How to enable Firefox WebExtensions on Mozilla websites
One of the limitations of the new WebExtensions add-on system of the Firefox web browser was up until now that these extensions would not work on some websites operated by Mozilla.
Only WebExtensions are hit by the limitation, and it means that functionality that these extensions provide is not available on sites and services such as addons.mozilla.org or www.mozilla.org.
Extensions cannot manipulate these pages in any way, for instance to provide additional functionality on them, modify content, or even block elements on them.
Update:
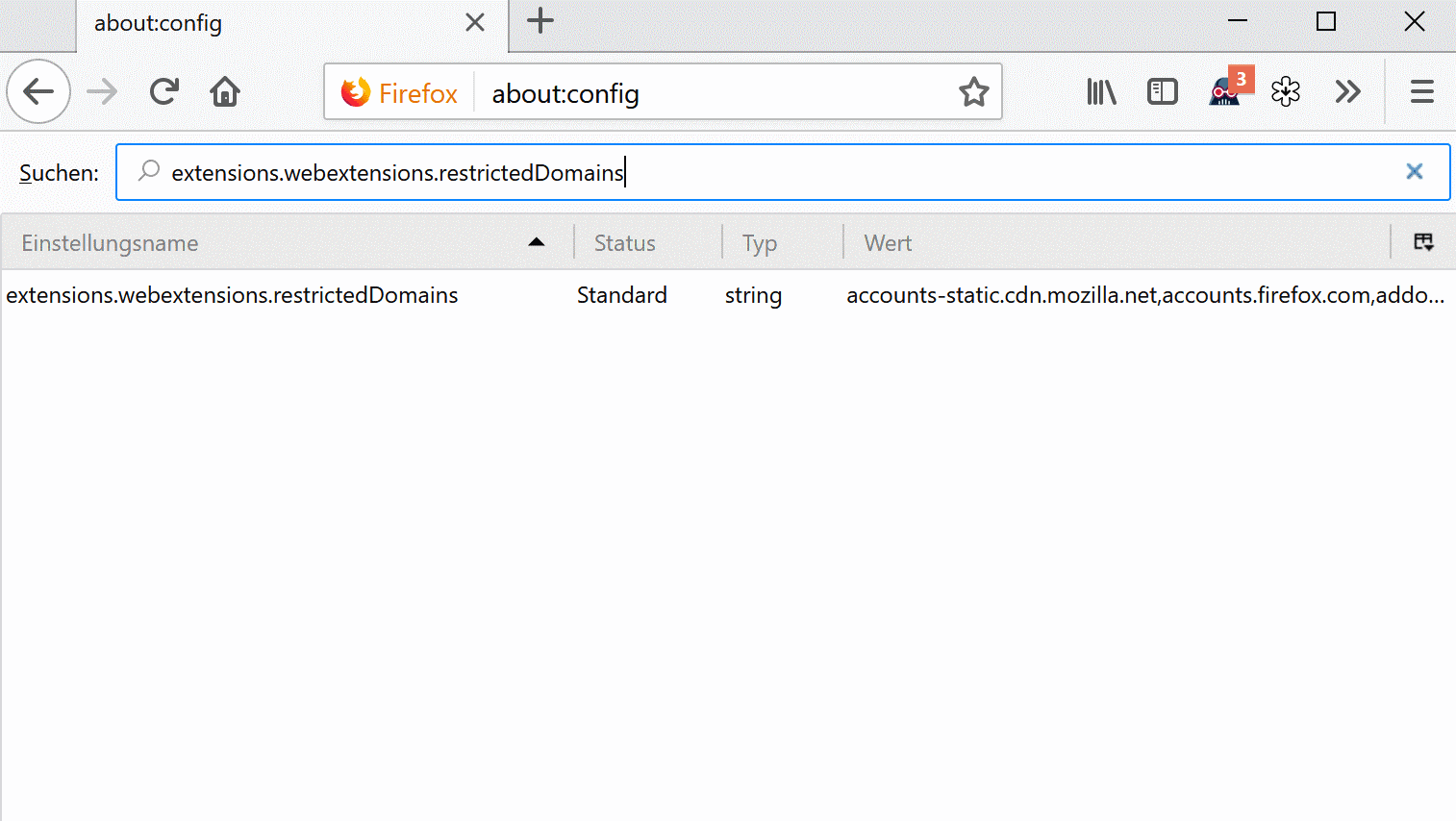
Mozilla changed the functionality in Firefox 60. Firefox 60 comes with a new preference called extensions.webextensions.restrictedDomains which lists domains that WebExtensions are not permitted to run on by default.
- Load about:config?filter=extensions.webextensions.restrictedDomains in the Firefox address bar.
- Remove one, some or all of the domains listed under value to remove the restriction.
Mozilla added a new -- hidden -- preference to Firefox 57 that you can set to do away with the limitation in the Firefox web browser.
Hidden preferences are those that are not visible by default when you open the about:config page of the web browser. They do exist, but you do need to know them to set them in the browser.

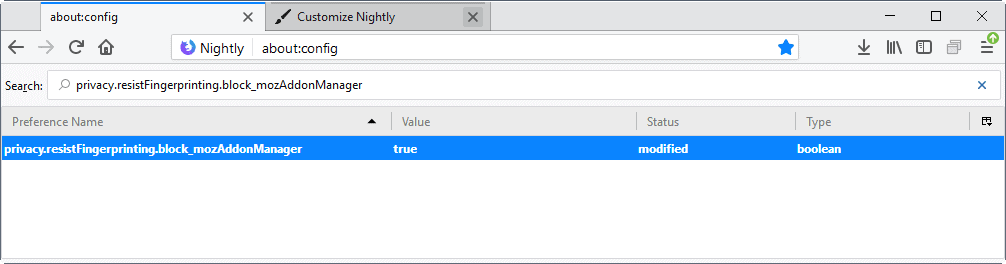
The hidden Firefox preference privacy.resistFingerprinting.block_mozAddonManager removes the WebExtensions restriction.
Here is how you set it:
- Load about:config in the Firefox web browser.
- You can run a search for privacy.resistFingerprinting.block_mozAddonManager just to make sure it does not exist. It does not in the most recent Firefox Nightly builds at the time of writing.
- Right-click in the part of the window that lists the preferences, and select New > Boolean from the context menu.
- Name the new Boolean value privacy.resistFingerprinting.block_mozAddonManager.
- Set its value to true.
A value of true means that WebExtensions work normally on Mozilla's website. You can undo the change at any time by setting the preference to false on the about:config page of the browser.
Mozilla added the new hidden preference to Firefox 57. It is not available in Firefox 56, and there is no option to introduce it in the browser. Firefox Stable users who run WebExtensions right now need to wait until the browser is updated to version 57 to set the preference and gain the functionality






















Always helpful thanks! It works on 69 nightly version
Mozilla is doing something weird again on addons.mozilla.org
The extension imagus is not working again on AMO and when i click on uBlock Origin’s Element Zapper or Element Picker on AMO i get a weird pop up at the top left which i’ve never seen on any other website.
Anyone else ?
i will restart Firefox and retest it soon. i’ll come back and update my findings.
Restarting Firefox made no difference.
Thanks, very useful! Does exists any ways to enable WebExtensions in Firefox in new tab, about:*, error pages, etc? This is very needed for Mouse Gestures extensions.
You now have to both create the Preference privacy.resistFingerprinting.block_mozAddonManager and set it to True
and Edit or Delete everything in the Preference extensions.webextensions.restrictedDomains
This doesn’t work anymore in Firefox 60+
the new key is
extensions.webextensions.restrictedDomains
This doesn’t appear to work anymore in Firefox 60.
Can anyone confirm?
Thank for the links. Was wondering why and thought I need to restart the browser. After clearing the preference “extensions.webextensions.restrictedDomains” and did a Refresh, it worked on the Add-on Page https://addons.mozilla.org/
Is there a way to remove the restricted on Internal About Page too? e.g. About:Config or About:Addons.
Once that is figure out, I guess I might consider Firefox 57+
A quick Google search shows that you now also have to edit the “extensions.webextensions.restrictedDomains” option to remove the domains you want to use WebExtensions for.
I’ve just changed the option so it is blank and that fixes the problem for me.
After the latest updates of FF dev. some more work is needed to get around the issue. Check this https://www.reddit.com/r/firefox/comments/84mghw/firefox_60_beta_lost_the_amo_working_extensions/
Thank for the links. Was wondering why and thought I need to restart the browser. After clearing the preference “extensions.webextensions.restrictedDomains” and did a Refresh, it worked on the Add-on Page https://addons.mozilla.org/
Is there a way to remove the restricted on Internal About Page too? e.g. About:Config or About:Addons.
Once that is figure out, I guess I might consider Firefox 57+
Not sure about that, maybe some very savvy folks know how to do it, but it hasn’t been shared so far.
Okay. So how do I defeat this “security” feature on FF56?
“Is there a pref. like this to make extensions work on internal pages, like about:addons and about:newtab?”
looking for this too, wanted to use mouse/mobile gestures in this pages, didn´t find anything yet, hope mozilla come up with native gestures to “solve” this
Is there a pref. like this to make extensions work on internal pages, like about:addons and about:newtab?
Great! It also works for Firefox Screenshots.
For those who care about security implications https://bugzilla.mozilla.org/show_bug.cgi?id=1406795
Read it. Confused. Outside of a rogue extension modifying AMO, is there any risk?
From what I understand, as long as you read UI prompts properly, you’re safe even if a rogue extension that you installed modifies AMO. But if you have a rogue extension you really have other problems than having it trick you into installing another rogue extension.
Absolutely fantastic tip.
Thank you Martin.
FYI: mozAddonManager API only covers these websites – https://dxr.mozilla.org/mozilla-central/source/toolkit/mozapps/extensions/AddonManagerWebAPI.cpp : addons.mozilla.org – discovery.addons.mozilla.org – testpilot.firefox.com
It was added for the Tor browser uplift. I hope Mozilla do not close this loophole. The protected about pages is not an issue (for me) since I block activity stream etc, and I do not use (and indeed hide) the get addons panel – so this closes all the GA BS’ery once and for all.
Wish extensions weren’t protected :-( Have to pay close attention to what they do and sniff like a beagle now
> Wish extensions weren’t protected :-( Have to pay close attention to what they do and sniff like a beagle now
Aren’t special rights being discussed ? I think I saw something like that, where for instance uBO would be able to control another add-on.
When I read that on Bugzilla, I couldn’t be certain that my understanding was correct. On top of that it was a couple months ago and my memory could be failing me. But I’ve got some vague hope lingering since then.
Do you, any anybody else, understand why this is categorized under ‘privacy.resistFingerprinting’?
*by 58 at the latest
AMO respects Do Not Track. If you go there with DNT enabled you don’t need to have anti-fingerprinting measures on Mozilla sites.
I tend not to use DNT, so I am happy that this pref is implemented into Firefox 57. To be honest I didn’t believe there wouldn’t be such a pref by at least 58.
So, wait, it’s concern that info is being exposed to AMO?
If you’re okay with data being exposed to AMO (and only AMO) is there any harm in enabling this pref?
Because it stops data being exposed to AMO (which can lead to tracking, FP’ing etc). Tor have no interest in AMO, they just want all users and data treated the same: i.e anonymous and protected as much as possible
https://bugzilla.mozilla.org/show_bug.cgi?id=1384330
https://bugzilla.mozilla.org/show_bug.cgi?id=1384330
>In Tor Browser, to protect against fingerprinting, we block window.navigator.mozAddonManager data from being exposed to AMO. We would like to propose uplifting this protection behind the “privacy.resistFingerprinting” pref.