Secure Gmail adds email encryption to Google Mail
With PRISM news losing momentum and shifting to Snowden's whereabouts almost entirely, it is likely that the majority of the world population will have forgotten about it very soon. It is unlikely that anything will be done about it to prevent that data is grabbed by agencies around the world, so that users are left with protecting their data individually.
Secure Gmail is one of those solutions. The application is currently only available as an extension for Google Chrome which somewhat limits its reach, but it is a start and it has a lot going for it. First, it is Open Source which means that you can dive right into the source code to check it out before you start using the extension.
Second, it does the encrypting and decrypting on the local system, so that emails cannot be read by Google or anyone else listening unless the correct password is known or guessed.
Third, it is super easy to set up and use.
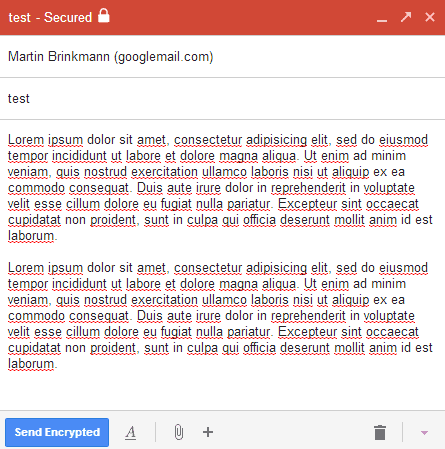
The first thing that you need to do is install the Secure Gmail extension for Google Chrome. Once you have done so you will find a new lock icon next to Gmail's compose button at the top. You click on it to create a secure message, or click on compose to create unencrypted emails instead.
The compose window highlights that the email is secured and you can use it as usual to write the message, add recipients and subjects and all that good stuff.

A click on send encrypted displays a password prompt that you need to complete. The password you select encrypts the message and needs to be known by the recipient so that it can be decrypted. You can optionally add a password hint to the encryption which may help the recipient figure out the password.
Most of the time though you may need to provide the recipient with the password as hints may help third parties with their decrypting attempts as well.
The email arrives encrypted in the recipient's inbox. Two different clear text messages are displayed on the screen depending on whether you have the Secure Gmail extension installed or not.
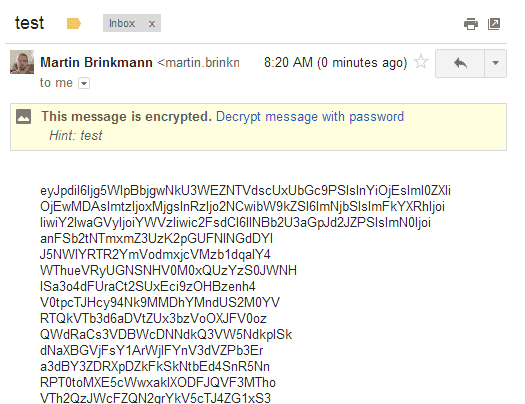
If you do have the extension installed, you get the message that it is encrypted, and that you need to decrypt the message with a password. The password hint is also displayed if it has been added by the sender.
A click on decrypt message with password opens a password prompt on the screen. Enter the password here and if it is correct, the original message is displayed on the screen.
If the Secure Gmail extension is not installed or if another browser is used or a third party email program, then you receive the message that the email is encrypted and that you need to download and install the extension first to decrypt it.
Observations
- The extension implements easy to use encryption on Gmail. Encrypting and decrypting is handled locally, and the only requirement to get started is that both sender and recipient have the extension installed.
- The recipient cannot reply via encryption. There is no option for that yet, so that it is necessary to click on the lock icon next to compose to reply with an encrypted message of your own. This means that it does not support conversations right now.
- The main limitation is that Secure Gmail is only available for Chrome right now. Extensions for other browsers and maybe even Outlook and Thunderbird would be helpful.
- The project uses an open source JS crypto library from Stanford.
- The extension prevents the saving of drafts for obvious reasons. Since drafts would be saved in unencrypted form to Gmail, they would leak information about the email to the server before it is encrypted.
- Attachments are not encrypted.
Closing Words
If you are looking for an easy to implement way to encrypt some of your emails, then Secure Gmail is definitely an extension to consider for that purpose. It is somewhat limited in terms of platforms it supports, and not the right tool if you want or require full encryption.
If you change passwords often, you may also run into decrypting issues eventually as it may be difficult to associate passwords with emails. There are a couple of ways, for instance by using the hint feature or by associating passwords with days, but even then, it may become too complex to be efficient.
Advertisement

















Sociometrics matter. First, the encryption algorithm should be portable within each e-mail so that the recipient can immediately use it in reply and new emails. The concept is called “viralability”. Second, only one password is needed. Hasn’t one already used a password to access the messaging? Third, the password should be sent in plaintext as part of the message. You did use a password to access the messaging? Why keep the encryption password a secret requiring silly issues for your reader? Fourth, a message password that changes every time serves the purpose of making messaging processing more expensive for wannabe GO’s and NGO’s.
1-plz stop supporting companies that are related to pris
2-learn abt gnu-linux
TechRepublic just emailed yesterday to me a story citing USA attorney Tyler Pitchford; per the story, it seems that although USA Courts may require that mere use of encryption must have “some relationship” to an actual offense to be captured/used in PRISM-like fashion, nonetheless the USA government views ALL even simple forms of encryption to be such “suspicious” data packets as will be detected and stored as long as the government wants…ahead of many unencrypted packets (one assumes deep packet sniffing of TCP/UDP alone can yield data headers “worth” saving). The sweep on encrypted seems to take in even say Keyscrambler, Zemana Antilogger, et al, or encrypted Google, common purpose supposedly to keep Joe Average safe from keyword redirectors and keystroke bank thieves.
Hello i use chrome 27.0.1453.116 m but the email encryption is not working for me so how you make it works?
I have never used these “browser based solutions”. I would strongly recommend you put in the extra effort and give Thunderbird and Enigmail a try. Once you set everything up, it’s very easy to send signed and encrypted emails (so long as the recipient is also using the same).
Can’t wait for the day when the web is 100% encrypted.
Should have been that way from day 1.
That’s the problem. The Internet was NOT built to be secure.
And all of these “work-arounds” are NOT good enough.
We need a new Internet in which security is priority number 1, and performance priority number 2.
Imagine if every single connection your router makes requires SSL. And if every ISP is required by LAW to use SSL for every connection. And imagine if 1024+ Bit was required.
Even if every human brain and every computer on Earth were used to crack the key, it would still take practically “forever”.
That day will come! And things such as PRISM will be extinct. The benefit to cost ratio would be sky high, and NOT even the NSA/CIA could afford to try and break the encryption.
We also need the Supreme Court of the United States to rule that the government can NOT force anyone to hand over encryption keys, period!
The court must rule that encryption keys create an “expectation of privacy” protected by the Fourth Amendment to the United States Constitution.
Only then will the Internet truly be secure “enough”. No such thing as “perfect security”, but it could be and will be a lot better in the near future.
Unfortunately from what I got out of the news about PRISM and similar NSA programs encryption might not be the sole solution to the program.
With new server farms about to be set up I think that encryptions will not stay encrypted for long. On the other hand it´s encrypted emails that will raise flags at the NSA. It will just encourage them to further investigate your data (emails, social network contacts…).
As far as they are concerned only those people encrypt their messages that have something to hide from them.
For one thing you do make it more costly for them to investigate into your net activities.
On the other hand – do you really want to raise flags at the NSA? ;-)
“…do you really want to raise flags at the NSA?”
As a non-US citizen, I don’t care (and I wouldn’t care even if I were an US citizen). Furthermore, I’d rather be “red flagged” by the NSA than have the NSA steal my intellectual property and research, or gather dirt on me (like the type of porn I view) that could later be used to blackmail me if I wanted to run for government or I managed to claw my way into a CEO position with a rich multi-national.
Privacy just happens to be a big deal to me, and rolling over just because I might be “red flagged” simply isn’t an option. I will defend my right to privacy using whatever means necessary (from any government).
“With new server farms about to be set up I think that encryptions will not stay encrypted for long”
While I agree that computing power is increasing, I very much doubt that 2048 or 4096 bit encryption has been crack yet. If it has been, someone would have written a paper about it. Remember – this stuff is subjected to the ruthless scrutiny of cryptanalysts all over the world. I recall reading that in 2006 is would take over 100 years to crack a 128 bit key using brute force (running constantly at 10 gigawatts). If you want to understand facts instead of letter FUD cloud your judgement in regards to the security of PGP, then don’t be a hater, and read this:
http://www.pgp.net/pgpnet/pgp-faq/pgp-faq-security-questions.html#security-how
An excerpt:
“Let’s say that you had developed a special purpose chip that could try a billion keys per second. This is far beyond anything that could really be developed today. Let’s also say that you could afford to throw a billion such chips at the problem at the same time. It would still require over 10,000,000,000,000 years to try all of the possible 128 bit keys. That is something like a thousand times the age of the known universe!”
One more thing – I’d still encrypt even if it could be broken by a super government agency. At least I’d still be protecting myself against those who don’t have super computers.
I agree with you regarding the quality of encryption. Therefore I think we should look for ways to encrypt in such a way, given the progress in processing power (Moore’s law comes to mind) and anticipating the abilities of the coming quantum computers, that it will take a lifetime before those creepy agencies will be able to decrypt our messages.
I’m not so concerned about ‘raising flags’, because ideally everybody should start encrypting all their communications now.
To be honest it`s been ages (10+ years) since I have taken a look into encryption/decryption in detail. I would be intersting to know how much processing power would be necessary to decrypt emails with a state of the art encryption.
On the other hand I would never get my friends (wich make up the majority of my email traffic) to decrypt their emails. Not because they are unaware of the situation but because they are probably to lazy ;-) .
The mojority of them make excessive use of whatsapp and facebook – what more do I have to say?^^
Friends can be your worst enemies when it comes to protecting your privacy!
sadly, not a very simple fix for most people without changing OS, and or email etc.
This is very sad. Not only sad, but most likely illegal. Once of the biggest problems is that Microsoft have locked in OEMs with licensing schemes/deals. The average consumer doesn’t have many options if he/she wants to go out and purchase a laptop (or desktop, for that matter) with Linux pre-installed. Microsoft strong-arms OEMs by telling them that if they sell their computers with Microsoft Windows exclusively, they get a huge discount. This clearly goes against many anti-competition/anti-trust laws.
For those of us brave enough to venture over to the Linux world, we usually find that we still have to pay for a Windows licence at the point of purchase. There’s also the problem of BIOS upgrades – many manufacturers now are providing a Windows executable to update the BIOS. And of course, we now have the problem of the UEFI “secure boot” fiasco. Installing Linux (dual-booting) just became a lot more difficult, even for those with some experience.
I guess it depends on what you’re after. If you don’t care too much about security and privacy, then Windows is just fine. You’re right though, there is no “simple fix”, but I’ve found that putting in a little extra effort is well worth it, especially when it concerns my personal privacy (something that’s very important to me).
Using a Windows PC for encryption is totally OK, as long as you keep it secure. This is also true for any other OS. Just because there are fewer attacks on other OS, like Linux, doesn’t mean that it can’t be subverted by a malicious party (NSA comes to mind).
Nebulus said on July 3, 2013 at 12:11 pm
“Using a Windows PC for encryption is totally OK, as long as you keep it secure.”
You are totally right. And I mentioned that: one should keep the data and its processing on a PC separated from the internet. This is the only possibility of ‘keeping’ Microsoft Windows secure, as neither can the Microsoft Company be trusted, nor can the internet providers and modem (firewall) builders, and also the ‘security software’ companies can not be trusted. They all will do as the government (NSA) tells them to do.
Agree with comments about Windows. Microsoft was also listed in the leaked slides as a “participant” and “data provider”. Use Linux!!
Make that gpg key 4096 bits long, sorry :)
A few comments:
1. Using a net connected (Windows) PC for en/decryption is totally self-defeating. ‘Side-channel attacks’ are very easy to carry out, and, with the symmetric encryption used in this pathetic attempt of google to pretend to care about our privacy, if the sender’s system can’t be attacked successfully, then the receiver’s probably can. And then there’s always the opportunity to catch the key during the transfer from sender to recipient.
2. I’m using Linux (Fedora) with the Evolution mail-client which natively supports gpg.
3. Even while using gpg with a 4048 bit key length, I’m not sure for how long this will ‘guarantee’ my privacy in the light of NSA etc. just vacuum up all communications for later decryption, possibly eventually with quantum computing and whatever may come next.
4. Encrypting and decrypting on an internet-connected PC is very very dangerous.
One should dedicate a separate and disconnected computer for encrypting, decrypting, storing and processing the data.
However, m a y b e Qubes-OS m i g h t be a viable solution to that problem.
A clarification:
1. Install Thunderbird
2. Install Gpg4win Vanilla (just the components you need)
http://files.gpg4win.org/gpg4win-vanilla-2.1.1.exe
3. Install Enigmail addon
Gpg4win Vanilla is a much cleaner, less confusing install.
It has only what is needed for Thunderbird.
Thanks for the correction, KK. I don’t use Windows, I use Linux, and GnuPG is installed by default (you can see this by starting a terminal and entering: pgp –version).
Sorry, correction: by entering gpg –version
Mailvelope which uses GnuPG, available for Chrome and soon Firefox, works with Gmail, Hotmail, Yahoo and GMX. It can also be configured for other mail providers.
I strongly agree with Caitlin Williams. Google is part of the problem as it was mentioned as a “data provider” to various NSA programs. If privacy is important to you, then you should not be using Google.
I’m not sure how “secure” the Secure Mail Extension for Chrome is, as I have yet to review the code. From what I’ve read in this article, it sounds like it’s using “symmetrical cryptography”. In other words, the same password used to encrypt is used to decrypt. This still leaves you with a very big problem – securely informing the recipient of the password.
Nebulus mentions the availability of EnigMail for Thunderbird. Personally, this is my favourite because it uses “asymmetrical cryptography”. In other words, you encrypt with one key, and decrypt with a completely different key. It’s something referred to as “public key cryptography”. In my humble opinion, this is by far the better option, because you can openly publish your public key which enables anyone to send you an encrypted email that only your private key can decrypt. Here’s the basic flow:
1. Install Thunderbird.
2. Install the EnigMail Plugin.
3. Follow the instructions to generate both your private and public keys.
4. Protect your private key with a password.
5. Publish your public key (this involves uploading it to a “key server”, like pool.sks-keyservers.net).
6. People can look up your public key on the key server.
7. Using your public key, people can send you encrypted emails.
8. Using your private key, you can decrypt those emails.
The added advantage of using public key cryptography is that you can also “sign” your emails. When you sign an email, a verification process is available that leaves zero doubt that you wrote the email (because you stamp it with something that’s encrypted with your private key that only your public key can decrypt, hence proving the email was signed by your private key).
Using public key cryptography can be daunting for the uninitiated, but once you get used to it, you wonder how you ever got by without it. There are downsides though:
1. The person you’re sending encrypted emails to must also have a public/private key pair and must also be using OpenPGP (EnigMail, or some other OpenPGP client).
If anyone wants to try out EnigMail, you’re more than welcome to email me:
a dot turfer at gmail dot com
You can search for my public key at: pool.sks-keyservers.net
Anyone who still values their privacy should be using EnigMail (or any other OpenPGP client).
hold your horses guys Startmail by Ixquick is coming soon :)
Cheers
Now that’s good news :)
Enigmail doesn’t work well with TB-Portable (even using GPG Portable). What I do is to access GMail via POP/IMAP using TB-Portable, then using its built-in s/mime functionality (no extensions needed). Email certs can be had free via Starcom or COMODO, and unlike PGP, s/mime is supported natively by the main email clients: TB, Outlook, WinMail, OE, The Bat…
I like OpenPGP, I even have my old 512 and 1024 bit keys (my current one is 2048), but it is often messy to implement using consumer email clients. I wish the major clients would support OpenPGP natively, but until that day comes, s/mime is good enough for my needs.
Thanks, very useful.
” Extensions for other browsers and maybe even Outlook and Thunderbird would be helpful.”
Thunderbird already has Enigmail.
Since it has been proven that Gmail has a NSA backdoor, it makes much more sense to never use Gmail and not trying to fix that backdoor. Not to mention that Chrome is also made by Google and deserves the same trust.
Google and their near monopoly is the problem.
The “solution” they developed forces people to use both their Gmail and Chrome platforms.
Using more google products is not the solution.
If your mail is encrypted you can store it in gmail. Even if the message is copied to the NSA server they can’t process it without cracking the key, which is a very hard and expensive process.
I entirely agree. Nevertheless should I be on Gmail and Chrome (both is asking me a lot) this extension would be my first move.
What may also be pointed out I think is the vulnerability of email, whatever be the OS and the e-mail client. Encryption is a requirement perhaps for any sensitive content.
This fails to encrypt the attachments… :-)
You are right, I have added that info to the review.