Mozilla plans to push privacy in Firefox
In Changing Our Approach To Anti-Tracking, Mozilla revealed plans to improve the privacy protection of Firefox users and the performance of the browser through the improved implementation of content blocking in the web browser.
Firefox will protect users by blocking tracking by default and improve performance at the same time according to Mozilla.
We reviewed the new content blocking options that Mozilla tests in Firefox Nightly currently already in July. The new feature, called Content Blocking in Nightly, integrates Firefox's long standing feature Tracking Protection and other content blocking options, and makes these more accessible in the browser.
Mozilla launched Tracking Protection in 2014 in Firefox Nightly but enabled it for Private Browsing only in Firefox 42. Two years later, Firefox users could enable Tracking Protection for regular browsing sessions as well.
Competing browsers introduced ad-blocking and content blocking functions of their own. Brave browser with its block-all approach, Opera browser with its integrated ad-blocking feature, and even Google launched a content blocker in Chrome to block advertisement on sites that use certain ad formats the company deems undesirable.
Mozilla's privacy push in Firefox

Mozilla plans to test and implement several privacy-improving features in the Firefox browser in the coming months.
A new blog post on the official Mozilla blog highlights three key areas of importance.
- Page Load Performance improvements thanks to the blocking of slow-loading trackers.
- Blocking storage access and cookies from third-party tracking content.
- Blocking harmful practices such as crypto-currency mining or fingerprinting.
Starting in Firefox 63 and dependent on a Shield study that Mozilla plans to run in September, Firefox will block slow-loading trackers automatically for all users in all browsing modes. Any tracker with a loading time of 5 seconds or longer is classified as a slow loading tracker by Firefox. Mozilla has high hopes that the blocking of slow loading trackers will improve the performance for Firefox users.
In Firefox 65, Mozilla plans to strip cookies from third-party tracking content and block storage access provided that a Shield study in September will yield satisfactory results.
Last but not least, Firefox will block harmful scripts and practices by default . Mozilla did not reveal a target version for the implementation only that it will land in a future version of the web browser.
Firefox Nightly users can test the content blocking functionality right now already. Current versions of Nightly display content blocking options in the preferences and when users click on the information icon next to the site's address in the address bar.
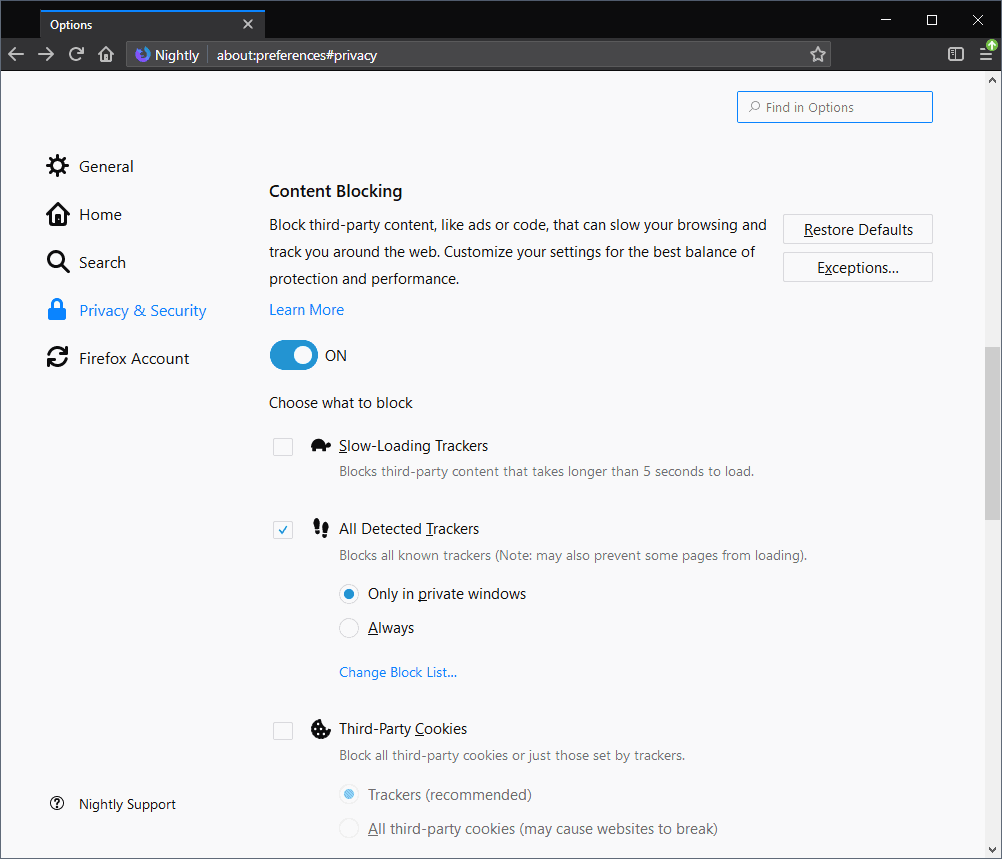
Current options allow users to block slow loading trackers, all detected trackers, and third-party cookie trackers or all third-party cookies.
The content blocking functionality supports exceptions to allow certain sites to run identified trackers, e.g. to avoid site breakage.
Is it enough?
Firefox will block some forms of tracking in the near future and that is definitely a good thing. Some may question why Mozilla makes a distinction between slow-loading trackers and all trackers in Firefox, and why Firefox does not block all trackers automatically by default.
One possible explanation for that is that blocking all trackers may prevent certain pages from loading correctly.
Still, with Google not being able to implement full-scale ad-blocking in Chrome, it is an area that Firefox could really outshine Google Chrome if implemented correctly.
The blocking of slow-loading trackers may be beneficial to privacy as well, but it is first and foremost an attempt to improve the performance of Firefox since any other tracker that is not slow-loading is still loaded by default.
Now You: What would you like to see in Firefox in this regard?






















Firefox is really becoming a bigger nightmare than it has ever been. This just seems like a hollow gesture to try to win back people they are currently losing. If Mozilla really wants to make Firefox private they should remove all telemetry and pocket. Then maybe they could also work on issues the browser is currently having with web pages not working. It seems like every single day another web page stops working with it, and it is not the settings or extensions doing it either. I will likely be uninstalling Firefox for good at some point this week just because it is horrible.
too little
too late
To block a ‘thing’, you must first identify a ‘thing’. To do so you must track every ‘thing’.
“To protect your privacy were are going to eliminate it” is all I hear.
I wish firefox would just go back to being a browser.
Your comment makes no sense. It is a browser and only that.
“Still, with Google not being able to implement full-scale ad-blocking in Chrome, it is an area that Firefox could really outshine Google Chrome if implemented correctly.â€
Google’s an ad company, they and facebook distribute half the ads online. They’ll never be evil to themselves.
@ULBoom, “Google’s an ad company, they and facebook distribute half the ads online. They’ll never be evil to themselves.”
Off-topic -start :
your comment gets me to wonder if the devil loves itself. That would be a fantastic paradox. And if it hates itself that would be an even greater paradox. Maybe neither in which case it’d be plain anarchy :=)
Off-topic -end.
I set Firefox to in general only allow cookies during the session. I then add a few exceptions to that manually.
One big drawback is that sites then for each sessions show various “do you accept cookies?” “do you accept our privacy rules?” type popups. UBlock origin filter out some of them, but not all.
I wish Mozilla added settings for automatic replies to a site’s privacy/cookie policy query. I’d then auto accept cookies and privacy agreements for all sites because I know I will delete them at the end of the session anyway.
You also have the SpywareBlaster solution which handles cookies as well (blacklist), runs on Internet Explorer, Google Chrome, Mozilla Firefox, Netscape, Seamonkey, Pale Moon, K-Meleon.
Free & paid, paid brings filters auto-update, free requires manual filters’ updates. I’ve been using it for years as an extra protection. Available at https://www.brightfort.com/spywareblaster.html
I also Similarly, it is recommended “the SpywareBlaster solution”.
The function of this application is secondarily effective for measures against “privacy policy violation” and “cross site scripting”!
Advantages over other Security applications:
· Since registering Cookies (when using the browser) in black list, spy / tracking by cookie can be blocked.
· System Resources (RAM, CPU) is a virtually “zero”!
· It is profitable and “unique function with high originality”.
· Although the presence is sparse like “air”, it becomes firmly “back shield”.
There is no negative element, so it is better to implement it.
With SpywareBlaster using browsers portable no possibility to add your own profile, useless to me.
There is no standard API so a browser doesn’t know when there is a privacy policy.
The privacy law is holding the browser makers hostage to accept third party cookies, otherwise users are bugged all the time with these annoying popups.
That means the only solution is either a very sophisticated blocking strategy, which only a minority is able to do, or a targeted cookie blocking solution like what Apple is implementing.
A working solution for Firefox does already exist in the name of Privacy Badger.
Better than nothing, better than present default privacy settings … for newcomers.
Far from ‘uBlock Origin’ capabilities for those who want a cat to hunt the Web’s mice.
I emphasize the article’s statement:
“Still, with Google not being able to implement full-scale ad-blocking in Chrome, it is an area that Firefox could really outshine Google Chrome if implemented correctly.”
That is indeed an area worth being ploughed.
The prompts will go away once the ePrivacy Regulation is in effect by next year.
This sounds like a positive development overall.
However, blocking all third party cookies will likely prevent people from commenting on articles from sites that use third-party commenting section service like Disqus. Since 9 out of 10 Internet users use browsers other than Firefox, it seems likely that few sites will drop Disqus and similar systems over it not working in Firefox, and many users will blame the browser.
Perhaps they should consider a “block select third party cookies” option and have the default install be set to that, which would whitelist third-party cookies necessary for functionality, and then have “opt-in” options available to block all third-party cookies, block no third party cookies, and to add to or subtract from the built in whitelist.
@John: “blocking all third party cookies will likely prevent people from commenting on articles from sites that use third-party commenting section service like Disqus”
Perhaps so (I don’t know). In my opinion, though, if a site is using Disqus (or any other commenting system not hosted by the site itself), that counts as “not allowing comments” anyway.
Disqus works but you have to login every time to post a comment and it doesn’t save your credentials.
@Anonymous
I didn’t mean to imply that Disqus didn’t work. If Disqus is the means by which a website allows comments, that counts as “doesn’t allow comments” to me because I actively don’t want yet another company involved in something that it doesn’t need to be involved with. Why should I let Disqus slurp my data?
They say third party trackers. Blocking all third party cookies makes my browsing somewhat unpredictable and wrecks some sites. I delete saved data on FF close and keep the setting to allow the browser to keep running after it’s closed turned off.
The best option is to erase all cookies at end of session by default.
This is true.
Makes you wonder why Mozilla is not doing it.
I mean it’s so simple it would basically take 5 minutes to implement and makes all kind of client side cross-session tracking technically impossible.
Well the most pervasive tracker on the internet is Google Analytics. My question to Mozilla would be whether they’ll treat it as what it is and block it, preferably by default for all Firefox users. I have my doubts, considering they use it on their own pages, and a while back some users objected to that for privacy reasons, and Mozilla brushed them off.
Mozilla doesn’t use Google Analytics on its sites if you have set Firefox to send “Do Not Track” signal to websites.
@ak,
“Mozilla doesn’t use Google Analytics on its sites if you have set Firefox to send “Do Not Track†signal to websites.”
I didn’t know that. I just checked https://addons.mozilla.org/ with ‘uBlock Origin’ :
“privacy.donottrackheader.enabled”, false : google-analytics.com appears in uBO
“privacy.donottrackheader.enabled”, true : google-analytics.com DOES NOT appears in uBO
privacy.donottrackheader.enabled is false by default
Well, at least one domain respects the DNT feature, not sure it’s not the only one …
tracking, tracking .. @mozilla, how about 1st party cryptocurrency mining (+ behind a proxy) resp. an automatic – throttle – function of “excessive javascript usage” in the browser? i don’t want an addon for it (except the mwb – addon beta, all other addons based only on blacklists have no effect and in some cases are themselves cryptocurrency miners). something must be done about this plague.
> @mozilla, how about 1st party cryptocurrency mining (+ behind a proxy) resp. an automatic – throttle – function of “excessive javascript usage†in the browser?
Why don’t you read their entire blogpost? They mention that they want to block JS cryptominers: https://blog.mozilla.org/futurereleases/2018/08/30/changing-our-approach-to-anti-tracking/
@mike
> And remove WebRTC completely to eliminate this ip leak
WebRTC is crucial for a lot of things, it shouldn’t be disabled by default.
@sam strange question. i know about their plans. also on ghacks a screenshot of mozilla was released, showing this option. but blacklists won’t help here. this is about 1st-party scripts / inline scripts (some behind a proxy). it takes much more than pure eyewash ala opera’s-coin-blocking-“blacklist”. mozilla have to take a deeper approach here. i suspect, however, that they will make it too easy for themselves.
I have never found a use for WebRTC
@Sam: “WebRTC is crucial for a lot of things, it shouldn’t be disabled by default.”
Well then, at the very least, it should be possible to disable it without having to resort to editing about:config settings. WebRTC is seriously problematic.
And remove WebRTC completely to eliminate this ip leak