Intel security update KB4346084 for Windows 10 released
Will it ever end? Microsoft released new Intel microcode updates for Windows 10 that install or update protections against various Spectre variants.
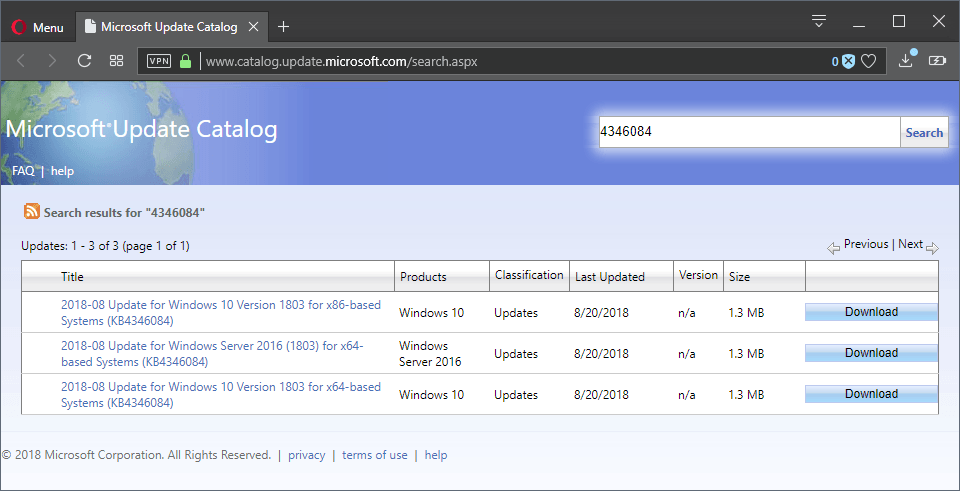
The updates are available for Windows 10 versions 1803, 1709, 1703, 1607 and 1507, and currently only available on the Microsoft Update Catalog website.
Günter Born notes that the update will also become available through Windows Update and WSUS, but this does not appear to be the case at this point in time.
The updates KB4346084, KB4346085, KB4346086, KB4346087, KB4346087 and KB4346088 update protections against attacks targeting vulnerabilities in Intel processors that affect most Intel processors.
If you don't know whether your Intel processor is affected try the free tool InSpectre for Windows to find out about it. You may also run commands from a PowerShell prompt to display vulnerability information.

The summary page highlights what the update does:
Intel recently announced that they have completed their validations and started to release microcode for recent CPU platforms that are related to Spectre Variant 3a (CVE-2018-3640: "Rogue System Register Read (RSRE)"), Spectre Variant 4 (CVE-2018-3639: "Speculative Store Bypass (SSB)"), L1TF (CVE-2018-3615, CVE-2018-3646: "L1 Terminal Fault"). In addition to microcode updates previously released in KB4100347​ to address Spectre Variant 2 (CVE 2017-5715: "Branch Target Injection"), this update also includes microcode updates from Intel for the following CPUs.
In other words, the new update adds protection against Spectre variants 3a and 4, and includes previous updates as well that Intel and Microsoft released earlier.
The updates are standalone updates for the version of Windows 10 they have been created for. The mitigations are active immediately on client systems; Server administrators need to make modifications to systems they administrate to apply the protections according to Microsoft.
Windows 10 version 1803 users who check Windows Update may get an updated version of KB4100347 at this point in time. It is unclear why this update is delivered since it has been replaced by the update mentioned below.
- Windows 10 version 1803: KB4346084 (Catalog link) -- the update replaces KB4100347
- Windows 10 version 1709: KB4346085 (Catalog link) -- the update replaces KB4090007
- Windows 10 version 1703: KB4346086 (Catalog link) -- the update replaces KB4091663
- Windows 10 version 1607: KB4346087 (Catalog link) -- the update replaces KB4091664
- Windows 10 version 1507: KB4346088 (Catalog link) -- the update replaces KB4091666
Closing Words
I wish Microsoft would make it easier for users and administrators to follow what is going on. Why is there no page on the Microsoft website that lists operating system versions and the patches available for them to deal with Spectre threats?



















I don’t think it is a good idea to run InSpectre to find out about one’s protection status in regards to these new flaws, namely 3a, 4, L1TF. GRC has not updated its little app (InSpectre) for a while now, so I don’t think it can give one a fair account of what one is up against.
Right, especially because Microsoft updated the SpeculationControl PowerShell script to include the latest checks.
In other words and in a nutshell, one is better off running the updated Speculation control PowerShell from Microsoft to have a sound evaluation of one’s protection against these new flaws. I wish I could have the link to the Microsoft’s page for this..
Maybe Martin can help or anyone else reading this article.
@ gnu
>This is great, But GNU/Linux etc are left out of the article.
Perens: Intel Publishes Microcode Security Patches, No Benchmarking Or Comparison Allowed
https://lwn.net/Articles/763284/
“Bruce Perens looks at the license agreement for Intel’s latest CPU microcode update and does not like what he sees. “So, lots of people are interested in the speed penalty incurred in the microcode fixes, and Intel has now attempted to gag anyone who would collect information for reporting about those penalties, through a restriction in their license. Bad move.””
https://perens.com/2018/08/22/new-intel-microcode-license-restriction-is-not-acceptable/
What’s the status of Spectre patches for AMD systems?
I wonder how many more of these performance sapping updates to Intel CPUs it will take before they perform like my overclocked FX6300. :)
When will it end? Well Intel says they are releasing the new processors by the end of the year, but the old processors will linger for decades to come. Cross your fingers that the new processors don’t have hidden security issues.
Be scared. Be very scared!
Intel will release new chips which do not have the current issues.
Many of us will rush out and buy them. Good move right?
Then a new flaw will be discovered.
@pHROZEN gHOST: “Many of us will rush out and buy them.”
Intel won’t be coming out with “fixed” chips in the near future, though. Personally, I’ve begun the process of replacing all of my machines that run on Intel chips with ones that don’t (and that don’t engage in speculate execution). This replacement process will probably take me a couple of years, but will be worth it in the end, and I don’t have to wait around for Intel. Plus it will be nice to stop relying on Intel — given how they’ve handled this fiasco, that can’t be a bad thing.
This is great, But GNU/Linux etc are left out of the article.
Martin, this is not complete as you missed L1TF:
In other words, the new update adds protection against Spectre variants 3a and 4, and includes previous updates as well that Intel and Microsoft released earlier.
To correct this fact and bring some light (as part of my work is securing our HW against these vulnerabilities), there were only 3 waves of CPU vulnerabilities that you have to fix on hardware CPU level (we skip IME portion of its own vulnerabilities).
1 – Spectre AKA Variant 2 (CVE 2017-5715), BIOSes released in December with fixes in February
2 – Variant 3a and Variant 4 (Intel-SA-00115), BIOSes released in July (our DELL stock has them)
3 – L1 Terminal Fault (Intel-SA-00161), BIOSes not yet available
First one requires OS hotfix as well to fully mitigate the vulnerability. As mentioned, OEM manufacturer released CPU microcode updates via BIOS firmware to address them.
Instead of waiting for your OEM to release BIOS update to fix it on HW level, Microsoft released above software patches that update microcode before booting into Windows. So BIOS update is not required.
It does have a catch.
– Is only for Windows 10
– Is only for 6th generation of HW (Skylake and above)
So for production machines out there you still need BIOS update to fix it on hardware level.
“Windows 10 versions 1803, 1709, 1703, 1607 and 1507″… five versions in three years. All of them plenty of cumulative problems and never ending freak and unexpected issues. And this september 1809, another one to the hall of fame of ridiculousness and hilarious Microsoft’s history. Please, someone to stop this madness and let common users to have an LTSB W10 free, please!
“Will it ever end?”
No, it won’t, at least until the compromised Intel chips are physically replaced. The thing is that no microcode changes can eliminate the underlying flaw. All that can be done is to prevent specific ways to leverage that flaw — but there are so many different specific ways that all Intel can do is play a constant game of wack-a-mole.
not in wsus yet will wait and see then test
Woody, of Ask Woody, says there is no need to install these updates as there are zero instances of the specific vulnerabilities being exploited.
Thanks for posting the past version of all these KB updates.
Interesting that 1511 isn’t there, but 1507 is. (Not that it should matter, most of us have updated anyway)
that’s because the v1511 release of Win10 Home/Pro ended October 2017 and the v1511 release of Win10 Education/Enterprise ended April 2018, Kofi. MS did not bother offering new microcode updates for 1511 at all.
The 5MHz Z80c processor in my 1982 Kaypro II is not vulnerable.
Chuckles …
I installed KB4346084, and rebooted the machine. They’re both listed.
Should I remove KB4346084, or leave it?
Meant to say, should I remove KB4100347 or leave it*
Good question: I’m not sure to be honest but would probably remove the replaced update as it is no longer needed or keep it if you don’t notice any issues.
No need to run any (free) tools. CPUs affected by the vulnerabilities are listed on this Intel site: https://www.intel.com/content/www/us/en/security-center/advisory/intel-sa-00161.html
These list only points to CPUs vulnerable to security advisory INTEL-SA-00161, i.e. L1 Terminal Fault. Also, it does not detect whether your OEM manufacturer has released new BIOS version updating it via CPU microcode, so OS patch is not required.
How about Windows 7 and 8.1 ? :/
They’re still eligible to security updates, and can handle CPU microcode updates too, since it has been done before (see KB3064209).
They will either release them at a later date or in the next month’s security update pack.
One hopes…
A different Martin, by the looks of it this patch has a significant performance impact. For something which is not that easily exploitable (and really if you end up in your system with such malware in the first place, it means you have bigger problems to concern about), I honestly don’t know if it’s worth it.