KB4077528 and KB4077525 for Windows 10 released
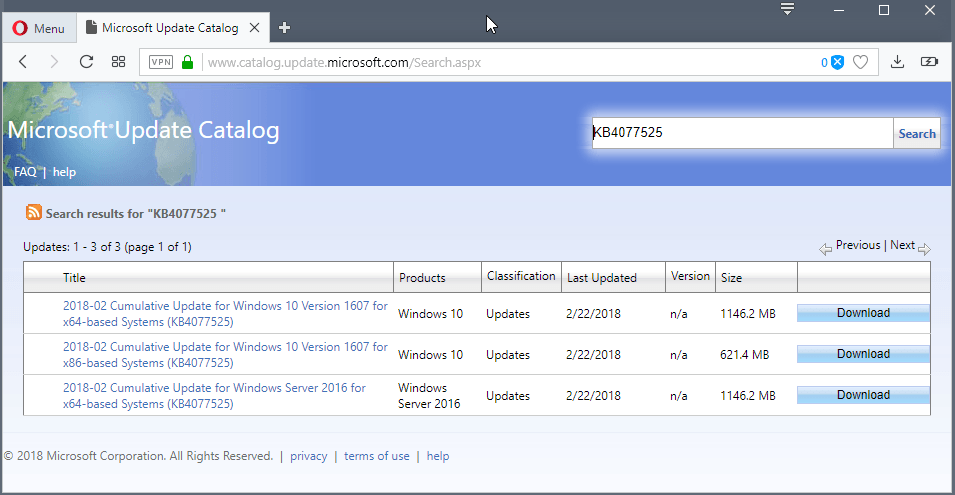
Microsoft released two cumulative updates for Windows 10 version 1607 and Windows 10 version 1703 yesterday under KB4077528 and KB4077525.
About 15% of all Windows 10 devices don't run the latest version, the Windows 10 Fall Creators Update, according to AdDuplex. While the Fall Creators Update should be available to all customers -- minus the ones that have incompatible hardware -- some admins and customers prefer not to install it yet or cannot install it because they run into issues doing so.
One of my machines is still on Windows 10 version 1703 because the update to version 1709 throws a BlueScreen error during the update process which I cannot get resolved on my end.
On to the February 22, 2018 released patches for Windows 10
KB4077525 for Windows 10 version 1607

KB4077525 is a massive non-security update for Windows 10 version 1607, also known as the Anniversary Edition of the operating system.
The update is available via Windows Update and also on the Microsoft Update Catalog website as a direct download.
It introduces the following improvements and fixes:
- Fixed Citrix XenApp users cannot change passwords using Ctlr-F1.
- Fixed error Access is denied. (Exception from HRESULT: 0x80070005 (E_ACCESSDENIED)) for members of the Performance Log Users group.
- Fixed error 0x6c6 (RPC_S_INVALID_BOUND) from target servers for WinRM event queries.
- Fixed a Microsoft Outlook authentication issue.
- Fixed the smart card logon error Signing in with a smart card isn’t supported for your account... after the authenticating DC has been restarted.
- Addressed issue with the certutil.exe -MergePfx command.
- Addressed SM3 cryptographic hash algorithm support issue on TPM devices.
- Addressed 0x06d9 failure issue during OS upgrades or LCU updates.
- Fixed error Stop D1 in tcpip!TcpSegmentTcbSend during file transfers.
- Addressed Remote Authentication Dial-In User Service (RADIUS) authentication issue during wireless network connections.
- Fixed iSCSI target redirection stop error 9f.
- Foxed stop error in MPIO.
- Updates MPIO path selection algorithm.
- Addressed CPU use increase issue in delay function in StorNVMe.
- Improves ReFS performance.
- Fixed Unified Write Filter and a connected USB hub booting issue that throws stop error E1.
- Fixed Internet connection service (ICS) connections don't persist across OS restarts or ICS service restarts.
- The correct public IP is cleaned for the SDN Network Manager.
- ADCS support for Certificate Transparency (CT) added.
- Addresses issue where there is missing information in the Value field of audit event 5136 for Directory Service Changes.
- Addresses issue where an HTTP 500 error occurs when an ADFS farm has at least two servers using Windows Internal Database (WID).
- Addresses issue in which AD FS can no longer ignore prompt=login during authentication.
- Addressed Certificate selection authentication issue in AD FS.
- Addresses issue where AD FS incorrectly displays the Home Realm Discovery (HRD) page when an identity provider (IDP) is associated with a relying party (RP) in an OAuth Group.
- Addresses issue where some Remote Desktop Protocol (RDP) clients that used an absolute URI (instead of a relative URI) were blocked by the Web Application Proxy (WAP) server from connecting to the Remote Desktop Gateway.
- Addressed the cause of the error messages "Error: 'XMLSerializer' is undefined", "‘DOMParser’ is undefined" and "Server execution failed" in GPMS reports.
- Addressed two Dedup data corruption issue for 2.2 TB or larger files.
- Fixed the DFS-Replication Group error The value does not fall within the expected range.
- Fixed Create Cluster wizard may unexpectedly close when selecting browse on the select servers page.
- Fixed Japanese keyboard layout issue during Remote Assistance sessions.
- Addresses issue where logons to a Remote Desktop VDI collection start to fail after a period of server uptime.
The cumulative update as two known issues. The first blocks updates if incompatible antivirus solutions are installed.
The second describes a server restart issue if Credential Guard is enabled. The error is "he system process lsass.exe terminated unexpectedly with status code -1073740791. The system will now shut down and restart".
The only workaround right now is to disable Windows Defender Credential Guard.
KB4077528 for Windows 10 version 1703
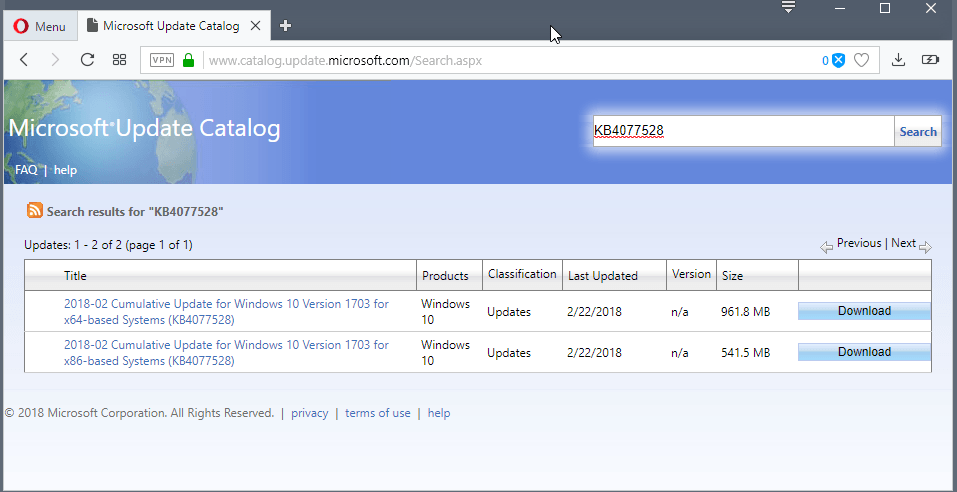
KB4077528 is a non-security update for Windows 10 version 1703. It is available via Windows Update and on Microsoft's Update Catalog website.
The update includes the following fixes and improvements:
- Addressed read or write attributes issue using Get/SetWindowWord, Get/SetWindowLong, or Get/SetWindowLongPtr.
- Fixed an Internet Explorer response issue that caused the desktop to appear with delays, the Start Menu to become unresponsive, and some system tray icons to disappear.
- Fixed Performance Log Users error message Access is denied. (Exception from HRESULT: 0x80070005 (E_ACCESSDENIED)).
- Fixed Microsoft Outlook authentication issue.
- Addressed Device Guard rules reliability issue that may cause the system to stop working.
- Addressed 0x06d9 failure during OS upgrades or LCU updates.
- Addressed file transfer error Stop D1 in tcpip!TcpSegmentTcbSend.
- Addressed print server wildcard character issue that prevented the Point and Print Restrictions Group Policy from taking effect.
- Addressed Remote Authentication Dial-In User Service (RADIUS) authentication issue.
- Fixed iSCSI target redirection error stop error 9f.
- Addressed server-side performance regression and poor transfer rates for high-latency scenarios.
- Addresses issue where the Internet connection service (ICS) connections don't persist across OS restarts or ICS service restarts.
Now You: Have you installed these updates? What's your experience?




















KB4077525 pulled for Windows 2016 server.
Worked but took up to 10 hours to install causing people to force reboot
They force people to upgrade from Windows 7 and 8.1. Now some of these devices can’t run the latest version…. Microsoft has become a shithole on Earth !
My legit 1709 was constantly rebooting at odd times, always when I wasn’t there to see it, and desktop icons constantly moving and game bar giving me ridiculous FPS issues in some games and all this because I foolishly upgraded from 1706 that I was happy with.
So I went to r/piracy and am running a “trial” version of Enterprise 1607. Fixed all my issues.
Maybe Windows is running Denuvo on the background, need to get the pirated version to play smoothly
@IFK,
I may be wrong. But check your video driver on 1709. When I was having issues on the AMD machine, MS had substituted their VD for the NVIDIA one I was using.
Just a thought.
I am at 1709 on my end. The Intel machine went smoothly. The AMD machine had an issue was rolled back using a full disk backup. It’s now at 1709.
SM3 cryptographic hash algorithm support issue on TMP devices.
TPM devices?
Trusted Platform Module. It’s a hardware feature used for full disk encryption, Microsoft’s BitLocker uses it by default. It’s a “convenience first” way of FDE and not the most secure one, imo. It’s actually completely useless, it only helps you if someone steals your HDD but leaves you your laptop for instance, lol.
“It’s actually completely useless, it only helps you if someone steals your HDD but leaves you your laptop for instance, lol.”
No, it’s not, wether the thief has your laptop or only its HDD changes nothing to the fact that Bitlocker’s encrypted disk will not magically unlock … Even if the thief has the laptop, the disk won’t be unencrypted: TPM will just act as a “key” to unlock disk and boot the OS on the encrypted disk without the hassle of typing a password to unlock it.