BlackBelt Privacy: install Tor, WASTE and MicroSip on Windows
BlackBelt Privacy is a free program for Windows that installs the anonymity focused applications Tor, WASTE and VOIP on the device you run the installer on.
While you can install all three clients manually on a Windows PC, the main advantage of using BlackBelt Privacy is simplicity provided that you want to use at least one, better two or three, of the services it installs on the computer.
Installation is painless and there is little that can go wrong in this regard. Firefox users should take note however as the installation may corrupt their session restore functionality if that is being used.
It is recommended to save the session to make sure it can be restored prior to installing BlackBelt Privacy.
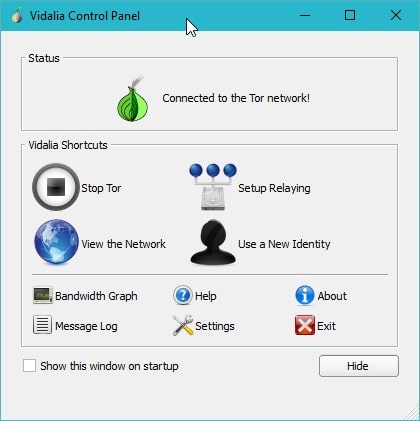
BlackBelt Privacy
When you install the program, several things happen. First, Tor, WASTe and MicroSip are installed on the PC. The program places several entries in the Windows Start menu and on the desktop that you can use to control the functionality of the applications.

BlackBelt Privacy attempts to create a Tor profile for Firefox during installation, but this did not work on the Windows 10 system and a regular Firefox stable installation that I tried this on.
That's a problem as Tor profiles for Firefox are designed to be hardened while regular Firefox profiles may leak information.
Vidalia, the Tor control panel, runs in the background and you can verify that it is working. While Tor is designed specifically to run in Firefox, you can use other browsers as well if you configure them to connect via localhost:9050 using Socks4.
A good way to check if everything is working is to look up the IP address used by the browser or application on the Internet. Use our own IP checker for instance to do that.
The two other programs that BlackBelt Privacy installs add free anonymous PC to PC calls, chat and file transfers.
MicroSIP enables you to make free PC to PC calls without account or routing through middlemen servers. WASTE on the other hand offers secure chat and file transfers.
It is highly recommended to read the readme file as it contains instructions and tips on how to use each of the supported programs. The readme, like all three applications, is linked from the start menu entry.
BlackBelt Privacy is compatible with all versions of Windows starting with Windows XP.
Now You: Do you use Tor or other services for anonymity on the Internet?
























There has been steady improvement to the suite since the excellent review by Martin.
We hope others feel the same and are happy to take this suite for a drive.
Thank you.
We have enabled the media encryption option within MicroSip. We have to acknowledge that zrtp is more desirable. We have done the best we can with MicroSip. If we can get zrtp into MicroSip we will.
With the default setting of Media Encryption enabled we at least were able to render Cain and Able VoIP sniffer software useless.
Its the best we can do at the present time.
MicroSip has no end to end encryption like ZRTP. BlackBelt Privacy shouldn’t put the word “privacy” into their software name.
We have improved the Browser Integration.
At present Firefox 32 and Cyberfox 32/64 are supported.
You can get the latest from here: http://sourceforge.net/projects/blackbeltpriv/?source=navbar
Thank you.
the thing about using privacy tools, like tor, is that all the government aims those software… they want to shut it down sooooo badly…. because they can’t control you that way. they say it’s to prevent people from stealing bank accounts and whatever, but they can’t deny freedom to people. you should be worried about your privacy and security. you think they care about your security??? they dont… just look at windows 10: ghacks.net revealed that microsoft knows E-V-E-R-Y S-I-N-G-L-E T-H-I-N-G you did on your computer. you can find the article here: https://www.ghacks.net/2016/01/05/microsoft-may-be-collecting-more-data-than-initially-thought/
the use of software like tor is recommended if you want total privacy. despite you, using antivirus, firewall, etc, I can still detect your location through your IP… using tor, ultrasurf or even hotspotshield means you are hidden. they cannot know your location. it’s the main purpose of using tor. just in somewhat an explanation, there is a story out there on gaming forums – which I dont know if it’s true or lie – about a kid that was always killing the same guy over and over and over… that guy got “sick” with the kid and one day he grabbed his IP, detected his location and after 6 months the “guy” went to the kid’s home and killed him. if that kid was using tor or ultrasurf he would live… but this is a stupid comparison.
so if you visit sensitive websites or websites that are monitored by the government, you should use tor or wait for CIA or FBI to go to your home and “kidnap” you :P
The NSA Is Targeting Users of Privacy Services, Leaked Code Shows
http://www.wired.com/2014/07/nsa-targets-users-of-privacy-services/
Flipping Heck Pants !
After reading your post, my brain is exhausted !
Time for a nap :-)
I think it is really disturbing that people consider that using a tool that makes them anonymous (like TOR) will turn them into a target. This is where our mass surveillance society brought us…
I have friends that use TOR and etc. but it is not for me. I just feel like I’m making myself a target when I have no reason to feel that way. That is just me people. That is the way I feel. I’m not saying just because you use TOR and etc. you are doing something wrong. Only you know that, Let’s don’t get started on that! I’m just speaking for the way it makes me feel.
I kind of aim towards privacy also, as Tom Hawack said.
An honest person acting in a other than normal manner near police will possibly draw their attention. Does anyone think using TOR does not provoke the curiosity of say, the NSA, or other similar government tracking agencies around the globe? Hmm?
If you want a wee peak and insight into OpSec, then read this article
https://theintercept.com/2016/01/12/sean-penn-el-chapo-opsec/
tl;dr: Its so easy to get wrong and basically every situation requires different OpSec measures. There is no one definitive answer – sometimes TOR is good, sometimes not (and a huge myriad of other issues).
@Mike O.
I’ve never acted normal in my life. Normal is eeeeeewwwwwww.
I’m strange and unusual. Police don’t bother me as long as I’m not doing anything wrong. That being said, they still turn and look at me but that’s with about 75% of people out there. I’m fine with that.
However, to use your analogy, that means anyone who isn’t directly connecting to websites through their ISP (VPN; public or private)or have extra connections coming out of their computer (work VPN) would draw the attention of NSA, CIA, KGB, M15/M16, BND, Boy Scouts, etc.also. If you really want to get down to it, visiting sites like GHacks, which has articles about privacy, should also do the same thing.
When it comes to Privacy and/or Anonymity, if you’re not open to the world, you’re not normal. Majority of the people who connect to the internet don’t have a clue about 90% of the stuff that they’re transmitting out when they go to any page. They just figure that as long as they don’t sign up to a website with their real name, they’re safe from everyone.
Privacy and anonymity indeed. Do we move in society dressed up with a mask like in “Mission:Impossible”? No. Do we move in society declaring to everyone our name, phone numbers, email and snail-mail addresses? No. We can be, and we are recognized by many who don’t know for most of them who we ARE, our identity. We are neither hiding nor disclosing our privacy, that’s the way it’s always been. Disclosing our privacy is a social and relational process requiring confidence.
Nevertheless there is a trend, a fashion initiated paradoxically by the Web which is reconsidering the very pertinence and even legitimacy of privacy. This leads to more and more people being asked — in the real world — about details of themselves, of their identity, of their lives, which has nothing to do with a commercial transaction. Recently I bought perfume as a gift and was asked while presenting my credit card my name and address! What to do then? If I play the anonymity role I’ll just lie, if I play the privacy role I’ll tell them in a straightforward yet polite way that it’s none of their business.
What I mean is this: it seems to me most of us choose an extreme position which is either anonymity or undressing oneself on the public arena, such as on social networks, when IMO the right balance is honesty together with awareness : say the truth but keep all the truth for your friends. On the Web as in life.
@Mike O
It’s a fairly complex situation. The first question anyone should ask is “who” are you trying to hide from? Is it state actors, family members, corporations, advertising networks and so on. Another consideration is whether you care or not that the metadata or contents are captured. Essentially it comes down to the circumstances, purpose and OpSec. Most certainly, TOR attracts attention and can even pinpoint you (see confirmation of DPR (silk road) as they monitored his network jumping in and out of TOR against posts by DPR, or see the student who posted a bomb threat via TOR and the university tracked him within minutes as he was the ONLY campus connection to use the protocol). The other question about TOR is who controls the exit node (I’m not an expert), and honeypots techniques. How many tor nodes are run by malicious/state actors. This is where, to answer your question, if TOR was for example, 15% of internet traffic, then it’s too mainstream to draw any real attention, and too mainstream to be effectively influenced by a third party.
There are other methods to hide your ID that don’t draw attention. For starters, I couldn’t give two flying hoots about leaking my IP (generally) if it was a one off mobile data plan bought using cash (and a disguise), or I piggybacked on someone else’s wifi/network (and they had no connection to me). OpSec still applies, such as not re-using the same connection and leaking other info (MAC addresses, other metrics, phrases/nicks used, and so on). The key is to keep each persona/id fully separate from each other. No dot connecting…
This is something that the Tor community battles with.
We cannot speak for them, but can refer you to their web site where you can actually see the kinds of people who use Tor.
https://blog.torproject.org/
This is the first program that 2 kind of people use after installing Windows: CIA employes and undiscovered pedophiles (probably you as well, for reading this article).
Please stop bringing up pedophiles in your posts.
I would had banned him already… and not just deleting his account, but ban his IP also… that guy is sick if I am allowed to use that word…
Ban ?? Block ??
Belated Happy New Year. Keep up the good work.
Holiday soon?
Nine days to go until take off. Happy New Year to you too. No blocking, editing or banning here unless there is no other option.
The only trusted download source for TOR is https://www.torproject.org/ ! Stay away from the bs advertised in this article!
Agreed and really are PowerUsers that lazy, that they need something like BlackBelt Privacy. Create a NAS\Server and store your data on it simple right.
This is absolutely true. Those that need to maintain the ultimate chain of trust should download the source code, review it and then build it.
Here is a link to the source code:
https://dist.torproject.org/
That way you can build the code yourself from source. The source is the ultimate truth for the Tor project runtime.
The resulting runtime you produce can then be copied into the installation folder.
That way all fear is alleviated and you have the best of all worlds.
This procedure is what we have followed.
Thank you
Whoa, Waste is still around? I thought it had been abandoned more than 10 years ago. It was a simple but great little program back when I used it. Worked like a charm every single time.
I was kind of surprised too when I saw waste mentioned…
I don’t use TOR nor any other hiding protocol. I’ve always aimed privacy, not anonymity. I don’t like the idea. If not displaying one’s emails, addresses, name is anonymity then I handle that anonymity. But if the scheme is that of being furtive, escaping like a fish, logging or signing on a blog/forum with different identities, then count me out.
Hi gHacks, Martin Brinkmann,
We are the authors of BlackBelt Privacy. We have duly noted your comments and critique. Thank you so much for reviewing the software.
The newest version has much better Firefox integration. You can find it at the download sites dotted around the globe, but Sourceforge is the place to get the latest stable and beta copies.
We thank you again for your review and will monitor this page for any more input from others.
We are heavily feedback driven, so people like yourself do us a great service.
We hope you enjoy using the software as much as we have enjoyed producing it.
Thank you again.
BlackBelt Privacy Team.
On further inspection there still appears to be a bug with Firefox Integration.
A new version is being shipped to sourceforge in the next 15 minutes.
Thank you for bringing this to our attention.