Check the state of Spectre and Meltdown mitigations on Windows
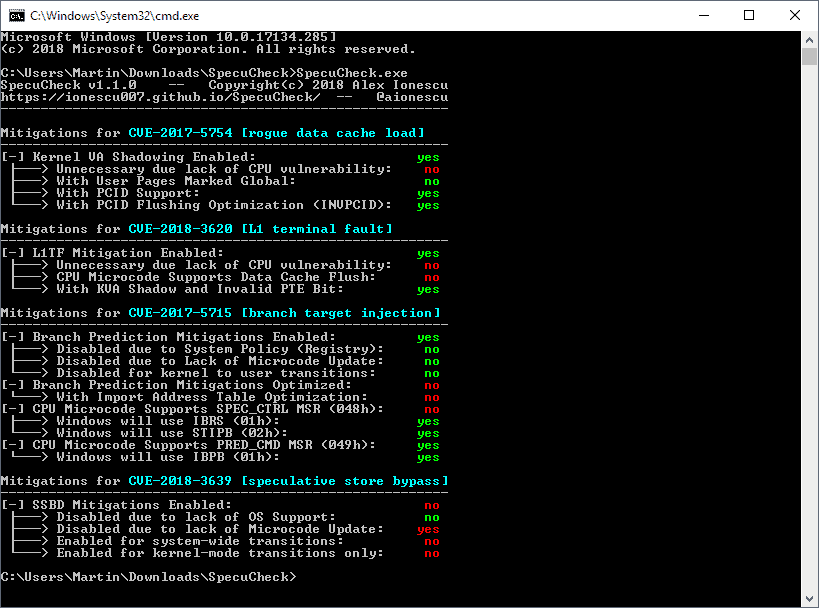
SpecuCheck is an open source program for Microsoft Windows devices that reveals the state of Spectre and Meltdown mitigations on the system it is run on.
In particular, it returns the state of software and hardware mitigations against CVE-2017-5754 (Meltdown), CVE-2017-5715 (Spectre v2), CVE-2018-3260 (Foreshadow), and CVE-2018-3639 (Spectre v4).
SpecuCheck

SpecuCheck is a command line tool that returns the state of mitigations against the listed vulnerabilities.
Some users may be turned away by the command line nature of the program; it is easy enough to use, however, and does not require elevated privileges.
Note: The developer suggests that users use Microsoft's PowerPoint CmdLet if they can to check the state of mitigations and SpecuCheck only for verification or research.
All you have to do is run specucheck.exe from the command line to get detailed mitigation information. The output is detailed; the most important information is whether mitigations are listed as enabled or not.
Users or admins who see "Your system either does not have the appropriate patch, or it may not support the information class required" should pay attention as it indicates that the system is vulnerable and not properly patched to mitigate the listed vulnerability.
How does it work?
[SpecuCheck] uses two new information classes that were added to the NtQuerySystemInformation API call as part of the recent patches introduced in January 2018 and reports the data as seen by the Windows Kernel.
The application provides no information or instructions to apply patches to protect the system against Spectre or Meltdown vulnerabilities. A good starting point is to search for the CVE on the Internet to find out how to download and install patches.
SpecuCheck is not the first tool to check whether a particular system is vulnerable and patched. Microsoft released a PowerShell tool to check if PCs are affected by Meltdown or Spectre, and there is also InSpectre by Gibson Research which does the same.
Closing Words
SpecuCheck is a useful tool to quickly check the state of Spectre and Meltdown mitigations on a system.
While it is suggested to use Microsoft's PowerShell tool to verify the findings, SpecuCheck does provide users and admins with a quick overview of the patched state of the system.



























I already know the state of Spectre mitigations on my laptop: I’m not getting an updated BIOS from Lenovo, ever, because my laptop is “too old” (an 8-year-old T-series that still works just fine, as T-series are — make that *were* — generally expected to do). I read a while back that recent Linux kernels inject the necessary microcode at boot-time, so there’s no need for a BIOS update if you run Linux (hooray!) … but that it only protects against Spectre v. 1, not Spectre v. 2 (boo!). So, InSpectre is just going to keep telling me that Meltdown is patched and Spectre isn’t … until I buy a new computer … which is *quite possibly* going to have a somewhat less vulnerable APU from AMD in it. I’ve read that AMD is once again giving Intel a run for its money in some performance-related areas anyway.
This whole thing with OEMs being stingy about issuing updated BIOSes for computers reasonably likely to still be in service — some OEMs don’t even go back a measly *three years* before the flaws were announced and patched — is beginning to feel a little like Apple’s stinginess with stuff like heat-damaged motherboards: a serendipitous (for them) forced (for us) obsolescence strategy.
I don’t understand the meltdown people seem to have about Meltdown and Spectre (and the new vulnerabilities). They have been around since at least when Windows 95 was released (confirmed). Still there is NO knowledge that the vulnerabilities ever have been used – or ever will be. Why so worried about this when f.ex Windows is filled with INTENTIONAL backdoors for NSA, CIA, FBI GCHQ and so on ? What about the other INTENTIONAL backdoors in the harddrives, SSD’s and so on ? Why not worry about them to, if You are worried about Meltdown and Spectre ? So hillarious…..
I have disabled them both on my gaming computer to cram some extra power out of it. Yes, these patches introduce bugs to f.ex in Windows 7 (32/64-bit and later Windows versions to). When disabled these bugs aren’t there.
I am sure of that Meltdown and Spectre both are INTENTIONAL. Too bad someone happened to find out, just as with the other, now known backdoors in most software and hardware….
how do you read the results that are returned to decide if patch is needed or not?
Check for “Your system either does not have the appropriate patch, or it may not support the information class required”. If you see it, you are missing patches.
I suggest you don’t try to get a green yes for each and every one of these. Instead monitor and benchmark your OS performance after the mitigations. You may realize it’s ok to run unpatched but the system runs much faster.
Microsoft’s own tool at https://gallery.technet.microsoft.com/scriptcenter/Speculation-Control-e36f0050 can’t do?
Hi Martin
I couldn’t see specucheck.exe on the landing page
just
.gitignore
README.md
SpecuCheck.png
SpecuCheck.vcxproj
_config.yml
specucheck.c
You need to click on “releases” on GitHub to display the download.
“Note: The developer suggests that users use Microsoft’s PowerPoint CmdLet if they can to check the state of mitigations and SpecuCheck only for verification or research.”
Should the word powerpoint in the paragraph above be PowerShell?
I think you’re right…i tried to use the Cmdlet and accidentally made a 10-slide presentation about pancakes :/
Hello, thanks for the Info.
I had problems to find the binary on the page you linked.
Because I have no C compiler at hand, I googled and found this Link:
https://github.com/ionescu007/SpecuCheck/releases
Thanks anyway for your Blog !
Thanks for proving one again that “Google is your friend”. I had to dust off 1984 DOS 2.1 skills, but I got expected results. A new PC a year or two from now should properly fix this problem and the ones not known yet.