srek=xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx&srk=xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
shows me only a blank page
No need for that, try again please and let me know if it works now (reload page).
yes, it works, thanks!
wow! video downloader plus has unsafe-eval! should we ditch it?
unsafe-eval is necessary to let some extensions work. I meant it’s imposible at all to release some functionality without the unsafe-eval. As an example many of JavaScript template engines and frameworks as Angular demands unsafe-eval if you use it in extensions.
There are so many “video downloader plus” extensions offered by different entities, to the point where this alone should be a red flag. Use youtube-dl instead. It’s a free and open source cross-platform command-line based program, which despite its name is capable of downloading from many websites. I tried it on YT and VK and it works perfectly.
My only two extensions are uBlockOrigin and uMatrix, installed from github. So I don’t have to check them, I trust gorhill enough.
same, I would send my data to gorhill anytime :)