Chameleon for Firefox: user agent and data spoofer
Chameleon is a new open source extension for Mozilla Firefox that is a port of the Firefox add-on Random Agent Spoofer for the browser.
Random Agent Spoofer added options to Firefox to spoof the user-agent and other information that the browser leaks to websites and servers on connect. The add-on is not compatible with Firefox 57 or newer, and Chameleon brings most of the functionality to Firefox 57 or newer devices.
There are plenty of things that you can do to modify a browser's fingerprint; sites and companies may fingerprint browsers using data that the browser reveals automatically or when scripts are executed.
Note: Chameleon is not related to the Chrome extension Chameleon with is also an anti-fingerprinting extensions.
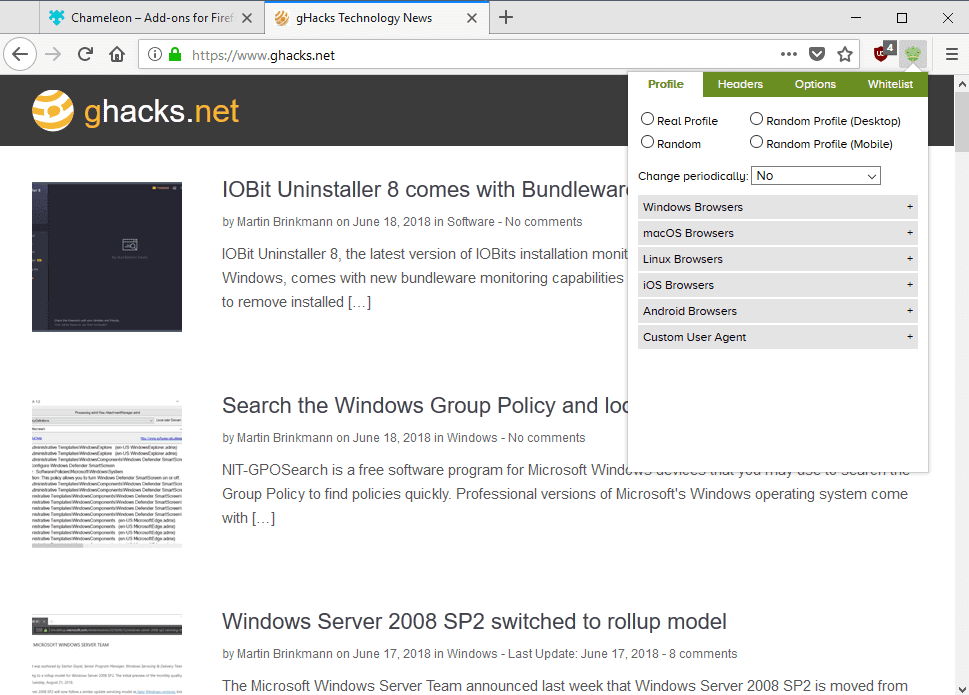
Chameleon for Firefox
Chameleon focuses on modifying the user agent of the browser. Firefox reveals the user agent to sites and servers when it connects to them. The user agent reveals the browser and version, operating system, accepted languages, referrer, and other information to sites.
The extension's core focus is the user agent but it provides options to change headers and configure other privacy related options next to that.
As far as the user agent is concerned, the following options are provided:
- Set a random user agent (mobile and/or desktop)
- Set a random desktop user agent.
- Set a random mobile user agent.
- Set a specific user agent. Supported are browsers for Windows, Mac OS X, Linux, Android, and iOS.
- Set a custom user agent.
You can make one-time changes to the user agent or configure the extension to change the user agent periodically. Available time intervals range from changing the user agent every minute to every hour; there is no option to change it less frequently, for example every six hours or once a day.
Chameleon comes with a big list of preset user agents. You can set the user agent to various Chrome, Firefox Microsoft Edge or Internet Explorer versions on Windows alone.
The user agents are necessarily up to date. The Firefox user agents are based on Firefox 59 even though Firefox 60 is already out. An option to set the user agent to the "real profile" is provided as well. The option can be useful if sites refuse to work with spoofed user agents.
Chameleon supports other browser header modifications and privacy options. When you switch to headers in the interface, you get the following options:
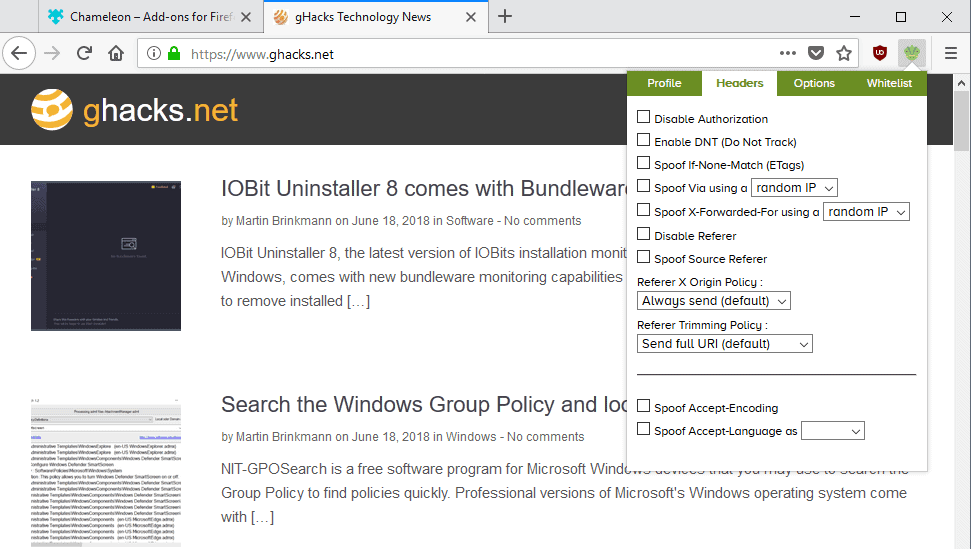
- Disable Authorization.
- Enable Do-Not-Track.
- Spoof if-none-match (ETAGs).
- Spoof via using a custom or random IP.
- Spoof X-forwarded-for using a custom or random IP.
- Disable Referer.
- Spoof Source Referer.
- Set Referer X Origin Policy.
- Set Referer Trimming Policy.
- Spoof Accept Encoding.
- Spoof Accept Language.
One issue that you may run into when configuring the headers options is that no explanation is provided. While it is easy enough to understand some options, Enable Do-Not-Track does exactly that, it is unclear what others like Disable Authorization or Spoof via do exactly.
A switch to the options tab displays another list of privacy related preferences that you may configure to your liking or needs.
To name just a few options:
- Disable WebSockets.
- Enable Script Injection.
- Protect window.name.
- Spoof the screen size.
- Enable tracking protection.
- Enable first-party isolation.
- Resist fingerprinting.
- Customize cookie behavior.
- Set several options in about:config using direct links, e.g. disable Pocket, Battery API, DRM, Device Sensors, or PDF.js, and several reporting options.
The browser extension supports a whitelist using a specific profile for use on sites. It is ideal for use on sites that don't work with spoofed profiles.
Comparison with Random Agent Spoofer
Chameleon supports most of the features that Random Agent Spoofer supports but there are differences. Random Agent Spoofer includes a larger set of user agents, e.g. Game Consoles or validators, and it supports more spoofing and privacy features such as spoofing accepted documents.
Most features, the core features, are supported on the other hand. Some suffer from WebExtension limitations such as the inability to modify about:config options directly.
Closing Words
Chameleon is an interesting option for Firefox 57 and newer users who used Random Agent Spoofer in the past or want to spoof the user agent and modify a large set of privacy related options in the browser.
Now You: Do you use privacy add-ons?


























This guy deletes posts that point out issues rather than address them. That’s shady!
Again, this product is Flawed; Windows uses UTC time and Chameleon uses GMT time. That raises red flags when creating google, twitter, etc accounts.
A guy who uses different names, posting the same thing over and over–that’s shady!
I don’t know what you’re on about, as UTC and GMT are THE SAME times. 17 hours UTC is the same as 17 hours GMT. 13:23 GMT is the SAME as 13:23 UTC. Etc, etc.
Anyway, you’ve posted here three times already about this–if this add-on, Chameleon, is not working for you, then do something USEFUL and contact the developer of the add-on! Or use another add-on. Random User-Agent works well. And privacy.resistFingerprinting, built-in to Firefox’s about:config, spoofs your time zone automatically if it is enabled.
One problem, which raises a red flag, is when an OS & browser use UTC time and Chameleon only spoofs in GMT time. Sites like DoILeak.com will flag this issue.
Chameleon has a great features set, but I do not like the fact that it essentially hijacks your browser and opens up the github page ‘https://github.com/sereneblue/chameleon/wiki’ every time it updates. This can be every day and more than once. You should be able to Opt out of that behavior.
I understand that changes may have been made which you may need to be aware of; but any program that takes control of your browser to load a webpage without user consent is treading a similar path to malware.
Seems to be an excellent add-on otherwise. Just my 5 cents.
A late comment in case you wish to spoof your MAC : for those, who run linux/ubuntu follow these commands:
sudu apt-get install macchanger
highlight Yes in the pop-up box
read more at mullvads site ( mullvad is an extremely privacy minded vpn company ) :
https://www.mullvad.net/en/guides/changing-your-mac-address/
This makes your browser just more unique and the more unique you are, the better they can track you. Just use different browsers with basic security like for instance one browser for banking, one for online payments, one for browsing. The most are also on a dyn. IP so I do not worry about these things. They have made it all so complicated and how more complicated they make, you need to do just the other way. Back to simplicity and you are ok. I ‘m here on the good but old Xp withthe old FF wit the ghacks tweaks and do crypto trading with a couple of 10K and no problems here at all but I have tweaked it with simple progs and the beauty is that I know Xp form the inside out and if there is something suspicious I will know it…
“They have made it all so complicated and how more complicated they make, you need to do just the other way. ” … that seems to me as wise as it can be, well said.
I’d just like to point out that tracking can be device-wide, the user followed from browsers to OSs to devices he may use. Even if I appreciate your state of mind, that of a return to simplicity in order to counter exponential complexity of the computing environment I’m not sure that it may be an absolute remedy against the deep increasing inquisition deployed which is amazing : fingerprinting is getting everywhere on the Web, everywhere, the tracking machines are getting more sophisticated day by day. I do hope the EU GDPR will bring its lot of fresh air.
Hi everyone.
I would be very glad if someone here can share his full set of tools for total fingerprint spoofing. The thing is that I’m mainly using Facebook business for my work, and they decided to flag an account previously. Since then, they keep recognizing me and banning my account. I will mainly use the tools for multi-accounting
I’ve had mixed results with add ons like this. In FF with Win 10, if the user agent is changed to a much older version, sites either break or act flaky. Spoofing a very different OS or browser such as iOS, chrome or safari, FF often just won’t work. Changing the user agent randomly while browsing breaks things too, sites suddenly hang.
Had the same results in Chromium with the added attraction of google’s sledgehammer captchas which never resolve and idiotic warnings including requests for my phone number!
Not sure why all these things happen but OS’s and browsers have changed a lot over the years. Today’s data grab software may be fundamentally different than older stuff, IDK.
Seems spoofing a recent version of FF or Chromium works OK but still hangs occasionally.
I think it makes a lot of sense to select a functioning combination of privacy apps. Many have redundant protections; redundant with the browser, other add ons and extensions, AV, etc., and can easily grind things to a halt. The EFF site can show you how buried your browser is in the noise in terms of process of elimination, part of the story.
For FF, we use Adguard, a bazillion about: config changes along with a VPN. I save profiles since config settings change slightly as versions progress and the lists out there typically don’t keep up well.
I use Tor Browser with the proxy set to my VPN provider’s proxy server. Fast and no problem with fingerprints or user agents. I have an additional Tor Browser instance with the proxy set to use Tor – I use for email (more secure but slower).
I use the Thor browser without connecting through the network and it seems to provide good anonymity according to tests sites such as whoer.net.
The one issue is that my local time gets transmitted as well as the VPN server’s which can raise red flags. I haven’t been able to find an extension which spoofs time headers reliably.
I often spoof my user agent, but not really for privacy reasons. When I do it, it’s to bypass a website that either refuses to work with my browser, or to avoid having the site change its contents based on the browser I happen to be using.
wont work with cyberfox. Bummer :(. Buttons dont work.
But maybe its possible to replace data.js with the new one in the old Random Agent Spoofer
> Name: “wont work with cyberfox.”
Chameleon is a WebExtension addon meant for Firefox v57+ & similarly updated forks.
The latest version of Cyberfox is forked from Firefox v52.x ESR, which uses XUL addons. As such, XUL addons like Random Agent Spoofer will work in Cyberfox, & probably Basilisk (whose more recent versions are also forked from Firefox v52.x ESR).
However, Random Agent Spoofer doesn’t work in PaleMoon (even though this supports many XUL addons developed for Firefox), because RAS requires the Australis GUI as backbone, while PaleMoon is pre-Australis.
@Name said: “wont work with cyberfox. Bummer :(.”
Yes, Chameleon seems to be a different kind of add-on, a web extension add-on, for the newest versions of Firefox Quantum. But instead for Cyberfox you can just use the original add-on from which Chameleon is derived: Random Agent Spoofer!
https://www.ghacks.net/2014/02/14/random-agent-spoofer-randomizes-identifiable-information-firefox/
about:config : privacy.resistFingerprinting . rest: https://ffprofile.com/#start
For Chrome users i highly recommend ‘Noiszy’
https://noiszy.com/
https://chrome.google.com/webstore/detail/noiszy/immakaidhkcddagdjmedphlnamlcdcbg
Obfuscation and blending within the crowd of billions online users is the right approach for online privacy
Not “stick out like a sore thumb” practices like this one with user agents/data spoofers tools
>blending within the crowd of billions online users
Unless that crowd of milliards of online users has the same IP, you are all unique, regardless of whether your browser has the same fingerprint or it’s different from each other.
Unique is not the same as being identified. We all know every single ip address that can exist, that does not mean we can say anything meaningful about most of them. Part of fighting fingerprinting is making it less useful to sell the combination of ip and fingerprinted ID information between networks.
Ad networks and ID merchants like fb use the combination to further combine ones actual id to web activities happening beyond their own network. Randomizing this information reduces the certainty that those networks rely on to sell their data to each other.
Yeah… if we think about it anti-fingerprinting is truly meaningful for users who use a VPN : would be a pity to be recognized by fingerprinting when true IP is hidden. But for users with direct connection, therefore identified by their IP, fingerprinting not only is less meaningful but can also be the opportunity for a big site administrator’s laugh when he finds the same IP associated to the plethora of anti-fingerprinting settings, moreover dynamic (“Hey, this IP was here 10 seconds ago with a different userAgent” : lol).
Well, you can set the user agent to a more common one to blend in better (e.g. Chrome).
Martin, Thanks for the article what appears to be a great web extension.
Martin (Or anybody else), After reading this article I am left wondering what the do with certain WebExtensions I have already installed, being:
The WebExtensions already installed where I am wondering about are:
1.) Privacy Badger (Because it sends also a Do Not Track signal when I am browsing. and Privacy Badger starts blocking once it sees the same tracker on three different websites.)
2.) Canvas Defender: who is adding a unique and persistent noise that hides main real canvas fingerprint. This add-on protects you while browsing both in normal and private mode. With Canvas Defender you are in control to drop your spoofed identity anytime.
3.) Decentraleyes, what prevents a lot of websites from making me silver bullets requests sending. Ultimately, I can make Decentraleyes block requests for any missing CDN resources, too.
Also, I really would like to hear your thoughts (Martin or anybody else) about what is the best configuration setting for this WebExtension?
As far as I know, this is how it works although it would be nice if someone could confirm this as I’m growing more and more curious regarding privacy matters every day.
1. Privacy Badger blocks trackers, or connection attempts from your browser to a particular domain that is not the website you are on. The main feature is that is not an ad-blocker, it learns as you browse, but it basically accomplishes the same result, since most ads nowadays are tracking you. This is useful also because you can use it along with other blockers such as UBlock Origin.
2. Canvas Defender spoofs your real canvas fingerprint with a unique hash (code or ID), which you can change at anytime if you’d like. The most important thing about how the fingerprint technology works is that the unique ID assigned to you cannot be reverse-engineered to find out your real canvas specifications. This is why is so useful that you can change it anytime, because if you ever “feel you are being watched” all you have to do is change the code. However this is just one of many factors used to track you online, and this does not provide you any cover for your user agent (I think??)
3. A lot of websites today need specific resources to work properly, but because it’s cheaper they are loaded from Content Delivery Networks. This is actually faster for the user, but there’s a privacy concern attached to requesting this information from a 3rd party constantly. Decentraleyes checks whether the resource is available locally and if so blocks the connection to the 3rd party, increasing loading speeds, saving bandwidth and increasing privacy.
I use all these extensions and I’d recommend to keep them unless you are having trouble loading some websites. Note that all three allow you to add a whitelist, in case you need to disable them for a specific site.
@thebrowser, as far as I know uBO makes ‘Privacy Badger’ obsolete. There’s an extension which brings ‘Privacy Badger’ to a higher level called ‘Privacy Possum’ which does bring an extra to uBO, but ‘Privacy Badger’ is uesless IMO with uBO.
‘Canvas Defender’ or ‘CanvasBlocker’ (I prefer the later, use neither at this time) do handle canvas fingerprinting which is totally out of the scope of uBO.
‘Decentraeyes’ as well handles CDNs by keeping a copy of most used scripts locally, not at all uBO’s job, so no redundancy as well.
I’m learning every day so this is really only how I understand these extensions and a few others at this time.
@Tom Hawack – The reason i like to use Privacy Badger as well is because i remember reading somewhere Raymond Hill saying the reason why he doesn’t accept donations is because if he ever wanted to stop development on uBlock Origin and uMatrix to do something else or for whatever reason, that he didn’t want to feel guilty like he owes people to continue development on them.
Well what if he stopped development on them? What if something happened to Raymond? if he passed or something? Does he have a plan for that scenario with the right people to execute that plan ?
Well i like the way Privacy Badger works. it is simple and it allows me to maintain a list-(as long as i don’t lose that data), a list of blocked domains, CDN’s and trackers. So if something happens to Raymond Hill or he quits development and uBlock Origin and uMatrix stops functioning properly say in future browser version or whatever, i have another blocking extension in Privacy Badger with a list already made that i can immediately fall back on.
Yeah people can fork uBlock Origin and uMatrix but can we trust the people that fork them? Can we have confidence in their vision for future development of them? i’m sure we can trust some of those those people but you never know, but what i do know is that i trust Raymond Hill and the development he has done so far on them and i have confidence in his future vision of them. We can’t say that for sure about others.
i trust EFF as well but what i’m saying is that it’s another tool with a list that i can fall back on, plus it can be used to block things in a way that i can in uMatrix, not as detailed as uMatrix but definitely more than uBlock Origin using Advanced Mode in Medium Blocking or Hard Blocking.
Just giving my 3 cents on it.
Also, Thumbs Up to Privacy Possum as well. i use all 4.
Happy Private Browsing to all.
I don’t think uBO makes Privacy Badger completely obsolete, since it does automatically recognize trackers as you browse the web, which makes it ideal for less tech-savvy users because you don’t have to do anything at all. On the other hand I have to agree that I rarely see the benefit of Privacy Badger since I use uBO pretty heavily, so I guess this is a good time for make the switch and try Privacy Possum out.
Hi Paulus,
ideally, you would use extensions that replicate the functionality of multiple WebExtensions that you run. I’m not sure if such a WebExtension exists though.
All three of the mentioned extensions serve a specific purpose. I’d say that Privacy Badger has the biggest effect as it blocks some third-party connections and tracking scripts and elements. If you do use a content blocker as well, you may not need to run Privacy Badger next to that especially if the content blocker supports lists or blocks all third-party connections outright.
The other two extensions serve very specific purposes. I’d keep them if you don’t notice issues, e.g. high RAM usage caused by them or lots of incompatibilities.
Concerning Web privacy I’ll have to admit that I focus more on pages free of ads and targeted ads than on data collection of my visited sites, even if I do try to hide (prevent or remove) my sessions as best as I can. It’s like having servants who know a lot about you but just won’t ever be able to make it public.
Many new privacy tools make their way, especially with browsers, particularly with Firefox. And among those redundancy may be problematic. As always the right balance is equidistant from too little and too much.
Firefox privacy/security extensions here & now are:
uBlock Origin, HTTPS Everywhere, Decentraleyes, Privacy Possum, ClearURLs, Skip Redirect, Forget Me Not. That’s about it. Combined with system-wide tools I enjoy ad-free Web pages and wonder meanwhile what data concerning myself may possibly be aggregated, don’t care too much as long as my computer blocks that data from serving pollution.
Hi all,
Actually i’m using the next extensions, and i want to know which ones do you think i should discard and which should i add if i’m not using them already.
– uBlock
– uMatrix
– Decentraleyes
– CanvasBlocker
– Cookie AutoDelete
– HTTPS Everywhere
– Privacy Badger
– Universal Bypass
– Firefox Multi-Account Containers + Temporary Containers
I’m using ghacks-user.js too, so, i think i can probably prescind of Firefox Multi-Account Containers + Temporary Containers, having Firefox isolation activated.
Chameleon looks nice, but i don’t know i really need it.
I would appreciate some opinions here. Thanks in advance.
Ainatar, long time no see. Unless you’re using a different moniker, come join us at github – missed your input.
As for MAC+TC (with or without FPI) – there’s a compelling argument to use this depending on your “threat model” in that in a hardened TC config you can eliminate in-session first party tracking (i.e every visit to site A is in a new temp container, so previous visits are isolated). I haven’t set this up yet, but I plan to do so. In this scenario I don’t think C-AD is needed (because TC clears using a different API call, and can clear more local storage items, eg IDB) – note: haven’t used MAC + TC yet, so I am assuming *every* tab/domain is in a container (C-AD does not work in containers AFAIK).
Chameleon is full of holes – leaks OS, platform and more (guess its still in development) – anyway, AFAIC random spoofing (raising entropy) is sh*t vs RFP/TBB’s spoofing/limiting (lowering entropy), so these sorts of extensions always get a big thumbs down from me. I wouldn’t touch it with Martin’s barge pole (yup, he has barge).
Thanks for your input, I appreciate your point of view. I think i will continue using my current configuration, at least for now.
I’m a faithful follower of your project in github, you are doing too well (compared to my amateur level, I don’t have anything good to contribute i’m afraid). Keep up the great work!
@Tom
Is Skip Redirect useful beyond ClearURLs? I use this last toghether with Redirector (personal rules) and I’m very satisfied.
You’ve right about redundancy; RAS has many items in Standard Option and I’ve to set it as the same of Privacy Settings, then I use this last to skip between Full Privacy and Privacy compatible choices. The only little thing I don’t like is that user agent options are not updated to to those in common use.
HTTPS Everywhere “Privacy” Policy: https://www.eff.org/code/privacy/policy
This policy describes our privacy practices for the information that’s collected and used by EFF software and technology projects, like HTTPS Everywhere (…) EFF is located within the United States, and therefore will transfer, process, and store your information in the United States, which may not provide as much protection as your home country. (We’re working to make US practices better.)
“US Practices better”… good luck with that!
Sometimes our software and technology projects may collect other types of information to help with technology research, which generally will not include personally identifiable information.
“Generally” I avoid that kind of software when I have a problem with its privacy rules.
EFF is Silicon Valley astroturf: https://thebaffler.com/salvos/all-effd-up-levine
Is HTTPS Everywhere necessary anymore, now with browsers blocking websites without the Certificate?
You have to actively choose to enter into a plain HTTP site nowadays.
@Shiva, if you have a link which is meant to open example.com and is written as,
before.com/?goes-to=example.com?source=thisIstheSiteIvisitedBefore
‘Skip Redirect’ will remove : before.com/?goes-to=
‘ClearURLs’ will remove : ?source=thisIstheSiteIvisitedBefore
Hence, with both, you’ll get directly to example.com and you’ll get there without trailing data.
This is a very basic example.
@Tom
Ok, thanks. So some rules are still not yet implemented in ClearUrls o the add-ons are fundamentally different?
@Shiva, the extensions are fundamentally different. ‘Skip Redirect’ as its name says it, concerns redirects; ‘ClearURLs’ is not concerned by redirects but by the data added to an url.
There’s one FF extension which is aimed at doing both, ‘Clean Links’ : IMO it does as well as ‘Skip Redirect’ for the anti-redirect function, but using its url cleaning function (that of ‘ClearURLs’ it requires regexp knowledge which is OK if you know how to set regexp : if you do then it’s great ecause the user can add his own filters (‘ClearURLs’ comes with a non-editable filters’ list but that list is very substantial). Because regexp is for me a nightmare I use both ‘Skip Redirect’ and ‘ClearURLs’ rather than the only ‘Clean Links’ …
@Tom
Oh, I see now that ‘Clean Links’ came back. I used it with PureUrls before switch to ClearUrls. Thanks for the tip, I will try ‘Skip Redirect’.
Well, thanks Martin for the notice of Chamaleon. A small step towards Firefox Quantum, I’ll just have to wait for another 20-30 add-ons, sidebar and statusbar… :-)
One thing to be careful of is when you go to download software to make sure you get the right download for your OS. You don’t want Mac on Windows or a Windows download on Ubuntu
Good point if you spoof the OS.
Major Problem — OS that only uses UTC time raises flags when the Time spoof of Chameleon only allows GMT time !