Create encrypted text that can only be decrypted by combining shares
In the movies you sometimes see plots were something can only be accessed by multiple actors. Say, the launch codes of nuclear bombs that need to be activated with two keys, or a safe that will only open if two people are authenticated properly.
Secret Sharp for Windows follows the same principle, only electronically. Instead of having keys, fingerprints, retina scans or other means of identification, you have so-called shares.
Each share is part of the puzzle, and taken together, reveal the secret message that lies behind.
Lets say you want to make sure that your family can access your encrypted PC after your death. You could make your encryption password the secret, and provide several family members and a notary with shares so that they can decrypt the password together and get access to the computer system.
The same is of course true for other information. Maybe you want to share a safe combination, a phone number, or simply a passphrase for backup purposes. It can also be used to send a message to a single recipient using different transport types to make it less likely that someone listening in on the communication can restore the message.
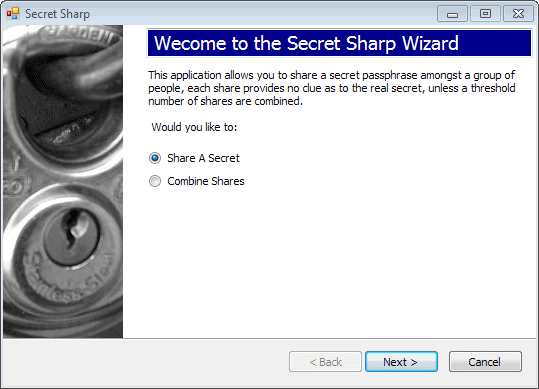
Using Secret Sharp is really easy. Once you have installed the program on your system, you are walked through the creation of a new secret and shares that protect it. Alternatively, you can select to combine shares to reveal an existing secret right away.
Select the number of shares and the minimum amount needed to reconstruct your secret. You can create four and have any two reconstruct it, or may configure the program to require all shares created to do so.
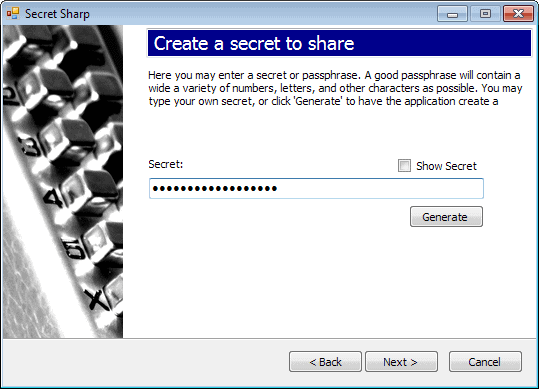
Type your secret on the next screen. You can show it here as it is hidden behind asterisks by default. Alternatively, have the program generate a secret for you.
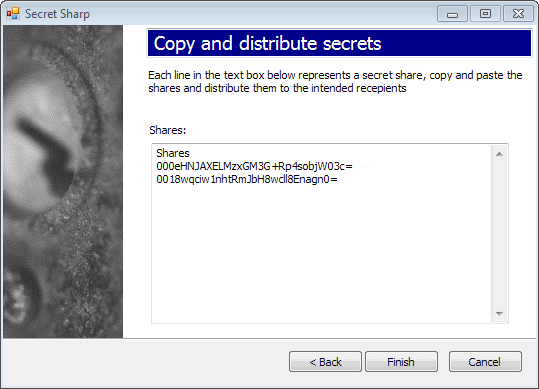
The shares required to reveal the secret are displayed on the next page. You need to copy and distribute them to recipients, or safe keeping on your devices.
The program is based on Shamir's Secret Sharing Scheme (ssss) which describes a method "for distributing a secret amongst a group of participants, each of whom is allocated a share of the secret".
According to Wikipedia, Shamir's secrete sharing is considered a secure secret distribution system:
AdvertisementIn contrast, consider the secret sharing scheme where X is the secret to be shared, Pi are public asymmetric encryption keys and Qi their corresponding private keys. Each player J is provided with {P1(P2(...(PN(X)))), Qj}. In this scheme, any player with a private key 1 can remove the outer layer of encryption, a player with keys 1 and 2 can remove the first and second layer, and so on. A player with fewer than N keys can never fully reach the secret X without first needing to decrypt a public-key-encrypted blob for which he does not have the corresponding private key - a problem that is currently believed to be computationally infeasible. Additionally we can see that any user with all N private keys is able to decrypt all of the outer layers to obtain X, the secret, and consequently this system is a secure secret distribution system.



















Hi
similar – but in my opinion better because it can also “split” files:
The Secret Splitter as discussed on
http://www.moserware.com/2011/11/life-death-and-splitting-secrets.html
Secret Splitter: https://github.com/moserware/SecretSplitter
Olaf
Sounds nice enough. Two problems.
1. What if any one of your “secret team” forgot / lost /destroyed /damaged … his share of the secret?
2. What’s the protected secret used for? For accessing an online account, that may be too troublesome. Maybe it’s fit for kids who need to buy things online, so that their account key can be protected with their parents’ or caretakers’ shares?
Neil, if too many shares are lost, to be precise, so many that the threshold cannot be reached anymore, then it cannot be decrypted anymore.
Protection can be used for anything but it only makes sense to protect important information. As I said, the master password to your PC, safe, or important messages that you need to send to someone.