Find out if your mobile is vulnerable with Stagefright Detector App for Android
Stagefright is a critical Android vulnerability that attackers can exploit using specifically prepared Multimedia Messaging Service messages (MMS).
What makes the vulnerability particularly troublesome is that it can be exploited passively on devices. All that it takes is to sent a prepared MMS to a device running Android to get system or media privileges on it.
Since it is possible to delete the MMS after it has been processed by the device and before the user had a chance to open it, it may go by completely undetected.
Considering how updates are deployed on Android, it make take weeks, months or even longer than that before devices are updated with patches for the vulnerability.
We have published a guide that explains how to protect your Android device from attacks regardless of patch status. To sum it up, all you need to do is disable the automatic retrieval of MMS on the device which most messaging apps support.
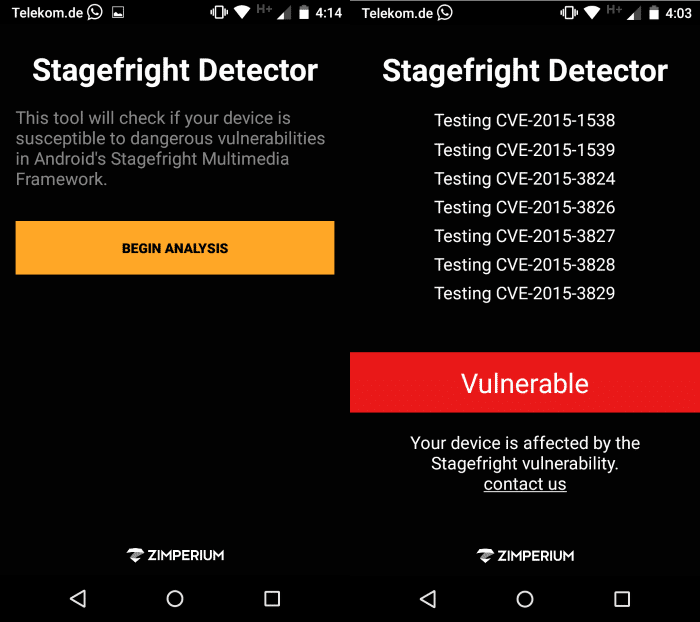
If you are unsure whether your device is affected by the issue you may use the Stagefright Detector App to find out about that.
To use the application download it from Google Play and start it afterwards. A click on the "begin analysis" button runs the vulnerability scan which should not take longer than a couple of seconds.
The result is displayed on the same page then so that you know whether your device is vulnerable or not.
The app may also point out that an operating system upgrade is needed to protect it from the vulnerability.
The Stagefright Detector App checks for the vulnerability but does not take into account the messaging settings. This means that it will conclude that your device is vulnerable to the Stagefright vulnerability even if you have disabled the automatic retrieval of MMS on it.
If you want to see Stagefright in action, watch the following exploit demo:
Now You: Is your device affected by Stagefright?




















“Considering how updates are deployed on Android, it make take weeks, months or even longer than that before devices are updated with patches for the vulnerability”
should be
“Considering how updates are deployed on Android, it may take weeks, months or even longer than that before devices are updated with patches for the vulnerability”
But considering how they are actually deployed, probably will be never for a minor update
Well, I should take that back….Issued on August 5th:
http://www.androidcentral.com/att-patches-stagefright-exploit-galaxy-s6-active-note-4-s5-and-s5-active
Sprint and ATT are pushing software updates to patch it. So I’d keep checking throughout the day for Software Updates on your phones (I’d manually do it).
My Nexus 4 got an update yesterday which should have fixed this, yet it tells that my device is vulnerable.
https://i.imgur.com/XFUoW9f.png
https://i.imgur.com/WfKMmzo.png
You could also use https://play.google.com/store/apps/details?id=com.lookout.stagefrightdetector
Made by LookOut
This reports my phone as safe :)
>it make take weeks, months or even longer than that before devices are updated with patches for the vulnerability
90+% of all current devices will never ever get an update.
That’s it. I’m quite disappointed that most news websites are saying something similar, although the truth >is< that most devices will remain vulnerable forever.
You should add a few lines about the app author company. Never heard of Zimperium before.
Zimperium is an Israeli mobile security company which has uncovered and published the Android Stagefright security bug.