How to identify and prevent programs from phoning home
Networking monitoring can be an eye opener in regards to network connections of programs that run on a computer system.
I started to monitor network connections closely recently and decided to take a closer look at some popular programs installed on a Windows test machine to check if they'd phone home automatically.
The program I'm using for the monitoring is Fiddler, but programs like Wireshark should work as well.
I set up Fiddler and started to monitor the program's output while launching and using programs such as Bandizip, Steam or Firefox.
Some network connections are required obviously. When I enter an address in the Firefox address bar for instance, I want that connection to be made.
But there are connections that are not initiated by the user. Some may still be necessary or wanted by the user, a check for updates for instance. If you monitor the connections closely however, you may notice some that you don't consider essential or required at all.
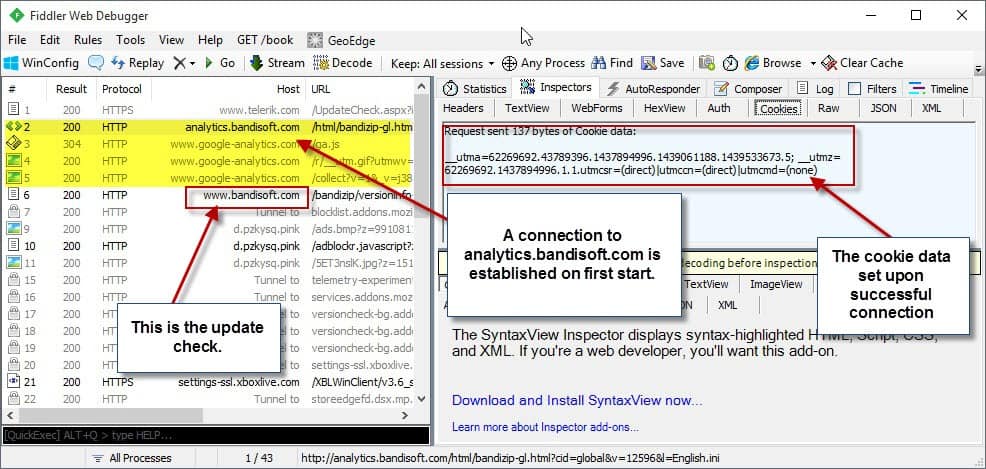
If you take the popular archive program Bandizip for instance. It checks for updates by default but also connects to analytics.bandisoft.com on first start as well.
While you can disable the update check in the program options, you cannot disable the ping to Analytics and the setting of a cookie on the system.
Dealing with unwanted connections
Once you have identified an unwanted connection on your system, you need to find a way to deal with it. You may have several options at your disposal, for instance by creating a new rule in a software or hardware firewall to block the domain.
One of the easier options is to use the Hosts file that every version of Windows ships with. Let me walk you through the steps of blocking the Bandizip Analytics domain from connecting to your system.
- Open File Explorer on your system. You may do so with the shortcut Windows-E, or by clicking on its icon in the taskbar.
- Navigate to c:\windows\system32\drivers\etc.
- Copy the hosts file to your desktop. This needs to be done as you cannot edit it directly in the directory.
- Right-click on the hosts file on the desktop and select edit. Use Notepad or another plain text editor to do so.
- Add the line 0.0.0.0 0.0.0.0 at the top.
- Add the link 0.0.0.0 analytics.bandisoft.com
- Save the document afterwards.
- Copy it back to the c:\windows\system32\drivers\etc and confirm the replacing of it.
This blocks connections to analytics.bandisoft.com by mapping it to the address 0.0.0.0 instead of its original IP address.
Why 0.0.0.0 and not 127.0.0.1? Because it is faster.
Closing Words
It takes time to monitor and identify unwanted connections on a system. A firewall may help with that if it is configured to prompt whenever a new connection is established for the first time.



















Eeek!
I had a look at gHacks info about Fiddler. It’s not that simple. Or maybe it’s because I’m feeling a bit brain weary. In any case, all I want to be able to do is run an app like for example “Hekasoft Backup and Restore”, and see if it’s phoning home each time I use it, even though I’ve unchecked the “Check for Updates on Launch” box. Is there not a simpler way of checking?
I used to use Zone Alarm Firewall many years ago until one of it’s updates to the AV component flagged and quarantined thousands of files. End result was having to re-install XP and swearing never to use ZA again. Anyway, ZA had a tray icon which flashed whenever an outbound connection was being made. Maybe I should look at ZA again. I think it’s available without having to use the AV component now.
Is that just too hit and miss?
here are all the domains windows uses to phone home
you can add them to the hosts file
i believe it is formatted as follow: please clarify if incorrect
127.0.0.1 “blocked.domain”
or as above:
0.0.0.0 0.0.0.0
0.0.0.0 “blocked.domain”
i typed them all out so you can copy and paste it
************************************************************************************************
# Copyright (c) 1993-2009 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a ‘#’ symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
# localhost name resolution is handled within DNS itself.
# 127.0.0.1 localhost
# ::1 localhost
0.0.0.0 0.0.0.0
0.0.0.0 vortex.data.microsoft.com
0.0.0.0 vortex-win.data.microsoft.com
0.0.0.0 telecommand.telemetry.microsoft.com
0.0.0.0 telecommand.telemetry.microsoft.com.nsatc.net
0.0.0.0 oca.telemetry.microsoft.com
0.0.0.0 oca.telemetry.microsoft.com.nsatc.net
0.0.0.0 sqm.telemetry.microsoft.com
0.0.0.0 sqm.telemetry.microsoft.com.nsatc.net
0.0.0.0 watson.telemetry.microsoft.com
0.0.0.0 watson.telemetry.microsoft.com.nsatc.net
0.0.0.0 redir.metaservices.microsoft.com
0.0.0.0 choice.microsoft.com
0.0.0.0 choice.microsoft.com.nsatc.net
0.0.0.0 df.telemetry.microsoft.com
0.0.0.0 reports.wes.df.telemetry.microsoft.com
0.0.0.0 wes.df.telemetry.microsoft.com
0.0.0.0 services.wes.df.telemetry.microsoft.com
0.0.0.0 sqm.df.telemetry.microsoft.com
0.0.0.0 telemetry.microsoft.com
0.0.0.0 watson.ppe.telemetry.microsoft.com
0.0.0.0 telemetry.appex.bing.net
0.0.0.0 telemetry.urs.microsoft.com
0.0.0.0 telemetry.appex.bing.net:443
0.0.0.0 settings-sandbox.data.microsoft.com
0.0.0.0 vortex-sandbox.data.microsoft.com
0.0.0.0 survey.watson.microsoft.com
0.0.0.0 watson.live.com
0.0.0.0 watson.microsoft.com
0.0.0.0 statsfe2.ws.microsoft.com
0.0.0.0 corpext.msitadfs.glbdns2.microsoft.com
0.0.0.0 compatexchange.cloudapp.net
0.0.0.0 cs1.wpc.v0cdn.net
0.0.0.0 a-0001.a-msedge.net
0.0.0.0 statsfe2.update.microsoft.com.akadns.net
0.0.0.0 sls.update.microsoft.com.akadns.net
0.0.0.0 fe2.update.microsoft.com.akadns.net
0.0.0.0 diagnostics.support.microsoft.com
0.0.0.0 corp.sts.microsoft.com
0.0.0.0 statsfe1.ws.microsoft.com
0.0.0.0 pre.footprintpredict.com
0.0.0.0 i1.services.social.microsoft.com
0.0.0.0 i1.services.social.microsoft.com.nsatc.net
0.0.0.0 feedback.windows.com
0.0.0.0 feedback.microsoft-hohm.com
0.0.0.0 feedback.search.microsoft.com
0.0.0.0 rad.msn.com
0.0.0.0 preview.msn.com
0.0.0.0 ad.doubleclick.net
0.0.0.0 ads.msn.com
0.0.0.0 ads1.msads.net
0.0.0.0 ads1.msn.com
0.0.0.0 a.ads1.msn.com
0.0.0.0 a.ads2.msn.com
0.0.0.0 adnexus.net
0.0.0.0 adnxs.com
0.0.0.0 az361816.vo.msecnd.net
0.0.0.0 az512334.vo.msecnd.net
Thanks bill gates. That’s one big list. Who knew. Not me obviously. But is it safe/wise for me to block all those Windows connections?
Would blocking ALL those windows domain phone homes have any undesirable effects on the smooth running of my Windows 8.0 system?
Are they all really totally unnecessary, at least for me with this now ancient OS.
Please, can someone provide a bit more information.
Thanks.
Martin, there is a way to directly edit the host file.
1. start => notepad => right click and run as administrator
2. now open your host file
3. save.
the problem with that is that you’ll have to start notepad as admin.
alternative, just edit it, found out that you can’t save there, so save it on your desktop.
then move it back to %windir%\system32\drivers\etc
Ann,
If people go to the mvps.org site, they go, in detail, into the best ways to edit the hosts file on the various flavors of Windows. It really is quite an excellent resource… :)
The MVP in the site name comes from the honored “MVP” designation given by Microsoft to various 3rd party contributors.
I have not yet used either fiddler (which I only recently found out about) or wireshark (which I’ve known about before) — more on that in a moment.
I have found this can be a very useful hosts file, and will block, avoid, you having to track down these bad guys in the first place.
WARNING: there may actually be some sites in there you want, so be sure to check it out. It’s 497kb in length — but if it blocks you from sites you actually want, you’ll find out soon enough. Further, they give you instructions on the care and feeding of your hosts file on various versions of Windows:
http://winhelp2002.mvps.org/hosts.htm
What I do use to monitor connections is use the SysInternals tcpview. The SI tools were apparently helpful in tracking down what was going on with stuxnet.
The SysInternals Suite can be found here:
https://technet.microsoft.com/en-us/sysinternals/bb842062.aspx (it’s free)
Just did a search on ghacks.net for SysInternals…I didn’t find as many references as I would have expected for this very savvy site!
It has seemed to me recently when doing searches on gHacks that the site’s search engine seems to be acting differently lately. It seemed to be returning only results which had my search term(s) in the article headline, and what I was looking for was either in the body of the article, or in the comments, and thus it was not showing up in the results. I could be wrong about this; that’s just how it seemed to me recently.
I succeeded in finding what I was looking for instantly by using the “Search this site” feature of the Ixquick toolbar. One can also use the “search this site” feature of their favorite search engine right from that search engine’s web page, as long as the proper search syntax is used.
Thanks for the reply … I can’t really speak to your searches, only my own — which were done from Google.
When I see a result which surprises me, I also look to see for ways in which the results I pulled up were wrong or skewed.
Now, back to the topic … and my comments about how or why MVPS hosts file and the SysInternals TCPView would appear to offer additional help to the initial concerns…
…I’d love to see a pro & con discussions about the various options. At least with TCPView, I don’t have to install a VM … :)
Thanks again!
For blocking connections within Firefox itself, I prefer BlockSite Plus: https://addons.mozilla.org/en-us/firefox/addon/blocksiteplus/
For blocking connections system-wide, both Emsisoft Anti-Malware and Emsisoft Internet Security have a “Surf Protection” component which I find provides a very handy way to fine-tune one’s Hosts file. Rather than simply “Allow” or “Block”, you have the choice of Blocking Silently always, Blocking and Notifying, and Alerting, so you can sometimes allow the connection if it is necessary in that particular instance, but otherwise block it when it occurs in other contexts.
What I miss dearly is the extremely granular information Emsisoft’s now-discontinued Online Armor firewall and HIPS provided. If anyone knows a good replacement for Online Armor, another program which provides such detailed firewall and HIPS information, I’d love to know. I tried Comodo but found it excessively complicated. I’m open to using two programs (one firewall, one HIPS) to replace Online Armor. Thanks!
There’s a hosts manager called HostsMan
http://www.abelhadigital.com/hostsman
This program is very good.
What if you want to block a wildcard domain, for instance *.googlesyndication.*, will it work when you add the asterisks to hosts?
No. Hosts files do not accept wildcards.
You need to use something like Acrylic DNS Proxy, which has a hosts file that accepts wildcards.
Thanks Martin this was helpful. Nasty Bandizip!
Martin,
If you use the 0.0.0.0 as you suggest, do you remove the 127.0.0.1 localhost lines at the top, or leave them in? In other words, should the top of the file look like this:
0.0.0.0 0.0.0.0
127.0.0.1 localhost
::1 localhost
0.0.0.0 click.buzzcity.net
……
Or like this?
0.0.0.0 0.0.0.0
0.0.0.0 click.buzzcity.net
…….
etc.
Thanks for this suggestion!
Keep it ;)
With new applications I generally test their phoning by using NirSoft’s TcpLogView.
If the application has phoned for no legitimate reason (i.e. update check I’ve decided, not if the app decides for me) then I decide to manage its connection with a small software called Firewall App Blocker (FAP) available at sordum dot org. FAP simply creates an in/out rule in Window’s firewall to block the connection of the calling application. Extremely simple scheme.Rules can be paused and removed of course from FAP itself.
FAP – excellent recommendation. Thank you!!
omg, Firewall App Blocker is great! thanks a bunch for the heads up on that! This makes it SO easy to add a bunch of exe’s from the same folder/app in one go, taking away the tedium of doing it manually in windows firewall. merci!
For something like this, wouldn’t outbound firewall whitelisting be better than using the hosts file? Or are you thinking along the lines of you want Bandizip to be able to connect to update.bandisoft.com, but not analytics.bandisoft.com?
However, ignoring the firewall option, I wonder whether some kind of system wide parental blocking feature would do a better job than the hosts file? The problem with hosts file is that it doesn’t allow wildcards, so although blocking one URL is pretty straight forward, it’s a problem when they use multiple subdomains, as you have to sit there trying to capture them all and you don’t necessarily know when they’re going to phone home.
Blocking *.bandisoft.com and then whitelisting update.bandisoft.com for example would be a lot easier than trying to manually block a whole list of subdomains.
You said you were on a Win7 machine – if you open Notepad as Administrator, and then open hosts, you can edit it directly in the C:\Windows\System32\drivers\etc directory.
Otherwise, BlueLife Hosts Editor is rather handy (and portable) http://www.sordum.org/8266/bluelifehosts-editor-v1-1/
Fiddler captures HTTP and HTTPS traffic, so it is of limited usefulness in debugging unwanted outgoing communications. Wireshark monitors all traffic, so it is superior in this area. You will want to use Fiddler when you discover a HTTPS communication and you are interested in its contents.
Another interesting tool that can be used to monitor computer communication is Microsoft Network Monitor 3.4 . I was forced to use it because Winpcap (the capture engine used by Wireshark) had some incompatibility with the Comodo firewall driver, and I didn’t want to give up using Comodo as firewall. Anyway, Microsoft Network Monitor does its job pretty well, can export files in a format that can be read by Wireshark and has an interesting feature: it can show traffic per application, so you can see what each application tried to do from a network perspective.
Thanks for calling attention to the inadequacy of just using fiddler. This article leaves the reader half-informed. Implying “Just use fiddler. Boom, you’re now omniscient” fosters a false sense of security. Oh well, at least the article represents an attempt to “raise awareness”.
I use another Bandisoft program, their Honeyview image viewer, and I noticed a while back that it too places a cookie on the system. I found that cookie using CCleaner. When people think of cookies, I’m sure many generally believe that’s something only web browsers do, but it’s sadly not the case.