Windows 10 Dominator: another privacy tool
Windows 10 Dominator is another entry in the ever growing list of privacy applications for Microsoft's Windows 10 operating system.
Privacy tools serve two purposes: make it easier to modify settings to improve privacy, and make available settings that are not that easy to change.
The first reason is pretty much self-explanatory, the second may require some explanation. Microsoft added a subset of available settings that control privacy related functionality on Windows 10 in the Settings application and during setup.
You need to enable policies or manipulate Registry values if you want access to additional preferences.
Windows 10 Dominator

Windows 10 Dominator is compatible with Windows 10. It is offered as a single executable file that you can run from any location without installation.
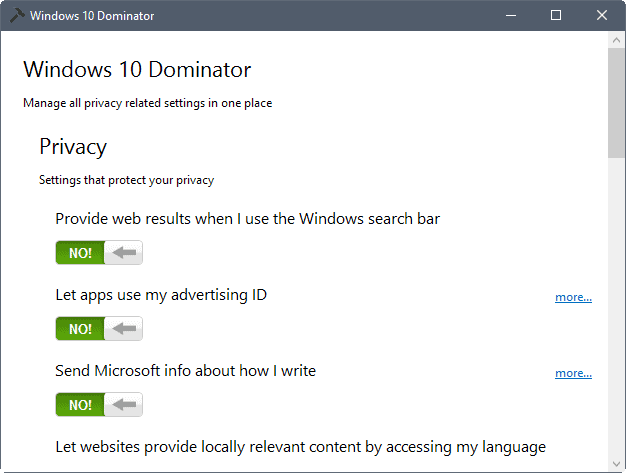
The application lists all available tweaks and settings on a single page in its interface. You need to scroll quite a bit thanks to the relatively large font that the application uses, lots of whitespace, and the number of tweaks it comes with.
Tweaks are divided into the three groups Privacy, Annoyances and Optional Protections. The first group is the largest, the two other groups are much smaller.
The program checks the status of each option and displays yes/no sliders for each preference so that you can toggle them with a click.
The following options are included in the latest version of Windows 10 Dominator:
- Provide web results when I use the Windows search bar.
- Let apps use my advertising ID.
- Send Microsoft info about how I write.
- Let websites provide locally relevant content by accessing my language list.
- Send data about functionality issues to Microsoft (Diagnostic Tracking Service).
- Ask for feedback.
- Log keystrokes (WAP Push Message Routing Service).
- Collect Telemetry data.
- Allow this PC to connect to Microsoft telemetry servers.
- Allow apps and services to request your location.
- Show Skype home and advertisements.
- Get updates from or send updates to other PCs.
- Turn on SmartScreen filter to check web content (URLs) that Windows Store apps use.
Simply flip a switch to activate or deactivate a tweak in the application. It is recommended that you create a backup or system restore point before you make changes using the application. Also note that it has last been updated in 2016. While its tweaks work fine as far as I can tell, there is a chance that things may break in the future when new Windows versions are released.
Closing Words
Windows Dominator is a light program for Windows to make changes to privacy related Windows 10 settings. It appears to have been abandoned by its author, and includes less options than other privacy programs for Windows 10.



























The inability to easy block ALL telemetry and data sending to MS and third-parties is the reason I don’t use W10.
The only way to easy block ALL telemetry is if someone develops open source program that will block internet connection to everything by default and only allow internet to user selected programs, example: firefox. A whitelist program as opposed to blacklist program which relies on ip lists. Whitelist wont have rely on any list.
Would be great to see an updated comparison of the best of these W10 privacy tools in detail.
In addition, do any of these tools actually block all the surreptitious MS calling home traffic, verified by a wireshark scan or the like? Given the vast amount of data MS have recently fessed up to taking, these tools seem a bit lightweight.
I use ShutUp10 and WPD which seem to cover most things
TinyWall isn’t under active development and should’t be used anymore besides it’s hard to install because the certificate is blocked.
This is just another useless tool, which also should’t be recommend or used. All the tools I know does nothing but changing registry related settings. Instead of messing with registry I would love to see a tool which imports the gpedit.msc related settings, because even if there entries are obsolete you can update the result asap and see if it works or not (use the /force param to update gpedit). On registry side you not know until you restarted and then you might see something or not it’s not that optimal compared to gpedit.
I managed to get a fair bit of privacy by selecting just one “NO!” setting. It was to the Get Windows 10 app.
Great comment, Norm ! :)
By telling us NO!, the switch box in the screenshot is very clear on what is chosen. This is much better that similar tools I’ve seen here. For some reason they all seem very vague at conveying what is actually enabled or not.
Does TinyWall block those telemetry connections, tracking services… by default?
I don’t know since I have replaced it with an awesome open source alternative called simplewall (https://github.com/henrypp/simplewall/releases) which does telemetry blocking nearly out of the box : just check “Enable blocklist” in Settings -> Filters
Added to my to try list. Thanks.