Detect and Mitigate Intel AMT vulnerability
A recently disclosed vulnerability in Intel products using Intel Active Management Technology, Intel Small Business Technology, and Intel Standard Manageability gives attackers remote access to the manageability features supported by these products.
First the good news: the vulnerability does not affect (most) consumer PCs with Intel consumer firmware.
These technologies have been created by Intel for remote management of computer systems. Functionality may include monitoring, upgrading, repairing and maintaining compatible devices.
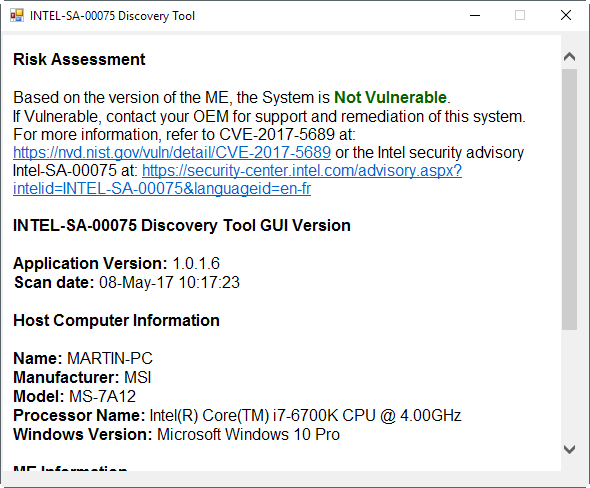
While you may use Intel's own advisory to find out if a computer system is vulnerable, it is easier to use the detection tool the company created and published for that instead.
You can download the tool from Intel's website, and may run it on all Windows versions starting with Windows 7. The program is portable, and it will tell you right away whether your system is vulnerable or not.
Note: Intel has published a guide to manually find out whether a system is vulnerable or not.
If the computer is not vulnerable, then you are done as there is nothing else to do. If the system is vulnerable however, you have one or two options depending on whether the manufacturer of the device has published an updated firmware already.
- First option is to check whether updated firmware has been released. If that is the case, update the firmware to plug the security vulnerability. You find the list of firmware updates on Intel's advisory page.
- If no firmware is available, you may use the third-party tool Disable Intel AMT, or one of Intel's suggested options described in the mitigation guide.
Disable Intel AMT is a basic batch file for Windows that renames the LMS.exe (Intel Local Management Service) binary so that it won't run anymore.
Intel's own solution requires multiple steps to complete. First, the unprovisioning of any provisioned system, then the disabling or deleting of the LMS service, and optionally configuring local manageability configuration restrictions.
Unconfiguring a system in CCM: ACUConfig.exe UnConfigure
Unconfiguring a system in ACM without RCS integration: ACUConfig.exe UnConfigure /AdminPassword <password> /Full
Unconfiguring a system with RCS integration: ACUConfig.exe UnConfigure /RCSaddress <RCSaddress> /Full
Intel published an unprovisioning tool which administrators may used if the above commands cannot be executed.
System administrators may also disable or remove LMS in the following way:
- Tap on the Windows-key, type cmd.exe, hold down the Shift-key and the Ctrl-key, and hit the Enter-key. This opens an elevated command prompt.
- To disable LMS: sc config LMS start= disabled
- To delete LMS: sc delete LMS
The vulnerability
If AMT is enabled, users may sign in locally or remotely. Intel uses HTTP Digest authentication for that, and anything that a user enters is computed to a hash and then authenticated by the interface.
The researchers discovered that the verification process that Intel implemented is flawed, as it accepts partial hashes or even an empty string. All an attacker requires therefore is knowledge of a working user account to sign in without knowing the correct password. (via Born)



















Thanks a lot !
Besides the vulnerable Intel AMT which is mainly for Remote Management, Intel ME(Management Engine) has the Intel Anti Theft technology for Remote Locking and Data Wipe which may be vulnerable also. Please see …….
http(semi colon)//www(dot)eweek(dot)com/security/intel-arms-lenovo-thinkpad-laptops-with-new-anti-theft-technology
(circa 2008)
Some people have conjectured that the Intel ME (and M$ Win 10) is an NSA backdoor spyware.
@AnorKnee Merce, you know you can post full URLs without changing : and . to words right?
Also seeing as the secret 3g Intel chip article you link to leads back to that whack job Alex Jones from Info Wars who admits everything he posts and talks about is just him “Playing a Character” and that “He is a performance artist”, seeing as (afaik) your claim of an NSA backdoor spyware built into Intel chip is based on what a confirmed conspiracy theorists has said you’ll have to forgive me for saying your claim lacks creditability.
Intel Anti Theft technology is already discontinued by Intel after their servers was hacked some time ago, it is no longer in use.
@ ecfx
Yes, the web-based subscription Anti-Theft Service has been discontinued by Intel but the Intel Anti Theft hardware/chipset feature is still present in Intel ME. Eg …….
http(semi colon)//www(dot)game-debate(dot)com/cpu/index.php?pid=2454&pid2=208&compare=core-i5-7400-3-0ghz-vs-core-i7-920-quad-2-67ghz
Also, …
https(semi colon)//www(dot)prisonplanet(dot)com/secret-3g-intel-chip-gives-snoops-backdoor-pc-access.html
(circa 2013)
For Linux, scan from another computer in LAN, scan will not work for your own host because you probably don’t have LMS driver.
nmap -p16992,16993,16994,16995,623,664 192.168.xxx.xxx
response can be something like this:
PORT STATE SERVICE
623/tcp closed oob-ws-http
664/tcp open secure-aux-bus
16992/tcp open amt-soap-http
16993/tcp open amt-soap-https
16994/tcp closed unknown
16995/tcp open unknown
then you can probe the open ports to see the IAMT version like this:
curl -sS http://192.168.xxx.xxx:16992 -i
and you will get something like this:
HTTP/1.1 303 See Other
Location: /logon.htm
Content-Length: 0
Server: Intel(R) Active Management Technology 10.0.38
that it is vulnerable.
Until a new BIOS upgrade – if you are lucky to get a new BIOS – you can mitigate by renaming default admin account to something random. Uninstall LMS drivers in windows. This vulnerability will not allow escalation of account rights only login to a know account name.
For more info about this mitigation check this:
https://forum.pfsense.org/index.php?topic=130046.msg716548
and this
https://forums.lenovo.com/t5/forums/v3_1/forumtopicpage/board-id/Security_Malware/thread-id/2678/page/3
L.
Can you give full ATM’s CPUs list?
Technically it’s any CPU that uses vPro, it’s best if you check specific CPUs due to vPro as the list would be took long due to it being included in CPUs since 2008.
Having said that it’s very unlikely that even if you did have a CPU that supported vPro that your average consumer would be effected by this, not only because vPro is mainly used in workstation CPUs (Xenon and some mobile CPUs) but also because you’d have to meet the following requirements.
1) A supported CPU
2) A supported chipset
3) Supported network hardware
4) The ME firmware to contain the AMT firmware
The following link gives a fairly well balanced overview of vulnerability.
https://mjg59.dreamwidth.org/48429.html
Any problems on a Linux server?
For linux: scan for IAMT open ports from another computer in lan.
nmap -p16992,16993,16994,16995,623,664 192.168.xxx.xxx
you will get something like this if IAMT working it is found:
PORT STATE SERVICE
623/tcp closed oob-ws-http
664/tcp open secure-aux-bus
16992/tcp open amt-soap-http
16993/tcp open amt-soap-https
16994/tcp closed unknown
16995/tcp open unknown
then:
curl -sS http://192.168.xxx.xxx:16992 -i
to check IAMT version and you will receive something like this:
HTTP/1.1 303 See Other
Location: /logon.htm
Content-Length: 0
Server: Intel(R) Active Management Technology 10.0.38
This is vulnerable but can be mitigate by changing default admin name account to something random so attacker will not know the admin account name to exploit it.
@corky @ecfx, thanks!
ATM is operating system agnostic: https://software.intel.com/en-us/Working%20with%20Intel%20AMT%20and%20Linux
@Shiro, https://github.com/CerberusSecurity/CVE-2017-5689
So, how do you test and fix it on Linux? The description and tool above is for Win only I believe, does anyone with Linux expertise know?
I ran the command “sc config LMS start=disabled” on my Thinkpad and it did not work. A warning indicated there must be a space between the equal sign and the value. The command should be “sc config LMS start= disabled”. After reentering the command with that space; success.
Mike, thank you very much. A space is required between an option and its value, as indicated here on Technet (https://technet.microsoft.com/en-us/library/cc990290%28v=ws.11%29.aspx?f=255&MSPPError=-2147217396#BKMK_examples) I have corrected the command.
I used the manual guide and found “Intel Management & Security Application Local Management Service” running in
Services, and then downloaded the INTEL-SA-00075 Discovery Tool and ran it. The tool showed “Not Vulnerable”.
So… maybe I don’t have this vulnerability. Great info as always Martin, thanks.