Firefox Shield study to import Windows root certificates
Mozilla wants to evaluate the impact that the importing of Windows root certificates has on Firefox.
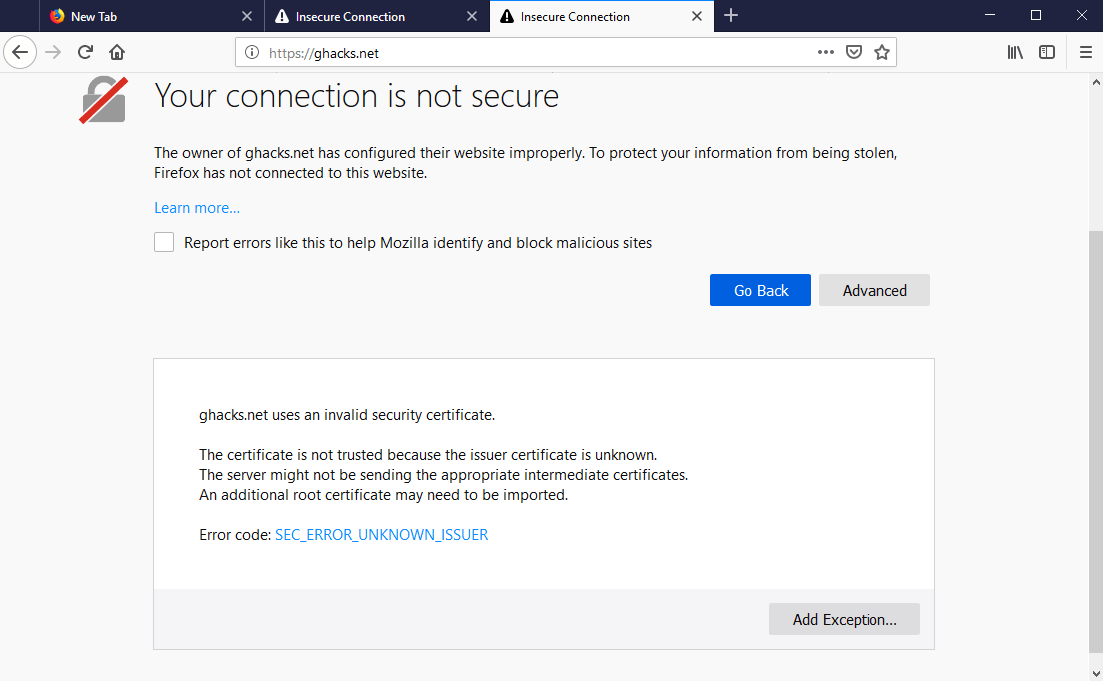
Firefox uses its own certificate store when it validates certificates of site connections by default. While that is beneficial in regards to control that Mozilla has over certificates, it recently introduces an issue that caused connections to secure sites to fail in the browser.
Mozilla had to halt the distribution of Firefox 65 to address the issue. The issue was caused by third-party antivirus engines that installed their own certificates into the Firefox certificate store to enable SSL scanning.
Firefox users would receive "your connection is not secure" and "SEC_ERROR_UNKNOWN_ISSUER" connection errors if affected by the issue.

Users could disable HTTPS scanning in the antivirus solution of choice or flip a preference in Firefox that would allow the browser to import certificates from the Windows Certificate store to mitigate the issue.
Mozilla discovered that the issue could have been prevented if Firefox would use certificates from the Windows Certificate store.
Mozilla wants to find out if using certificates from the Windows Certificate store has any negative effects on Firefox. The assumption is that there won't be any ill-effects; if that is the case, Firefox will import Windows root certificates by default going forward.
The security team confirmed that having the preference security.enterprise_roots.enabled set to true would have fixed all of these issues without known regressions and we want to validate that in the presence of an AV, enabling this preference would have a positive impact on retention and engagement
The parameters of the Shield study:
- Version: Firefox 66
- Platform: Windows 8.1 and Windows 10.
- Other: Antivirus installed that is not Windows Defender.
A test group and a control group is selected. The test group will have the preference security.enterprise_roots.enabled set to True while the control group won't. The default value of the preference is false.
The preference defines whether Firefox will use certificates from the Windows Certificate store (True) or not (False). The parameter has been added in Firefox 49 with a default value of False.
Telemetry will be collected to determine the impact of the preference change. Firefox users who don't want certificates from Windows to be imported can set the parameter to False to prevent that from happening.
Now You: Did you run into SSL connection issues recently? (via Bleeping Computer)






















Allowing an anti-virus solution man-in-the-middle access is the most stupiest thing in the first place. Same for having a root certificate store trashed with CA certificates. If a CA certificate is missing in the store, the Web browser will download anyway; and the user is in charge whether to install or not. Unfortunately, nobody tells users how things work and how to properly set up a secure computer.
I think Mozilla should work on disabling ‘Permanently store’ invalid certificates by default. For years I’ve been wondering why this is default practice? Other browsers don’t do this
@Anonymous: Being able to permanently allow invalid certs is something I consider extremely important for certain of my use cases. I sincerely hope they don’t remove that, as it would make the browser unusable for me.
However, it would be fine if they made it more difficult to do (after all, you shouldn’t do it unless you really know what you’re doing), just so long as it was still possible.
@John Fenderson
I didn’t mean to disable the function. I want them to make the checkbox to store the certificate to be ‘off’ by default. It’s not a good thing to trust self signed/broken certificates blindly.
@Anonymous: Ah, I misunderstood your comment. Reading it again, I was clearly having a brain malfunction. Thank you for the clarification!
Would they eventually enable this functionality [not the study] on Windows 7 too?
If so, what happens if a root certificate gets compromised, but the Windows system does not receive updates to have it removed? Would Firefox still use it?
@Nick Venenga: “I don’t see why this is an issue unless you don’t trust Microsoft’s cert store”
No cert store should be blindly trusted because no root certs should be blindly trusted. That said, Mozilla’s has long been more trustworthy than Microsoft’s, as Mozilla take more care to curate the certs in theirs.
I think this makes a lot of sense. Linux-native software tends to try to copy/paste the Linux way of doing things over to Windows and you end up with each piece of software trying to manage it’s own cert store and it becomes a nightmare if you want a certificate to be universally trusted. On Linux, most software uses the OS-wide cert store so I don’t see why this is an issue unless you don’t trust Microsoft’s cert store. If that’s the case, I would imagine you have manually modified it or don’t use Windows to begin with (since various pieces of the OS also use that cert store and tons of other software)
The root cert situation generally is problematic from a security point of view, and more so if we accept Windows root certs. I understand what Mozilla’s thinking is here, but it makes me very nervous. On the other hand, the cert problem is such that I’m not sure if accepting Windows certs makes the situation so much worse that it matters.
So, color me ambivalent.
Very useful to know, toggling this setting has finally resolved this issue for me with FF and Bitdefender free antivirus – which has persisted through many FF version updates. Bitdefender support were unable to resolve the issue.
I haven’t ran into SSL connection issues with Firefox, be it recently or as far as I can remember, for reasons pertinent to a certificate issue. But, 1- “Don’t get around much anymore” as the song puts it, and 2- I don’t run third-party antivirus engines or whatever code interfering in Firefox’s certificates.
What bothers me in this study, possibly becoming factual, to import Windows root certificates is a link once again to Microsoft. Fortunately as long as the preference security.enterprise_roots.enabled exists that link won’t be mandatory.