Microsoft: phishing up, ransomware down in 2018
Microsoft published the company's Security Intelligence Report for the year 2018 recently; the security data analysis provides an insight into major threat types in 2018.
In short: ransomware is on a decline, phishing is on the rise, crypto-mining is prevalent, software supply chains are a risk, and overall malware decreased in 2018.
Phishing
Phishing remains one of the top attack vectors used to deliver malicious zero-day payloads to users, and Microsoft has continued to harden against these attacks with additional anti-phishing protection, detection, investigation, and response capabilities to help secure users
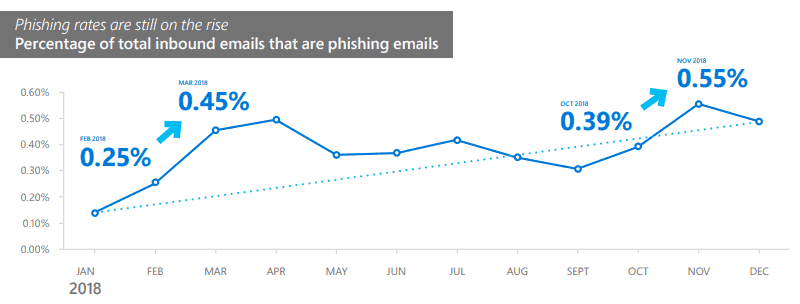
Phishing messages increased by 250% between January and December 2018 according to Microsoft. The company scanned more than 470 billion email messages for malware and phishing monthly in 2018.
Phishing methods evolved further in 2018. Microsoft notes that attackers use more sophisticated methods to make attacks more powerful. The times of using single URL, domain, or IP addresses to send emails are long gone as attackers moved to "a varied infrastructure with multiple points of attack".
The nature of phishing campaigns changed as well. Attackers use different delivery spans and schedules, and rely more on using hosted infrastructure and cloud services in their attacks to make detection difficult.
Different phishing types
- Domain spoofing -- email message domain is an exact match of the expected domain name,
- Domain impersonation -- email message domain looks similar to the expected domain name.
- User impersonation -- impersonating a trusted user.
- Text lures -- text that looks as it if comes from a legitimate source.
- Credential phishing links -- email links to a page that looks legitimate.
- Phishing attachments -- the phishing email includes an attachment with malicious payload.
- Links to fake cloud storage locations -- asks users to give permissions or sign in to access cloud content.
Ransomware
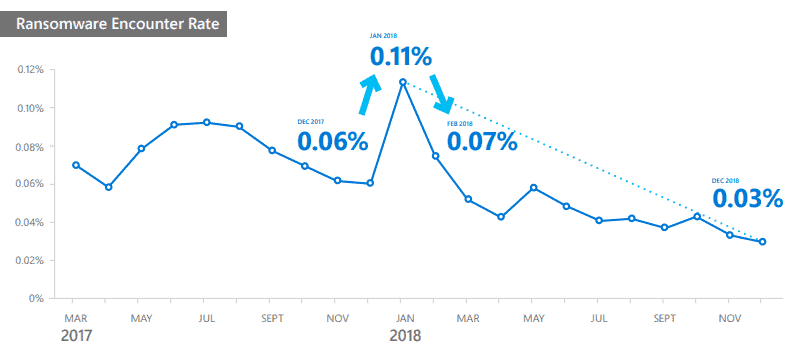
The decline in ransomware encounters was due in part to improved detection and education that made it more difficult for attackers to profit from it. As a result, attackers began to shift their efforts away from ransomware to approaches such as cryptocurrency mining, which uses victims’ computing resources to make digital money for the attackers.
Detected ransomware attacks dropped by approximately 60% between March 2017 and December 2018. Microsoft suggests that user and organization awareness and improved protection and detection options played a role in the decline.
Cryptocurrency Mining
In 2018, the average worldwide monthly cryptocurrency coin mining encounter rate was 0.12 percent, compared to just 0.05 percent for ransomware
The change to encounter coin mining attacks was more than two times as high as encountering ransomware in 2018. The average worldwide cryptocurrency coin mining encounter rate was 0.12% in 2018.
One major factor that played a role was the rise of in-browser mining operations; these don't require user input and work on the majority of setups out of the box (blocking JavaScript is an effective option).
Supply Chain Compromise
The first major software supply chain attack incident of 2018 occurred on March 6, when Windows Defender ATP blocked a massive campaign to deliver the Dofoil trojan (also known as Smoke Loader). The massive malware campaign was traced to a poisoned peer-to-peer application.
Supply chain attacks focus on attacking development or update processes to "incorporate a compromised component" into legitimate applications or update packages.
Incident examples:
- Dofoil trojan mining in March 2018.
- Compromised Chrome extensions that installed malware.
- Compromised Linux repositories.
- Malicious WordPress plugins.
- Malicious Docker images.
- Compromised scripts.
Malware in 2018
The five locations with the highest malware encounter rates during the January–December 2018 period were Ethiopia (26.33 percent average monthly encounter rate), Pakistan (18.94), the Palestinian territories (17.50), Bangladesh (16.95), and Indonesia (16.59), all of which had an average monthly encounter rate of approximately 16.59 percent or higher during the period
Malware encounter rates dropped from an high at about 7% in 2017 to "just above" 4% in the end of 2018.
Now You: What has your experience been in 2018?




















“The company (Microsoft) scanned more than 470 billion email messages for malware and phishing monthly in 2018.” What did they do to the known malware that was discovered? Did they remove it, or did allow it to be delivered, to see what would happen?
The paper’s most interesting data is about threats in rich western nations (US, Europe, Japan, Australia, Canada, Iceland, etc.). Let’s see:
Ransomware: 0.02%
Cryptomining: 0.02%
Web-Cryptomining: Down to 0% a the end of 2018
Malware: 1.82%
Phishing: No data
I’d say our web is essentially sterile nowadays. This is in part due to new Windows Software, but also Google Safe Browsing https://transparencyreport.google.com/safe-browsing/overview?hl=en
Security companies always use the numbers from Russia, Pakistan, India, Northern Africa and China to scare rich people in the west out of their money.
The only real problem is malware, and the most prevalent purpose of malware is to somehow get people to see ads. It’s annoying, but it isn’t really risky.
“the most prevalent purpose of malware is to somehow get people to see ads. It’s annoying, but it isn’t really risky.”
No, the most prevalent purpose of malware is to collect data, with major operating systems and browsers and popular mobile apps, and the risk of that is largely underestimated.
Not necessarily true.
1) https://resources.malwarebytes.com/files/2019/01/Malwarebytes-Labs-2019-State-of-Malware-Report-2.pdf
2) https://imgur.com/a/itFpKVA
Adware is the #1 threat for consumers, and also a big threat for businesses, according to malwarebytes.
And even so-called Trojans which are not classified under adware are often nothing but adware. Just look at the mobile trojan “Shedun” which was used to serve ads on smartphones.
Why is this so? Because it is actually extremely hard to make enough money with anything but ads, except in the business sector (where you make money with social engeneering).
My theory: Majority of practical threats for consumers are adware, but this is disguised by the interests of the security industry in the consumer sector.
What I mean is that their report does not consider the larger prevalence of malware that collects data but is not illegal (except maybe under GDPR), including Windows 10 and Android operating systems, and all the “respectable” software that considers it either a fair form of payment or its natural right to collect everything it can, sometimes stealing legal consent with dark patterns. Apparently, they can be sued for blocking malware that’s not illegal. And the very needed privacy laws to outlaw that kind of very prevalent malware often don’t exist yet, or like GDPR, are not seriously enforced yet even on the worse offenders.
Besides, I’m not even sure that their definition of adware implies no data collection for ad targeting.
Yes, everyting is about data after all, and the big corporations want to make sure to protect “their” user base from all competition, illegal and legal. Most often they fight harder against the legal competition than the black hat threats.
“Yes, everyting is about data after all, and the big corporations want to make sure to protect “their†user base from all competition, illegal and legal.”
No, in addition to spying on their users, big corporations do *not* protect them from spying “competitors”. They do often take a cut from the sales of third-party malware, that should therefore be seen more as their partners in crime. One example :
https://www.gnu.org/proprietary/proprietary.html#M201902140
“The AppCensus database gives information on how Android apps use and misuse users’ personal data. As of March 2019, nearly 78,000 have been analyzed, of which 24,000 (31%) transmit the Advertising ID to other companies, and 18,000 (23% of the total) link this ID to hardware identifiers, so that users cannot escape tracking by resetting it.
Collecting hardware identifiers is in apparent violation of Google’s policies. But it seems that Google wasn’t aware of it, and, once informed, was in no hurry to take action. This proves that the policies of a development platform are ineffective at preventing nonfree software developers from including malware in their programs.”
Their report on major threats forgot that part :
https://www.gnu.org/proprietary/malware-microsoft.html