Chrome's inline extension install ban already bypassed
Developers of Chrome extensions had two main options when it came to getting Chrome users to install their extensions for the browser.
They could rely on the Chrome Web Store presence and link to it from third-party sites to get users to install the extension or use inline installations instead.
Inline installations kept the install process on a third-party website; convenient on the one hand as it meant that users could install the extension from the developer's website or another third-party site. Problematic on the other as the system was abused by malicious actors to push installations of extensions.
All it took was to upload the extension to Chrome and integrate it on third-party websites so that the extension would install without users leaving that site or having to visit the Chrome Store. Malicious actors used various methods to push extensions to user versions of Chrome that way.
Google revealed in early 2018 that it would add more protections against deceptive inline installations by retiring the functionality in June 2018.

Retirement of inline installation functionality meant that extension developers could no longer push extension installations directly on their sites if the extensions were hosted on the Chrome Web Store.
Chrome extensions need to be installed from the Chrome Web Store website but that has not kept malicious developers from pushing extensions on to user systems.
While they can't use inline installations for that anymore, they soon came up with an ingenious workaround as reported by Bleeping Computer that works similarly.
Users are asked to click on an install button on the third-party website to start the process. The site loads the Chrome Web Store page the extension is hosted on in a popup and places it on top of the loaded webpage in a way that only some information on the Chrome Web Store page such as the title of the extension and the "add to Chrome" button are visible.
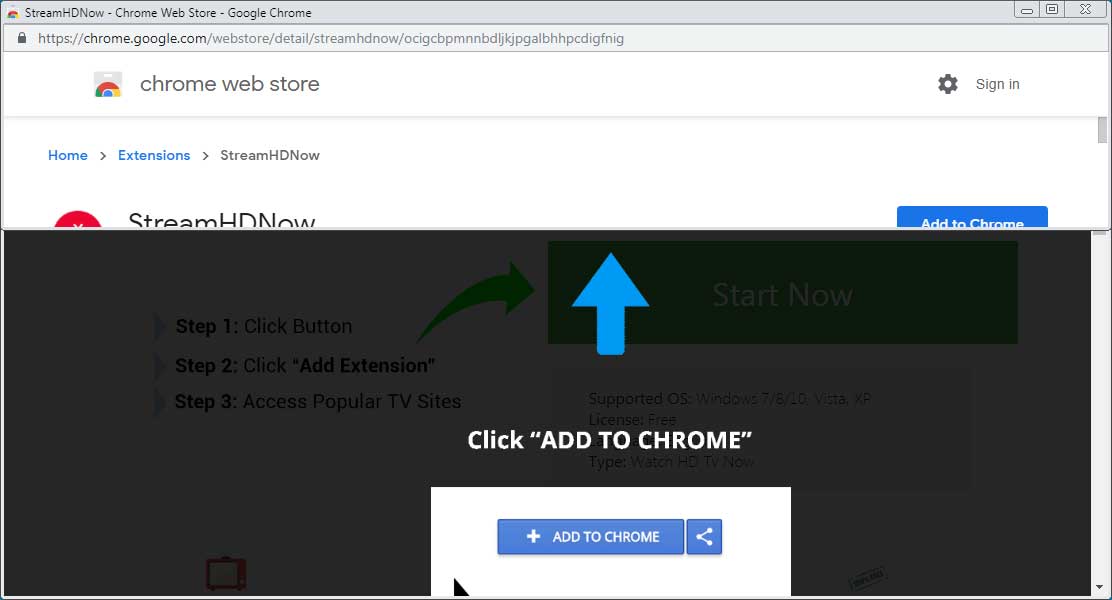
While it is possible to scroll the window to see information such as the extension's rating or installs, it is likely that some users will just activate the "add to Chrome" button to install the extension without paying attention to these things or the fact that a popup window was just spawned on their device.
The workaround offers an experience that is very similar to inline installs. While it is necessary to click on the "add to Chrome" button to display the installation prompt known from inline installs and Chrome installations from the Chrome Web Store, it is unlikely that this will stop most users exposed to the scheme from continuing with the installation.
Closing Words
While it may sound good on paper to recommend to Chrome users that they install extensions only directly from the Chrome Web Store, it is not something that is 100% safe either considering that these deceptive extensions are stored there as well.
Google has more control over extensions and options to prioritize some over others but it has happened in the past that malicious extensions landed in the Chrome Web Store.
We suggest that users verify Chrome extensions before they install them in the browser.



















Opera is nice in this case, because it doesn’t officially use .crx extensions. You can make it use them, but not by default so even if it’s a Blink browser, it’s not affected by this.
bypass-paywalls-chrome 1.3.4
https://github.com/iamadamdev/bypass-paywalls-chrome
Use Load Unpacked to install the extension.
I wish there was a browser setting to disallow websites from opening new windows altogether. The existing “popup blocker†setting just doesn’t get the job done properly (e.g., on torrent sites). For the few legitimate reasons for opening new windows, I would be more than willing to manually maintain an allow-list in my browser’s settings.
/* 2212: limit events that can cause a popup
* default is “change click dblclick mouseup pointerup notificationclick reset submit touchend”
* [1] http://kb.mozillazine.org/Dom.popup_allowed_events ***/
user_pref(“dom.popup_allowed_events”, “click dblclick”);
This what I use (and I also force new windows as new tabs) and for me this is all fine and dandy. This will stop a metric fuckton of popups (I basically never see any to be honest), but I do have other methods in place (uMatrix in super-uber hardened mode etc)
– http://www.kephyr.com/popupkillertest/index.html
– http://www.popuptest.com/
I should test myself on these again, but last time I checked I was good against all but a couple.
Of course, this will not stop the situation in the article (popup on click), but I was really just replying to you about your overall private popup hell/ dilemma. Of course you could try life with the pref set to blank
Holy cow, setting that flag to a blank string actually prevents all popups on torrent sites. This is exactly what I wanted.
Now, if I could only tell Firefox somehow to allow all popups on certain sites. But let’s first see how much I really need this. Maybe sites are more resilient to popup blockers than I thought.