New Phishing Attack fakes Google sign in on Google servers
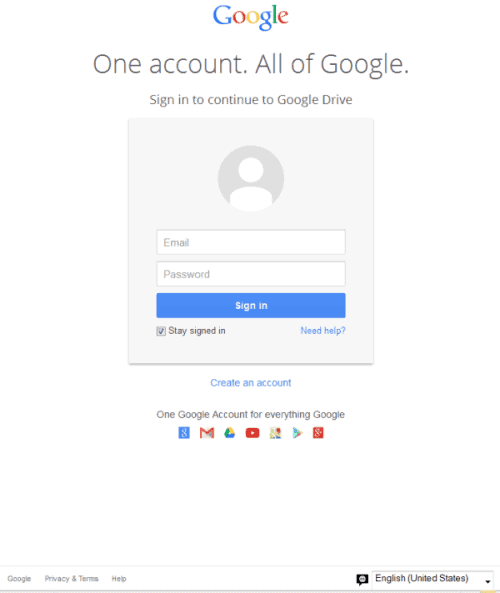
Most phishing and data grabbing attacks have a major problem: they cannot use the domain of the official service, but need to use another one.
Some use similar looking domains, or very long domain names that start right but are only sub-domains and end with an unrelated domain name.
The latest phishing scam that Symantec noticed recently takes the idea to a whole new level. Instead of hosting the fake website on a different domain, the attackers use Google's own Drive and Docs service to host the files.
The effect? When you check the url, you see that it is using https and that it is a google.com domain. So, everything is alright then, right?
The scam begins like many other scams. You get an email with a link. This link points to a google.com address, and when you follow it, you are asked to sign in.
The problem here is that this is not an official Google sign-in link, even though it is hosted on a Google domain and using a Google SSL certificate.
How the spammers do it? They have created a folder on Google Drive, made that folder public, uploaded a file to it, and use the preview feature of Google Drive to get a publicly accessible address that they use in their phishing attempts.
So, the sign-in form is fake, even though it looks real, is on google.com, and uses SSL.
If you sign-in here, your authentication credentials are transferred to a PHP script on a compromised web server. You are redirected to a Google document afterwards, which means that you may not even realize what just happened -- that you gave away your Google account to a third-party.
There are a couple of indicators that may warn you that something is not alright. First of all, the link you are taken to is not a Google Sign-in link which -- as far as I know -- always begins with accounts.google.com no matter which service you are accessing from the company.
If you do not see accounts.google.com, chance is that you are not on an official sign-in page.
Second, and this is more a behavioral suggestion: never click on links directly in emails, especially not if you do not know the sender of that email. Instead, visit the website of the service directly by loading the page manually in your web browser of choice, signing-in there, and checking out whatever someone added to the email.
And even if you click on the email link, warning flags should go up when you are asked to sign-in if you are already signed in to your account.
Google seems to have fixed the issue according to Gizmodo information. Fixed in this case means that Google has removed the fake pages but has not yet released a fix that protects future abuse. The team appears to be working on that though.
Google suggests that you reset your password if you think that you may have given out your account information accidentally.
Closing Words
Phishing attacks get more sophisticated all the time, but this is a whole new level. If you can host your fake login pages on domains owned by the company that you want to steal user credentials from, then it is taking phishing to a whole new level.
Advertisement
















The situation reminds me very much of natural predator-prey evolution. The most unsettling aspect to me: while this Google-hosted fake page takes phishing to a whole new level, what with the NEXT level after that be? I suppose it’s a never-ending progression of attack-and-defend.
I don’t know if this will help but I am going to henceforth log into my account a couple of times using false log-in information to see if my account will open up!
Hmmm.
Again, Mr. Brinkmann et al thank you for all of your Timely articles – – especially in this S-c-a-r-y day and age!
Not gonna help, really – because in the back the form actually tries to authenticate you with the credentials you’re entering, so if you put in faux login info it will fail (and therefore show you a message to log in again), and if you put the right credentials it’ll see that it’s right and redirect you to the document. Classic “man-in-the-middle”.
Only way to be 100% on the safe side, imho: when you see a form like this coming up from a link to a document, open a valid google.com account login (like mail.google.com or docs.google.com), login there and then try to open the document again; if the login form persists it’s this scam, if the document opens it’s the real deal.
i was just asked to sign into google at howtogeek. i’m always signed into google !!! i better do some checking…
I just browsed to how-to-geek. No Google sign-in entering User/Password requested. You can sign-in with your Google (or Facebook…) account on numerous sites, but there in no need to enter your user+password once you have logged in any Google service (Gmail, Docs…).
you must have went to a completely different howtogeek, nice try though…
Can you tell what page exactly did you get this? I would like to see how this thing is working.
Thanks.
So Question: Is the picture above a legit Google sign in request page? I just saw this page a couple days ago when trying to goto Google docs and I did think it was wierd because I’m usually always signed into to gmail. I just thought since I hadn’t been to Docs in a while it was a verifing me.
Scary stuff…
RK
According to Symantec, this is a fake one. I think it is hard to tell without seeing the full address.