Microsoft Security Bulletins November 2016
Yes, it is this time of the month again. Microsoft just released updates for all client and server versions of Windows and other company products.
Our Microsoft Security Bulletins November 2016 provides you with information so that you can prioritize updates for deployment, or find out what they do before installing them.
The overview begins with an executive summary that highlights the most important bits of information. It is followed by the operating system and other Microsoft product distribution that lists products and the number of security updates and their severity.
This is followed by the list of security bulletins, security advisories and updates, and non-security updates released in the past 30 days.
The last part details how to download these updates. It offers direct update download links that point to Microsoft's Update Catalog, and reference links that you can load for additional information and research.
Microsoft Security Bulletins November 2016
Executive Summary
- Microsoft released 14 security bulletins on the November 2016 Patch Day.
- 6 of the bulletins are rated with a severity rating of critical, the remaining 8 with a rating of important.
- All client and server versions of Windows are affected by at least one critically rated bulletin.
- Microsoft published updates for Microsoft Edge, Microsoft SQL Server, Office and other Microsoft products as well.
Operating System Distribution
Windows 8.1 and 10 are affected by more vulnerabilities than Windows 7 and Vista on the client side. This is explained by the security update for Adobe Flash MS16-141 which is released for Windows 8.1 and 10 only, and MS16-129, the cumulative security update for Microsoft Edge.
The new Windows Server 2016 is affected by MS16-130 and Ms16-131 critically, while previous versions of Windows Server are either not affected at all, or only with important severity.
- Windows Vista: 2 critical, 6 important
- Windows 7: 2 critical, 6 important
- Windows 8.1: 3 critical, 7 important
- Windows RT 8.1: 1 critical, 7 important
- Windows 10: 4 critical, 7 important
- Windows Server 2008: 1 critical, 6 important
- Windows Server 2008 R2: 1 critical, 6 important
- Windows Server 2012 and 2012 R2: 6 important, 2 moderate
- Windows Server 2016: 2 critical, 5 important
- Server core: 8 important
Other Microsoft Products
- Microsoft Office 2007, 2010, 2013 and 2016: 1 important
- Microsoft Office 2013 RT: 1 important
- Microsoft Office 2011, 2016 for Mac: 1 important
- Microsoft Office Compatibility Pack Service Pack 3: 1 important
- Microsoft Excel Viewer: 1 important
- Microsoft PowerPoint Viewer: 1 important
- Microsoft SharePoint Server 2010, 2013: 1 important
- Microsoft Office Web Apps 2010, 2013: 1 important
- SQL Server 2012 Service Pack 2, Service Pack 3: 1 important
- SQL Server 2014 Service Pack 1, Service Pack 2: 1 important
- SQL Server 2016: 1 important
Security Bulletins
Red = critical
MS16-129 -- Cumulative Security Update for Microsoft Edge (3199057)
This security update resolves vulnerabilities in Microsoft Edge. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Microsoft Edge.
MS16-130 -- Security Update for Microsoft Windows (3199172)
This security update resolves vulnerabilities in Microsoft Windows. The most severe of the vulnerabilities could allow remote code execution if a locally authenticated attacker runs a specially crafted application.
MS16-131 -- Security Update for Microsoft Video Control (3199151)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution when Microsoft Video Control fails to properly handle objects in memory.
MS16-132 -- Security Update for Microsoft Graphics Component (3199120)
This security update resolves vulnerabilities in Microsoft Windows. The most severe being of the vulnerabilities could allow a remote code execution vulnerability exists when the Windows Animation Manager improperly handles objects in memory if a user visits a malicious webpage.
MS16-133 -- Security Update for Microsoft Office (3199168)
This security update resolves vulnerabilities in Microsoft Office. The most severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted Microsoft Office file.
MS16-134 -- Security Update for Common Log File System Driver (3193706)
This security update resolves vulnerabilities in Microsoft Windows. The vulnerability could allow elevation of privilege when the Windows Common Log File System (CLFS) driver improperly handles objects in memory.
MS16-135 -- Security Update for Windows Kernel-Mode Drivers (3199135)
This security update resolves vulnerabilities in Microsoft Windows. The most severe of the vulnerabilities could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application that could exploit the vulnerabilities and take control of an affected system.
MS16-136 -- Security Update for SQL Server (3199641)
This security update resolves vulnerabilities in Microsoft SQL Server. The most severe vulnerabilities could allow an attacker could to gain elevated privileges that could be used to view, change, or delete data; or create new accounts.
MS16-137 -- Security Update for Windows Authentication Methods (3199173)
This security update resolves vulnerabilities in Microsoft Windows. The more severe of the vulnerabilities could allow elevation of privilege. To exploit this vulnerability, the attacker would first need to authenticate to the target, domain-joined system using valid user credentials.
MS16-138 -- Security Update to Microsoft Virtual Hard Disk Driver (3199647)
This security update resolves vulnerabilities in Microsoft Windows. The Windows Virtual Hard Disk Driver improperly handles user access to certain files. An attacker could manipulate files in locations not intended to be available to the user by exploiting this vulnerability.
MS16-139 -- Security Update for Windows Kernel (3199720)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker runs a specially crafted application to access sensitive information.
MS16-140 -- Security Update for Boot Manager (3193479)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow security feature bypass if a physically-present attacker installs an affected boot policy.
MS16-141 -- Security Update for Adobe Flash Player (3202790)
This security update resolves vulnerabilities in Adobe Flash Player when installed on all supported editions of Windows 8.1, Windows Server 2012, Windows Server 2012 R2, Windows RT 8.1, Windows 10, and Windows Server 2016.
MS16-142 -- Cumulative Security Update for Internet Explorer (3198467)
This security update resolves vulnerabilities in Internet Explorer. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer.
Security advisories and updates
KB3201860 -- MS16-128: Security Update for Adobe Flash Player for Windows 10 Version 1607, Windows 10, Windows 8.1, Windows RT 8.1, Windows Server 2012 R2, Windows 8 Embedded Standard, and Windows Server 2012
Non-security related updates
Cumulative updates not yet published on the update history pages. Will update the article as soon as that happens.
KB3197867 -- November, 2016 Security Only Quality Update for Windows 7 and Server 2008 R2
- Security updates to Microsoft Graphics Component, kernel-mode drivers, Microsoft Video Control, Common Log File System driver, Windows authentication methods, Windows operating system, Windows File Manager, Windows registry, OpenType, Internet Explorer 11, and Windows Component.
KB3197868 -- November, 2016 Security Monthly Quality Rollup for Windows 7 and Server 2008 R2
- Support page MIA. No information other than the security updates that it includes.
KB3197873 -- November, 2016 Security Only Quality Update for Windows 8.1Â and Windows Server 2012 R2
- Support page MIA. See KB3197867 above for list of updates.
KB3197874 -- November, 2016 Security Monthly Quality Rollup for Windows 8.1 and Windows Server 2012 R2
- Support page MIA. No information
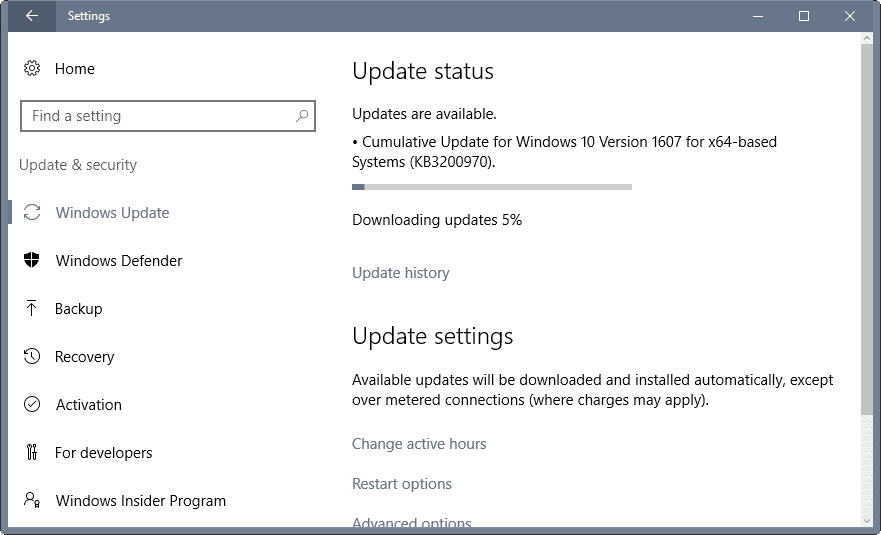
KB3200970 -- Cumulative Update for Windows 10 Version 1607 and Windows Server 2016
- Addressed issues that prevented users from connecting to virtual private networks (VPNs).
- Improved reliability of Internet Explorer, Remote Desktop and multimedia audio.
- Fixed a system tray issue in regards to WiFi connections not showing up.
- Fixed unnamed issues in various Windows components including Microsoft Edge, Internet Explorer 11, Remote Desktop, Active Directory, Windows shell, enterprise security and more.
- Security updates for a number of Windows components including Boot Manager, kernel-mode drivers, Edge, IE11, Microsoft Video Control and more (as outlined in the Security Bulletins section above).
KB3197954 -- Cumulative Update for Windows 10 Version 1607 and Windows Server 2016
- Improved reliability of many components including Windows kernel, Internet Explorer 11, Start, File Explorer, graphics.
- Fixed crash in System Center Operations Manager (SCOM).
- Fixed connectivity issues in Remote Desktop Gateway.
- Addressed updates restoration issue when doing system resets.
- Fixed an issue that caused domain logons to fail after upgrading from Windows 10 Home to Pro.
- The HTTP Strict Transport Security (HTST) preload list was updated.
- Addressed unnamed issues affecting USB, Wi-Fi, Bluetooth, Windows kernel, Microsoft Edge, Internet Explorer 11, PowerShell, and more.
Check out the support article linked above for a full rundown.
KB2976978 -- Update for Windows 8.1 -- Compatibility update for keeping Windows up-to-date in Windows 8.1 and Windows 8 -- This update performs diagnostics on the Windows systems that participate in the Windows Customer Experience Improvement Program
KB3199375 -- Update for Internet Explorer -- FIX: "Do you want to open this file" error message after you apply security update 3185319
KB3200006 -- Update for Internet Explorer -- System Center Operations Manager Management Console crashes after you install MS16-118 and MS16-126
KB3192321 -- Update for Windows 8.1, Windows Server 2012 R2, Windows Embedded 8 Standard, Windows Server 2012, Windows Embedded Standard 7, Windows 7, and Windows Server 2008 R2 -- Turkey ends DST observance
KB3192403 -- October, 2016 Preview of Monthly Quality Rollup for Windows 7 and Windows Server 2008 R2
KB3192404 -- October, 2016 Preview of Monthly Quality Rollup for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2
KB3192406 -- October, 2016 Preview of Monthly Quality Rollup for Windows Embedded 8 Standard and Windows Server 2012
KB3198591 -- Update for Windows 7 and Windows Server 2008 R2 -- Windows Server 2008 R2 domain controller crashes when two threads use the same LDAP connection
How to download and install the November 2016 security updates

Windows 7, 8.1 and 10 users get so-called monthly rollup releases. On Vista, individual patches are made available.
Windows users can download and install the patches via Windows Update:
- Tap on the Windows-key, type Windows Update and hit the Enter-key.
- If the update check is not performed automatically, click on "check for updates" on the page that opens.
- Updates that are found may be installed automatically, or displayed to the user instead for manual selection.
Updates are also made available on Microsoft's Download Center, as monthly security releases, and through the Microsoft Update Catalog.
Direct Microsoft Update Catalog download links:
Windows 10, Windows Server 2016
- KB3200970 -- Cumulative Update for Windows 10 Version 1607
- KB3197954 -- Cumulative Update for Windows 10 Version 1607
Windows 8.1, Windows Server 2012 R2
- KB3197874 -- November, 2016 Security Monthly Quality Rollup for Windows 8.1 and Server 2012 R2
- KB3197873 -- November, 2016 Security Only Quality Update
Windows 7, Windows Server 2008 R2
- KB3197868 -- November, 2016 Security Monthly Quality Rollup for Windows 7 and Server 2008 R2
- KB3197867 -- November, 2016 Security Only Quality Update
Additional resources
- Microsoft Security Bulletin Summary for November 2016
- List of software updates for Microsoft products
- List of security advisories of 2016
- Microsoft Update Catalog site
- Our in-depth update guide for Windows
- Windows 10 Update History
- Windows 8.1 Update History
- Windows 7 Update History





















Vista Users, and others having trouble with redirects.
Use a VPN, with Firefox browser and Random Agent Spoofer add-on which you can also get here
https://github.com/dillbyrne/random-agent-spoofer
A good paid for VPN is best, like Private Internet Access. Yearly subscription is very good value with most VPNs having servers around the world and simple to install apps you can run. Starting your VPN, then running Tor Browser Bundle works pretty well. A VPN can also help avoid problems with DNS, local network issues and provider DNS and get you online when other locals might not be able to. It can also bypass government internet blocks in case they decide to block internet access locally or collect meta-data on their citizens.
Encrypting DNS with something like EasyDNSCrypt, with a VPN is a little harder. You will need to read how to do it as you need to launch EasyDNSCrypt, then type “ipconfig /flushdns” into CMD that is run as Admin, start your VPN, then ipconfig /flushdns again and check that EasyDNSCrypt has set your DNS setting back to 127.0.0.1 for your network adapter and replaced your VPNs DNS settings. Your VPN app will have to be set to only use another DNS to establish it’s initial VPN connection, but some VPNs allow you to add your own DNS addresses to use.
Foxy Proxy is good for quickly adding proxy settings changing between proxy and normal browsing. If you have the Foxy Proxy using a proxy, you can enable cookies temporarily to download from sites while using proxy (setting Foxy Proxy to use cookies when proxy is active will have to be set each time, as it aytomatically disbales cookies when you switch to a proxy).
Privacy Badger, uBlock Origin, are simple and work very well. Decentraleyes add-on can reduce databases being built about your habits by google and others, and still have web function without having to be too technically proficient.
HTTPS Everywhere, NoScript Security Suite, are also really good. You may have to set “Temporarily Allow All” for legitimate sites you use often as NoScript will block some functions websites need to work. NoScript also blocks malware and many exploits so is great. Use “Temporarily Allow” with NoScript as occasionally it will stop websites you use functioning too well after a new Firefox update, but it can be disabled in Add-ons and restart Firefox if need be, and it is updated regularly and very quickly. Excellent plugin and blocks many advertisements and not too hard to learn to use, but you can always disable and restart Firefox when you can’t figure it out.
Disable WebRTC, is also a good add-on, but may need to also be disabled if some websites don’t function that you need to log into or download from. IPFlood can be used to generate random IP addresses to help from being tracked by IP.
Setting your TCP/IPv4 manually is a good idea, disabling IPv6 and Link-Layer Discovery Responder unless you need it. Also for TCP/IPv4 under Properties>Advanced>WINS you should also disable netBIOS over TCP/IP as you likely won’t use it if you don’t know what it is and it’s a vulnerability.
Lastly backup your hosts file C:\Windows\System32\drivers\etc\hosts (copy and paste it to a folder like My Documents>Original Hosts). You can give your Personal Account and Administrator account Full Control under Properties>Security, and all other accounts “Read & Access” and “Read” permissions. Then open your hosts file in notepad, paste in anything you want to add to hosts, Save As… “hosts” (with the quotes) in notepad and set to save as All Files *.* for the file type. Finally set your modified hosts file to Read Only under Properties and add it to your Exceptions list in your Antivirus or it will try to reset it all the time.
* It is better to set microsoft and other telemetry and monitoring block lists in a very good quality router that supports PROPER BLOCK LISTS, preferably compatible or already installed with DD-WRT or Tomato as that IS MUCH MORE EFFECTIVE than a microsoft windows hosts file.
Ever since these updates my Microsoft office 2010 is acting weird. I can’t open excel, no response. Also word and powerpoint takes forever to open. Any suggestions?
Microsoft -Update Catalogue ist nit availale for Vista Users. Ist redirect
http://www.catalog.update.microsoft.com/Error.aspx?id=-1914896352
How can Vista Users get manually Updates since Nov. 2016?
Fyi, after some checking, the monthly Security-Only Updates that hv to be manually installed via M$ Download Center or Update Catalog are not cumulative, whereas the monthly Patch Rollups that are automatically installed via Windows Update are cumulative. …….
httpssemicolon//blogsdottechnetdotmicrosoftdotcom/windowsitpro/2016/10/07/more-on-windows-7-and-windows-8-1-servicing-changes/
.
.
Imagine some months from now, u hv to do a clean reinstall of Win 7/8.1 with Security-Only Updates, eg the HDD became faulty. It will entail quite a lot of work, ie manually installing them ONE-BY-ONE.
It also means quite a bit of finding the right download links which may not be super easy as well.
KB3177467 is listed as an important non-security update for me. Description says it is something called a servicing stack. Is that safe to install or one of the unneeded updates better to avoid?
There seems to be a mistake with versions.
“KB3197867 — November, 2016 Security Only Quality Update for Windows 8 and Server 2008 R2”
then later on you write that that’s the update for Windows 7.
Right, thanks for letting me know. It is the W7 update.
Hi Martin,
Thanks for all the info.
I note that updates can be downloaded directly from the Microsoft Catalog site using Firefox now, so no need to use the Rss feed link as before. It behaves slightly differently than using IE11 though and clicking the Download link on http://www.catalog.update.microsoft.com/Search.aspx?q=3197873 launches a popup which contains the actual link to the file you want to download. I assume it works the same way for Google Chrome and other browsers.
good article, martin. +1
…and as always i’m very content with wsusoffline taking care of my remaining 8.1 and 2012r2 machines. :)
Maybe someone know the reason why my SCCM skipping security only updates when syncing with WSUS?
For example: Skipped update 67f7223a-468a-41e8-9217-c856c369ebad – November, 2016 Security Only Quality Update for Windows Server 2012 (KB3197876) because it was superseded. SMS_WSUS_SYNC_MANAGER 11/8/2016 8:44:53 PM 11140 (0x2B84).
Why these updates marked as superseded?
Did you by chance install the November, 2016 Security Monthly Quality Rollup before?
If not, check this support thread where admins are reporting that the November security only update is showing up as superseded already.
https://social.technet.microsoft.com/Forums/windowsserver/en-US/63976761-37c6-4198-99c2-653b33cc1ed4/security-only-quality-updates-for-november-superseded-already?forum=winserverwsus
Solution posted that may help:
Excellent article as always regarding Windows update. Not your fault Martin, I know you are making your best to educate people like me trying to update their system with only security patches, unfortunately from now on as I understand nothing I lost my trust in Microsoft and I will stop updates. Why making things complicated M§ when you can make it simple? Hackers and gangsters have bright future.
Hehehe. Martin Brinkman has proven to be Our Hero when it comes to alerting and informing us about Microsoft Mischief. While I tend to agree with the “Install gentoo” comment, there are many of us who are stuck with Windows for business reasons, although it is becoming much easy to break away these days.
If M$ were honest about their updates and the actual versus purported intention behind each of them, we wouldn’t be having this conversation. It is very sad that in a day when almost anyone who uses computers and devices that are networked is very concerned about security, Microsoft is still doing its best to make it an untrustworthy source of patches to software it sells.
Maybe, with Trump as President, DCMA can be altered to allow each of us to LEGALLY examine and modify to our hearts’ content any software, firmware, hardware that we purchase (a license for), or which is embedded in some other product we have, such as a motor vehicle. If we are expected to live with some of these modern day necessities, we should at least be able to repair them as needed with no penalty under law.
Vendors, such as M$, should have to provide at least as much information about what their products and updates for same actually do/contain, just as the FDA requires (many, not all) companies that sell medicines and foodstuffs we ingest to accurately describe what they include.
Is there any other way to download http://www.catalog.update.microsoft.com/Search.aspx?q=KB3197867? That keeps giving me an Error number: 8DDD0020. I can get the page to load for a second by hitting the stop button but the download button is non-functional even then.
Last month one could just get the update from https://www.microsoft.com/en-us/download/details.aspx?id=53990. Is that possible this month? Is there a direct link like that for KB3197867?
Thank you.
install gentoo
Yes, thanks for the excellent overview, Martin.
Just like mentioned in the list here, today Windows Update once again tried to push the KB2976978 “compatibility update” to my 8.1 system. This is the update that will flag systems that (from Microsoft’s point of view) ought to be “upgraded” to Windows 10. And for the third or fourth time, I rejected this one by “hiding” it.
Consider KB2976978 some kind of little bird: it tells us that Microsoft may very soon unleash a fresh assault against all those poor game-spoilers who still dare to hold on to Windows 7 or 8.1.
Somebody can tell me if I install the KB3192391 security only update from the october patch then i dont have to install KB 3185330 and KB 3188740? And what about the office kb3118312 update? I can install it or not?
Fyi, the Nov 2016 Win 7 Patch Rollup contains all the needed updates from May, June, July, Aug, Sep, Oct n Nov 2016, eg 133MB in size for the Nov 2016 KB3197868 Rollup.
……. So, at this rate, the April 2017 Patch Rollup for Win 7 should be about 200MB in size, ie excluding other updates for .NET framework, IE 11, etc which should add about 50MB more. The Dec 2017 Patch Rollup should be about 400MB in size.
……. If things stay the same, the Jan 2020 Patch Rollup for Win 7 should be about 1.2GB in size.
Pls disregard the above. Sorry for the wrong info.
Dan
KB3192391 is the security only update for October. It only includes security patches released in October (read those usually with bulletins associated).
KB3185330 is the regular monthly update that includes security and other updates.
KB3188740 is a .NET update which needs to be installed separately.
@ Martin B ……. Fyi, the July 2017 Rollup KB3172605 for Win 7 64bit was 29MB in size, for August 2016 KB3179573 was 2MB in size n for Sept 2016 KB3185278 was 60MB in size. The Oct 2016 Patch Rollup KB3185330 was 119MB in size. The Nov 2016 Patch Rollup is 133MB in size.
.
So, looks like u r correct, ie the monthly Patch Rollups for Win 7/8.1 are not cumulative. My apologies.
.
.
P S – Since security-only monthly Patch Rollups can only be installed manually, those who will be doing a clean reinstall of Win 7/8.1 some months from now will be stumped if they want security-only updates, ie Windows Update Service only enables automatic security n non-security monthly Patch Rollups..
November Security Only — is this now October + November Rollup?
Which supplemental .net security updates are needed?
The security updates are not cumulative. This means that you need to install them for each month separately.
Martin, thanks that is awesome having the links to the Catalog. We now only have two low-use 8″ tablets with win8.1 on them as they will not run any Linux distros that I can find. Everything else is now Ubuntu for this family. :)
I agree. You provide a wonderful service that saves others a lot of time. Thank you.
KB3197874 contains that telemetry garbage :(