Sites may detect the local IP address in browsers supporting WebRTC
Whenever you connect to sites on the Internet information about the connection and the underlying system are available to the site automatically.
Information include the web browser and version used to connect, the language, operating system and also the remote IP address.
While there are means to prevent the IP address from being revealed, by using proxy servers or virtual private networks for example, one IP address is revealed in the end.
The local IP address on the other hand was protected up until now which meant that sites could not use JavaScript to look it up. While plug-ins like Java allow sites to do that, users are usually notified when plug-in contents are executed on sites.
The recent integration of WebRTC in Firefox, Chrome and other Chromium-based browsers such as Opera have privacy implications as sites may use it to detect the local IP address of the computer.
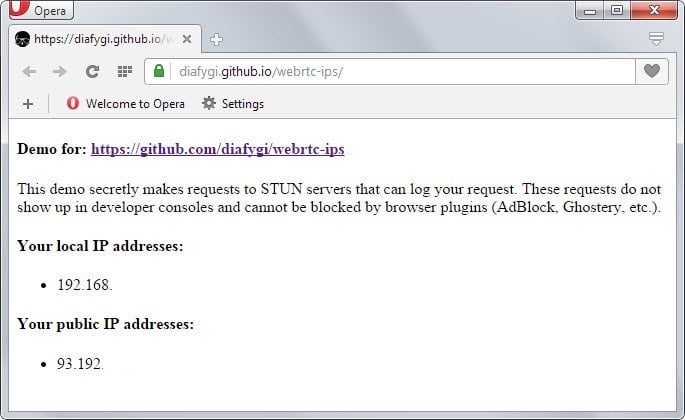
You can test this by visiting this Github page which will reveal the local and public IP address when opened.
The main issue is that the local IP address can be used to identify your system when used in conjunction with other information retrieval techniques.
So how does it work?
WebRTC allows requests to be made to STUN servers (Session Traversal Utilities for NAT) which return local and public IP addresses for the system that is used by the user.
The results can be accessed using JavaScript which means that the only requirements for this to work are WebRTC support in the browser and JavaScript.
Protection
Ad-blockers such as Adblock Plus or Ghostery don't block these requests as they are made outside of the "normal XMLHttpRequest procedure".
The only extensions that block these look ups are JavaScript blocking extensions such as NoScript for Firefox. It is naturally also possible to disable JavaScript to prevent this from happening but this renders many websites unusable as well.
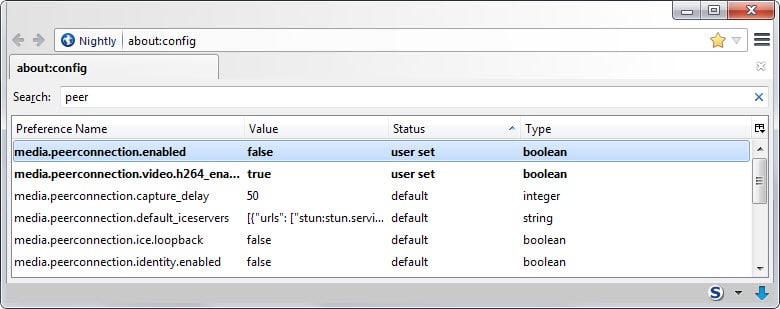
Firefox users can disable WebRTC
- Type about:config in the browser's address bar and hit enter.
- Confirm you will be careful if the prompt appears.
- Search for media.peerconnection.enabled.
- Double-click the preference to set it to false. This turns of WebRTC in Firefox.
Note: Turning of WebRTC means that services and applications that make use of it, such as Firefox Hello, won't work anymore.
Google Chrome and other Chromium-based browser users can install the WebRTC Block WebRTC Leak Prevent extension which disables WebRTC in the browser.
Additional information about WebRTC spying are available here.


















Hello,
I did a test with an other tool : https://anonymster.com/dns-leak-test/ (DNS Leak Test).
I would like to recommend any VPN user to test their VPN for leak… This can expose the real ip.
May wish to update your link as the one published is dead. Here is another one.
https://chrome.google.com/webstore/detail/webrtc-leak-prevent/eiadekoaikejlgdbkbdfeijglgfdalml
Duh… two in one day…
From: https://support.mozilla.org/en-US/kb/config-editor
To access the config editor, go to Tools | Options, select the Advanced panel,
select the General tab, and click Config Editor….
Not exactly obvious but I found it…
Now the $64000 dollar question, how do you test that Web RTC is disabled in Thunderbird???
Duh… I solved my own problem in Seamonkey by using the above mentioned:
about:config…….media.peerconnection.enabled set to false
Also mentioned was Thunderbird… For someone who’s never changed Thunderbird
how does one get into about:config in Thunderbird???
As mentioned previously IE8 and Pale Moon are secure and I’ve managed to fix Firefox but
Seamonkey reveals my local IP address.
Does anyone know how to stop it in that browser?
I just released this add-on for Firefox that will prevent all WebRTC at the same time notifying the user to accept a connection:
https://addons.mozilla.org/en-US/firefox/addon/statutory/
lite_version 10kb: https://bugzilla.mozilla.org/attachment.cgi?id=8570682
These demos to test it:
https://diafygi.github.io/webrtc-ips/
http://ipleak.net/
https://bugzilla.mozilla.org/show_bug.cgi?id=271559
Chrome:
A less-drastic way to address this issue is to set the following preference (added in Chrome 42).
webrtc”: {
“multiple_routes_enabled”: false
},
For the location of the prefs file, see http://www.chromium.org/administrators/configuring-other-preferences.
This forces all WebRTC connections to only use server-reflexive and relay ICE candidates, and only on the default IP route. While this may cause a QoS hit (two users behind NAT can no longer keep their traffic internal to the NAT), it does allow the issue mentioned here to be fully addressed without disabling WebRTC altogether.
This security flaw will only reveal your local IP. So if you use a router with NAT for your local network and a VPN on your computer for anonymity reasons a website would not be able to get your real IP. It’s only when you are not using a NAT this is a problem!
How is webrtc turned off in the Aviator browser by whitehatsec.com ? They say that the Aviator Browser is the securest on the web but the browser reveals all of the IP addresses. aviator@ whitehatsec.com is their website e-mail address. Please reply ,Thank you.
Sorry to be so late on this. Does anyone have the problem I am having with IP leakage with WebRTC? I am using OpenVPN to connect to a VPN provider. Visiting https://diafygi.github.io/webrtc-ips/ page (with Google Chrome) mentioned in article, both my local IPs are visible: 192.xx.., and 10.xx… Also, both my regular public IP and VPN IP are visible even though I am connected through the VPN. Does this break the privacy of VPN’s or am I leaking my non-VPN IP somehow and not knowing?
New story in TorrentFreak (http://torrentfreak.com/huge-security-flaw-leaks-vpn-users-real-ip-addresses-150130/) addresses my concerns. Both the home IP and VPN IP are shown by WebRTC even when connected through the VPN. Fixes mentioned here and running the VPN on the router will work.
WebRTC Block for chrome no longer works (as of 05 February 2015). https://diafygi.github.io/webrtc-ips/ has been updated and all IPs are now again visible.
Used Pale Moon happily until all of my FF plugins broke, then jumped to Cyberfox AMD. Thanks for bringing this (mostly useless) plugin to our attention. I could imagine such a thing being abused and little in the way of utilitarian benefit.
I think browsers should not support WebRTC natively.
Plugin support, as used in IE and Safari, is preferred.
FireFox
about:config…….media.peerconnection.enabled
set to false
Disable WebRTC 1.0.1 Add On works fine in Firefox.
What does this involve:
Maelish January 27, 2015 at 2:56 pm #
Also… folks with Thunderbird might want to use the `about:config` setting as well.
My Pale Moon v25.2.1 (x64) and Internet Explorer 11 v11.0.9600.17501 do not show my IP addresses on that Github page, but Firefox v35.0.1 does. It’s a good thing that I only use IE or Firefox when Pale Moon doesn’t work with a site (which is rare)? As discussed in other recent articles, by default Firefox now has a lot of privacy holes (in addition to breaking a lot of add-ons). I should just uninstall Firefox, since I rarely use it anymore.
Thank you Martin for another great ‘heads up’ article.
In chrome/chromium is possible to disable webrtc by launching the browser with the command line switch “–disable-webrtc”.
For reference and full list of chrome/chromium command line switch check here: http://peter.sh/experiments/chromium-command-line-switches/
Obviously you can’t change on the fly, so for many people is likely better using some webrtc-block extensions, but if you run chrome/chromium episodically the command line switch do the trick (I’m on linux: I use chromium with the pepperflash plugin only for a couple of sites).
:)
It’s not worked. I just tried it.. Any new solution?
Thanks, that is a good point and definitely useful to some Chrome users who don’t need it at all.
Pale Moon is safe.I guess it doesn’t support WebRTC.
That’s correct, Pale Moon does not support WebRTC and I’m sure never will. Which, in my opinion, is a good thing. I hadn’t tested my installed browsers but I”m happy to say that at least for me Pale Moon, Firefox, Chrome and IE11 all passed the test.
There is an extension called “WebRTC Block”. This is for Chrome. For it to work in Opera you need to install the “Download Chrome Extension” extension. Going to the “github” page my IP address is not displayed. So I’m assuming it works.
I tested in Chrome Canary, Chrome Beta, Opera Dev, FF 34.05 (my IE 11.0.96 doesn’t support webRTC) on Win7
none of them exposed my local IP
(only one flag in canary “#Enable Delay Agnostic AEC in WebRTC”, left on default )
http://prntscr.com/5xoiyw
*sigh* Just another thing that eagerly leaping forward without thinking has given us.
Although the article doesn’t mention it, there are 2 add-ons for Firefox that will disable WebRTC just like the Chrome mentioned above. They are available from the regular mozilla add-ons directory. Just search for `webrtc` and you’ll find them.
At least one of the two add-ons you mention (I presume the one I have in mind is in the lot) is the best method IMO to conciliate privacy and WebRTC advantages : it includes a toolbar button that switches WebTRC on/off. Considering the privacy implications I would have appreciated and considered it as adequate for a company that makes privacy its badge, that such a toolbar button be included by default in the browser when WebRTC was launched.
Here we’ve disabled WebRTC, Loop and anything to do with what I consider as a function which is not a natural browser component. A better, more secure, faster browser : YES. A bloated interface which happens to be a browser : NO.
At least we have as always with Firefox (easy) access to enable/disable their latest fantasies. Still, if it weren’t for sites like gHacks many users as always would ignore where the switches are, especially when they are so called “hidden” that is accessible only from about:config.
I’m sorry, you are right.
>”At least we have as always with Firefox (easy) access to enable/disable their latest fantasies.”
Not really, you can no longer disable social bloat api. They have removed the about:config preference for that. Also click-to-play-per-element won’t work with E10, unless Mozilla brings it back.
As for NoScript for Firefox being the only extension which can protect users from script-relied attacks – there is the excellent HTTP Switchboard extension for Opera which brings the script blocking of NoScript and a lot more. Unfortunately it lacks the other security enhancements that come with NoScript.
I never said NoScript is the only extension. HTTP Switchboard is great.
Also… folks with Thunderbird might want to use the `about:config` setting as well.