EA's Origin platform vulnerable to remote code execution attack
Electronic Arts, one of the largest game publishers, has a lot of problems these days. First there was the Sim City fiasco where the company decided that it is more important to fight piracy and push micro-transactions than to provide users with a game that they can actually play.
Yesterday, company CEO John Riccitello announced that he would step down and while that is not necessarily related to Sim City or other issues the company is currently facing, it is a clear sign that things look dire for EA right now.
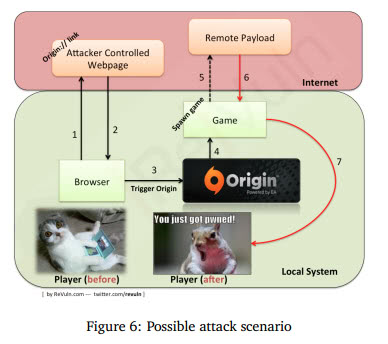
If that was not bad enough, it became known today that the company's digital distribution and game management platform Origin is vulnerable to remote code execution attacks. Security research company [Re]Vuln released a paper and demonstration video that explains in detail how Origin users may be attacked.
The basic idea behind the attack is the following. Origin, much like Steam, uses a protocol - origin:// - to launch games on local systems. These links can be shortcuts on the local system or displayed on websites on the Internet. Attackers can make use of that by manipulating the links to load remote payloads on local systems.
While this still means that users need to click on those links, it is likely that mass distribution, for instance via email or a popular website, can lead to a series of attacks on user systems.
The attacker needs to reference a game installed on the user's PC for the payload to be loaded on it. This can be easily done via a brute force type of attack as Origin accepts multiple game IDs listed in the launch url. To make matters worse, the payload can be started with silent commands.
The only workaround right now is to only run games right from within Origin and not from shortcuts or websites. This may limit the available launch parameters right now and if you can't abstain from using shortcuts or links, make sure you only execute them on sites that you trust. Even better, right-click those links and analyze them to make sure that they do not include remote payload commands (check the paper for how this looks like, basically, you should find an IP or domain name near the end that references the attack server).
EA is investigating the issue.
Advertisement
















DRM: putting paying customers in harm’s way since 2005.