How to stop Google from knowing all your WiFi passwords
Android's backup and reset feature looks on first glance like a great feature. It backs up app data, Wi-Fi passwords and other settings to Google servers, so that you can restore them at a later point in time. This can come in handy if you lose access to your phone and get a new one. Instead of having to enter the data again manually, you simply restore it to have access to it again right away.
Most Android users have the setting probably enabled by default, and those who do are not likely to object to it at all. A issue however came to light recently. If WiFi passwords are backed up as well, it means that Google can in theory access those passwords.
Some may suggest that Google is using a password or other means of protection, like it does on Chrome, so that the company cannot read the data. But if you have ever lost access to your phone and bought a new one, you may have noticed that the restore feature added hotspot and password information back to the phone automatically and without you having to enter any password or other data before that happened.
This means that Google can read the data. Even if you think that Google won't read it, it is still bound by law. And since Google is a US company, it can be asked to provide information without being allowed to talk about it.
If you look at the big picture, you will notice an alarming situation. With more than 750 million Android phones being sold in 2013 alone, Google sits on a goldmine of WiFi data. Even if Google does not access it at all, it may be forced to share the data in the US.
Block the transmission of WiFi passwords in Android
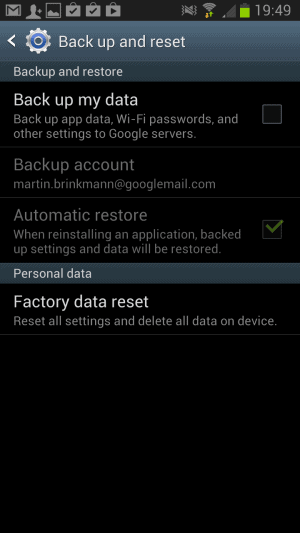
I checked my Samsung Galaxy Note II phone and noticed that it too was set to backup data to Google automatically. What you need to do is disable the feature to block the passwords from being submitted to Google. This disables the back up feature of the phone, so that you need to take other precautions, like backing up all data locally so that you have full control over it at any time.
Here are the steps to turn the feature off:
- Open the settings of your phone or tablet.
- Select Back up and reset.
- Uncheck the back up my data option.
Google notes that unchecking the option will stop the backup and delete all existing data on Google servers as well.
If you want to be extra-careful, change the WiFi passwords that you have used in the past.
Please note that the steps may be different depending on your Android version and phone manufacturer. On Android 2.x, you need to select Settings > Privacy and then the back up option displayed there. It is interesting to note that you won't find WiFi passwords mentioned here at all.
You find additional coverage of the issue over at Micaflee's blog, The Register and Tech Republic.
Advertisement



















hello thanks for guide
Excellent summary of the situation Martin. Thanks.
I use the Wi-Fi password only on the router, so if someone can read that password, it works only with my Wi-Fi (and not on my e-mail, etc).
On my dd-wrt router MAC-filtering is enabled, so even if you have that password, you can not connect.
So: should I still uncheck this confortable feature in the settings after this?
Remind me to show you how trivial it is to spoof a mac address. In fact, your home router probably has a feature built in for this to deal with fussy cable modems. Also, MAC collisions can occur when manufacturers re-use mac addresses. We need ways to handle these problems, ; )
It is very easy to spoof MACs. A simple Internet search comes up with dozens of free means to do so.
Zsolt,
If someone has the password to your router in can change your router configuration (DNS…)
and route all data in your network through a bogus server….
Mac Filtering is not a secure protection.
Report: NSA Mimics Google to Monitor “Target” Web Users
Buried in a Brazilian television report on Sunday was the disclosure that the NSA has impersonated Google and possibly other major internet sites in order to intercept, store, and read supposedly secure online communications. The spy agency accomplishes this using what’s known as a “man-in-the-middle (MITM) attack,” a fairly well-known exploit used by elite hackers….
http://www.motherjones.com/politics/2013/09/flying-pig-nsa-impersonates-google