Google improves recent activity information for accounts
There is a lot that you can do to improve the security of your Google account. It starts with a secure password but does not end there. You can enable 2-step verification for example to add another layer of protection to the account, or make sure that you receive phone alerts when suspicious activities are recognized by the system.
The Security Settings page is the central hub for many of these security related preferences and information. There you can change your account password, enable or disable 2-step verification, configure phone alerts, check app and website permissions, or set recovery phone and email.
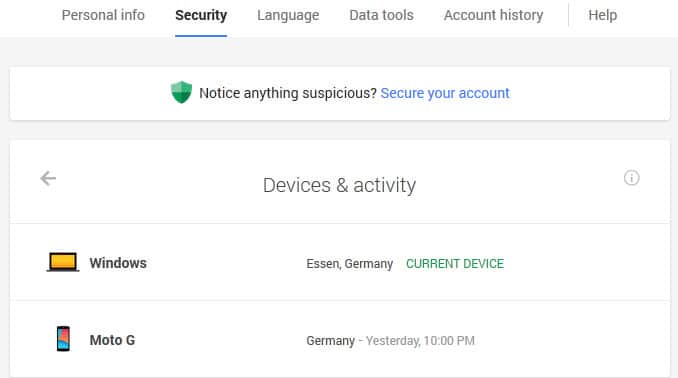
The Recent Activity pages have been improved in recent time. The page lists two, devices & activity and notifications & alerts.
Devices & Activity lists all devices that have been used to connect to the Google account in the past 28 days. The page lists each device with its name (or operating system), a location and when the sign in was recorded.
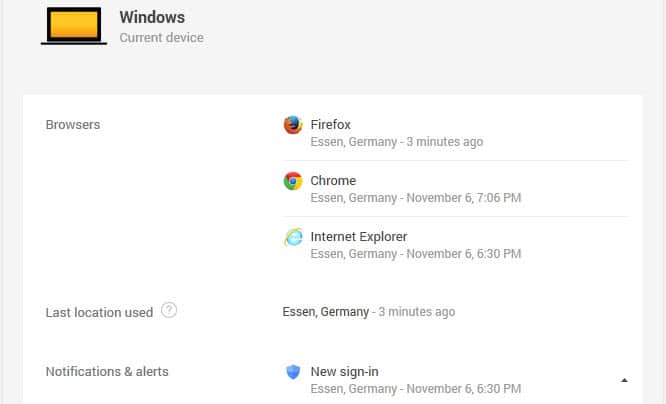
A click on a device displays additional information about it. This includes web browsers or programs used to connect, the device model if it is a mobile device, the login location for each browser used, the type of access and whether a device has full account access or not.
For some devices sign in information may be available. If that is the case you can reveal information about the IP address used as well.
Access can be removed for devices connected to the account in the past which is useful if you lost your phone, if your computer got stolen or if your account has been hacked and devices are used to connect to it that you don't own.
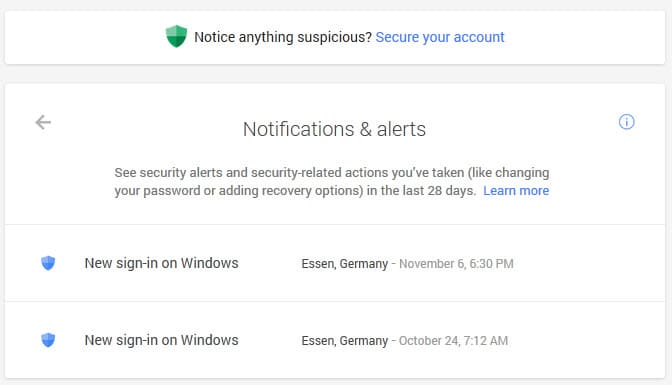
The Notifications & Alerts page on the other hand lists all security alerts and security-related actions of the last 28 days. This includes sign-ins, password changes, the use of recovery options or if the phone number has changed or was added in the first place.
A click on a log entry displays IP addresses, the device used for the connection and the location.
This can be quite useful as well as you can check if you recognize all activities. If you don't, you find information about what a third-party did, for instance that someone changed the recovery phone number or signed in at a time where you were not on the Internet.
You can bookmark those two pages directly or the central page. It is probably a good idea to check the two pages regularly to make sure that everything's alright with the account. It can also be useful to unlink any old device from the account.
Now You: What's the first thing you do when you notice unauthorized access to your account? (via Caschy)





















Under “Devices & activity” mine shows an iPad, synching yesterday… except I don’t have one! All my other devices show, so it doesn’t seem like one is mislabeled. Expanding the iPad, there’s no “Remove” button and “Last location” only shows the country, nothing more specific. I’ve got 2 factor enabled and no “app passwords”, but this device still keeps synching. How do I remove it or track it down???
I get a warning every day when i fire-up the PCs, and tablet. Since it doesn’t indicate the app which was blocked, and I have never gotten an app which said that it failed to sign-on, I am at a loss as to what to do with such info. It is when I sign on and at my location — this I know. Now what? Useless.
You can also view your account’s last activity and each ip address used when you sign in by going to Gmail and clicking the very tiny button on the bottom on the page to view the “Details” about your “Last account activity”. A new window will pop up with all the information and include a button to sign you out of all other sessions too.
I’ve had a Gmail account since before it was released to the public. I have never noticed anyone’s IP address in there but my own. I use the full 100 characters in my password and use the new two step verification. I’m surprised we are restricted to 100 characters. Facebook and Twitter seem to be unlimited. I use more than 300 characters there.
I use the HTML version. So I doubt I’ll see these changes.
You are quite the character! ;)
Really Helpful! Thanks!
Still waiting for “destroy all user data among servers” feature. But it’s rather impossible.
I doubt this will ever happen unless Google is forced to add the option.
Thanks!!