Configure DNS Over HTTPS in Firefox
DNS over HTTPS is a relatively new feature designed to improve the privacy, security and connection reliability of DNS look-ups; the feature is currently in draft status and tested by companies such as Google, Cloudflare or Mozilla.
DNS resolves play an important part on today's Internet; domain names that you enter in your browser's address bar need to be linked to IP addresses, and that is what DNS is used for. These DNS look-ups happen automatically and often without any form of encryption or protection from prying eyes or tampering.
DNS over HTTPS attempts to fix this by sending DNS requests in encrypted form to a compatible DNS server so that these don't reveal the target of the request anymore to third-parties, e.g. someone on the same network or an Internet Service Provider.
Internet users up until now had options to connect to a non-leaking VPN provider, switch the DNS provider to one that promises better privacy and security, or use DNSCrypt to improve privacy and security.
DNS Over HTTPS in Firefox

DNS Over HTTPS offers another option. Mozilla added the core functionality in Firefox 60 and ran tests in Firefox Nightly to find out how good of a solution the new technology is.
Mozilla started to roll out DNS over HTTPS for Firefox users in the United States in 2019. The service is in fallback mode which means that the browser will first try to use DNS over HTTPS for the query and only if that fails traditional unencrypted DNS to ensure that the query is successful.
Firefox users in the United States will receive a popup notification in the browser when DNS over HTTPS is first enabled. The prompt explains what the feature does and includes an option to disable it.
Note that the feature won't be enabled if any of the following is found:
- Parental controls are used (as these often use DNS filtering).
- If the default DNS provider supports malware filtering.
- If the device is managed by an organization.
Users who opted in may opt out on about:studies at any time by removing the "DNS over HTTPS US Rollout" study.
Configure DNS over HTTPS manually in Firefox
Firefox users from around the world may configure the browser to use DNS over HTTPS. Type about:support to check the version of Firefox; it if it at least version 60.x, you may configure the feature. Please note that this may lead to connectivity issues (which may be limited by configuring a fallback).
Note: You may use a number of DNS over HTTPS supporting services now. You can check out the latest listing on GitHub. Some examples:
- Adguard: https://dns.adguard.com/dns-query
- Cloudflare: https://cloudflare-dns.com/dns-query
- Google RFC 8484: https://dns.google/dns-query
- Google JSON API: https://dns.google/resolve
- Open DNS: https://doh.opendns.com/dns-query
- Secure DNS EU: https://doh.securedns.eu/dns-query
- Quad 9: https://dns.quad9.net/dns-query
All current versions of Firefox come with options to enable DNS over HTTPs in the settings. These don't provide the same level of customization that the advanced configuration offers but it is easier to setup
It is necessary to change three Trusted Recursive Resolver preferences in the browser. Here is how that is done:
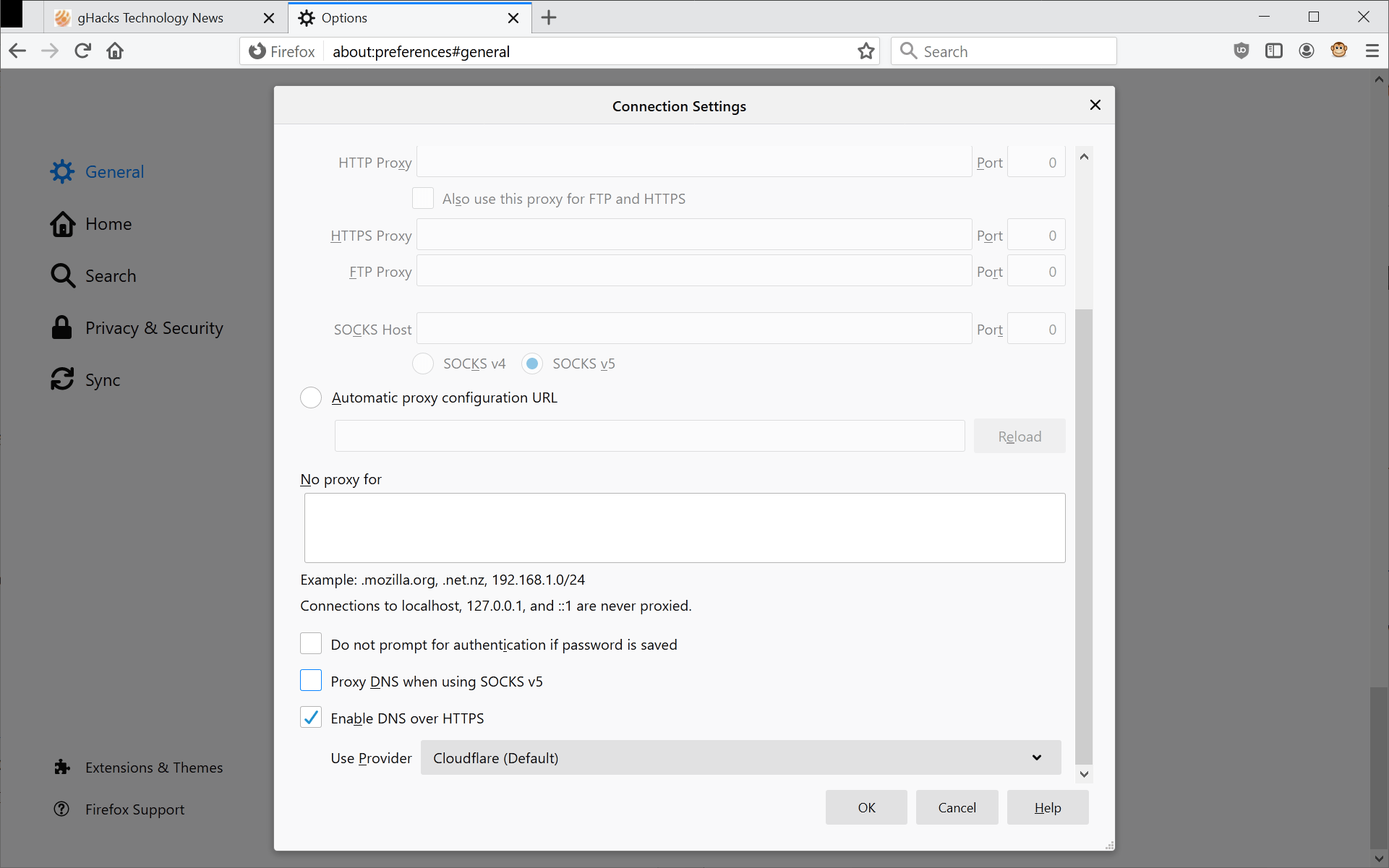
- Load about:preferences#general in the web browser's address bar.
- Scroll down to the Network Settings section (at the bottom of the page) and activate the Settings button.
- Scroll down on that page until you find the "Enable DNS over HTTPS" setting.
- Check the box and pick one of the providers (Cloudflare or NextDNS), or pick custom to specify a custom provider (see list above).
- Click okay to complete the configuration change.
Firefox users who want more control over DNS over HTTPS may configure additional details in the advanced configuration:
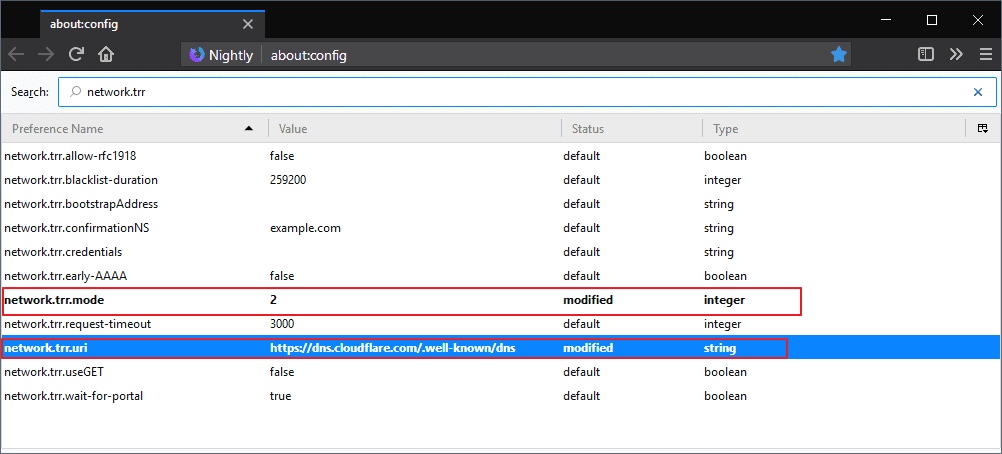
- Load about:config in the Firefox address bar.
- Confirm that you will be careful if the warning page is displayed.
- Search for network.trr.mode and double-click on the name.
- Set the value to 2 to make DNS Over HTTPS the browser's first choice but use regular DNS as a fallback. This is the optimal setting for compatibility.
- Set the value to 3 to only use DNS over HTTPS (no fallback).
- If you want to set it to off, set the value to 0. Configuration values 1 and 4 are no longer used.
- Search for network.trr.uri. Firefox expects a DNS over HTTPS server. Double-click on the name and add the URL of one of the providers listed above.
- Search for network.trr.bootstrapAddress and double-click on it. Note that this is no longer required from Firefox 74 onward if mode 3 is being used.
- Set the value to 1.1.1.1 (if you use Cloudflare, or look up the IP on the provider's website or use a DNS query tool to find out)
Tip: Use the preference network.trr.excluded-domains on about:config to exclude domains from DNS over HTTPS. Edit the value, add domains, and separate them with a comma. See also Mozilla's help article on configuring networks to disable Dns over HTTPs.
Note: Mozilla has a special agreement with Cloudflare which limits the logged data and data retention. Cloudflare launched the public DNs service 1.1.1.1 yesterday which supports DNS over HTTPS as well.
Tip: Check out our Firefox DNS over HTTPS article which lists all available parameters and what they do.
Closing Words
The core benefit of DNS over HTTPS is that you limit exposure of your DNS queries. You need to trust the public provider, Cloudflare or Google are the only ones right now. It is likely that other providers will introduce support for it if the feature is integrated into the stable versions of popular web browsers.
Now You: Have you changed the DNS provider on your devices?






















This can now be set in connection settings without having to dig in about:config
I have a problem with Google DNS over HTTPS.
I have set it up in Firefox correctly but 1.1.1.1/help says I am not using DNS over HTTPS?
Waiting for DoH in Chrome
Hey Ghacks, Google just update their DNS: https://security.googleblog.com/2019/06/google-public-dns-over-https-doh.html
Thank You!
Anyone get ESNI working on Firefox 66.03 stable on a Mac?
Not working for me. The rest do, just not ESNI
I’ve got a unique issue.
I have “network.trr.mode;2” set
I get a timeout when I’m on my work domain and enter an internal subdomain that’s not exposed to the outside.
I believe it’s because the fallback dns is external and has no record of the internal subdomains.
Is there anyway to have the fallback use the system dns? Or even a whitelist of domains that query internal domains.
Maybe I’m missing a setting.
Thanks!
You don’t have to use Cloudflare or Google, there is a large list of DNS over HTTPS servers you can use right here: https://github.com/curl/curl/wiki/DNS-over-HTTPS
Awesome article and comments, thanks a lot !
This is what worries me:
“Cloudflare will not retain or sell or transfer to any third party (except as may be required by law)”.
That part “required by law” in a country such as America means that NSA gets a copy of it.
If you need a filtered DNS, you can use CleanBrowsing DoH:
https://doh.cleanbrowsing.org/doh/adult-filter/ (to filter adult content)
https://doh.cleanbrowsing.org/doh/security-filter/ (to filter malware and phishing)
More details:
https://cleanbrowsing.org/dnsoverhttps
If i have cloudflare dns already setup in the router do i still need to change anything in the about:config?
Most current stock configurations resolve domains without encryption even if you’re using Cloudflare DNS (1.1.1.1) or Google DNS (8.8.8.8), unless you’re using something similar to Simple DNSCrypt for example.
DoH as explained in the article is about utilizing a DNS resolver over HTTPS within Firefox, so no other party would know which domains you’re visiting, except for the resolver you’re trusting, of course.
So if your router is configured already over HTTPS, then no, you don’t need to do anything. However, if it’s configured normally just by filling the two DNS IP fields, then yes, you should do it on Firefox as well or as I said earlier use tools such as Simple DNSCrypt.
I’ve waited for Firefox 60 to be released to test this because I run the stable branch of the browser. Now that it’s out, I can confirm that it’s working wonderfully and so far it’s running really well even on TRR only mode using Cloudflare.
Great guide and article.
I never bothered to run bleeding edge nightly versions but now that my country (S. Korea) started to censor[1] DNS request entirely (yes, entirely—even if you use third party dns like 8.8.8.8 or 1.1.1.1..its done at packet inspection level), I turned to nightly and thank you my internet is free again (well, at least until they introduce SNI censorship..which they promised to implement by 2019)
[1] https://translate.google.com/translate?sl=auto&tl=en&js=y&prev=_t&ie=UTF-8&u=http%3A%2F%2Fwww.mcst.go.kr%2Fweb%2Fs_notice%2Fpress%2FpressView.jsp%3FpSeq%3D16672&edit-text=&act=url
couldn’t find english resource. the detail is in the attached file which says they will (and has started by now) censor dns request then will implement sni censoring to block chosen https sites eventually. its said to be done for “Prevention of copyright infringement” purpose.
dosnt work with blocked pages.
i agree :(
it’s worked but not worked as well. When I’m trying to open any blacklisted adress, I got this error…
SSL_ERROR_RX_RECORD_TOO_LONG
The name “network.trr.bootstrapAddress” used to have to have a value of 1.1.1.1. But now it only works for me if I reset it to default, which is empty.
why it’s not working for me:(
my config :
http://uupload.ir/files/opnn_untitled.png
remove adrees from “NS” or reset it.
dnscrypt + a non logging servers. High time builds include this by default…
I doesn’t work on Android :/
Anyone having it working on Android?
My VPN (Mullvad) has their own DNS server so everything is routed through them.
Just notice if you do this on Firefox for Android, host based adblocking won’t work, which make sense since it relies on DNS lookups.
Martin, could it bypass Squid censorship?
Use “https://developers.cloudflare.com/1.1.1.1/dns-over-https/request-structure/” instead of the other one.
Source: https://developers.cloudflare.com/1.1.1.1/dns-over-https/request-structure/
…for dns over https in firefox beta 60: do i have to set network.trr.bootstrapAddress : 1.1.1.1 to, when i’m already using the public DNs service 1.1.1.1 ?
Then if you read a bit further…
“**any personal information, IP addresses or other user identifiers** from the DNS queries sent from the Firefox browser”
I note that if they assign you a UID (that can be based on, but not part of the DNS query), this promise is essentially worthless.
Then you read a bit further :)
Cloudflare will not sell, license, sublicense, or grant any rights to your data to any other person or entity without Mozilla’s explicit written permission.
WHY is this data needed for 24 hours if not used oh wait, they can sell it if Mozilla agrees?
Sometimes it looks like a service is running great, then you check the logs and your service is practically in flames.
You’ll also note that user IP somehow isn’t in the list: Resolver IP address refers to something else though this needs to be double checked
“oh wait, they can sell it if Mozilla agrees?”
That popped out at me too. It’s pretty strange and not terribly conducive to trust to put a loophole into their “we won’t abuse you” clause.
> WHY is this data needed for 24 hours if not used oh wait
@Anonymous
For network protection. Even fucking Startpage keeps some data for a day IIRC, and they have the best privacy policy I’ve ever seen
Having some logs around is helpful for troubleshooting. I’m not really bothered by that, though I would appreciate an explicit statement in their policy to the effect that this data is intended solely for that purpose.
>>>You need to trust the public provider, Cloudflare or Google are the only ones right now.
Trusting Google is sort of like trusting…………Facebook
Doesn’t work for me on 61 and setting number 3 with either provider address.
try `https://cloudflare-dns.com/dns-query` as in https://developers.cloudflare.com/1.1.1.1/dns-over-https/request-structure/
Thanks for the info, but I still can’t get it to work, accoding to user ak in the comments of this page it needs further steps also:
https://www.ghacks.net/2018/03/20/firefox-dns-over-https-and-a-worrying-shield-study/
but I still couldn’t get it to work after following them either, I am on todays FF Nightly.
Change this line too:
network.trr.bootstrapAddress
with value 1.1.1.1
That works for me
Same here. But after changing this value
network.trr.bootstrapAddress;1.1.1.1
the DoH works fine in Firefox
Thanks for your help, I got it going adding that setting too, Martin should add that info in the article IMO.
Interesting feature. :)
Cloudflare will “only” collect the following…
https://developers.cloudflare.com/1.1.1.1/commitment-to-privacy/privacy-policy/firefox/
No thanks.
Much less than what the ISP collects (ie everything)
LOL #Fact
@Anonymous Replied out of the comment tree by mistake: See here https://www.ghacks.net/2018/04/02/configure-dns-over-https-in-firefox/#comment-4368109
@ Anonymous
I second your “no thanks”. WHY is all this information required by Cloud flare ?? :(
Because you’re not paying for this service and none of these companies has any incentive to give free, expensive service for nothing. If they anonymize it, and deleting the bulk of it – give it a break.
Quote:
>All of the above information will be stored briefly as part of Cloudflare’s temporary logs, and then permanently deleted within 24 hours of Cloudflare’s receipt of such information
Sorry Martin, started at the top and was working my way down.
How do you know when it’s working?
about:networking#dns . if all TRR entries = “false”, it’s not working.
Thank you !
You could set the value to 3 to enforce the use and see what happens. I’m not entirely sure how to see that easily, you could monitor traffic as suggested here: https://www.robertputt.co.uk/securing-dns-traffic-with-dns-over-https.html
Interesting. Do you have any thoughts on 1.1.1.1 ?
https://blog.cloudflare.com/announcing-1111/
Yes, https://www.ghacks.net/2018/04/02/cloudflare-launches-fast-and-privacy-focused-dns-at-1-1-1-1/