Enable unwanted redirection protection in Google Chrome
Google plans to enable a new security feature in Chrome 64 Stable that protects users from several forms of unwanted redirects on the Internet.
Unwanted redirects come in many forms, but they all have in common that users are redirected to web pages they did not request.
Google discovered that these redirects come often from third-party scripts embedded in those sites; in fact, Ghacks' mobile site experienced such a issue just recently where Google ads redirected users to a different site.
We've found that this redirect often comes from third-party content embedded in the page, and the page author didn't intend the redirect to happen at all
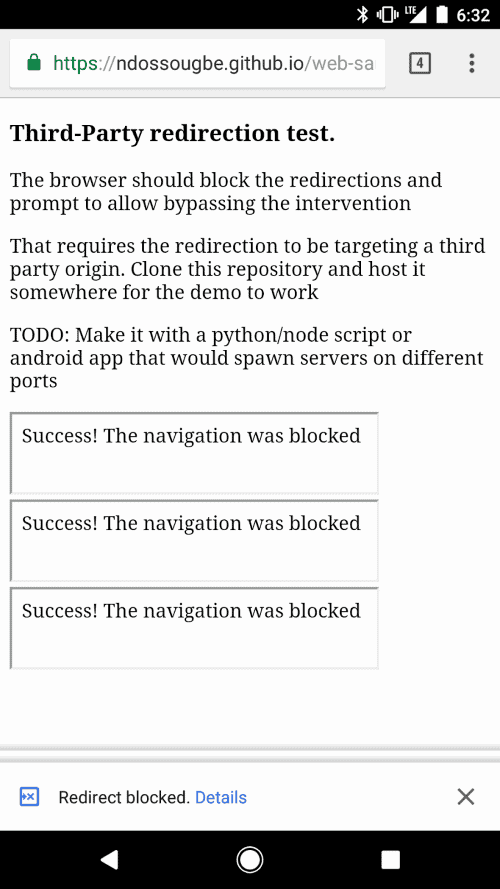
Google Chrome will display a notification in the browser UI if content on a web page attempted to redirect to another page or content starting in Chrome 64. The redirection happens when users interacted with the content that is responsible for the redirection.
Google plans to address another issue related to unwanted redirects, this one in Chrome 65. This particular form of unwanted redirection happens after user actions, for instance the click on a button or link.
Sites that implement these technologies may open the destination of the link or button in a new tab, and load other content in the active tab the user sees at the time.
Google Chrome 65 will display a notification in the browser UI when it detects that sites have that behavior, effectively blocking it.
The company acknowledges that other forms of abusive redirection behavior exist that are harder to detect.
These include links to third-party websites disguised as play buttons or other site controls, or transparent overlays on websites that capture all clicks and open new tabs or windows.
Google announced previously that Chrome will come with an improved popup-blocker that prevents these scenarios.

Chrome users who don't want to wait this long can enable the new unwanted redirection protection right now in Chrome:
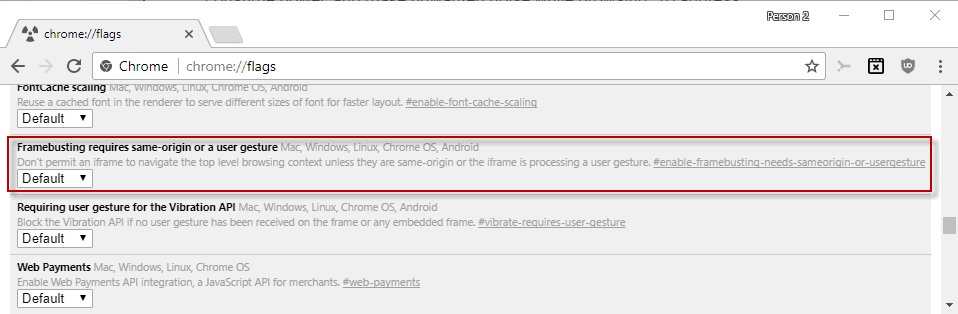
- Load chrome://flags/#enable-framebusting-needs-sameorigin-or-usergesture in the browser's address bar.
- Switch the status of the "Framebusting requires same-origin or a user gesture" experimental flag from default to enabled.
- Restart the Chrome browser.
Webmasters may check the Abusive Experiences Report that Google added to its search console for webmasters to find out if Google detected any violations on sites.
Closing Words
It is about time that browser makers do something about unwanted redirection and other abusive behavior on the Internet. It is not without irony that Google announced these changes, considering that the company's Adsense/Adwords division allows ad scripts with this abusive behavior on its network (allows meaning that these scripts run on sites).
Now You: What is your take on these changes?




















Firefox has had this option or used to have this option for years.
this is hardly innovation and does not invoke confidence.
what a childish comment
https://ndossougbe.github.io/web-sandbox/interventions/3p-redirect/ link to test (from article)
Thanks Stefan.
Is there anything comparable in Firefox (about:config or add-on)? :)
I’m not aware of any about:config entry that is comparable to the framebusting flag in Chromium browsers, which by the way has been available for months. I’m hoping Mozilla will come up with something similar.
As far as addons go there are a bunch of different options. One of the easiest options, if you already use uBlock Origin, is to globally disable 3rd-party frames, which will work on the link in the comment by Stefan which is below your comment. Because I’m lazy, I only disable 3rd-party frames myself, but you could also globally disable 3rd-party scripts, 1st-party and inline scripts as well, which is all way to hard-core for me personally. With my uBO config I can’t remember the last time I experienced a redirect, it’s been a very long time. ;)
That said, globally disabling 3rd-party frames is a huge improvement security wise. One side-effect will be that it will prevent a lot of embedded videos and images. I use a little over a dozen noop rules, that have to be entered into the “My rules” tab of uBO, the rules allow almost all embedded content that I run across. It’s not hard to figure out the rules. FB, Instagram, Twitter and YouTube are a few.
Other options for addons are NoScript, uMatrix which I like better but currently have disabled, Javascript Control and No-Script Suite Lite which is what I’m using now but it doesn’t block 100% of javascript in FFv56 but does a better job in Nightly but still not 100%, oddly enough it works perfectly in Chromium browsers. I like addons that by default block javascript, meaning js is off until it is enabled per site and then remembered in a whitelist, first day or two will be a pain. That way when going to a new site you are automatically protected. There are addons for js where the default is on but I haven’t used any, might as well just bookmark “about:config?filter=javascript.enabled” and do it yourself.
You can test the effectiveness of an addons ability to block javascript by going to: “http://tools.add0n.com/check-javascript.html”
I’ve been seeing inconsistent results when using No-Script Suite Lite in FF, Nightly and Waterfox when testing using the site that I linked to in the above post. I was able to get the addon working 100% in all of my browsers by uninstalling then deleting the “{86d73a1c-2ec5-4b7a-b249-60cec805dc99}” folder from inside the “browser-extension-data” folder that is inside the profile folder and then re-installing. A new install should be fine. I like No-Script Suite Lite because it’s light on resources and very simple. In the past I had swapped the extension folder between browsers to get them all using the same list, maybe that’s what screwed it up. Just a guess.
I thought I was the only one who used the lazy approach of just blocking 3rd-party iframes by default, haha…
Rarely a site breaks because of that and, as a plus, there’s a huge security benefit. I only had to noop a few rules globally a few months ago and that’s it.
Of course the better approach would be to block 3rd-party scripts along with 3rd-party iframes (which is basically the medium mode), but it’s just a pain in the ass and it gets tedious very quickly.
Glad to know that the test mentioned in the article is circumvented by blocking 3rd-party iframes globally.
Google is only doing this to discourage users from installing ad blockers on Chrome.
They plan to implement an anti-coin miner on the browser because of the same thing.