Google Public DNS supports DNS-over-TLS: but you probably can't use it right now
Google revealed last week that it added support for the privacy feature DNS-over-TLS to the company's public DNS service Google Public DNS.
Google launched Google Public DNS in 2009 at a time when many Internet companies started to hop on the DNS bandwagon. Some companies exited the DNS business again, Symantec retired Norton ConnectSafe (DNS) in 2018, while others such as Cloudflare, Verisign, Quad9 DNS or AdGuard DNS launched in recent years.
Google claims that its service is the "world's largest public Domain Name Server (DNS) recursive resolver"; it turns domain names into IP addresses required for communication on the Internet.
DNS-over-TLS and DNS-over-HTTPS are two approaches to making DNS requests more private by using encryption. One of the main differences between the two implementations is the port that is used. DNS-over-TLS uses port 853, DNS-over-HTTPS the standard HTTPS port 443.

Mozilla started to experiment with DNS-over-HTTPS in recent development versions of Firefox already, and it is likely that other browser makers and DNS provider will start to support these privacy features eventually as well.
Google implemented the DNS-over-TLS specification outlined in RFC7766.and suggestions to improve the implementation; Google's implementation uses TLS 1.3 and supports TCP fast open, and pipelining.
Most experts would probably agree that encrypting DNS to improve privacy and security, e.g. from tampering, is beneficial and desirable.
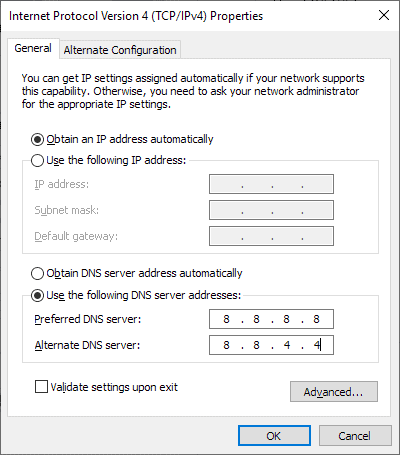
The main issue with Google's implementation at this point in time is that it is not widely available. It is supported on Android 9 devices only at the time officially, and as a stubby resolver for Linux.
Google's implementation guideline highlights for Windows and Mac OS X that the operating systems don't support DNS-over-TLS by default. The only option at this point to add support would be to set up a proxy resolver according to Google.
Windows users may use something like Simple DNSCrypt to encrypt DNS traffic
Closing Words
Users who use Google DNS already benefit from google's implementation of DNS-over-TLS provided that it is supported on their devices or set up using proxies. Users who don't trust Google or don't want to send all their DNS traffic to Google won't start using Google Public DNS because encryption does not change that.
Now You: Which DNS provider do you use, and why?





















LOL at all those people using mainStrasse G00gle and CloudFlare botnets. You’re totally monitored on DNS by these NSA-backed enterprises.
According to Bleepingcomputer.com in an article concerning a weakness in the Telegram app, quote: “…TLS alone is not enough to ensure robust encryption by today’s secure communication standards…”
https://www.bleepingcomputer.com/news/security/flaw-in-telegram-reveals-awful-opsec-from-malware-author/
dns.adguard.com
See https://adguard.com/ for details.
I use it in my home router, so all home devices block ads, and in my smartphone when I’m away.
Highly recommended.
I use 1.1.1.1 & 9.9.9.9 partially for ease & partially cause Im unsure whats best.
I would like to thank Martin & all of the other many gHack geniuses for
enabling me to be informed about the many ways of surveillance is used against me..
Cloudflare’s 1.1.1.1 & 1.0.0.1 is faster than Quad9’s 9.9.9.9 & 149.112.112.112 but the latter is meant to include security (“The system uses threat intelligence from more than a dozen of the industry’s leading cyber security companies”) and exclude profit (“Quad9 is a nonprofit organization, with no commercial motivation or desire to profit from or distribute data which we believe to be private and vital to an open and free Internet.”). Both quotes are from Quad9.
btw, I use cloudflare for now, it’s fast. And test with their url:
https://www.cloudflare.com/ssl/encrypted-sni/
The bromite browser, a chromium variant, supports dns over https (doH).
FF64 for android or desktop does as well, but also has encrypted server name identifier (esni).
Both browsers work on android version 4.1
doH has its advantages in getting past local controls..
Unbound on the Raspberry Pi (running raspbian) is a cheap and reliable DNS forwarding solution for your LAN.
Change your gateway router (if possible) or client settings. Nslookup should show you what DNS resolver is in effect.
IPREDATOR DNS servers
One of the most important parts of a working Internet is an uncensored DNS. We run a pair of public resolvers which provide access to the ICANN root zone.
Servers for IPv4:
194.132.32.32 (supports dnscrypt, see below)
46.246.46.246
Servers for IPv6:
2001:67C:1350:DEAD:BEEF::246
2C0F:F930:DEAD:BEEF::32
A dedicated set of DNS servers is available for use when connected to the VPN.
Servers for IPv4:
194.132.32.23
46.246.46.46
Servers for IPv6:
2C0F:F930:DEAD:BEEF::23
2001:67C:1350:DEAD:BEEF::46
DEAD BEEF LOL You sure this is better than Google spyware DNS? I’ve been using Cloudflare lately. I would not be surprised if Cloudflare does as much tracking as Google and the data goes to the same people, there isn’t really any guarantee with any of these companies. If they are in a Five Eyes country they are forced to cooperate with the government… or in the case of Google ARE the government.
“Which DNS provider do you use, and why?”
I use my ISP’s DNS, because while I don’t trust my ISP, I don’t know of a consumer-level DNS provider that I have any greater level of comfort with. The offer of encrypted DNS that doesn’t use HTTPS would be enough to get me to change, though! I may not trust the DNS provider, but at least it would reduce the attack surface.
I very much prefer DNS-over-TLS over DNS-over-HTTPS! I hate to root for Google, but in this case, I hope that their effort succeeds over Mozilla’s.
“I very much prefer DNS-over-TLS over DNS-over-HTTPS!”
Why ?
Because shoving everything through HTTPS is a terrible idea with problematic security implications. It’s better to have distinct services run on distinct ports. Using TLS for this is itself a compromise, but one that makes a little more sense and is a little more manageable than doing it through HTTPS.
My ISP’s DNS services unless I’m using a VPN, then theirs.
I’ve used some others, AdGuard’s and whatever showed up in DNS Switcher in an attempt to speed up DSL a few years ago.
The issue I’ve had with brewing my own DNS is remembering how it was set up if something goes wrong and being able to troubleshoot if DNS resolvers are at fault when connections get slow or drop. No DNS service is completely reliable; it’s easier to let your ISP or VPN provider fix the problem.
Associating any google product with the word “privacy” is immediately suspicious. Google doesn’t provide services to a user’s ISP or all the free DNS companies? They have a long row to hoe to be considered trustworthy.
I manage DNS servers together with blocklists with the ‘Acrylic DNS Proxy’ application.
Concerning the DNS servers here are those I’ve fed Acrylic with:
; ADGUARD DNS : 176.103.130.130 & 176.103.130.131
; BOUYGUES TELECOM : 194.158.122.10 & 194.158.122.15 (my ISP, but non-default)
; CLOUDFLARE : 1.1.1.1 & 1.0.0.1
; FRENCH DATA NETWORK : 80.67.169.12 & 80.67.169.40
; QUAD9 : 9.9.9.9 & 149.112.112.112
In practice I use essentially ADGUARD DNS and FRENCH DATA NETWORK, never Cloudflare, seldom Quad9
I’ve been a user of DNSCrypt-proxy for quite some time but switched to Acrylic mainly for an easier management of blocking lists, because I happen to give more importance to blocking lists then to encrypted dns requests, where I could be wrong.
I have been using Quad9 for quite a while on Windows 10. I suggest reading https://www.quad9.net/private-dns-quad9-android9/ for caveats they have found for Android.
@Martin,
> “It is supported on Android 9 devices only at the time officially, and as a stubby resolver for Linux.”
Also macOS and Windows has been tested and is supported. See https://github.com/getdnsapi/stubby#installing-using-a-package-manager
`stubby` works very well as a standalone however another option is using `unbound` in a certain local network configurations with a DNS caching/forwarding setup. e.g. multiple computers… one forwarder and just point the rest to that localnetwork/localdomain DNS, then voila. :)
Haven’t tried `stubby` on Android at all especially when “roaming” outside of local network though. That might be useful to link in when found for those staring at their tiny screens. ;) :)
CloudFlare, among some others with other features like “parental control” filtering or other filtering, is also available as an alternative to the actual authoritative DNS. So far I prefer CF because it is unfiltered.
https://github.com/jedisct1/dnscrypt-proxy
That’s all you will ever need. All platforms supported. Lots and lots of servers to choose.
My doubt with this is whether this servers are trustworthy or not.
Just a blunt example, but how do I know that every request I make is pointing me to the actual website I want to go to? I’d have to check all of them manually.
Let’s say I want to go to Paypal.com, I’d have to double check what dnscrypt resolves is actually the IP I want to go to.
Or is there some sort of easier way to check this?
DoT via. Google – the joke of the year, for what DNS encrypt when the requests end up with the largest data octopus again.
https://dnsprivacy.org/wiki/
CloudFlare DNS ftw!
As mentioned before, I’ve found that setting up the unbound DNS forwarder on my Raspberry Pi (running Raspbian) has been very reliable; it is very low power consuming and can be used for all LAN devices. Cloudflare DNS seems to be very fast and stable.
You may have to set your client IP settings to manual if your gateway router isn’t flexible enough (lookin at you Comcast).
So how does it work?
Setting 1.1.1.1 will automatically use encryption? How to check that requests are encrypted when this DNS provider is selected?
Also, in case of VPN, would you override your VPN provider DNS with Cloudfare 1.1.1.1 (if it’s encrypted, I assume is better, as never trust any VPN provider).
> “Setting 1.1.1.1 will automatically use encryption?”
Not quite. You must use an intermediate resolver to divert the DNS port to DoT. `stubby` is covered in another comment as soon as it is approved with the URL reference. There are a few others as well.
However using that IP will use CloudFlare instead of your ISP’s. *(or VPNs)* … so it is a step in the right direction, usually on a router. Not sure if any router natively supports DoT yet… but there may yet be other options not found.
In other words, for quickstart and amateurs reading these comments (count me in), the options are (for the lesser evil thus skipping google but agreeing to the ‘honesty’ of Cloudfare):
HOME
On you router:
good: Set your DNS provider on your Wi-Fi router to 1.1.1.1 (Cloudfare)
results: DNS still in plaintext but visible by Cloudfare (not your ISP)
better: Set up encrypted resolver, DNS over TLS (DoT) with 1.1.1.1 (Cloudfare do not support DoH or DNS over HTTPS). For this, you will require a 3rd party app, some listed here:
https://dnsprivacy.org/wiki/display/DP/DNS+Privacy+Clients
results: encrypted DNS with company which is not your ISP
If router configuration does not allow it and installation of third party program to windows is not your cofee, the third option is:
Set up DoH in your browser on every single device, say Firefox. Not sure which resolver to choose then (Cloudfare says 1.1.1.1 dies not support it). Instruction somewhere
Once outside, where DNS comes from your Mobile provider and Starbucks, you have to set it up in your VPN program. Either trust VPN DNS providers, or somehow configure device to use VPN but transfer DNS say via 1.1.1.1 but that is bigger topic to cover here.
@curious
Good summary. :)
Regarding some other reply in this plethora of comments someone mentioned a link to setting “Private DNS” in Android: Unfortunately in a check of it Samsung’s flag ship doesn’t appear to have that option yet *(at least in this version of the phone software I get… not rooted)* e.g. they only have a DNS primary and secondary. So this is where DoT can be useful via `unbound`… and again at very least a router skipping your ISPs if chosen.
Loading a third party app, especially via the Google Store, seems “leaky” on startup as someone else noted in a link. But if it is the best that one can achieve it’s better than nothing I suppose.
So the `unbound` option will encrypt the phone while not traveling since can be pointed to that DNS forwarder.
`unbound` should allow one to multi-task requests between a list of upstream resolvers so you can fragment your requests to make logging a bigger chore.
Who you trust is your own decision but if you get bored/challenged use them all, a portion of them, or just your ISP.
Keep in mind that DoH may bottleneck HTTP/HTTPS and they aren’t the only well-known protocol in TCP/IP stack ports.
When I configured DoH in Firefox, my VPN provider is refusing the connection.
I see all 4 TRR entries as false in about:networking#dns and also when Firefox mode is forced (trr.mode value = 3) I cannot resolve any website. This test proves that it is not working.
That means that browser configuration has its limit if VPN provider is blocking DoH – in my case might be my VPN proxy (work one).
Any advise? Am I doing something wrong? I used Cloudfare provider.