Enterprise Policy Generator add-on for Firefox
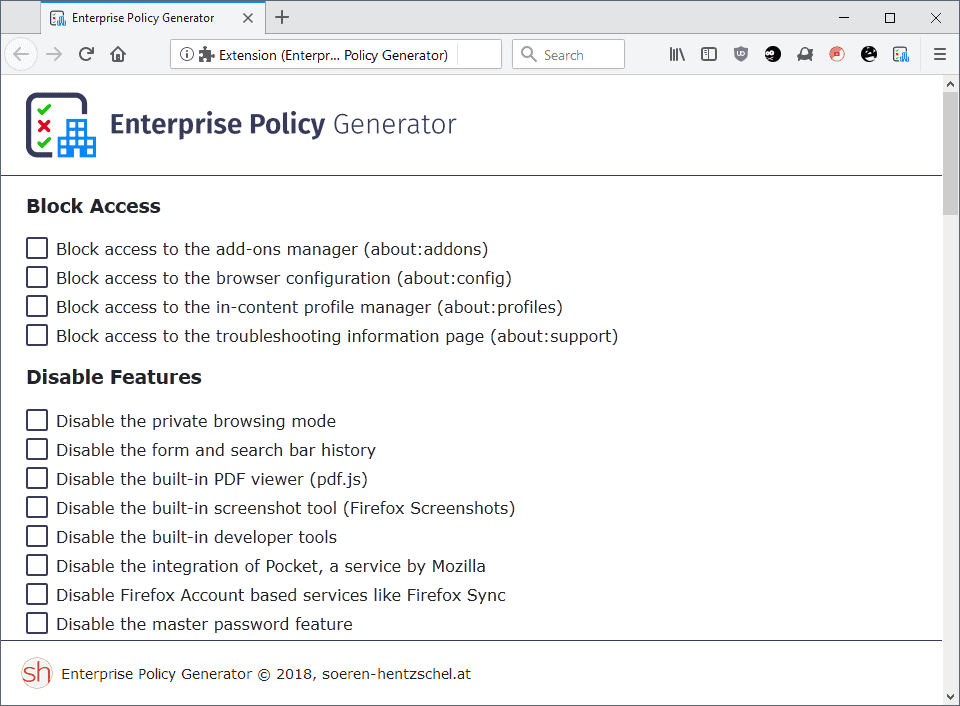
Enterprise Policy Generator is a new add-on for the Firefox web browser by Sören Hentzschel to create cross-platform policy files for Firefox. Designed for use in Enterprise and business environments, policy generator can be installed and used by any Firefox user or system administrator.
Mozilla launched the Enterprise Policy Engine in Firefox 60 and Firefox 60 ESR. While that included Firefox Group Policy Support for supported versions of Windows, it also meant that administrators and users could create configuration files for deployment.
The core advantage of the Enterprise Policy Engine is that it is cross-platform whereas the Group Policy option is only available for Windows devices.
Update: Sören released version 2.0 of the extension recently. It adds options to save, load, and delete configurations.
Enterprise Policy Generator

Enterprise Policy Generator is not the official successor of CCK2 Wizard, a Firefox add-on that organizations used in the past for deployment of Firefox. CCK2 Wizard is not compatible with Firefox 57 or newer. While not the official successor, it is fair to say that it shares the core feature set with the popular but now incompatible extension.
Enterprise Policy Generator supports all policies that Mozilla added to Firefox 60. Sören plans to update the extension when new policies get released and add version information to each policy as well so that it is clear which Firefox version individual policies require.
Usage is simple: You may use the shortcut Shift-F10 to open the policy generation page or click on the extension's icon in the Firefox toolbar to do so.
The extension lists all policies sorted into groups for easier recognition and reveals whether a policy is available for regular versions of Firefox and Firefox ESR, or only extended support releases of the web browser.
Just check the box in front of a policy to include it in the configuration file or leave a box unchecked to keep the default Firefox status of the feature or setting.
Some policies require additional data while others are simple enable/disable preferences. If you select "install, uninstall or lock extensions", for example, you are asked to specify add-in installation paths, extensions IDs for the removal or locking of add-ons.
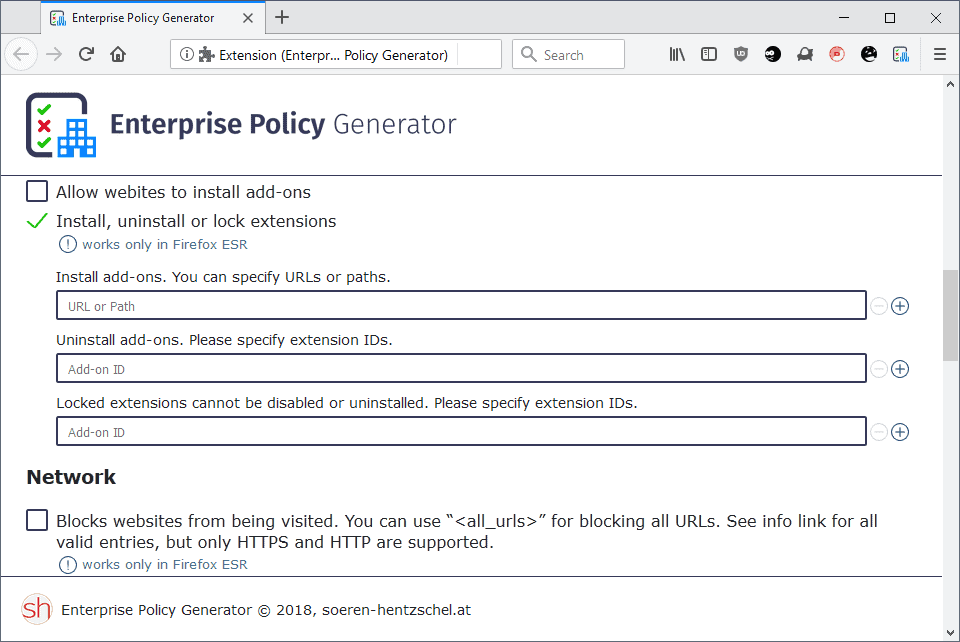
Some fields require text input while others come as menus that you select options from.
If there is one thing to criticize here, it is that there is no indication whether a policy requires additional input or not before you select it. Granted, it is not a big deal and it is clear for the majority whether additional input is required or not.
Here is what you can use the extension for right now:
- Block access to the add-ons manager (about:addons)
- Block access to the browser configuration (about:config)
- Block access to the in-content profile manager (about:profiles)
- Block access to the troubleshooting information page (about:support)
- Disable the private browsing mode
- Disable the form and search bar history
- Disable the built-in PDF viewer (pdf.js)
- Disable the built-in screenshot tool (Firefox Screenshots)
- Disable the built-in developer tools
- Disable the integration of Pocket, a service by Mozilla
- Disable Firefox Account based services like Firefox Sync
- Disable the master password feature
- Disable the feature to set an image as desktop background
- Disable the “Forget†toolbar button which can be used to forget the last browsing history
- Disable the “Import data from another browser†menu item in the library
- Disable the “Refresh Firefox†button in about:support
- Disable the ability to restart Firefox with add-ons disabled (safe mode)
- Disable the menu items “Submit Feedback†and “Report Deceptive Site†in the help menu
- Show the menu bar by default
- Show the bookmarks toolbar by default
- Set the homepage (works only in Firefox ESR)
- Whether the search bar is unified or separate (works only in Firefox ESR)
- Modifies the list of search engines built into Firefox (works only in Firefox ESR)
- Don't create the default bookmarks bundled with Firefox, including the smart bookmarks (most visited, recent tags). Note: this policy is only effective if used before the first run of the profile
- Create default bookmarks
- Allow websites to install add-ons
- Install, uninstall or lock extensions
- Blocks websites from being visited. You can use “<all_urls>†for blocking all URLs. See info link for all valid entries, but only HTTPS and HTTP are supported. (works only in Firefox ESR)
- Configure proxy access to the internet
- Sites that support integrated authentication (works only in Firefox ESR)
- Allow or deny websites to set cookies
- Clear all browser data on shutdown
- Enable or disable tracking protection
- Allow or deny Flash plugin usage
- Prevent certain security warnings from being bypassed
- Read certificates from the Windows certificate store (Windows only)
- Prevent Firefox from updating (works only in Firefox ESR)
- Prevent Firefox from installing and updating system add-ons (works only in Firefox ESR)
Prevent Firefox from sending technical and interaction data to Mozilla (telemetry) (works only in Firefox ESR) - Prevent Firefox from installing and running studies (SHIELD studies)
- Allow or deny pop-up usage
- Allow or forbid Firefox to offer to remember saved logins and passwords
- Don't check if Firefox is the default browser at startup
- Override the first run page. Set this policy to blank if you want to disable the first run page. (works only in Firefox ESR)
- Override the post-update “What's New†page. Set this policy to blank if you want to disable the post-update page. (works only in Firefox ESR)
The descriptions are sufficient to understand what individual policies do. Some policies include "more information" links which lead to Mozilla's Developer Network site.
Instructions for deployment
Click on the generate policies button once you have selected the policies from the available list. The extension displays the JSON structure of the policy file; you may copy the data and create the policies.json file by yourself or click on "download policies.json to download the file instead to the local system.
It is necessary to create a folder called distribution in the Firefox program folder (not profile folder) on the system and place the policies.json file instead.
The selected policies are applied automatically on start of the Firefox browser. Since the policies file is placed in the program folder, it applies automatically to all Firefox profiles.
Closing Words
Administrators can create policy files manually but Enterprise Policy Generator makes the whole process more comfortable and easier.
One downside of the current version is that policy configurations are not saved which means that you can't update existing configurations but need to start anew each time you need to update the policies file.
Sören plans to add save and load options to the extension at a later point in time which takes care of that then.
You may add individual policies manually to existing files in the meantime.
Enterprise Policy Generator is a useful extension for Firefox. While it may appeal to administrators the most, Firefox home users may use it as well to configure the browser regardless of whether they do so on a single system or home network.


























In v4.1.0 it states that : “removed the policy to disable the safe mode because it’s not supported via policies.json, only via GPO”
However, it still works with policies.json and I still see this policy in https://github.com/mozilla/policy-templates.
The policy only disables the menu item but it’s still possible to launch Firefox in safe mode. However, the policy will be re-added in Enterprise Policy Generator 5.0 and I will make clear that the policy will only disable the menu item.
How do you set this up on an android device?
There is no Android support.
Hello,
is there a way to use relative paths for installing extensions?
Regards
Earl
@Jamy: Some policies *WERE* “ESR only” when Firefox 60.0 and Firefox ESR 60.0 were released. All “ESR only” policies but the SearchEngines policy are *NO LONGER* ESR only since Firefox 62 and Firefox ESR 60.2.
Of course your DXR links show that the SearchEngines policy is the only “ESR only” policy because you didn’t used permalinks for a outdated revision but the current version. The current version of Firefox ESR is Firefox ESR 60.4.
Of course all descriptions in the Enterprise Policy Generator refer to the current versions of Firefox. And of course Martin wrote “ESR only” for a few policies more because when Martin wrote the article Firefox 60.0 and Firefox ESR 60.2 were the current versions and the version of Policy Enterprise Generator wrote “ESR only” for these policies at that time. The content of this article refers to May 2018, not January 2019.
Thanks for clarifying! Zero doubt can be left now. I wonder why the SearchEngines policy is not supported on Release if all other policies are, some of which seem more critical. But I can live without figuring it out :)
Cheers
That’s because of the fact that search engine hijacking was always a serious problem for Firefox users, so it’s kind of a protection for the users that search engines can’t be changed “from the outside”. But in general Mozilla doesn’t want to restrict policies, so the SearchEngines policy is an exception.
Ok, thanks :)
Which reminds me of one question. I don’t have group policy for Firefox when I look into gpedit.msc. There is no “Mozilla” entry where there should be. I’m on Windows 7 Ultimate and Firefox 64. Could it be because I declined to install the “maintenance service” ? Because I installed in D: with the OS installed in C: ? Or is that a bug I should report ?
It never worked, from 60 to 64, no group policy for Firefox. I use a JSON file so it’s okay, but if it’s a bug I’ll consider taking some time to report.
It does seem like DisableAppUpdate also works on the Release channel, not just ESR. While I can’t really verify it by testing, the source code doesn’t seem to show much of a difference regarding this policy between Release and ESR 60 ?
ESR 60: https://dxr.mozilla.org/mozilla-esr60/search?q=DisableAppUpdate&redirect=false
Release 64: https://dxr.mozilla.org/mozilla-release/search?q=DisableAppUpdate&redirect=false
So what do you think ? Where did that ESR-only info originate from ? Thanks
@Martin:
Are you sure this only works in ESR ? I tried the following in Firefox 62.0.3 Release (yeah, outdated, but not ESR) and it did block websites.
{
“policies”: {
“WebsiteFilter”: {
“Block”: [“”]
}
}
}
I tried this in order to check that all the “only works on ESR” options really didn’t work. It’s annoying to check if DisableAppUpdate is working, so I went for an obvious option like WebsiteFilter. Since it works, I’m questioning other items too.
Do you remember what your source was ?
Since Firefox 63+ suppresses the app.update.enabled about:config options, I’d like to make sure DisableAppUpdate replaces it properly.
Thanks!
Sorry for the centuple post. I confirmed that SearchEngines policy does not work on the Release channel.
I also confirmed that SearchBar, Homepage and WebsiteFilter, DisableTelemetry, the only four policies that I can test without a hassle and that this article marks as “ESR-only”, actually work on Release. I’m going to extrapolate these results to all other policies listed as ESR-only in the article except SearchEngines, including auto-updates and system add-on updates.
Also, I’m pretty sure even SearchEngines policy works on Beta and Nightly, not just ESR. But it does fail on Release and it’s most likely the only policy that does, according to this digging into the source code + partial testing.
A bit more research suggests that there are policies that will not work on the Release channel. Those should be marked with “enterprise_only”: true in the source code.
But the only policy marked as “enterprise_only” is SearchEngines, for instance DisableAppUpdate isn’t.
Is there anything you know that contradicts this and turn DisableAppUpdate into an enterprise_only feature not available on the Release channel ?
Your site security has sanitized the important part of my JSON, here’s the corrected version
Hi All,
Could i please get some help with the deployment of firefox 64.0.
– Created the .json file using the Enterprise Policy Generator
– Installed Firefox onto the test machine, created the distribution folder under c:\program files\Mozilla Firefox and copied the json file in distribution folder
– Launched Firefox, all the things I configured didn’t work
– Added certificate
– Setup Homepage
– Proxy setting changed to Automatic configuration URL
Thanks for your help in advance
Regards,
Hi, I could not find any documentation about this. Everybody writes about putting the policies.json file into the distrubtion directory in the program folder…
This seems to be wrong imho.
– Delete or move the old profiles and configuration of Firefox in “%appdata%\Mozilla”.
– Unpack the Firefox-setup.exe with 7Zip or any other unpacker: Here we call it “Firefox-setup\”
– Put the directory “distribution” and the policies.json file within into “Firefox-setup\core\”
– Start the Setup with “”Firefox-setup\setup.exe”
I would appreciate any other comment on this. This was the only way I could apply the policies.json.
Greetings
Earl
> This seems to be wrong imho.
You need to put the file policies.json into the distribution directory inside the installation directory of Firefox. That’s what you can read anywhere and that’s the correct way for sure.
I don’t use Windows and I don’t know why you modify the installer. But I guess Firefox-setup\core\ contains the content of the later Firefox installation directory. If it works for you just check the installation directory after the setup.
Hi,
enter about:policies into the address bar and press enter. If your policies.json file contains errors there will be an error tab where you can see the errors.
FYI: I implemented a lot of new features and improvements in the past three months:
– you can save different configurations, load them at a later time and of course delete them (since Version 2.0)
– configurations can also be exported and re-imported on other devices (since Version 3.0)
– a filter field has been added. Both the descriptions of the policies and the internal policy names can be searched (since Version 4.0)
– if a policy requires a newer version than Firefox 60.0 or Firefox ESR 60.0 a notice is displayed (since Version 2.0)
– added a basic validation for fields where a valid URL is required (since Version 3.0)
– small design and other improvements
– and of course a lot of policy updates to support all new policies and policy options implemented by Mozilla
– the downloads permission is no longer mandatory (since Version 1.1)
– added French and Chinese translations
If some of you are still missing things please let me know! :)
Hi Martin,
thanks for writing about my add-on! :)
> If there is one thing to criticize here, it is that there is no indication whether a policy requires additional input or not before you select it. Granted, it is not a big deal and it is clear for the majority whether additional input is required or not.
That was an explicit design decision. Let me explain why I chose this UX.
In the first pre-release versions of the extension, all suboptions of all policies were visible before you selected a policy. The suboptions looked disabled but were visible. This meant that you had to scroll a lot and scan a lot of information with your eyes to see and understand all the policies, even though most of the users are probably only interested in a few policies anyway. In addition, Mozilla is already implementing more policies, do it’s becoming more of a factor with each new policy.
Therefore, the decision was made to only make visible what is relevant and to improve the UX. And if I don’t enable a policy, the suboptions have no relevance.
But additional input is required for a policy and there is no default value then there is a clear indication of the mandatory field(s).
I hope that makes sense.
Sören sure that makes sense. I did not mean to expose the entire options right away, just a small icon or something to indicate that you need to do more than just check the box to use the policy.
I didn’t use it (yet) but I like the idea of this addon. Thanks, Sören!
Nice one Sören, great extension (not that I have played with it yet)