CCleaner Malware second payload discovered
A new report by Cisco's Talos Group suggests that the CCleaner hack was more sophisticated than initially thought. The researchers found evidence of a second payload during their analysis of the malware which targeted very specific groups based on domains.
On September 18, 2017 Piriform reported that the company's infrastructure distributed a malicious version of the file cleaning software CCleaner for about a month.
The company's infrastructure was compromised, and users who downloaded version 5.33 of CCleaner from the website or used automatic updates to install it, got the infected version on their system.
We talked about methods to identify if an infected version is installed on the system. Probably the best indicator, apart from checking CCleaner's version, is to check for the existence of Registry keys under HKLM\SOFTWARE\Piriform\Agomo.

Piriform was quick to state that users could resolve the issue by updating to the new malware-free version of CCleaner.
A new report suggests that this may not be enough.
Talos Group found evidence that the attack was more sophisticated, as it targeted a specific list of domains with a second payload.
- singtel.corp.root
- htcgroup.corp
- samsung-breda
- samsung
- samsung.sepm
- samsung.sk
- jp.sony.com
- am.sony.com
- gg.gauselmann.com
- vmware.com
- ger.corp.intel.com
- amr.corp.intel.com
- ntdev.corp.microsoft.com
- cisco.com
- uk.pri.o2.com
- vf-es.internal.vodafone.com
- linksys
- apo.epson.net
- msi.com.tw
- infoview2u.dvrdns.org
- dfw01.corp.akamai.com
- hq.gmail.com
- dlink.com
- test.com
The researchers suggest that the attacker was after intellectual property based on the list of domains that belong to high profile tech companies.
Interestingly the array specified contains Cisco's domain (cisco.com) along with other high-profile technology companies. This would suggest a very focused actor after valuable intellectual property.
Talos Group suggested to restore the computer system using a backup that was created prior to the infection. The new evidence reinforces this, and the researchers suggest strongly that it may not be enough to simply update CCleaner to get rid of the malware.
These findings also support and reinforce our previous recommendation that those impacted by this supply chain attack should not simply remove the affected version of CCleaner or update to the latest version, but should restore from backups or reimage systems to ensure that they completely remove not only the backdoored version of CCleaner but also any other malware that may be resident on the system.
The stage 2 installer is GeeSetup_x86.dll. It checks the version of the operating system, and plants a 32-bit or 64-bit version of the trojan on the system based on the check.
The 32-bit trojan is TSMSISrv.dll, the 64-bit trojan is EFACli64.dll.
Identifying Stage 2 Payloads
The following information helps identify if a stage 2 payload has been planted on the system.
Registry Keys:
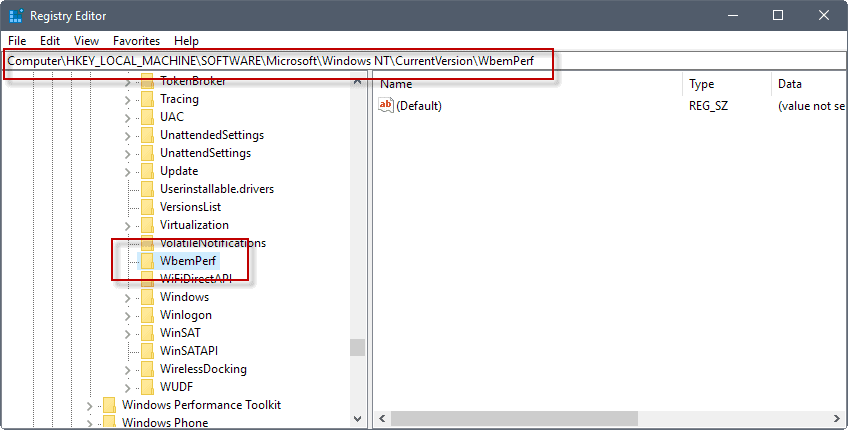
- HKLM\Software\Microsoft\Windows NT\CurrentVersion\WbemPerf\001
- HKLM\Software\Microsoft\Windows NT\CurrentVersion\WbemPerf\002
- HKLM\Software\Microsoft\Windows NT\CurrentVersion\WbemPerf\003
- HKLM\Software\Microsoft\Windows NT\CurrentVersion\WbemPerf\004
- HKLM\Software\Microsoft\Windows NT\CurrentVersion\WbemPerf\HBP
Files:
- GeeSetup_x86.dll (Hash: dc9b5e8aa6ec86db8af0a7aa897ca61db3e5f3d2e0942e319074db1aaccfdc83)
- EFACli64.dll (Hash: 128aca58be325174f0220bd7ca6030e4e206b4378796e82da460055733bb6f4f )
- TSMSISrv.dll (Hash: 07fb252d2e853a9b1b32f30ede411f2efbb9f01e4a7782db5eacf3f55cf34902 )
- DLL in Registry: f0d1f88c59a005312faad902528d60acbf9cd5a7b36093db8ca811f763e1292a
- Stage 2 Payload: dc9b5e8aa6ec86db8af0a7aa897ca61db3e5f3d2e0942e319074db1aaccfdc83



















I was a big proponent of Ccleaner and taught it’s use in my classes. Decided to let it go and installed Bleachbit, same as I use for Linux. Be careful with it if you switch. Read the how to use. I also switched to Avast from Avira.
Hi, not got an issue, as my system is 64-bit, and I did not install this bad release (It was just in my download area, luckily I did not have time to install it). Just curious why the “second stage” info includes “EFACli64.dll” as this is a LEGITIMATE Norton AV module (Extended File Attributes CLI handler), in its x86 file path. Does the author mean a bad DLL with the SAME name, but in a DIFFERENT area than the Norton AV program area?
“Craig Williams, a senior technology leader and global outreach manager at Talos, said […] ‘When you look at this software package, it’s very well developed. This is someone who spent a lot of money with a lot of developers perfecting it. It’s clear that whoever made this has used it before and is likely going to use it again.’ ”
https://arstechnica.com/information-technology/2017/09/ccleaner-malware-outbreak-is-much-worse-than-it-first-appeared/
The article quotes Craig Williams (a senior technology leader and global outreach manager at Talos) when he states:
“Now that it’s known the CCleaner backdoor actively installed a payload that went undetected for more than a month, Williams renewed his advice that people who installed the 32-bit version of CCleaner 5.33.6162 or CCleaner Cloud 1.07.3191 reformat their hard drives. He said simply removing the stage-one infection is insufficient given the proof now available that the second stage can survive and remain stealthy.”
Now this is serious business. A payload in progress.
I checked the registry wbemPerf and mine shows exactly as shown in the screen shot towards the end of the article “Type”=REG_SZ “Data” =(value not set)
Does this mean I’m safe? My win 10 x64 defender detected and quarantined the virus. I uninstalled it using revo uninstaller and did an advance scan and cleared all left over registry then re installed ccleaner to the latest version.
I have no restore points and am dreading if I need to re install my windows…
Please tell me is that registry key normal? I will check the second payload keys now..
Thanks!
@Emrah — There is a possibility that the hackers could have coded the trojan to trigger different batches of infected PCs call home & download additional 3rd/4th etc. malicious payloads at different time periods. Exactly when one gets “called up for service” may depend on one’s “usefulness” profile, geographic region, IP address, WIn OS version, etc.
So for Stage 1, if your WbemPerf registry key is empty, it merely means that you might be safe where Stage 1 is concerned. Since the hacker-suspects are known to be very sophisticated, there might be further stages of deployment for infected machines.
Stage 2 Symptoms: Since you are using Win 10 x64 (home PC presumably), you may wish to check if the following DLL files exist on your system & if they are legitimately signed:
A) TSMSISrv.dll (signed by: Microsoft)
B) VirtCDRDrv.dll (signed by: Corel Inc.)
C) localspl.dll (signed by: Microsoft)
Files A & B probably shouldn’t exist on a home (non-server) version of Win OS, & if you have never installed any Corel-related software. If you have File C (the legit file itself is related to Windows printer spooler), make sure that it is digitally signed by Microsoft, & that the signing date isn’t too recent.
If any of the above files exist AND are not signed, they are malicious FAKE files generated by the Floxif trojan, & their presence likely implies a Stage 2 infection.
Note: The above is all that is publicly known at this point in time (as of 21/22 Sep 2017), for investigations are incomplete, So it can’t be discounted that there could be future stages of deployment involving other infected files.
In case of any signs of infection, stop using the PC immediately, & get the HDD formatted before fresh-installing Win OS. Use a different user login password for the new Win OS install, & make sure to carefully scan whatever backup files you might be transferring to the new install. In addition, after making sure that your PC/ new install is not infected, change all your offline & online passwords ASAP.
Regardless of whether one’s PC currently exhibits infection symptoms or not, as long as one has used the trojan-compromised version of CCleaner, it is best to practise vigilance during the upcoming weeks or even months. An analogy would be to treat this malware episode like how one might monitor an infectious biological epidemic involving unknown pathogens with unpredictable behaviours. Good luck & keep safe always !
Wow! Very much appreciate all the comments, information and links. I’ve always been one to intentionally drag my feet updating to the newest software versions, unless it’s a critical update. Now I definitely have more incentive to stay apprised of the frequency and why. I actually put off updating CCleaner for a couple weeks thinking that might give enough time for any ‘bugs’ related to the new acquisition to come to light but still ended up with v5.33 on my system. Wouldn’t Avast have done a security audit on Piriform before the purchase? Anyway, I think I will reevaluate my update frequency, how necessary it is, and… let others be the beta testers. ;)
Good read, not to technical
blog.talosintelligence.com/2017/09/avast-distributes-malware.html
a few comments at the bottom.
For info, based on an initial MalwareBytes’ threat scan report, another registry key that might point to infection by the 1st-stage payload is:
HKU\S-1-5-21-1758246276-2774224944-794278675 …
Ref: [https://www.bleepstatic.com/swr-guides/f/floxif/mbam-floxif.jpg]
This Floxif-Nyetya trojan (ie. 1st-stage payload injected into CCleaner’s binaries at Piriform’s backend build environment) is known to further propagate itself by injecting malicious code into other legitimate (& hence presumed safe) executable files on the compromised PC. Biological analogy: A virus contagion that rapidly mutates into various forms to further infect other cells in the body.
Besides collecting various system & device data, the trojan may also record keystrokes — think: Windows user login, database login, online services login, banking credentials, etc.
So it’s surprising that Piriform & Avast (earlier) claimed that the only remedial action necessary is to update CCleaner to the latest clean version. In fact, besides either reverting the infected machine to a known-safe restore point/ image backup or even formatting the HDD & reinstalling WIn OS, to be on the safe side, one might also have to change all online passwords from a known uninfected machine. And of course, don’t reuse the same system & local database login passwords after system restore/ reinstall.
So far, this particular strain of the Floxif/Nyetya trojan is known to infect & inject bad code into the below files — which may not comprise an exhaustive list, since file forensics is still ongoing, & the 2nd-stage payload may possibly exhibit further mutation activity, &/or contact another (unknown but working) server to fetch additional mutable trojan payloads …
On Win 7 & above:
C:\Windows\system32\TSMSISrv.dll (related to Windows’ Terminal Server & Remote Desktop Session), which in turn generates an infected VirtCDRDrv.dll (ie. masquerading as Corel Inc’s VirtCDRDrv Module).
On Win XP:
C:\Windows\system32\spool\prtprocs\w32x86\localspl.dll (related to Windows’ Local Printer Provider & print spooler), which in turns generates an infected SymEFA.sys (ie. masquerading as Symantec Endpoint’s Protection Client).
According to the severely-limited amount of logs available (only 3 days, since all the earlier days were wiped from malicious server), 20 machines are known to have already contacted the malicious server & downloaded the 2nd-stage payload. Based on extrapolation, Avast & Cisco-Talos surmised that the actual number of machines that downloaded the 2nd-stage payload should be at least “in the order of hundreds” to date (21 Sep 2017).
Or in other words: you can be quite happy if you’ve been using CCleaner on a personal computer from a residential connection. The security breach of over 700k installed systems was bad enough, but the attackers were thankfully not interested enough in messing with your systems further, aside from the gathering of some system specific data. The several hundred government machines across the world among this list had a lucky break, considering the real target of the hack appears to be the first step in compromising corporate systems.
@Dan82 — Except that from the view-point of China/PRC (& its like-minded authoritarian allies), there is often no division between government (ruling regime), “corporate” entities, civilians — & even “country” (ie. ruling party = country, country = ruling party).
In the preliminary list of “targeted” domains released by Cisco-Talos, one of the domains — in fact, the very 1st one at the top of the list — stood out starkly for its infamy: singtel.corp.root
While all the other currently-known targeted domains appear to be independent commercial entities, Singtel (aka SingNet) is the largest national Internet Service Provider that happens to be very incestuously-linked to the host country’s one-party ruling government.
So who knows … perhaps, “target” or “victim” may not always imply that, but sometimes “collaborator” or “accessory” instead ?
Background:
All the large so-called “commercial” or “corporatized” entities in Singtel’s host country — including all the newspapers, TV stations, national ISPs, major banks, etc. — are majority-owned & controlled by the ruling government, which also traditionally has very close ties with China. In fact, numerous Chinese nationals both in China & within Singtel’s host country refer to the latter as “Greater China” & “Pore County of China”.
Furthermore, $timezone = ‘PRC’ as shown in the log is also exactly the same time zone for Singtel’s host country, although the threat actor involved might have deliberately styled it as such to be a synonymous but still-indicative red herring.
More crucially, back in 1999, Singtel-SingNet (80% owned by the rulling government) was caught red-handed using nefarious tools like NetBus & Back Orifice to repeatedly “scan” the home PCs of more than 200,000 people. Its official excuse was that it was helping the host government’s Ministry of Home Affairs to “scan” civilians’ home PCs to check for malware. This wasn’t the 1st incident either — in 1994, another government-owned ISP “scanned” 80,000 PCs without the owners’ knowledge or consent, on the pretext of checking for porn.
Refs:
Cyber-Crime: The Challenge in Asia (HK University Press – May 2005):
[https://books.google.com/books?id=6V7QAQAAQBAJ&pg=PA338&dq=singnet+scanning]
Transparency & Authoritarian Rule in Southeast Asia (Routledge – 2004):
[https://books.google.com/books?id=BnZ_AgAAQBAJ&pg=PT167&dq=singnet+scanning]
[http://edition.cnn.com/TECH/computing/9905/06/ispscan.idg]
[http://www.mondaq.com/x/6859/Ecommerce/SingNet+scanning+computers]
Today, infamous tools like NetBus & Back Orifice are categorized as backdoor trojans that hackers utilize to remotely take over PCs. inject malicious code, record keystrokes, etc. Doesn’t this particular piece of history smell fishy-familiar — esp. in light of recent backdoor incursions by the compromised version(s) of CCleaner ?
And coincidentally (or not), a local resident in Singtel’s host country innocently wrote to the government-controlled national newspaper about his recent (unusual) experience with CCleaner. His letter was published on 20 Sep 2017, before Cisco-Talos & Avast revealed their findings about the 2nd-stage malware payload:
[http://www.straitstimes.com/forum/letters-in-print/keep-even-legal-software-to-a-minimum]
Excerpt:
“Recently, I installed CCleaner — a legitimate free software — in to a new laptop. I had been using an older version of CCleaner for years without any problem but after my recent update, I sensed that my computer was slower and I promptly uninstalled it. Yesterday, it was reported that hackers had successfully breached CCleaner’s security to inject malware into the software.”
Talking about red herrings & neon-lit “victim” fishes …
Recent news (21 Sep 2017) about the increasing spread of the stealthy FinFisher/ FinFly ISP&USB/ FinSpy surveillance-cum-hacking trojan whose primary propagators are government-owned ISPs:
[http://www.zdnet.com/article/isp-involvement-suspected-in-latest-finfisher-govt-spyware-campaign]
[https://www.welivesecurity.com/2017/09/21/new-finfisher-surveillance-campaigns]
[http://thehackernews.com/2017/09/gamma-finfisher-hacking-tool.html]
The ISPs concerned invisibly redirect legitimate download links at developers’ websites for popular software such as web browsers, VLC video player, Skype messenging app, etc. to equivalent software packages pre-poisoned with FinSpy by the ISPs. It wouldn’t be far-fetched that some of these ISPs might see CCleaner as a potential future “messenger” to deliver FinSpy to shoals of end-users, who may then point fingers at CCleaner for the fishy infection.
Incidentally, CCleaner’s recent Floxif trojan’s top-listed target “victim” (ISP Singtel)’s host government is a bulk customer of this FinSpy trojan suite via an intermediary IT company with 5 employees: [https://www.techinasia.com/wikileaks-singapore-firm-government-ties-bought-cyber-snooping-software]
@ Cigologic : Thanks for the clarification, your references were an interesting read and I wasn’t aware of much of that previously. That being said, I wonder if this too, could not have been a red herring to obscure the real source of the hack. I mean, with the hindsight of knowledge you’ve provided, it would look kind of obvious to see that SingTel domain listed at the very top.
Does anyone know if the process of installing ccleaner alone was enough to execute the malicious payload or would the 32bit executable of ccleaner.exe itself have to have be executed post-installation?
Is the process of installing ccleaner alone enough to execute the malicious payload or would the 32bit executable of ccleaner.exe itself have to be executed post-installation?
@A different Martin
Webroot, which I had liked but had to uninstall because of a new EULA, with more than one year of my 2 year subscription unused.. After some searching I found a EULA that I could live with. It was Emsisoft.
Is the process of installing ccleaner alone enough to execute the malicious payload or would the 32bit executable of ccleaner.exe itself have to be executed post-installation?
CCleaner has built up a lot of good will over the years, I am not going to ditch them this easily. This slip up is not as
bad as my last antivirus program (paid) which was selling my browsing info and installed programs list to third parties.
I did ditch them.
Just between you and me, was it AVG? If so, no worries! They were acquired by Avast!
A friend of mine recently compared the free AV code between AVG and Avast and found them exactly the same. Since I did not personally see the result, I can’t answer questions about that, but I regard him as highly competent.
I totally agree that you still can trust CCleaner because:
* They informed us and fixed as asap.
* Everyone can (theoretically) compromised exactly the same way. The attackers here not wanted to reach the little guy, they wanted more the big ones like Intel,…
* As long they tell us how to remove the malware, it shows they really care. Otherwise why would they show us?
* The digital certificate was already changed since .35
* BlechBit isn’t an alternative at all, as I explained in the other CCleaner Ghacks news.
* Avast is not even and other AV’s which not immediately detected it, because new things always takes some times, until there the corresponding checksum updates
* 64bit version was not affected
* They informed us and fixed as asap.
A whole month later is not what i’d called asap
* As long they tell us how to remove the malware, it shows they really care. Otherwise why would they show us?
They don’t want to lose customers and destroy their reputation further perhaps?
* BlechBit isn’t an alternative at all, as I explained in the other CCleaner Ghacks news.
BB is a good alternative perhaps not as polished or feature full as CC but it gets improved on each new version.
* 64bit version was not affected
Wrong again 64bit were infected aswell, read the updated info.
TYPO: GeeSetup_x86.dl should read GeeSetup_x86.dll (with two ls at the end).
Also, all hashes are SHA265, right?
Finally, I don’t understand what “DLL in registry” and “Stage 2 Payload” refer to. What files am I supposed to hash for those?
Avast says :
“For consumers, we stand by the recommendation to upgrade CCleaner to the latest version (now 5.35, after we have revoked the signing certificate used to sign the impacted version 5.33) and use a quality antivirus product, such as Avast Antivirus.”
https://blog.avast.com/progress-on-ccleaner-investigation
Interesting this is on Avast’s blog, not on Piriform’s, which has not updated its security alert.
https://www.piriform.com/news/release-announcements/2017/9/18/security-notification-for-ccleaner-v5336162-and-ccleaner-cloud-v1073191-for-32-bit-windows-users
Switch to BleachBit. It’s open source unlike CCleaner.
The attempt to go after intellectual property does point the finger at a state actor. The time zone indicates that it is China, but it could also be Russia or North Korea. We know that their intelligent services have hackers that spy as well as commit criminal acts and they also pay outsiders to hack for them. Using a product like Ccleaner is indeed a clever use of a trojan horse and I bet these hackers considered more than one product (that has as much access as a system cleaner) to carry out their intentions. THIS ONE got rolled inside our so-called fortress, but was ‘somewhat’ thwarted.
As my system was infected, I followed the update route, but today I have chosen Cisco’s original advise – restore to an image backup created before August 2017. No point trying to sword fight the invaders when I have the ability to annihilate them with a click. It will cost me, but it is only a month and a half of activity that needs to be redone.
On the previous thread, I mentioned Russia using a similar method to infect computers through an Ukrainian accounting package. It seems this attack is coming from China espionage services.
My PC runs on Win10 (Desktop PC).GData AV found the Trojan attached to Ccleaner during its routine operation (no extra scan was required) and could clean it easily. The Emsisoft AV installed on the same PC did not notice anything on the system. This was three days ago.
After that event I uninstalled CCleaner and all past downloaded versions . My desire to deal with a company Avast is very limited !
I am using ‘Glary utilities’ as replacement for CC very successfully.
I had a panic attack because I do have WbemPerf in registry exactly like the picture in your article.
Is it ok if it is empty?
It’s. I did a clean install this week, no CCleaner installed at all and I do have the empty WbemPerf entry.
thanks for the confirmation. that picture in the article is misleading…
Found WbemPerf. It’s set to default and states “value not set”. Nothing else in there.
Am I supposed to leave it like that or delete the key ?
Leave it as it is, that’s the nominal value, no problem.
Good question. I’m wondering if I can delete that empty key too, without breaking something.
This whole issue has made me wonder why CCleaner at all publishes regular updates through an .exe installer. Wouldn’t it be enough to update non-binary lists of files and hashes to detect and clean, similar to how adblockers update their blocklists?
quite true..they should have done this .. thye were sitting on a security issue all the time…. plus hosting it on filehippo what if filehippo gets hacked… USERS BEWARE
For the next months, I will kick the ccleanersetup.exe through VirusTotal before I install the program.
I always use CCleaner on Windows and I update it every darned time, I am certain I have the 5.33 on one of my laptops with 32-Bit Windows 7. And now because of THIS I am encouraged to reinstall Windows or use system restore? No thanks. I had thought about putting Solus on that laptop for some time now, so this is the final straw in Windows world. Thanks for making the decision for me Piriform and Redmond!
PS: Yes I know Solus is 64-bit, my laptop processor can handle it.
Wow.. I have been using CCleaner since 2004.Time to say goodbye?
You can also stay with an older version for a while. The code is potentially compromised in several places, the differential between recent and older versions must receive a full audit IMO.
If I was a CCleaner user, I would stay on some older unaffected version instead of updating to latest.
I agree with you and I am doing the same…..But I wonder about V5.35 with the new changed cert.
Will the old versions with the same cert. as the comp. version be in trouble?
I did a computer Image Restore back to version 5.32.
Does anyone trust CCleaner anymore? Or Piriform for that matter? I certainly don’t!
Trust is a big word. I won’t stop using CCleaner given the circumstances. Many sites have been, are targeted by attacks, it’s not a deliberate Avast/Piriform decision which would have led to these consequences, but one of those filthy Web attacks we are unfortunately facing more and more often. What can be, what is always proclaimed is that the company is responsible even if not guilty and should have infrastructures blocking the attack vectors. Sometimes there is a true, obvious lack in attacked companies’ security, sometimes the lack is as thin as a feather and finally : there is no 100% guaranty. I don’t know what happened exactly, I just know the problem was acknowledged and fixed, at least I hope. Now, should further attacks be victorious over CCleaner, again and again, I’d start wondering about Piriform’s competence, but until then I use and will continue running this little gem called CCleaner, along with several other applications from the same company.
I do feel sorry that Piriform was sold, I feel even worse when the buyer is Avast (forget a trial this is personal feeling free of documented accusations). What I can say is that experience showed and shows that several, many application development companies, once bought, deliver less good code.
@ A different Martin
Yes, and those concerns are justified, as opposed to other concerns voiced here on the lines of :
1. C-Cleaner has been compromised once, so it can’t be trusted anymore.
This is wrong, because as far as we can figure right now, this was a worldwide, sophisticated and targeted operation mounted by Chinese cyber-war spooks, in order to, at least, steal secrets from major tech corporations, banks and governments. Very few organisations can boast of being totally out of reach of such a high-level operation, and possibly none. You can’t blame someone because he has just been hit by a nuclear bomb, unprovoked. This will probably happen again. Including to open source software, which is not the silver bullet some people pretend it is.
If you think you need to ditch C-Cleaner because of that, then you need to ditch your computer as well. (OK, maybe just the Internet.)
2. I knew it, knew it, I knew it : Avast is evil, it buys out Piriform, and now see what happens.
This is wrong, because as I explained, it’s possible Piriform is better protected against such attacks by being part of Avast, than by staying independent. What we know is the infection probably occurred before Piriform was acquired by Avast. At worst, it might have happened roughly at the same time, which means Piriform was operating under their own rules and habits, not Avast’s.
@Clairvaux:
For people who had reservations about Avast’s acquisition of Piriform, I got the impression that the biggest concerns were (1) reduced respect for user privacy and (2) more aggressive efforts to monetize Piriform’s free products.
In fact, Avast says that as a result of the compromise, they integrated the Piriform team in their own computer network. The assumption there is that Piriform let themselves be attacked because they were too small to erect powerful defenses, were not concerned enough by threats to envision such a scenario, or both.
Whatever one may think of Avast products, this is an entirely likely explanation. The onus is on C-Cleaner haters (I’m using the term in jest) to prove Piriform is less secure after the acquisition than before. One way to do this would be to point to an instance when Avast installers were compromised by third-party malware. I’m not aware of any.
I want to agree with you, but the fact that the infected version was available on their website for almost a month, is a turn off for me.
I will never install CCleaner on my systems and will instead use built in Windows/browser cleanup functions.
@ Sir Pixelot
If you have checked that the registry entries and the DLL are not there.
This was a very sophisticated, targetted attack. It had specific targets. There have been many similar attacks in the last few months on other software companies.
Read this blog:
https://www.bleepingcomputer.com/news/security/ccleaner-hack-carried-out-in-order-to-target-big-tech-companies/
After doing that, read some other security blogs on the same site.
https://www.bleepingcomputer.com/
For example, read about Safebrowse the Chrome extension.
For now trust is gone down < 72%, but is question for the next days possible see third discovery.
I only use the portable versions of CCCleaner so there should not be anything in registry keys. And there is nothing under the keys you list. Hooray!
I think using a portable version of CCleaner is good because you will avoid the dangers of an installer (sometimes they try to install Chrome or much worse), but it does not create a virtual environment, and it writes to the registry as well. I noticed that even with little apps I wrote myself without intending to modify the registry.
I also only use the portable versions, but while using that version at my firm it got flagged (via file signature I suppose). I would be wary of it at best.
The portable 32 bits CCleaner.exe file of version 5.33 was infected.
Then I guess it was good that I never executed the program.
Actually I had the 64 bit version installed and Windows Defender identified it as malware (trojan).
Found WbemPerf in registry but its empty so good news I guess.
Am searching windows folder now. Changed file explorer options to “Always search file names and contents” which slows this down a bit.
Me to. Empty WbemPerf key in HKLM\Software\Microsoft\Windows NT\CurrentVersion\ on Windows 10 Creators Update 64 bit. Guess I’m safe.
+1
I think it’s normal to have an empty WbemPerf in the registry. Correct me if I’m mistaken, please.
Yes it’s normal.
A month from now this would be no issue at all as I like starting fresh but the fall creators update wont be released til what the 17th?