You should disable automatic downloads in Chrome right now
Google Chrome users on Windows are advised to disable automatic downloads in the web browser to protect authentication data against a new threat discovered recently.
The Chrome browser is the most popular browser right now on desktop devices. It is configured to download safe files automatically to the user system without prompt by default.
Any file that Chrome users download that passes Google's safe browsing checks will land in the default download directory automatically. Chrome users who want to pick the download folder instead for downloads need to change that behavior in the options.
The new attack, described in detail on the Defense Code website, combines Chrome's automatic download behavior with Windows Explorer Shell Command File files that have the .scf file extension.
The aging format is a plain text file that includes instructions, usually an icon location and limited commands. What's particularly interesting about the format is that it may load resources from a remote server.
Even more problematic is the fact that Windows will process these files as soon as you open the directory they are stored in, and that these files appear without extension in Windows Explorer regardless of settings. This means that attackers could easily hide the file behind a disguised filename such as image.jpg.
The attackers use a SMB server location for the icon. What happens then is that the server requests authentication, and that the system will provide that. While password hashes are submitted, the researchers note that cracking those passwords should not take decades anymore unless they are of the complex kind.
Regarding password cracking feasibility, this improved greatly in the past few years with GPU-based cracking. NetNTLMv2 hashcat benchmark for a single Nvidia GTX 1080 card is around 1600 MH/s. That's 1.6 billion hashes per second. For an 8-character password, GPU rigs of 4 such cards can go through an entire keyspace of upper/lower alphanumeric + most commonly used special characters (!@#$%&) in less than a day. With hundreds of millions leaked passwords resulted from several breaches in the past years (LinkedIn, Myspace), wordlist rule-based cracking can produce surprising results against complex passwords with more entropy.
The situation is even worse for users on Windows 8 or 10 machines who authenticate with a Microsoft account, as the account will provide the attacker with access to online services such as Outlook, OneDrive, or Office365 if used by the user. There is also the chance that the password is reused on non-Microsoft sites.
Antivirus solutions are not flagging these files right now.
Here is how the attack goes down
- User visits a website which either pushes a drive by download to the user system, or gets the user to click on a specially prepared SCF file so that it gets downloaded.
- User opens the default download directory.
- Windows checks the icon location, and sends authentication data to the SMB server in hashed format.
- Attacks may use password lists or brute force attacks to crack the password.
How to protect your system against this attack
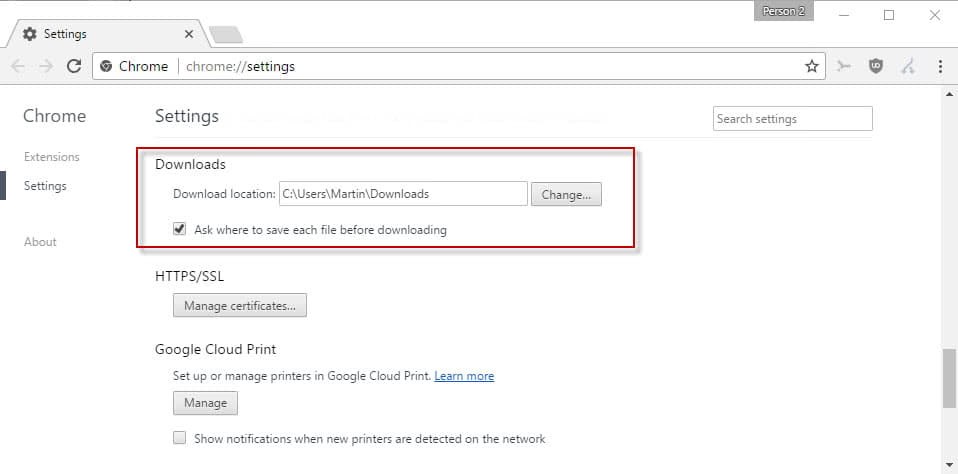
One option that Chrome users have is to disable automatic downloads in the web browser. This prevents drive by downloads, and may also prevent accidental downloads of files.
- Load chrome://settings/ in the browser's address bar.
- Scroll down and click on the "show advanced settings" link.
- Scroll down to the Downloads section.
- Check the preference "Ask where to save each file before downloading".
Chrome will prompt you for a download location each time a download is initiated in the browser.
Caveats
While you add a layer of protection to Chrome's handling of downloads, manipulated SCF files may land in different ways on target systems.
One option that users and administrators have is to block ports used by SMB traffic in the firewall. Microsoft has a guide up that you may use for that. The company suggests to block communication from and to the Internet to the SMB ports 137, 138, 139 and 445.
Blocking these ports may affect other Windows services however such as the Fax service, print spooler, net logon, or file and print sharing.
Now You: How do you protect your machines against SMB / SCF threats?
Thank you for the information , don’t need to get hatched
This is great information thanks
Get rid of Crome
Is there a solution to deploy this across company? I mean, enable the check box via registry or GPO.
TCP/UDP 137, 138, 139 and 445 ports are blocked for years on my Windows PCs.
Anyone is doing this via GPO/regedit? Can’t find anything which does that in chrome.
Removing the extension seems to be a good idea too, a registry change should be sufficient to update all windows client.
I updated the registry and changed HKEY_CLASSES_ROOT\SHCmdFile\shell\open\command from %SystemRoot%\explorer.exe to %SystemRoot%\explorer-DISABLED.exe via GPO (https://technet.microsoft.com/en-us/library/cc753092(v=ws.11).aspx) or you can delete the whole HKEY_CLASSES_ROOT\SHCmdFile tree if you prefer, using the same technique.
Here is a solution to all security issues.
Get rid of all forms of technology and move into a log cabin in a remote area without running water, roads or hydro.
For serious work, will drones replace carrier pigeons?
+1 to that!
Another good reason to use linux .
Windows 10 users aren’t affected by SMB holes cause it’s patched + there is Windows Defender which also already got the database signatures immediately. For older OS users you can disable it via registry:
Windows Registry Editor Version 5.00
; https://support.microsoft.com/en-us/help/2696547/how-to-enable-and-disable-smbv1,-smbv2,-and-smbv3-in-windows-vista,-windows-server-2008,-windows-7,-windows-server-2008-r2,-windows-8,-and-windows-server-2012
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters]
“SMB1″=dword:00000000
“SMB2″=dword:00000000
The thing is that disabling every single service is a no go, because in sever environment this isn’t a ‘solution’ because you depending on such services and that’s the real issue not the single user targets.
Export the following key from the registry, then delete it:
HKEY_CLASSES_ROOT\SHCmdFile
Easy peasy
I did exactly the same thing and was going to post it on here, but you beat me to it, awesome.. Now windows doesn’t recognise the extension and can’t run it with user intervention asking what to open it with.
I set blank value for .scf extension (removed FIle Explorer). It’s better option.
How
Or with FileTypesMan. You find .sfc extension and remove associated program.
Remove the following node from the registry.
HKEY_CLASSES_ROOT\SHCmdFile
Export the key first, of course.
I always wondered when there would start to be attacks through Chrome. Everyone stopped use IE because it was so much targeted, being the world’s most used browser. But now Chrome has taken the crown I wondered when it would start on them, as hackers don’t care who they hit, as long as they get the most people.
“…against a new thread…” Martin, I think you most likely meant “threat.” :)
Good luck; seems any browser I set to not update automatically updates automatically. Except for Cyberfox. Google is the worst. It’s running in the background even if I turn off the Google Update Service. The silly service simply creates a new
Service entry to run as it will. Firefox–let’s not go there.
It is the file download dialogue, not the automatic update. With the automatic update you would get the patch in a few days, but you disabled it…
Google is also working on a fix for Chrome, so that should be coming out shortly, so non-advanced users who are not familiar with settings in the firewall, and think they may make matters worse by changing settings, and can really only disable the automatic downloads, should be safe(r) soon enough.
Which password would a Windows 7 system send? The log on password to authentificate into Windows? I wouldn’t worry too much about that (personally I don’t even have one). Also I wonder what would happen if you disable the “show thumbnails” option under appearance and performance. I know it stops looking for icons on exe files, judjing by the activity led.
Anyway, that setting is something I always do on all browsers, I’d hate my browser to initiate a download without asking me first.
Martin,
Where you mentioned the most commonly used special characters (!@#$%&) does those include the open/closed brackets?
As regards SMB, I’ve disabled “SMB 1.O/CIFS File Sharing Support” in the “Turn Windows features Off and On” menu in Windows 8.1
I also have the premium version of Malwarebytes 3.1.2 installed and only use Firefox.
In addition, I log into the OS with a local account.
Hi, no it does not. Those enclose the characters only.
OK, thanks.
But I’ll avoid using the most often used characters when compiling passwords in future so thanks for the tip regarding that aspect.
already disabled windows SMB feature + blocked all related ports,
actually i want chrome to save image without save as dialog :(