Shodan, a search engine for vulnerable Internet devices
Most search engines index all kinds of contents, not only web pages and services. You may use them to find open web cams, printers that can be remotely controlled or other devices connected to the Internet that either are not protected at all and therefore publicly accessible, or using protection that is not very secure, for instance when the authentication information are contained in the source of when the devices use known default passwords.
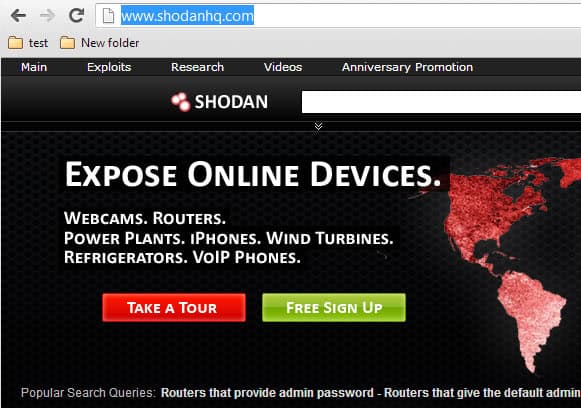
Shodan is a search engine for vulnerable Internet devices, a specialized search engine so to say that crawls the web exclusively for devices that are accessible publicly in one way or the other. The search engine concentrates on SCADA (supervisory control and data acquisition) systems and findings range from stand alone workstations to wide area networking configurations.
One of the best ways to get started using the search engine is to either take the tour, or click on one of the popular search queries displayed by the search engine on its front page. Examples include a search for routers that use the default admin password, web services that use default passwords, anonymous ftp servers or Cisco devices that do not require authentication at all.

You can filter by country or service right from the main page by clicking on the down arrows beneath the search form. Here you can select one or multiple countries that you want to include in the search as well as popular services.
Shodan makes available contents that are publicly available. It does not crack, hack or decrypt information to make the services available, it only adds information that it finds to its database and makes that database available for searches. There is a high chance that the information that it finds get used by malicious users and organizations, but also by security researchers and businesses. One effect that Shodan may have is to bring security more into the focus of the public.
Advertisement



















Defcon talk about this
http://www.youtube.com/watch?v=5cWck_xcH64
Don’t Use Linksys Routers
…I hooked it up and spent maybe 30 minutes testing the security of the embedded website used to manage the device, then never used it again. What I found was so terrible, awful, and completely inexcusable! …
https://superevr.com/blog/2013/dont-use-linksys-routers
Linksys (Cisco) has been sold last week to Belkin.
….that is unless you plan on flashing it with dd-wrt or some other third-party firmware, in which case it’ll be rock solid and much better (and safer) than stock.
Running latest Tomato (by shibby) on mine; it’s just amazing.
Also, I love the System Shock series of games.
99% of home users buying the popular Linksys routers don’t know what Firmware or flashing mean.
To remind you : A researcher has found 420,000 vulnerable devices connected to the Internet, , hacked those device into a botnet in order to scan for all ipv4 addresses. :
Port scanning /0 using insecure embedded devices
Carna Botnet
While playing around with the Nmap Scripting Engine (NSE) we discovered an amazing number of open embedded devices on the Internet. Many of them are based on Linux and allow login to standard BusyBox with empty or default credentials. We used these devices to build a distributed port scanner to scan all IPv4 addresses. These scans include service probes for the most common ports, ICMP ping, reverse DNS and SYN scans. We analyzed some of the data to get an estimation of the IP address usage…
http://internetcensus2012.bitbucket.org/paper.html